Which of the following is the best way to consistently determine on a daily basis whether security settings on servers have been modified?
Which of the following is an example of a false negative vulnerability detection in a scan report?
Which security controls is a company implementing by deploying HIPS? (Select two)
An organization discovers that its cold site does not have enough storage and computers available. Which of the following was most likely the cause of this failure?
A business received a small grant to migrate its infrastructure to an off-premises solution. Which of the following should be considered first?
A security engineer at a large company needs to enhance IAM to ensure that employees can only access corporate systems during their shifts. Which of the following access controls should the security engineer implement?
During a penetration test, a vendor attempts to enter an unauthorized area using an access badge Which of the following types of tests does this represent?
A company with a high-availability website is looking to harden its controls at any cost. The company wants to ensure that the site is secure by finding any possible issues. Which of the following would most likely achieve this goal?
Sine© a recent upgrade (o a WLAN infrastructure, several mobile users have been unable to access the internet from the lobby. The networking team performs a heat map survey of the building and finds several WAPs in the area. The WAPs are using similar frequencies with high power settings. Which of the following installation considerations should the security team evaluate next?
An organization issued new laptops to all employees and wants to provide web filtering both in and out of the office without configuring additional access to the network. Which of the following types of web filtering should a systems administrator configure?
Which of the following is a qualitative approach to risk analysis?
An employee used a company's billing system to issue fraudulent checks. The administrator is looking for evidence of other occurrences of this activity. Which of the following should the administrator examine?
A security analyst is assessing several company firewalls. Which of the following cools would The analyst most likely use to generate custom packets to use during the assessment?
Which of the following is a benefit of launching a bug bounty program? (Select two)
Which of the following is used to validate a certificate when it is presented to a user?
Which of the following environments utilizes a subset of customer data and is most likely to be used to assess the impacts of major system upgrades and demonstrate system features?
A network administrator deploys an FDE solution on all end user workstations. Which of the following data protection strategies does this describe?
Which of the following mitigation techniques would a security analyst most likely use to avoid bloatware on devices?
An IT manager is putting together a documented plan describing how the organization will keep operating in the event of a global incident. Which of the following plans is the IT manager creating?
A security analyst learns that an attack vector, which was used as a part of a recent incident, was a well-known IoT device exploit. The analyst needs to review logs to identify the time of initial exploit. Which of the following logs should the analyst review first?
Employees sign an agreement that restricts specific activities when leaving the company. Violating the agreement can result in legal consequences. Which of the following agreements does this best describe?
Which of the following is a primary security concern for a company setting up a BYOD program?
An administrator learns that users are receiving large quantities of unsolicited messages. The administrator checks the content filter and sees hundreds of messages sent to multiple users. Which of the following best describes this kind of attack?
Which of the following phases of an incident response involves generating reports?
Which of the following can be used to mitigate attacks from high-risk regions?
A penetration test has demonstrated that domain administrator accounts were vulnerable to pass-the-hash attacks. Which of the following would have been the best strategy to prevent the threat actor from using domain administrator accounts?
A security analyst must prevent remote users from accessing malicious URLs. The sites need to be checked inline for reputation, content, or categorization. Which of the following technologies will help secure the enterprise?
Which of the following cryptographic methods is preferred for securing communications with limited computing resources?
Which of the following best describes why me SMS DIP authentication method is more risky to implement than the TOTP method?
Which of the following actions best addresses a vulnerability found on a company's web server?
Which of the following would be best suited for constantly changing environments?
Which of the following threat actors would most likely target an organization by using a logic bomb within an internally-developed application?
While investigating a possible incident, a security analyst discovers the following log entries:
67.118.34.157 ----- [28/Jul/2022:10:26:59 -0300] "GET /query.php?q-wireless%20headphones / HTTP/1.0" 200 12737
132.18.222.103 ----[28/Jul/2022:10:27:10 -0300] "GET /query.php?q=123 INSERT INTO users VALUES('temp', 'pass123')# / HTTP/1.0" 200 935
12.45.101.121 ----- [28/Jul/2022:10:27:22 -0300] "GET /query.php?q=mp3%20players I HTTP/1.0" 200 14650
Which of the following should the analyst do first?
