An administrator wants to add a user named comptia to the system administrators group. Which of the following commands will accomplish this task?
A system administrator needs to run a job called payments_Reconciliation on the last day of the month at the end of the day. Which of the following lines in crontab should be inserted to complete job?
A)
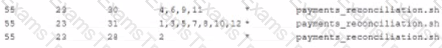
B)
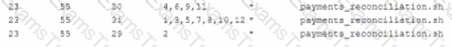
C)
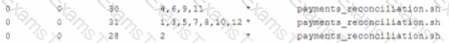
D)
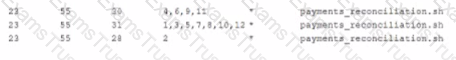
A security team informs the Linux administrator that a specific sever is acting as a n pen relay. To which of the following is the security team referring?
Which of the following files would a junior systems administrator check to verify DNS server settings?
An administrator wants to use a Linux server’s GUI remotely but is limited by security to using TCP port 22. Which of the following is the BEST choice for installation on the Linux server to enable this functionality?
The dracut command is used to:
A systems administrator needs to install software packages on a server from an Internet-based repository. The server does not have Internet connectivity.
Which of the following can be used to allow the server to connect to the Internet through the systems administrator’s desktop?
Users are receiving permission-denied messages when trying to access a spreadsheet file within the company’s filesystem. A Linux administrator receives a ticket and begin to investigate the following output:
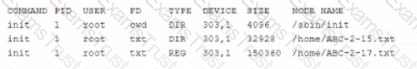
Which of the following command would produce the presented output?
An administrator is utilizing an automation engine that engine that uses SSH to run command on remote systems. Which of the following does this describe?
A system administrator recently installed and configure a web proxy server with the IP address 192.68 address. What is the should be implemented on then proxy server to ensure traffic is processes.
A)
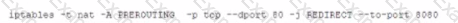
B)
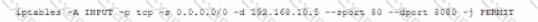
C)
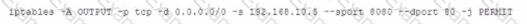
D)
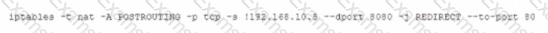
An administrator recently installed a second NIC in a server to interact with machines in an isolated enclave. However, the mnetworking on the server has not worked since it was installed. The administrator reviews the following output:
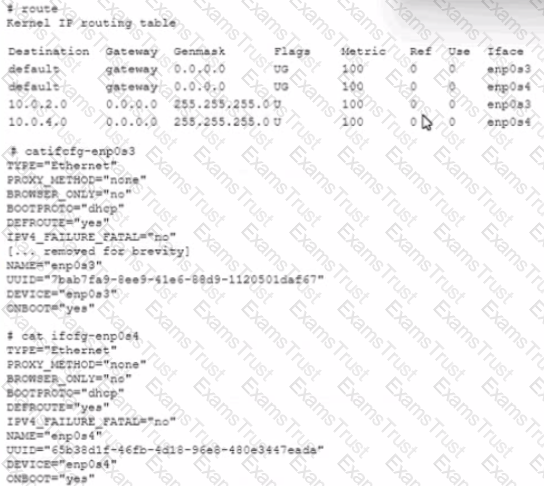
Which of the following should be the FIRST action to remediate the issue?
Which of the following is the MOST common method used to access Windows systems that are running in a cloud provider from a Linux system?
A systems administrator copied the latest archive Of the corporate application, corpapp.tar.gz, to a new server. The backup software lists the following entry in the log file:
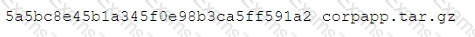
Which of the following should the administrator run to verify the archive copied correctly without corruption?
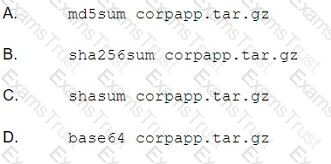
Which of the following commands will result in the HIGHEST compression level when using gzig to compress a file name file, txt?
An administrator is provisioning and attaching a secondary disk to a Linux server as a data drive. Which Of the following commands the administrator use to find the UUID Of the disk so the drive can be mounted upon boot?
A systems administrator wants to increase the existing drive space on a Linux server with a software RAID. After physically adding the new drive to the system, and then adding the drive to the RAID array,
the administrator notices the available drive space has not increased. A status of the array shows the new drive and the original storage space:
md0 : active Raid sdd1[3]S sdc1[2] sdb1[1] sda1[0]
954585654 blocks level5 64K chunk algorithm 2 [3/3] [UUU]
Which of the following should the administrator do to make all storage space available on the RAID array?
A technician reviews the following output:
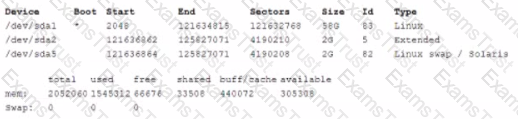
Which of the following commands should the technical execute to ensure the system has the appropriate paging? (Select TWO.)
