A SaaS provider has decided to leave an unpatched VM available via a public DMZ port. With which of the following concepts is this technique MOST closely associated?
A new printer was assigned a static IP address within the DHCP scope of a QA subnet. There are 243 workstations on the LAN five servers, and four existing printers on the network. The network administrator configured the network with the following parameters:
192.168.51 -192 168.5 5 static IPs assigned to servers
192.168.5.6 -192 168.5 250 DHCP scope for workstations
192.168.5.251 -192.168.5 254 static IPs assigned to printers
Which of the following should the network administrator perform to minimize the disruption to the users and keep the LAN secure while setting up the new printer?
A network team has reopened multiple outages caused by unauthorized access to the IDF. Which of the following would BEST prevent this issue from reoccurring?
A network engineer is deploying a new PBX for a customer. Although all new phones will be IP-based, the office will still use a few POTS-based phones and a fax line. Which of the following will be needed to connect the fax line?
A user is reporting poor network performance A network technician starts by looking at port statistics on that user's connected switchport. The technician notices there is a high level of collisions on the port. Which of the following is the MOST likely cause?
A customer has asked a technician to upgrade the wireless router to the fastest speed possible. The technician performs a site survey and notices several older devices will not be able to connect to router that operates In the 5GHz range. Which of the following options should the technician suggest to the customer?
A technician is installing and configuring a SOHO network from a DOCSIS compliant ISP. Which of the following requires installation at the customer’s site?
A store owner would like to have secure wireless access available for both equipment and patron use. Which of the following features should be configured to allow different wireless access through the same
equipment?
A technician is connecting multiple switches to create a large network for a new office. The switches are unmanaged Layer 2 switches with multiple connections between each pair. The network is experiencing an extreme amount of latency. Which of the following is MOST likely occurring?
The main purpose of jumbo frames is to increase the:
Which of the following BEST describes a VLAN hopping attack?
A malicious traffic exiting the network on a specific port. The technician is working with the security team to modify the ACL on the company's firewall. Which of the following should be updated immediately?
A coffee shop wants to provide WiFi to Its customers. The shop wishes to support as many devices as possible, so it wants to support all available frequencies. Which of the following 802.11 standards should the coffee shop utilize to meet this requirement?
A network engineer is reviewing a construction proposal for improving the roadways on a campus. The engineer needs to determine if any of the fiber infrastructure between the buildings will need to be relocated. Which of the following will the engineer MOST likely use to make the determination?
A network manager is reviewing recent changes after learning the network health metrics are no longer being recorded. The manager discovers the ACL has been updated to the following:
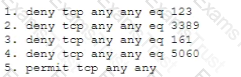
Which of the following lines in the ACL points to the issue?
A company recently implemented a new VoIP solution to replace copper lines that cost too much to maintain. Users have been complaining of the voice quality when they are on phone calls, and management wants the network team to address the concerns. Which of the following should the network team do to improve the performance and security of the VoIP phones?
A network engineer is hardening the security of a remote office. The firewall at this location needs to remain accessible for remote management by technicians. The firewall vendor advises disabling port 443 from WAN-facing access. In addition to disabling port 443, which of the following can the engineer do to MOST effectively balance the remote connectivity and security needs for this site?
Which of the following DNS record types assists with the routing of email?
Which of the following technologies requires a username and password to authenticate to a backbone network?
A network technician is upgrading the software on a switch, but the switch will no longer boot after the upgrade. Which of the following should the network technician have verified before the upgrade?
An engineer is rebooting a remote server after applying monthly patches. The patches are large and may take the server down for up to 20 minutes. The engineer wants to know exactly when the server
comes up. The server's static IP address is 192.10.10.54. Which of the following commands can the engineer issue to accomplish this task?
A wireless administrator needs to implement an authentication method that provides individualized, scalable security for the users of a WLAN where roaming is a regular event. PKI is not available. Which of the following BEST addresses the requirements of this topology?
Which of the following BEST explains why a firewall would be subject to international export controls?
Which of the following do ports allow for in TCP/IP communication?