Which of the following definitions best describes the concept of log co-relation?
Which of the following would best explain why a security analyst is running daily vulnerability scans on all corporate endpoints?
A company must ensure sensitive data at rest is rendered unreadable. Which of the following will the company most likely use?
A company discovers suspicious transactions that were entered into the company's database and attached to a user account that was created as a trap for malicious activity. Which of the following is the user account an example of?
A cyber operations team informs a security analyst about a new tactic malicious actors are using to compromise networks.
SIEM alerts have not yet been configured. Which of the following best describes what the security analyst should do to identify this behavior?
A company is utilizing an offshore team to help support the finance department. The company wants to keep the data secure by keeping it on a company device but does not want to provide equipment to the offshore team. Which of the following should the company implement to meet this requirement?
Which of the following would be the most appropriate way to protect data in transit?
An organization wants to donate its aging network hardware. Which of the following should the organization perform to prevent any network details from leaking?
A systems administrator notices that one of the systems critical for processing customer transactions is running an end-of-life operating system. Which of the following techniques would increase enterprise security?
Which of the following would be the greatest concern for a company that is aware of the consequences of non-compliance with government regulations?
A security team wants WAF policies to be automatically created when applications are deployed. Which concept describes this capability?
An administrator must replace an expired SSL certificate. Which of the following does the administrator need to create the new SSL certificate?
A security report shows that during a two-week test period. 80% of employees unwittingly disclosed their SSO credentials when accessing an external website. The organization purposelycreated the website to simulate a cost-free password complexity test. Which of the following would best help reduce the number of visits to similar websites in the future?
Which of the following is a risk of conducting a vulnerability assessment?
A company’s web filter is configured to scan the URL for strings and deny access when matches are found. Which of the following search strings should an analyst employ to prohibit access to non-encrypted websites?
A company wants to use new Wi-Fi-enabled environmental sensors to automatically collect metrics. Which of the following will the security team most likely do?
During a recent log review, an analyst discovers evidence of successful injection attacks. Which of the following will best address this issue?
A systems administrator needs to provide traveling employees with a tool that will protect company devices regardless of where they are working. Which of the following should the administrator implement?
Which of the following should a security operations center use to improve its incident response procedure?
An employee receives a text message that appears to have been sent by the payroll department and is asking for credential verification. Which of the following social engineering techniques are being attempted? (Choose two.)
An employee recently resigned from a company. The employee was responsible for managing and supporting weekly batch jobs over the past five years. A few weeks after the employee resigned. one of the batch jobs talked and caused a major disruption. Which of the following would work best to prevent this type of incident from reoccurring?
An administrator investigating an incident is concerned about the downtime of a critical server due to a failed drive. Which of the following would the administrator use to estimate the time needed to fix the issue?
Which of the following most accurately describes the order in which a security engineer should implement secure baselines?
A company's antivirus solution is effective in blocking malware but often has false positives. The security team has spent a significant amount of time on investigations but cannot determine a root cause. The company is looking for a heuristic solution. Which of the following should replace the antivirus solution?
An administrator wants to perform a risk assessment without using proprietary company information. Which of the following methods should the administrator use to gather information?
Two companies are in the process of merging. The companies need to decide how to standardize their information security programs. Which of the following would best align the security programs?
Which of the following actions could a security engineer take to ensure workstations and servers are properly monitored for unauthorized changes and software?
Which of the following topics would most likely be included within an organization's SDLC?
While conducting a business continuity tabletop exercise, the security team becomes concerned by potential impacts if a generator fails during failover. Which of the following is the team most likely to consider in regard to risk management activities?
Several customers want an organization to verify its security controls are operating effectively and have requested an independent opinion. Which of the following is the most efficient way to address these requests?