A Linux administrator needs to run a command in the background of a terminal, Which of the following commands will BEST accomplish this task?
A systems administrator needs to prevent the root account from being used to log in to a Linux server via SSH. Which of the following configuration ies does the systems administrator need to edit to perform this task?
A systems administrator is installing an HTTPD server on a Linux server and configuring it as a proxy server. The administrator runs the following commands to verify that the service is running:
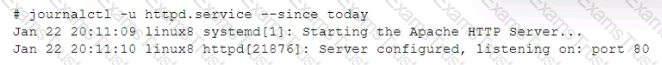
However, the administrator is getting a 503 error when browsing to portal . company. internal. After reviewing the logs, the following error information is discovered:
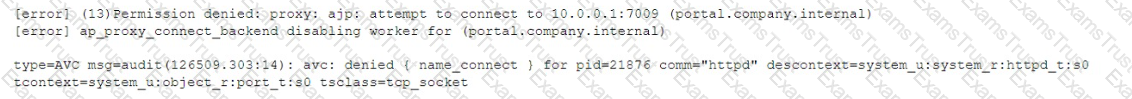
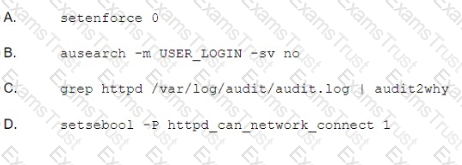
Which Of the following commands BEST resolves the issue?
An administrator is writing a Bash script to audit SSH logins. Which of the following logs would the administrator parse to find the needed information?
A Linux administrator is tasked with implementing a solution that will centralize information and allow it to be searchable and available for reporting purposes. Which of the following server roles should the administrator implement?
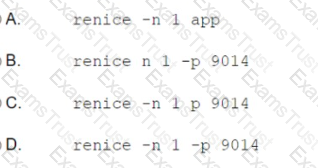
A Linux administrator is optimizing a system in which an application needs to change the priority to one for the running process: 9014. Which of the following commands will achieve this task?
Which of the following would be used to check a sensor input to a Linux system?
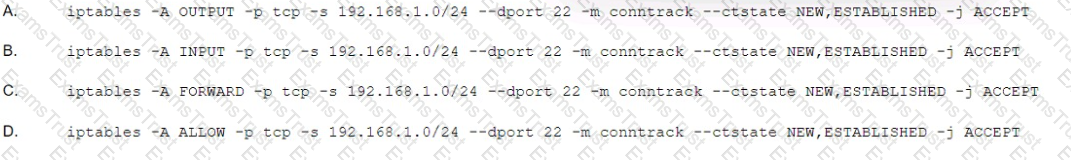
A systems administrator is required to allow only SSH access to the Linux servers from the 192.168.1.0/24 network. Which of the following iptables rules would accomplish this requirement?
The ability to add web servers dynamically during peak user activity and remove them when user activity decreases is an example of:
An administrator added a disk to a virtual machine. The administrator attempts to mount the first partition with the following command:
Mount/devsda1/mount_point
The administrator receives the following error message:
Mount: /mount_point: does not exist.
Which of the following BEST solves thrs issue and allows the administrator to run the mount command?
An administrator needs to examine two text files and select identical lines from the files. Which of the following commands wooW BEST accomplish this task?
A user deleted a log file because the disk was running out of space on a system running a mission-critical application. Even though the log file was large, the available disk space did not increase. The systems administrator determines the following files are still open:
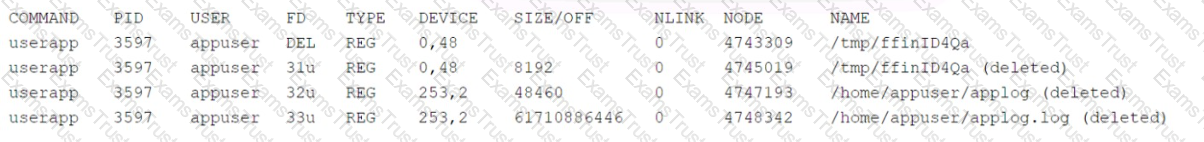
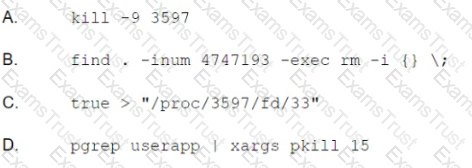
Which of the following should the systems administrator perform to BEST free up disk space?
A technician needs to install the package, tar,gz, which contains the source code of custom software The technician downloaded the file in /crap Which of the following commands should the technician use to install the executable? (Select Two.)
A Linux administrator mounts a directory to a Linux workstation by executing the command mount -t ext4 /dev/sdb /mnt /leg. After rebooting the workstation the mounted device is missing. Which of the following commands should it is mounted after reboot?