The Chief Information Officer (CIO) of a large company wants to migrate the ERP system into a cloud provider. Company policy states it is necessary to maintain control over the computer resources that run this software. Which of the following cloud models should be used in this scenario?
Which of the following policies is MOST commonly used for guest captive portals?
A network technician needs to visit a datacenter. To be admitted, the security officer requests to see a driver's license, and then directs the technician to a fingerprint scanner. Which of the following authentication factors is the facility requiring for admittance? (Select TWO).
A company has moved to a building with a large number of WLANs. All clients are 802.11b/g/n capable. Which of the following can be performed to reduce the chance of interference with the nearby APs and maintain or improve the performance of the wireless clients?
To increase security and usability of the wireless network, a back-end RADIUS server is used to authenticate users. Which of the following encryptions methods should be used to accomplish this?
A wireless administrator has configured a secure wireless network that can only be associated to specific domain accounts. This was done to help mitigate any risks associated with the wireless signal propagating outside of the facility. Which of the following has the administrator implemented?
A network technician is attempting to locate a server in a large datacenter that has no connectivity. Which of the following is the BEST reference for the technician to use?
A client moving into a new office wants the IP network set up to accommodate 412 network-connected devices that are all on the same subnet. The subnet needs to be as small as possible. Which of the following subnet masks should be used to achieve the required result?
Which of the following would MOST likely provide continuous power during a short brownout?
A network engineer was alerted to a break in a primary fiber-optic data cable. In which of the following OSI layers was this issue found?
Which of the following allows for connectionless communications?
A security manager asks a technician to install a network device that will provide information about attacks against the network but will not stop them. Which of the following devices is MOST suited for this task?
A network technician is coordinating the upgrade of the company’s WAP firmware with all the remote locations. The company has occasionally experienced errors when transferring large files to some of the remote offices. Which of the following should be used to ensure files arrive without modifications?
When trying to determine why users are unable to access a web-based application that was working the previous day, which of the following should be the FIRST QUESTION NO: to ask to determine the scope of the issue?
A technician is asked to provide centralized SSID management across the entire WAN. The BEST solution would be to:
A technician is required to install a new DOCSIS-based Internet connection. Which of the following medium types does this use?
A network administrator has signed up for service with a new ISP. The administrator was given the IP address of 172.17.10.254/30 to use on the external interface of the Internet-facing router. However, the network administrator cannot reach the Internet using that address. Which of the following is the MOST likely?
A network administrator is securing the wireless network in a multitenant building. The network uses a passphrase for authentication so it is easy to allow guests onto the wireless network, but management would like to prevent users from outside the office space from accessing the network. Which of the following security mechanisms would BEST meet this requirement?
A technician is installing a SOHO router. Which of the following should be performed on every installation and periodically maintained to prevent unauthorized access? (Choose two.)
Which of the following technologies allows network traffic to come into the network on a certain port and go to a destination server with a different port?
Joe, a network technician, has received a report that one of his clients is experiencing an issue connecting to the network. Joe observes two clients are connected to a hub, which is connected to separate wall jacks. Which of the following has MOST likely occurred?
A new technician has been tasked with checking the status of a switchport. The technician needs to find the information quickly without the use of command-line utilities. Which of the following remote management methods would help the technician?
A network technician is assisting a SOHO environment with wireless connection issues. The business uses 802.11n and WPA2 encryption. The on-premises equipment is located toward the back of the building and includes a router, firewall, and WAP. The users at the front of the building are experiencing very slow response times due to distance limitations. Which of the following should be done to remediate the slow speeds of the users?
A technician restored network connectivity on a user’s laptop. After validating full system functionality, which of the following steps should the technician take NEXT?
Which of the following routing conventions is known as a link-state protocol?
A network team at a large company has received funding for a WiFi refresh. One of the requirements in the RFP is the new WLAN infrastructure must provide APs that support multiple streams of information at the same time. For which of the following WiFi features is the network team looking?