An administrator assists the legal and compliance team with ensuring information about customer transactions is archived for the proper time period. Which of the following data policies is the administrator carrying out?
A company wants to ensure secure remote access to its internal network. The company has only one public IP and would like to avoid making any changes to the current network setup. Which of the following solutions would best accomplish this goal?
A store is setting up wireless access for employees. Management wants to limit the number of access points while ensuring full coverage. Which tool will help determine how many access points are needed?
A company is implementing a vendor's security tool in the cloud. The security director does not want to manage users and passwords specific to this tool but would rather utilize the company's standard user directory. Which of the following should the company implement?
Which of the following is the best way to securely store an encryption key for a data set in a manner that allows multiple entities to access the key when needed?
The help desk receives multiple calls that machines with an outdated OS version are running slowly. Several users are seeing virus detection alerts. Which of the following mitigation techniques should be reviewed first?
Which of the following hardening techniques must be applied on a container image before deploying it to a production environment? (Select two).
Which of the following Is a common, passive reconnaissance technique employed by penetration testers in the early phases of an engagement?
Which of the following is prevented by proper data sanitization?
Which of the following is a type of vulnerability that involves inserting scripts into web-based applications in order to take control of the client's web browser?
The internal audit team determines a software application is no longer in scope for external reporting requirements. Which of the following will confirm management’s perspective that the application is no longer applicable?
Which of the following describes the difference between encryption and hashing?
Which of the following is the best method to reduce the attack surface of an enterprise network?
Which of the following allows a systems administrator to tune permissions for a file?
A systems administrator receives an alert that a company's internal file server is very slow and is only working intermittently. The systems administrator reviews the server management software and finds the following information about the server:
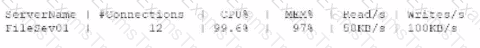
Which of the following indicators most likely triggered this alert?
Which of the following best describe a penetration test that resembles an actual external attach?
Which of the following can best contribute to prioritizing patch applications?
Which of the following types of vulnerabilities is primarily caused by improper use and management of cryptographic certificates?
An organization wants to limit potential impact to its log-in database in the event of a breach. Which of the following options is the security team most likely to recommend?
An administrator is installing an SSL certificate on a new system. During testing, errors indicate that the certificate is not trusted. The administrator has verified with the issuing CA and has validated the private key. Which of the following should the administrator check for next?
A company plans to secure its systems by:
Preventing users from sending sensitive data over corporate email
Restricting access to potentially harmful websites
Which of the following features should the company set up? (Select two).
A company is developing a business continuity strategy and needs to determine how many staff members would be required to sustain the business in the case of a disruption. Which of the following best describes this step?
A software developer wishes to implement an application security technique that will provide assurance of the application's integrity. Which of the following techniques will achieve this?
A security analyst has determined that a security breach would have a financial impact of $15,000 and is expected to occur twice within a three-year period. Which of the following is the ALE for this risk?
A security officer observes that a software development team is not complying with its corporate security policy on encrypting confidential data. Which of the following categories refers to this type of non-compliance?
Various company stakeholders meet to discuss roles and responsibilities in the event of a security breach that would affect offshore offices. Which of the following is this an example of?
A security analyst investigates abnormal outbound traffic from a corporate endpoint. The traffic is encrypted and uses non-standard ports. Which of the following data sources should the analyst use first to confirm whether this traffic is malicious?
Which of the following makes Infrastructure as Code (IaC) a preferred security architecture over traditional infrastructure models?
Which of the following should an organization focus on the most when making decisions about vulnerability prioritization?
An administrator wants to automate an account permissions update for a large number of accounts. Which of the following would best accomplish this task?
An organization is required to provide assurance that its controls are properly designed and operating effectively. Which of the following reports will best achieve the objective?
A business is expanding to a new country and must protect customers from accidental disclosure of specific national identity information. Which of the following should the security engineer update to best meet business requirements?