A newly deployed application is not able to reach the database that is running on a Linux server. The connection should occur at port 1521/tcp from appsrv 192.168.1.11 to dbsrv
192.168.1.12.
A server administrator runs a few diagnostic commands with following results:
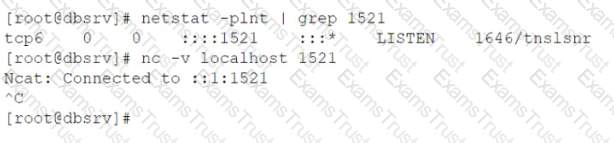
The same command when run from the application server gives the following result:
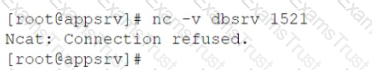
Both machines are in the same IP subnet, so no external network device is causing the issue.
Which of the following commands BEST solves the connectivity issue at the dbsrv machine? (Select TWO).
An administrator is investigating issues with an unresponsive website hosted on an internal web server named websrv. After gathering diagnostics data the administrator performs the following analysis:
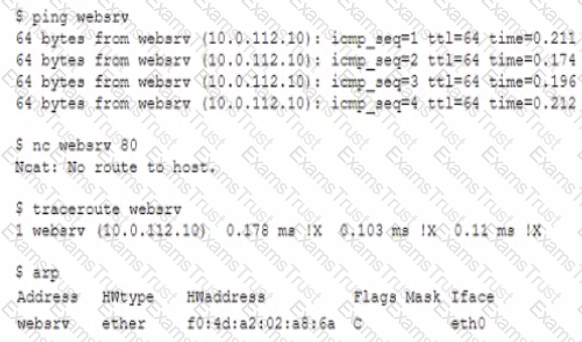
Which of the following would MOST likely resolve the issue on the web server?
A Systems administrator needs to examine the output of all kernel-related events since the system was booted. Which of the following would BEST display this information?
A Linux administrator updated the graphics drivers using a package manager but now the server does not boot. Which of the following is the BEST way to get the server back into an operational state?
Whenever an administrator merges the feature branch into master, a binary is created and saved in the artifact repository. Which of the following does this desenbe?
A Linux administrator tries to ping a hostname in a network but receives the message: hostname not found. The administrator is sure the name exists on the network and wants to verify if the DNS server is correctly configured on the client. Which of the following files should the administrator use to verify this information?
A junior administrator is configuring local name lookups for fully qualified domain names in an isolated environment. The administrator is given a checklist and must accomplish the following tasks:
Given this scenario, which of the following steps should the administrator perform to accomplish these tasks?
When requesting SSH access to a remote system, a user accidentally emailed the id_rsa key to the
administrator. Which of the following should the user do NEXT?
A systems administrator is using a Linux laptop to troubleshoot network devices. The administrator runs the
following command:
# screen /dev/USB0
Which of the following does this command MOST likely accomplish?
A new user has been added to a Linux machine. Which of the following directories would contain the user’s
default files?
A systems administrator manually added a new library to the server. The administrator wants to rebuild the
library cache for immediate use.
Which of the following commands should the systems administrator run to achieve this goal?
The following tools help maintain consistency across different systems in an infrastructure:
SUSE Manager
Red Hat Satellite
Spacewalk
If a system file is changed, the tools roll back the file to a predefined configuration.
Which of the following concepts BEST describes this behavior?
A Linux administrator recently changed the IP addresses of all the web servers from 10.10.50.x to 10.10.100.x. The administrator needs to update the serverlist.txt file to reflect the change.
The file contains the following:
10:WebSvr01:10.10.50.21:Main
11:WebSvr02:10.10.50.22:Acconting
12:WebSvr03:10.10.50.23:Intranet
20:NFS01:10.10.20.21:FileServer
30:SMTP01:10.10.30.31:Email
Which of the following commands will change the IP addresses and update the files in place?
Which of the following default files are typically used to contain a list of public keys from other computers? (Choose two.)
A technician suspects a company's border firewall is down, thus blocking Internet access. The technician executes the following commands:
#ping -c 1 firewall.company.com
64 bytes from firewall.company.com (192.168.1.1): icmp_seq=1 ttl=64 time=0.061ms
#ping -c 16
16 packets transmitted, 0 received, 100% packet loss, time 14999ms
Which of the following commands should the technician use to BEST determine the source of this outage?
An administrator is installing a new kernel but is getting an error indicating the filesystem is out of space. A disk
usage check shows / has plenty of space.
Which of the following BEST represents where the administrator should check next?
An administrator is trying to access a server in a cloud via SSH but is unable to log in. The administrator determines the company’s IP address has been blocklisted on the server.
Which of the following should the administrator do to prevent being blocked in the future?