A security administrator wants to implement the ability to prevent an authorized user from tailgating into the office building. Which of the following should be implemented?
A network technician needs to subnet the network. The marketing department has 28 devices. Which of the following private IP address spaces should be used to ensure the MINIMUM number of unused IP addresses?
A network technician attempts to limit access to a wireless network by using WPA2 and a pre-shared key; however, employees have been sharing this key with others. Which of the following methods should the technician configure on the wireless access point to ensure only corporate systems can connect using the least amount of effort?
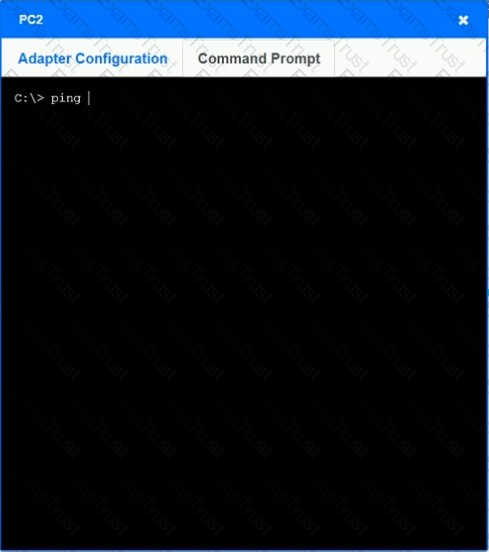
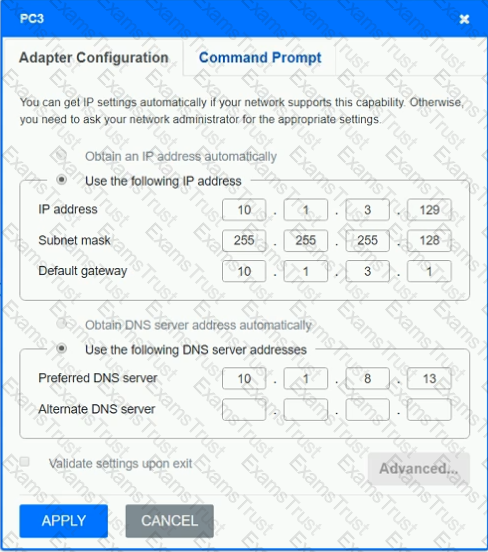
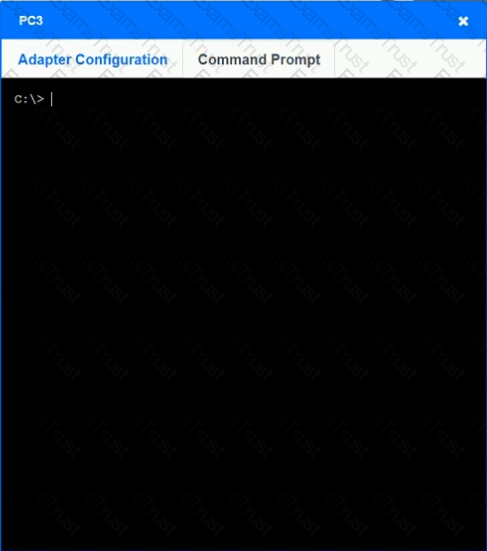
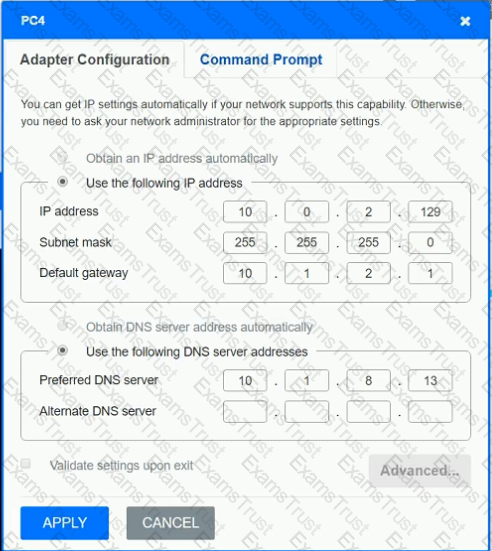
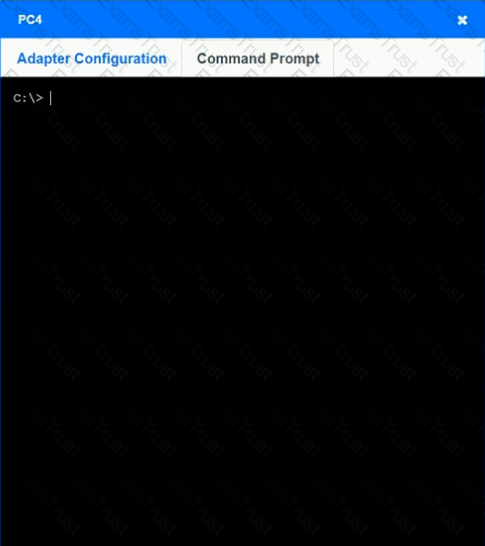
After recent changes to the pictured network, several users are unable to access the servers. Only PC1, PC2, PC3, and PC4 are clickable and will give you access to the command prompt and the adapter configuration tabs.
