Teachers and students at a school currently share the same bandwidth. The Internet performance for the teachers in the classroom is becoming extremely slow. Which of the following is the BEST method to mitigate the issue?
Which of the following would Karen, a technician, do to monitor remote traffic through an access point?
After installing new cabling, Karen, a technician, notices that several computers are connecting to network resources very slowly. Which of the following tools would BEST help in determining if the new cabling is the cause of the problem?
A network administrator opens up the RDP port to access network resources from home. Several months later, the administrator’s account is getting locked out constantly. After closing the port, which of the following should be used to identify the source of the attack?
Sandy, a technician, decides to upgrade a router before leaving for vacation. While away, users begin to report slow performance. Which of the following practices allows other technicians to quickly return the network to normal speeds?
Which of the following is used to verify configuration updates on a firewall?
A new business’ web server has seen a huge spike of legitimate traffic in the last week. The owners want to ensure the site has no problems as the business continues to grow. For Kim, a network administrator, which of the following is the MOST important concern for this company?
The day network administrator is having problems on the network and realizes that the night administrator implemented a new device that is causing broadcast traffic. Which of the following should be implemented to avoid miscommunication between the administrators?
A network administrator wants to see what ports are open on a server. Which of the following commands will show open ports?
Which of the following network performance methods would Lisa, a technician, use with SIP phones?
Karen, an administrator, has created a patch cable. Which of the following tools should she use to check the integrity of the cable?
Which of the following does SNMPv3 BEST provide over previous versions?
A technician has traced a POTS line to a 110 block. Which of the following devices would the technician MOST likely use to see if the line carries a dial tone?
Kim, a network technician, needs to identify the MAC address of a device that is creating broadcast storms on the network. Which of the following tools will provide the needed information?
A network technician is concerned that a user is utilizing a company PC for file sharing and using a large amount of the bandwidth. Which of the following tools can be used to identify the IP and MAC address of the user’s PC?
A technician suspects invalid information in the local DNS cache of a workstation. Which of the following commands can be used to clear this?
Which of the following performance optimization techniques would be MOST beneficial for a network-wide VoIP setup? (Select TWO).
A company has gone through several upgrades on their network but unfortunately have no way of identifying who approved the upgrades. Which of the following should be implemented to track this type of work?
A proxy server would MOST likely be installed to provide which of the following functions? (Select TWO).
Lisa, a network technician, needs to push changes out to network devices and also monitor the devices based on each device’s MIB. Which of the following should she use?
Users report that an internal file server is inaccessible. Of the following commands, which would be the MOST useful in determining network-layer connectivity?
A computer has lost network connectivity. The network technician determines the network cable and the cable drop are both good. Which of the following would the technician use to test the computer’s NIC?
Which of the following devices should Jeff, an administrator, connect to a protocol analyzer in order to collect all of the traffic on a LAN segment?
A public website using round robin DNS is an example of:
During a blizzard, a technician decides to work from home but is unable to connect to the company’s network. Which of the following is MOST likely taking place at the office?
Which of the following can a technician use when a company implements redundant WAN links?
Which of the following wiring distribution types, often found in company closets, is used to connect wiring from individual offices to the main LAN cabling?
A user reports that they are unable to access a new server but are able to access all other network resources. Based on the following firewall rules and network information, which of the following ACL entries is the cause?
User’s IP: 192.168.5.14
Server IP: 192.168.5.17
Firewall rules:
Permit 192.168.5.16/28192.168.5.0/28
Permit 192.168.5.0/24192.168.4.0/24
Permit 192.168.4.0/24192.168.5.0/24
Deny 192.168.5.0/28192.168.5.16/28
Deny 192.168.14.0/24192.168.5.16/28
Deny 192.168.0.0/24192.168.5.0/24
Which of the following ports is used by Telnet?
Zach, a network technician, is unable to remotely manage or ping certain layer 2 switches. To manage those devices remotely, which of the following will MOST likely need to be configured?
Which of the following BEST describes the difference between layer 2 switching and layer 2 routing?
Which of the following is associated with DNS reverse lookup zones?
Which of the following wiring components is used as a central point of termination for all network jacks through a building area?
If a wireless key gets compromised, which of the following would MOST likely prevent an unauthorized device from getting onto the network?
A user wants to send information and ensure that it was not modified during transmission. Which of the following should be implemented?
Which of the following VPN technologies uses IKE and ISAKMP for key exchange?
Which of the following DNS records must be queried to resolve the IPv6 address of a website?
Which of the following DNS records is used to identify a domain’s SMTP server?
Which of the following is a square shaped fiber connector that is slightly smaller than a standard copper network cable connector?