A vendor salesperson is a personal friend of a company’s Chief Financial Officer (CFO). The company recently made a large purchase from the vendor, which was directly approved by the CFO. Which of the following best describes this situation?
A systems administrator is looking for a low-cost application-hosting solution that is cloud-based. Which of the following meets these requirements?
An administrator discovers that some files on a database server were recently encrypted. The administrator sees from the security logs that the data was last accessed by a domain user. Which of the following best describes the type of attack that occurred?
Visitors to a secured facility are required to check in with a photo ID and enter the facility through an access control vestibule Which of the following but describes this form of security control?
Which of the following would most likely be deployed to obtain and analyze attacker activity and techniques?
Which of the following should an internal auditor check for first when conducting an audit of the organization's risk management program?
The Chief Information Security Officer gives the security community the opportunity to report vulnerabilities on the organization’s public-facing assets. Which of the following does this scenario best describe?
An administrator has identified and fingerprinted specific files that will generate an alert if an attempt is made to email these files outside of the organization. Which of the following best describes the tool the administrator is using?
Which of the following is the best mitigation for a zero-day vulnerability found in mission-critical production servers that must be highly available?
Which of the following elements of digital forensics should a company use If It needs to ensure the integrity of evidence?
Which of the following practices would be best to prevent an insider from introducing malicious code into a company's development process?
Which of the following will harden access to a new database system? (Select two)
Which of the following can be used to compromise a system that is running an RTOS?
Which of the following should a systems administrator use to ensure an easy deployment of resources within the cloud provider?
Which of the following data types relates to data sovereignty?
Which of the following would help ensure a security analyst is able to accurately measure the overall risk to an organization when a new vulnerability is disclosed?
A bank insists all of its vendors must prevent data loss on stolen laptops. Which of the following strategies is the bank requiring?
In which of the following scenarios is tokenization the best privacy technique 10 use?
An organization implemented cloud-managed IP cameras to monitor building entry points and sensitive areas. The service provider enables direct TCP/IP connection to stream live video footage from each camera. The organization wants to ensure this stream is encrypted and authenticated. Which of the following protocols should be implemented to best meet this objective?
A penetration testing report indicated that an organization should implement controls related to database input validation. Which of the following best identifies the type of vulnerability that was likely discovered during the test?
An accounting clerk sent money to an attacker's bank account after receiving fraudulent instructions over the phone to use a new account. Which of the following would most likely prevent this activity in the future?
Which of the following tools can assist with detecting an employee who has accidentally emailed a file containing a customer’s PII?
The number of tickets the help desk has been receiving has increased recently due to numerous false-positive phishing reports. Which of the following would be best to help to reduce the false positives?
A security analyst wants to automate a task that shares data between systems. Which of the following is the best option for the analyst to use?
The private key for a website was stolen, and a new certificate has been issued. Which of the following needs to be updated next?
A security manager created new documentation to use in response to various types of security incidents. Which of the following is the next step the manager should take?
Which of the following provides resilience by hosting critical VMs within different IaaS providers while being maintained by internal application owners?
Which of the following is most likely to be used as a just-in-time reference document within a security operations center?
Which of the following should an organization use to protect its environment from external attacks conducted by an unauthorized hacker?
Which of the following describes a situation where a user is authorized before being authenticated?
A security professional discovers a folder containing an employee's personal information on the enterprise's shared drive. Which of the following best describes the data type the securityprofessional should use to identify organizational policies and standards concerning the storage of employees' personal information?
Which of the following activities is the first stage in the incident response process?
An unknown source has attacked an organization’s network multiple times. The organization has a firewall but no other source of protection against these attacks. Which of the following is the best security item to add?
The security team notices that the Always On VPN solution sometimes fails to connect. This leaves remote users unprotected because they cannot connect to the on-premises web proxy. Which of the following changes will best provide web protection in this scenario?
During a routine audit, an analyst discovers that a department uses software that was not vetted. Which threat is this?
A company receives an alert that a widely used network device vendor has been banned by the government. What will general counsel most likely be concerned with during hardware refresh?