INSTRUCTIONS
Verify the settings by using the command prompt, after making any system changes.
Next, restore connectivity by making the appropriate changes to the infrastructure.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
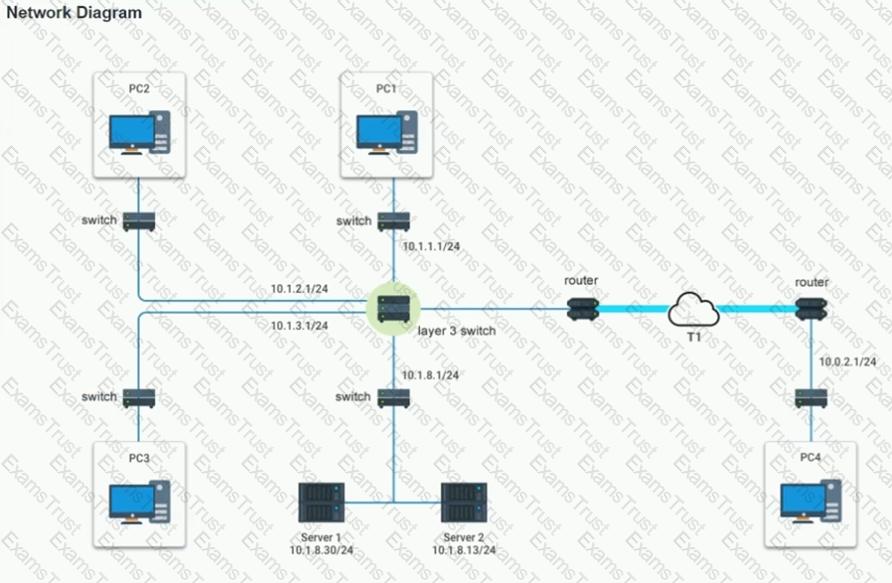
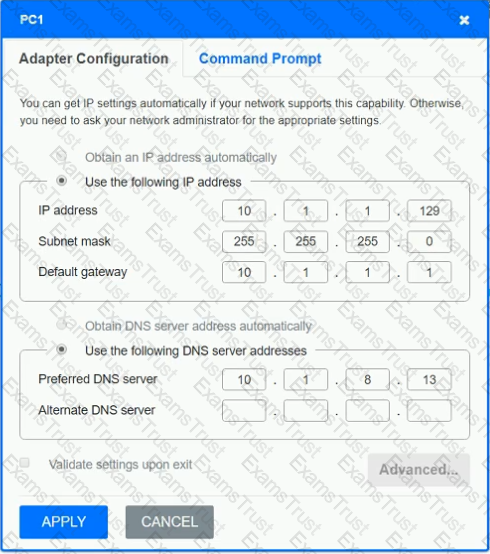

A network engineer wants to change how employees authenticate to the wireless network. Rather than providing a pre-shared key, the engineer wants employees to be able to authenticate with the same unique company user ID and password they use for accessing other services, such as email and document sharing. The engineer also wants to receive daily reports of login attempts on the wireless network. Which of the following should be installed to achieve this goal?