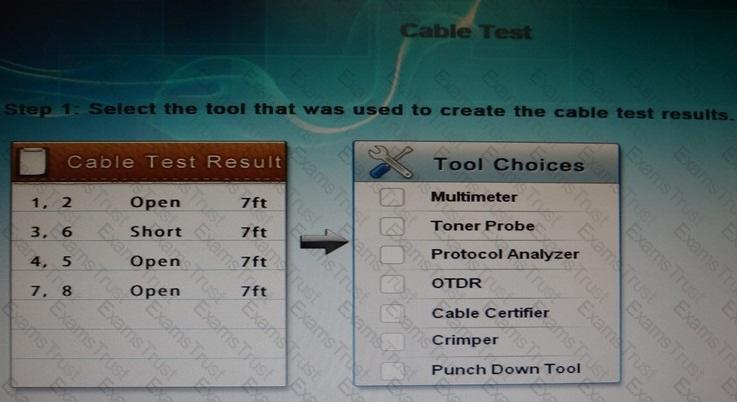
You have been tasked with testing a CAT5 cable. A summary of the test results can be found on the screen.
Step 1: Select the tool that was used to create the cable test results.
Step 2: Interpret the best results and select the options that explains the results.

Which of the following 802.11n features allows for the use of multiple simultaneous frequencies in order to increase usable bandwidth?
A technician needs to test the length of a newly installed cable run because it is believed that it exceeds the maximum specification length. Which of the following tools should be used?
A network administrator is tasked with blocking unwanted spam is being relayed by an internal email server. Which of the following is the FIRST step in preventing spam that is originating from bots on the network?
A MAC address is a part of which of the following OSI model layers?
A network administrator has been assigned the 192.168.2.64/26 network and assigns the following computer’s IP addresses:
192.168.2.70
192.168.2.100
192.168.2.125
192.168.2.130
When the administrator tries to ping the other computers from 192.168.2.130, an ECHO REPLY is not received. Which of the following must the network administrator do?
Which of the following wireless parameters may need to be modified when a new cordless telephone is installed?
A technician is installing an 802.11n network. The technician is using a laptop that can connect at a maximum speed of 11 Mbps. The technician has configured the 802.11n network correctly but thinks it could be the type of WLAN card used on the laptop. Which of the following wireless standards is the WLAN card MOST likely using?
Zach, a technician, is installing an 802.11n network. Which of the following should he disable to stop broadcasting the network name?
Stateful packet inspection is a security technology used by which of the following devices?
Ann, a home user, wishes to confine a wireless network to devices ONLY inside of her house. Which of the following will accomplish this?
Which of the following tools could attempt to detect operating system vulnerabilities?
Which of the following network access methods is the MOST secure?
A company has only three laptops that connect to their wireless network. The company is currently using WEP encryption on their wireless network. They have noticed unauthorized connections on their WAP and want to secure their wireless connection to prevent this. Which of the following security measures would BEST secure their wireless network? (Select TWO).
An administrator configuring remote access opens ports 500/UDP and 10000/UDP on the firewall. Which of the following services are MOST likely being allowed? (Select TWO).
Sandy, a home user, wishes to confine a wireless network to devices ONLY inside of her house. Which of the following will accomplish this?
A firewall that examines all the incoming traffic and decides if the traffic is going to be allowed though or dumped is a example of which of the following?
Which of the following security protocols would BEST protect a connection to a remote email server and ensure full integrity of all transmitted email communication?
Which of the following is the MOST secure way to prevent malicious changes to a firewall?
Jeff, a company executive, has noticed that a wireless network signal from the company’s WAP can be seen in the company’s parking lot. Jeff is very worried that this is a potential security threat. Which of the following can be done to eliminate this threat?
Which of the following would be the BEST solution for an IDS to monitor known attacks?
Which of the following protocols works at the LOWEST layer of the OSI model?
Which of the following solutions will detect and disable a rogue access point?
A user is unable to connect to a remote computer using RDP. The technician checks the firewall rules and notes that there is no rule that blocks RDP. Which of the following features of the firewall is responsible for blocking RDP?
Which of the following uses SSL encryption?
Joe, a network technician, is implementing a wireless network and needs to support legacy devices. He has selected to use WPA mixed mode. WPA mixed mode is normally implemented with which of the following encryption factors? (Select TWO).
An administrator determines that an attack is taking place on the email server from a group of users on the same ISP. Which of the following is the BEST way to mitigate an attack on the network?
Which of the following would be used to place extranet servers in a separate subnet for security purposes?
Which of the following security devices is used in providing packet and MAC address filtering services for the network?
A technician needs to restrict access to a SOHO wireless network to specific devices. Which of the following would MOST likely be used with minimal client configuration?
Honeypots and honeynets are different in which of the following ways?
Kim, a user, reports that the web browser is indicating the site certificate is not trusted. Which of the following attacks may be in progress?
An organization only has a single public IP address and needs to host a website for its customers. Which of the following services is required on the network firewall to ensure connectivity?
Which of the following DNS records would a web browser access to determine the IP address of an Internet web page?
Lisa, a network technician, is attempting to map a FQDN to an internal server at the address of 10.0.0.15 without NAT/PAT. Which of the following is the reason this will ultimately not work?