An organization has too many variations of a single operating system and needs to standardize the arrangement prior to pushing the system image to users. Which of the following should the organization implement first?
Which of the following agreements defines response time, escalation, and performance metrics?
A security officer is implementing a security awareness program and is placing security-themed posters around the building and is assigning online user training. Which of the following would the security officer most likely implement?
A security manager wants to reduce the number of steps required to identify and contain basic threats. Which of the following will help achieve this goal?
Which of the following describes an executive team that is meeting in a board room and testing the company's incident response plan?
An IT manager informs the entire help desk staff that only the IT manager and the help desk lead will have access to the administrator console of the help desk software. Which of the following security techniques is the IT manager setting up?
A security analyst needs to improve the company’s authentication policy following a password audit. Which of the following should be included in the policy? (Select two).
A new employee logs in to the email system for the first time and notices a message from human resources about onboarding. The employee hovers over a few of the links within the email and discovers that the links do not correspond to links associated with the company. Which of the following attack vectors is most likely being used?
Which of the following risk management strategies should an enterprise adopt first if a legacy application is critical to business operations and there are preventative controls that are not yet implemented?
A security administrator recently reset local passwords and the following values were recorded in the system:
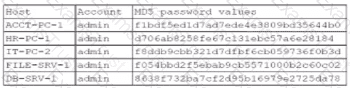
Which of the following in the security administrator most likely protecting against?
A security administrator observed the following in a web server log while investigating an incident:

Which of the following attacks did the security administrator most likely see?
A systems administrator wants to use a technical solution to explicitly define file permissions for the entire team. Which of the following should the administrator implement?
Which of the following is a social engineering attack in which a bad actor impersonates a web URL?
A company recently decided to allow employees to work remotely. The company wants to protect us data without using a VPN. Which of the following technologies should the company Implement?
A systems administrator is auditing all company servers to ensure. They meet the minimum security baseline While auditing a Linux server, the systems administrator observes the /etc/shadow file has permissions beyond the baseline recommendation. Which of the following commands should the systems administrator use to resolve this issue?
A certificate authority needs to post information about expired certificates. Which of the following would accomplish this task?
Which of the following methods will most likely be used to identify legacy systems?
A company plans to secure its systems by:
Preventing users from sending sensitive data over corporate email
Restricting access to potentially harmful websites
Which of the following features should the company set up? (Select two).
An organization recently started hosting a new service that customers access through a web portal. A security engineer needs to add to the existing security devices a new solution to protect this new service. Which of the following is the engineer most likely to deploy?
Which of the following is the most likely benefit of conducting an internal audit?
Which of the following should be used to ensure that a new software release has not been modified before reaching the user?
While troubleshooting a firewall configuration, a technician determines that a “deny any” policy should be added to the bottom of the ACL. The technician updates the policy, but the new policy causes several company servers to become unreachable.
Which of the following actions would prevent this issue?
Which of the following prevents unauthorized modifications to internal processes, assets, and security controls?
Which of the following would best allow a company to prevent access to systems from the Internet?
Which of the following security controls is a company implementing by deploying HIPS? (Select two)
Which of the following should be used to ensure that a device is inaccessible to a network-connected resource?
A security analyst is concerned malicious actors are lurking in an environment but has not received any alerts regarding suspicious activity. Which of the following should the analyst conduct to further investigate the presence of these actors?
A security analyst is prioritizing vulnerability scan results using a risk-based approach. Which of the following is the most efficient resource for the analyst to use?
Which of the following data recovery strategies will result in a quick recovery at low cost?
Which of the following is a common source of unintentional corporate credential leakage in cloud environments?
Which of the following is a vulnerability concern for end-of-life hardware?
A company hired a consultant to perform an offensive security assessment covering penetration testing and social engineering.
Which of the following teams will conduct this assessment activity?
Which of the following examples would be best mitigated by input sanitization?