A technician installed a new fiber optic cable to connect two sites. Although there is a link light on the port at each site, the customer reports traffic is dropping intermittently. Which of the following should the technician do NEXT to troubleshoot the issue?
An attacker quickly gains administrative access to a network device. Which of the following MOST likely allowed the attacker to guess the password?
A new DSL circuit was installed to replace the cable service and is not functioning. A network administrator needs to create a cable to connect the circuit. Which of the following connector types should the network administrator use on the cable?
A network administrator is deploying a new switch in an existing IDF. The current switch has only copper Ethernet ports available to use for the trunk ports. Which of the following cable types should the network administrator deploy?
A technician recently ran a new cable over fluorescent lighting. Assuming the technician used the appropriate cables, which of the following connectors should be used to terminate it?
A company has experienced a major security breach. Which of the following should the network administrator reference to determine the next steps?
A user wants to secure a network closet and be able to tell if anyone makes changes in the closet. Which of the following would be the BEST detective physical security devices in this situation? (Choose two.)
A network manager notices several outages have occurred due to modifications that were made without being properly tested. Which of the following will the network manager MOST likely implement to prevent future occurrences?
Which of the following statements about the OSI model is true?
A switch vendor recently released a patch to fix a critical vulnerability found in its switch OS. Which of the following should a network administrator do NEXT according to best practices?
A network technician is supporting a library system that w ants to streamline the checkout of books and media. Which of the following technologies will the technician MOST likely use to facilitate this initiative?
A network technician is reviewing the following output from a router:
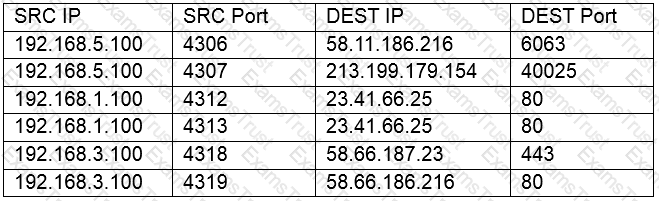
Which of the following is this an example of?
First thing on Monday morning, after a maintenance weekend, the help desk receives many calls that no one can access the Internet. Which of the following types of documentation should the on-call network administrator consult FIRST?
A user claims to have no Internet access but can access local resources. A technician determines the issue is with a configuration because a ping to a working public website shows a response that starts with:
Ping request could not find host
Which of the following is the MOST likely misconfiguration?
A network technician is installing a wireless solution. The solution needs to support new and legacy wireless network clients at the maximum possible speed. Which of the following wireless standards should the technician install?
A small company has decided to use a single virtual appliance to filter spam as well as reverse proxy and filter traffic to its internal web server. Which of the following has the company MOST likely deployed?
A company wishes to allow employees with company-owned mobile devices to connect automatically to the corporate wireless network upon entering the facility. Which of the following would BEST accomplish this objective?
Management is concerned there is excessive traffic on the network. A network technician wants to run a quick port scan to see any systems that have open ports. Which of the following tools should be used to do this?
A network technician Is segmenting network traffic Into various broadcast domains. Which of the following should the network technician utilize?
A network technician is installing and configuring a new router for the sales department. Once the task is complete, which of the following needs to be done to record the change the technician is masking to the company network?
A technician has been asked to install biometric controls at the entrance of a new datacenter. Which of the following would be appropriate authentication methods to meet this requirement? (Choose two.)
A technician discovered a company computer had a virus but was unable to remove it. The technician decided to erase the hard drive to eliminate the threat .Which of the following policies did the technician violate'?
A network technician is setting up the wireless network for a company's new branch office. After doing a site survey, the technician discovers there is a lot of interference from 2.4GHz devices at the location on channel 11. Which of the following would be the BEST channel on which to set up the WAPs?
