Which Custom Template app connectors are appropriate to use if a website does not require user authentication?
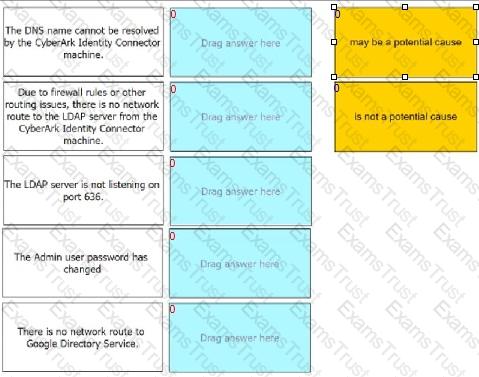
For each statement listed, indicate if it may be a potential cause of this problem.
You are tasked to enforce certificate based authentication onto all the domain-joined Windows machines within your organization. Based on the inventory record, there are 1000 Windows machines, which include 150 standalone Windows machines. The enrollment will be conducted from either the office network or through the Virtual Private Network (VPN).
Which parameter(s) should you define within the enrollment code to ensure the security of the code and that only the authorized endpoints get registered?
When logging on to the User Portal, which authentication methods can enable the user to bypass authentication rules and default profile? (Choose two.)
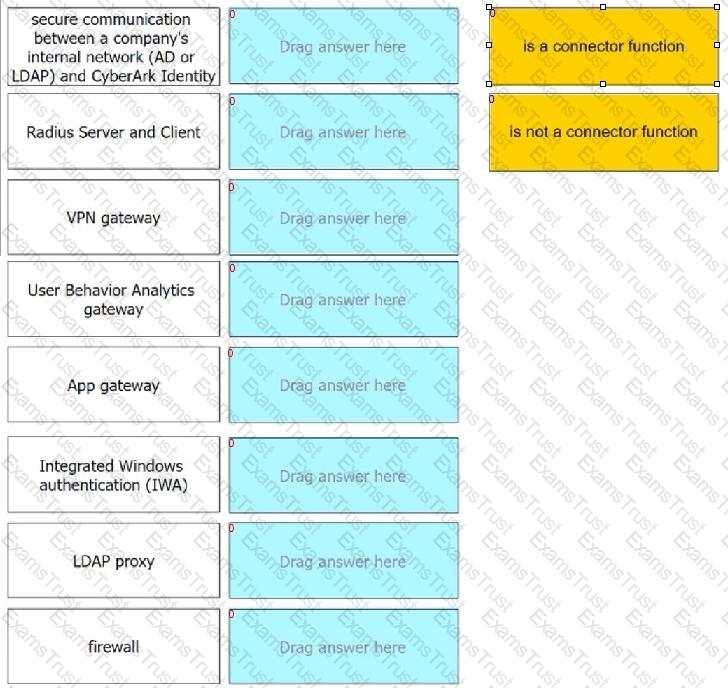
For each option listed, identify if it is a CyberArk Identity connector function.
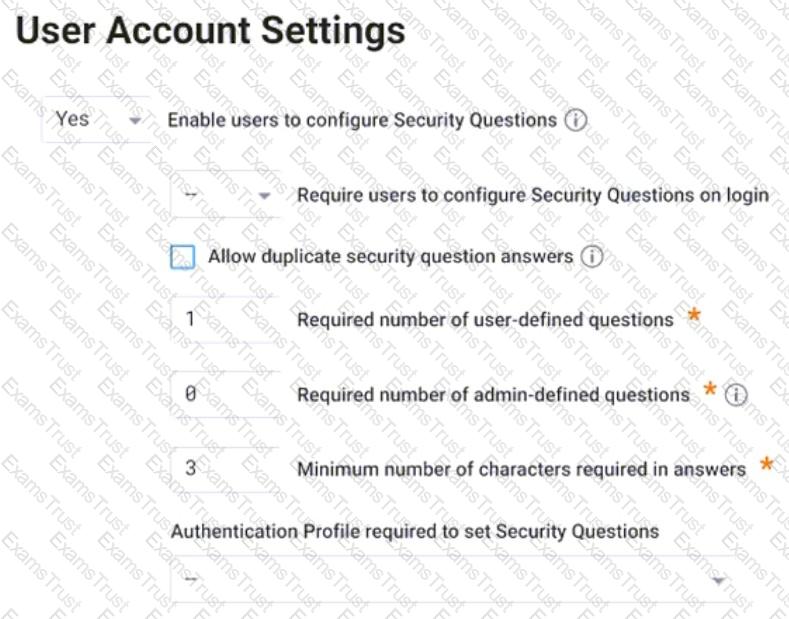
Refer to the exhibit.
Which statement is correct about this configuration shown?