A company's Chief Information Security Officer (CISO) wants to enhance the capabilities of the incident response team. The CISO directs the incident response team to deploy a tool that rapidlyanalyzes host and network data from potentially compromised systems and forwards the data for further review. Which of the following tools should the incident response team deploy?
A systems administrate wants to implement a backup solution. the solution needs to allow recovery of the entire system, including the operating system, in case of a disaster. Which of the following backup types should the administrator consider?
In which of the following will unencrypted PLC management traffic most likely be found?
During an investigation, a security analyst discovers traffic going out to a command-and-control server. The analyst must find out if any data exfiltration has occurred. Which of the following would best help the analyst determine this?
A government official receives a blank envelope containing photos and a note instructing the official to wire a large sum of money by midnight to prevent the photos from being leaked on the Internet. Which of the following best describes the threat actor's intent?
An employee decides to collect PII data from the company's system for personal use. The employee compresses the data into a single encrypted file before sending the file to their personal email. The security department becomes aware of the attempted misuse and blocks the attachment from leaving the corporate environment. Which of the following types of employee training would most likely reduce the occurrence of this type of issue?
(Select two).
Cadets speaking a foreign language are using company phone numbers to make unsolicited phone calls lo a partner organization. A security analyst validates through phone system logs that the calls are occurring and the numbers are not being spoofed. Which of the following is the most likely explanation?
A software development manager wants to ensure the authenticity of the code created by the company. Which of the following options is the most appropriate?
A growing organization, which hosts an externally accessible application, adds multiple virtual servers to improve application performance and decrease the resource usage on individual servers Which of the following solutions is the organization most likely to employ to further increase performance and availability?
Which of the following outlines the configuration, maintenance, and security roles between a cloud service provider and the customer?
A company implemented an MDM policy 10 mitigate risks after repealed instances of employees losing company-provided mobile phones. In several cases. The lost phones were used maliciously to perform social engineering attacks against other employees. Which of the following MDM features should be configured to best address this issue? (Select two).
A security engineer is implementing FDE for all laptops in an organization. Which of the following are the most important for the engineer to consider as part of the planning process? (Select two).
A financial institution would like to store its customer data m the cloud but still allow the data to be accessed and manipulated while encrypted. Doing so would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution Is not concerned about computational overheads and slow speeds. Which of the following cryptographic techniques would best meet the requirement?
An organization would like to calculate the time needed to resolve a hardware issue with a server. Which of the following risk management processes describes this example?
A security analyst scans a company's public network and discovers a host is running a remote desktop that can be used to access the production network. Which of the following changes should the security analyst recommend?
A malicious insider from the marketing team alters records and transfers company funds to a personal account. Which of the following methods would be the best way to secure company records in the future?
A company makes a change during the appropriate change window, but the unsuccessful change extends beyond the scheduled time and impacts customers. Which of the following would prevent this from reoccurring?
An external security assessment report indicates a high click rate on suspicious emails. The Chief Intelligence Security Officer (CISO) must reduce this behavior. Which of the following should the CISO do first?
A company receives an alert that a network device vendor, which is widely used in the enterprise, has been banned by the government.
Which of the following will the company's general counsel most likely be concerned with during a hardware refresh of these devices?
An organization recently updated its security policy to include the following statement:
Regular expressions are included in source code to remove special characters such as $, |, ;. &, `, and ? from variables set by forms in a web application.
Which of the following best explains the security technique the organization adopted by making this addition to the policy?
A systems administrator is creating a script that would save time and prevent human error when performing account creation for a large number of end users. Which of the following would be a good use case for this task?
Which of the following data states applies to data that is being actively processed by a database server?
The security operations center is researching an event concerning a suspicious IP address A security analyst looks at the following event logs and discovers that a significant portion of the user accounts have experienced faded log-In attempts when authenticating from the same IP address:

Which of the following most likely describes attack that took place?
Which of the following tasks is typically included in the BIA process?
A company wants to reduce the time and expense associated with code deployment. Which of the following technologies should the company utilize?