A network administrator reviews the following command output while troubleshooting a system that is unable to connect to the website:
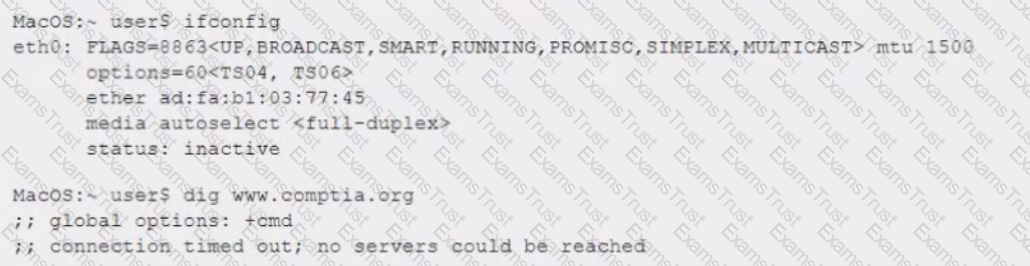
Which of the following is the reason the system cannot connect?
A network technician is configuring network addresses and port numbers for a router ACL to block a peer-to-peer application. Which of the following is the HIGHEST layer of the OSI model at which this router ACL operates?
A technician is troubleshooting a server In the finance office that hosts an internal accounting program. The ticketing desk has received several calls from users reporting that access to the accounting program is degraded, and they are experiencing severe delays, sometimes timing out entirely. The problem has been isolated to the server. Which of the following tools should the technician use on the server to narrow down the issue?
An on-site systems administrator is attempting to log in to several workstations remotely to apply patches. One of the systems on the network is refusing the connection. The administrator is able to log in locally and apply patches. Which of the following should the administrator perform to allow for remote administration?
Which of the following Is an object held within an MIB?
A technician has been assigned to capture packets on a specific switchport. Which of the following switch feature MUST be used to accomplish this?
Management requires remote access to network devices when the ISP is down. Which of the following devices would provide the BEST solution?
A technician needs to add ten additional Ethernet ports to a small office network. A new basic function switch Is added. Hosts connected to the new switch are unable to see any computers on the network other than those connected to the new switch. Which of the following should the technician perform to ensure the hosts on the new switch can communicate with the existing network?
Which of the following ports are used for electronic mail protocols? (Choose three.)
Which of the following protocols are used to configure an email client to receive email? (Select TWO).
When configuring a new switch in a packet-switched network, which of the following helps protect against network loops?
Which of the following types of attacks is characterized by encrypting data and locking out a user from access to certain data within a workstation?
A small team is overloaded with requests for database resources. The Chief Information Officer (CIO) is concerned the company does not have the resources to deploy and manage these additional services efficiently. Which of the following types of cloud services would be the MOST effective?
Which of the following storage network technologies has the HIGHEST throughput?
A development team has been testing a web server on a virtual server to create a web application. Once satisfied, the development team clones the entire virtual server into production. The development team needs to use HTTP, HTTPS, and SSH to connect to the new server. Which of the following should the network administrator do to help secure this new production VM? (Choose two.)
A vendor is installing an Ethernet network in a new hospital wing. The cabling is primarily run above the ceiling grid near air conditioning ducts and sprinkler pipes. Which of the following cable types is required for this installation'?
To increase speed and availability, a high-traffic web application was split into three servers recently and moved behind a load balancer. Which of the following should be configured on the load balancer to allow for a single destination?
According to the troubleshooting methodology, which of the following steps will help a technician gather information about a network problem? (Select TWO).
A company hires some temporary workers. On day one, the temporary employees report they are unable to connect to the network. A network technician uses a packet analysis tool and finds that many clients are continuously sending out requests for an IP address, but many of them are not receiving a response. Which of the following could be the cause of this issue?
A technician is trying to identify the cause of an issue several wireless users are experiencing at an office. The office is in a square-shaped building, with four 802.11b WAPs with omnidirectional antennas located in the
four corners of the building. Users near the center of the building report sporadic issues connecting to resources. The technician checks the signal strength in the middle of the building and determines it is adequate. Which of the following is causing the reported issue?