Which statement is correct about the CyberArk Identity Windows Device Trust enrollment process?
Your team is deploying endpoint authentication onto the corporate endpoints within an organization. Enrollment details include when the enrollment must be completed, and the enrollment code was sent out to the users. Enrollment can be performed in the office or remotely (without the assistance of an IT support engineer). You received feedback that many users are unable to enroll into the system using the enrollment code.
What can you do to resolve this? (Choose two.)
Which 2FA/MFA options can fulfill the "Something you are" requirement? (Choose two.)
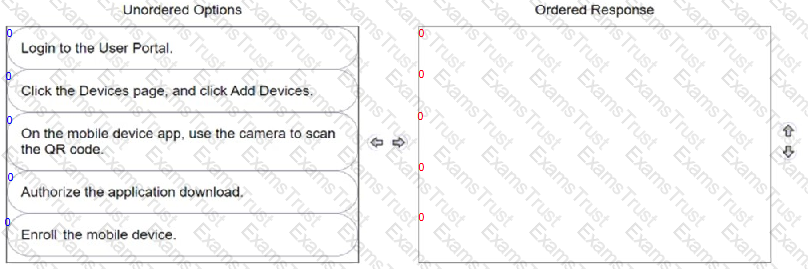
A user wants to install the CyberArk Identity mobile app by using a QR code.
Arrange the steps to do this in the correct sequence.
Which CyberArk Identity supported web standard is commonly used for enterprise Single Sign-On and issues XML tokens for authentication?
When can 2FA/MFA be prompted? (Choose two.)
Which protocols can CyberArk provide MFA for VPN? (Choose two.)
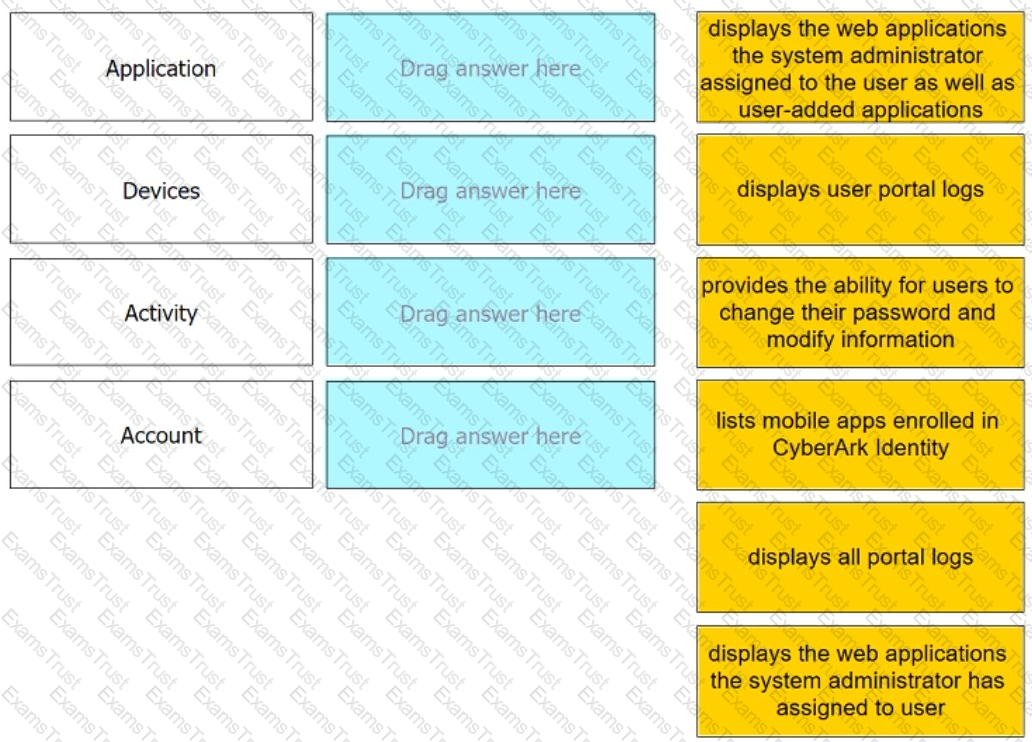
Match each User Portal tab to the correct description.
You want to find all events related to the user with the login ID of "ivan.helen@acme".
Which filter do you enter into the UBA portal data explorer?
What does the CyberArk Identity App Gateway work with? (Choose three.)
Which feature does the CyberArk Identity Connector provide?
ACME Corporation employees access critical business web applications through CyberArk Identity. You notice a constant high volume of unauthorized traffic from 103.1.200.0/24 trying to gain access to the CyberArk Identity portal. Access to the CyberArk Identity portal is time sensitive. ACME decides to enforce IP restrictions to reduce vulnerability.
Which configuration can help achieve this?
Which statement is true about the app gateway?