A user wants to use terminal services from a Windows workstation to manage a Linux server. Which of the following should be installed on the Linux server to enable this functionality?
An administrator is installing a Linux VM on a personal hypervisor. The administrator wants to have the VM’s IP address on the same network as the hypervisor host so the VM has the same network properties as the physical interface of the host. To which of the following should the administrator set the network properties?
An administrator needs to kill the oldest Bash shell running in the system. Which of the following commands
should be issued to accomplish this task?
A Linux administrator is configuring a server to log security events for the ping command while allowing the request to occur. The Linux server is using AppArmor to manage its security services.
Which of the following commands is the BEST option?
A corporate server security policy states, “Ensure password hashes are not readable by non-administrative
users.” The administrator should check the permissions on which of the following files to ensure the server
satisfies this policy?
A directory called /employee is shared with many employees in a company. New hardware was acquired, and the systems administrator needs to back up all files in /employee before the server is replaced.
Which of the following commands should be used to back up all the files and compress them to use little space in the filesystem?
A user wants to list the lines of a log, adding a correlative number at the beginning of each line separated by a set of dashes from the actual message. Which of the following scripts will complete this task?
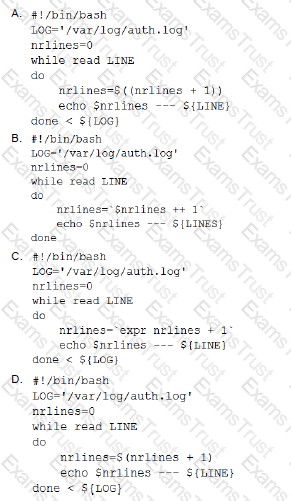
An administrator needs to see a list of the system user’s encrypted passwords. Which of the following Linux files does the administrator need to read?
A Linux administrator needs to remotely update the contents of the URL.
Which of the following commands would allow the administrator to download the current contents of the URL before updating?
A technician wants to secure a sensitive workstation by ensuring network traffic is kept within the local subnet. To accomplish this task, the technician executes the following command:
echo 0 > /proc/sys/net/ipv4/ip_default_ttl
Which of the following commands can the technician use to confirm the expected results? (Choose two.)
A Linux server needs to be accessed, but the root password is not available.
Which of the following would BEST allow an administrator to regain access and set a new known password at the same time?
A Linux administrator needs the “tech” account to have the option to run elevated commands as root.
Which of the following commands would BEST meet this goal?
An administrator has written the following Bash script:
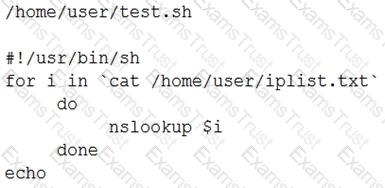
All necessary files exist in the correct locations. However, when the administrator executes /home/user/test.sh the following error is received:
No such file or directory
Which of the following is the MOST likely cause of the error?
A Linux engineer is troubleshooting a newly added SCSI device for a Linux server that needed more disk
space without rebooting. The engineer discovers that the new device is not visible by the Linux kernel in
fdisk -l output. Which of the following commands should be used to rescan the entire SCSI bus?
A junior Linux administrator is trying to verify connectivity to the remote host host1 and display round-trip statistics for ten ICMP.
Which of the following commands should the administrator execute?
A Linux administrator needs to switch from text mode to GUI. Which of the following runlevels will start the GUI by default?
An administrator needs to mount the shared NFS file system testhost:/testvolume to mount point /mnt/testvol and make the mount persistent after reboot.
Which of the following BEST demonstrates the commands necessary to accomplish this task?
A systems administrator needs to install a new piece of hardware that requires a new driver. The driver should be manually installed. Which of the following describes the order of commands required to obtain module information, install the module, and check the log for any errors during module installation?
An administrator needs to create a shared directory in which all users are able, write, and execute its content but none of the regular users are able to delete any content.
Which of the following permissions should be applied to this shared directory?
A Linux administrator must identify a user with high disk usage. The administrator runs the # du –s /home/* command and gets the following output:
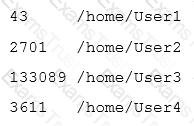
Based on the output, User3 has the largest amount of disk space used. To clean up the file space, the administrator needs to find out more information about the specific files that are using the most disk space.
Which of the following commands will accomplish this task?
Which of the following BEST describes the purpose of the X11 system?
An administrator needs to deploy 100 identical CentOS workstations via PXE boot. Which of the following should the administrator use to minimize the amount of interaction with the consoles needed?
While creating a file on a volume, the Linux administrator receives the following message: No space left on device. Running the df –m command, the administrator notes there is still 50% of usage left. Which of the following is the NEXT step the administrator should take to analyze the issue without losing data?
A systems administrator configured a new kernel module, but it stopped working after reboot. Which of the following will allow the systems administrator to check for module problems during server startup?