Users have been experiencing connection timeout issues when using a web-based program. The network technician determines the problem happened due to a TTL setting that was set too low on the firewall. Which of the following BEST enabled the network technician to reach this conclusion?
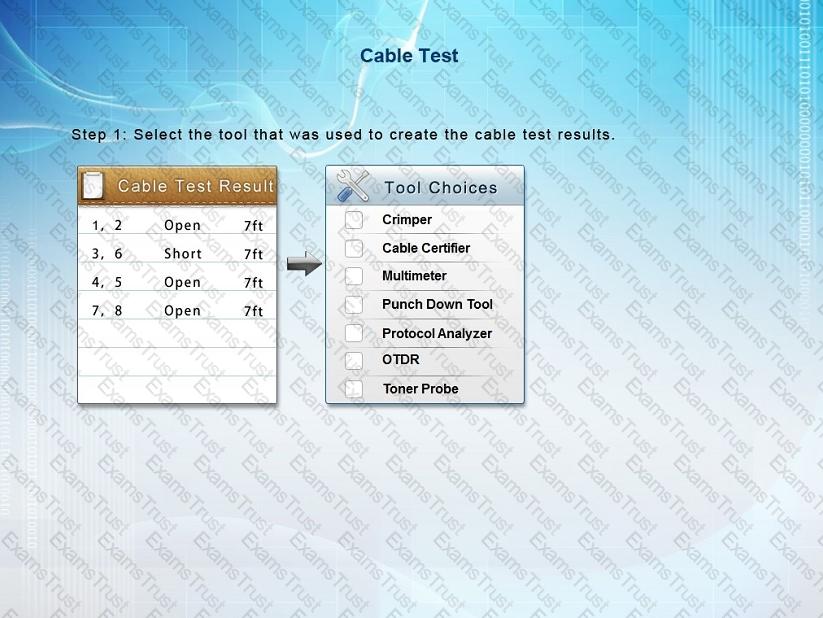
You have been tasked with testing a CAT5e cable. A summary of the test results can be found on the screen.
Step 1: Select the tool that was used to create the cable test results.
Step 2: Interpret the test results and select the option that explains the results. After you are done with your analysis, click the 'Submit Cable Test Analysis' button.
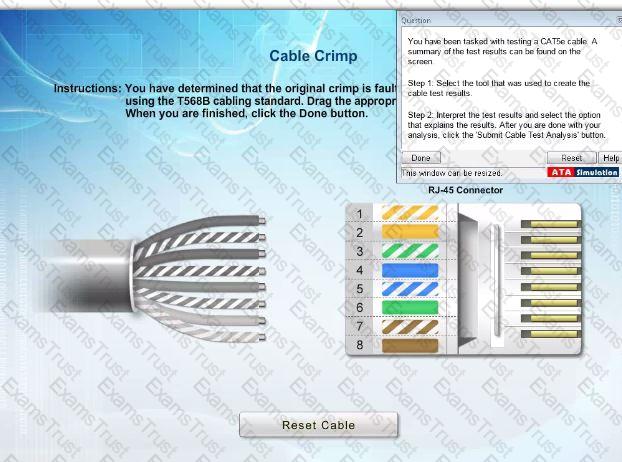
A network technician is performing an initial configuration of a new network switch. Per company policy, the only authorized manner for remotely administering the switch is through a command line. Which of the following protocols should the technician disable to adhere to the company policy?
A network technician has provisioned a new Linux instance in public cloud provider’s IaaS environment. The technician did not install a graphical user interface. The technician wants to connect to the server’s public IP address securely to start a console session. Which of the following remote access methods should the technician use?
A company has decided to allow certain users lo work remotely by opening up a VPN connection through the firewall. The security policy has been updated to allow VPN connections only from certain users and lo specific areas on the network Along with configuring the correct policies on the firewall, which of the following also needs to be configured on users' mobile devices to allow these VPN connections?