A technician has narrowed down the cause of a problem to two possible sources. Which of the following should the technician do NEXT?
Which of the following allows for groups of ports on the same switch to operate as a part of different segmented networks?
A home user states during a basement remodel, one of the workers cut the network cable that goes from the modem to the WAP and nothing else has changed. According to the network troubleshooting methodology, which of the following is the NEXT step?
A forward lookup zone converts which of the following?
Which of the following OSI layers BEST describes where an HTTP proxy operates?
Which of the following DNS record types provides the hostname to IP address mapping?
Which of the following ports would Zach, a technician, need to open on a firewall to allow SSH on the default port?
Which IEEE protocol is used with VLAN technology?
Which protocol is represented by the packet capture below?
UDP 0.0.0.0:68 -> 255.255.255.255:67
Which of the following has the LEAST amount of collisions in a domain?
After Kurt, a technician, has established a plan of action to resolve the problem, which of the following steps should he perform NEXT?
A web server that provides shopping cart capabilities for external end users will likely function with which of the following protocols?
Jeff, a user, can no longer access the accounting file share, but others are still able to access the share. Which of the following would be the FIRST step in troubleshooting the issue?
Which of the following services are affected by closing the default ports of 80 and 21 via ACL on a company router?
Which of the following is used to embed the MAC address of an Ethernet interface in a corresponding IPv6 address?
Data arranged into packets would be on which of the following layers of the OSI model?
At which layer of the OSI model do MAC addresses operate?
After the technician has established a theory of probable cause of a user reported problem, which of the following should the technician do NEXT in the troubleshooting process?
Which of the following services do TCP connections provide to application layer protocols? (Select TWO).
Which of the following should be used when throughput to the destination network is a priority?
After a new firewall is installed, users report that they do not have connectivity to the Internet. The output of the ipconfig command shows an IP address of 169.254.0.101. Which of the following ports would need to be opened on the firewall to allow the users to obtain an IP address? (Select TWO).
Multiple networked devices running on the same physical hardware that provide central access to applications and files, where each device runs as a piece of software are known as:
A user would like to connect two laptops together and transfer files via the Ethernet ports. Which of the following should MOST likely be provided to the user to accomplish this?
The ISP needs to terminate the WAN connection. The connection should be located in the network server room where the company LAN equipment resides. Which of the following identifies the location?
Which of the following WAN technologies utilizes an optical SONET carrier and has a maximum bandwidth of 155.54Mbps?
Which of the following connectors is used for coaxial copper cable?
802.11n can operate at which of the following frequencies? (Select TWO).
The network technician is troubleshooting a connectivity issue on a CAT5 cable with a wire map and notices that only pins 1, 3, and 6 are mapping correctly. Which of the following pins are open and keeping traffic from flowing correctly?
Which of the following technologies can cause interference for 802.11g?
Which of the following defines the pinout of an 8P8C eight pin modular jack for a CAT6a cable?
In a small office environment, one computer is set up to provide Internet access to three other computers that are not interconnected. This is an example of which of the following topology types?
Joe, a technician, is troubleshooting connectivity issues with a new data circuit. Joe verifies that the ST fiber jumper is good. Which of the following is the problem?
Which of the following colors represents the outer leads on a connector head of a 568B patch cable? (Select TWO).
Jeff, an administrator, is using a punch-down tool to connect a cable. To which of the following is Jeff MOST likely connecting?
Which of the following connectors push and twist-on?
Kim, a technician, is connecting a new desktop computer to a switch. She was only able to locate one cable in the office for the installation. The wires at each end are color coded as follows:
End A: orange-white, orange, green-white, blue, blue-white, green, brown-white, brown
End B: green-white, green, orange-white, blue, blue-white, orange, brown-white, brown
Which of the following should Kim do to complete the installation?
Which of the following cable types is required to run through an air duct?
Which of the following is a packet switching WAN technology?
Which of the following 802.3 classifications has a MAXIMUM segment distance of 984 feet (300 meters)?
A technician has been dispatched to investigate connectivity problems of a recently renovated office. The technician has found that the cubicles were wired so that the network cables were run inside the conduit with the electrical cabling. Which of the following would MOST likely resolve the connectivity issue?
Which of the following is the MAXIMUM distance a single 1000BaseT segment can cover?
In the 2.4GHz range, which of the following channel combinations are non-overlapping?
Which of the following standards can operate at 40MHz channel spacing?
When examining a suspected faulty copper network cable, Kim, the administrator, notices that some of the pairs are untwisted too much. This is MOST likely causing which of the following?
Ann, a technician, is installing network cables for an office building. Some of the cables are not showing active on the switch even when moved to different ports. Which of the following is MOST likely the cause?
Lisa, an administrator, has been tasked with running cables from one office to another neighboring office by running cables over the light fixtures in the ceiling that connects them. To prevent interference, which of the following cable types should Lisa use?