An MSSP manages firewalls for hundreds of clients. Which of the following tools would be most helpful to create a standard configuration template in order to improve the efficiency of firewall changes?
An incident response specialist must stop a malicious attack from expanding to other parts of an organization. Which of the following should the incident response specialist perform first?
The Cruel Information Security Officer (CISO) asks a security analyst to install an OS update to a production VM that has a 99% uptime SLA. The CISO tells me analyst the installation must be done as quickly as possible. Which of the following courses of action should the security analyst take first?
The Chief Information Security Officer (CISO) at a large company would like to gain an understanding of how the company's security policies compare to the requirements imposed by external regulators. Which of the following should the CISO use?
Which of the following steps in the risk management process involves establishing the scope and potential risks involved with a project?
A client asked a security company to provide a document outlining the project, the cost, and the completion time frame. Which of the following documents should the company provide to the client?
A security team receives reports about high latency and complete network unavailability throughout most of the office building. Flow logs from the campus switches show high traffic on TCP 445. Which of the following is most likely the root cause of this incident?
A new vulnerability enables a type of malware that allows the unauthorized movement of data from a system. Which of the following would detect this behavior?
A new employee can select a particular make and model of an employee workstation from a preapproved list. Which of the following is this an example of?
Which of the following consequences would a retail chain most likely face from customers in the event the retailer is non-compliant with PCI DSS?
Which of the following vulnerabilities is associated with installing software outside of a manufacturer’s approved software repository?
Which of the following involves an attempt to take advantage of database misconfigurations?
Which of the following control types involves restricting IP connectivity to a router's web management interface to protect it from being exploited by a vulnerability?
A systems administrator is redesigning now devices will perform network authentication. The following requirements need to be met:
• An existing Internal certificate must be used.
• Wired and wireless networks must be supported
• Any unapproved device should be Isolated in a quarantine subnet
• Approved devices should be updated before accessing resources
Which of the following would best meet the requirements?
A systems administrator receives a text message from an unknown number claiming to be the Chief Executive Officer of the company. The message states an emergency situation requires a password reset. Which of the following threat vectors is being used?
A forensic engineer determines that the root cause of a compromise is a SQL injection attack. Which of the following should the engineer review to identify the command used by the threat actor?
An enterprise is trying to limit outbound DNS traffic originating from its internal network. Outbound DNS requests will only be allowed from one device with the IP address 10.50.10.25. Which of the following firewall ACLs will accomplish this goal?
An organization disabled unneeded services and placed a firewall in front of a business-critical legacy system. Which of the following best describes the actions taken by the organization?
Which of the following can be best used to discover a company's publicly available breach information?
Which of the following data protection strategies can be used to confirm file integrity?
An administrator is Investigating an incident and discovers several users’ computers were Infected with malware after viewing files mat were shared with them. The administrator discovers no degraded performance in the infected machines and an examination of the log files does not show excessive failed logins. Which of the following attacks Is most likely the cause of the malware?
Which of the following most securely protects data at rest?
A legal department must maintain a backup from all devices that have been shredded and recycled by a third party. Which of the following best describes this requirement?
A systems administrator notices that the research and development department is not using the company VPN when accessing various company-related services and systems. Which of the following scenarios describes this activity?
Which of the following is the best way to improve the confidentiality of remote connections to an enterprise's infrastructure?
A customer of a large company receives a phone call from someone claiming to work for the company and asking for the customer's credit card information. The customer sees the caller ID is the same as the company's main phone number. Which of the following attacks is the customer most likely a target of?
Which of the following teams combines both offensive and defensive testing techniques to protect an organization's critical systems?
An administrator discovers a cross-site scripting vulnerability on a company website. Which of the following will most likely remediate the issue?
A security administrator is implementing encryption on all hard drives in an organization. Which of the following security concepts is the administrator applying?
Which of the following technologies can achieve microsegmentation?
Which of the following data types best describes an AI tool developed by a company to automate the ticketing system under a specific contract?