A network administrator suspects a broadcast storm is causing performance issues on the network. Which of the following would be used to verify this situation?
A network administrator has just been notified about the loss of Internet connectivity. Another technician had just performed non-scheduled maintenance and mentioned that some cabling may have been moved. Which of the following MOST likely caused the loss of Internet connectivity?
A technician is troubleshooting a wireless network that was setup previously. The network is a hybrid of 802.11g and 802.11n WAPs. Users are not able to view or connect to the 802.11n WAPs. Which of the following is MOST likely the cause?
A network administrator is adding 24 - 802.3af class 2 VoIP phones and needs to purchase a single PoE switch to power the phones. Which of the following is the MINIMUM PoE dedicated wattage the switch supports to power all of the phones at full power?
A user cannot access the LAN after working successfully most of the day. Which of the following should the network administrator check FIRST?
When a patch cable is plugged into a switch, all port activity indicators turn on and users instantly lose network connectivity. Which of the following is the MOST likely diagnosis?
A technician has been dispatched to investigate an issue where several users in the same aisle have stated they have had no network connection for over an hour. When the technician gets there, the network seems to be up and running. Which of the following should the technician do NEXT?
Which of the following can be used to limit wireless network access to a single computer?
Which of the following standards can operate at either 20MHz or 40MHz channel spacing?
A user is on a network with two upstream connections to the Internet and is experiencing intermittent issues while connecting to websites. Some websites are available but others are not. Which of the following is the MOST likely cause of the condition?
A user calls the helpdesk to report not being able to access network resources over the company’s Wi-Fi connection. During information gathering, the user mentions that the wireless network their computer is signed into is not the same name as it had been previously. Which of the following is the underlying cause?
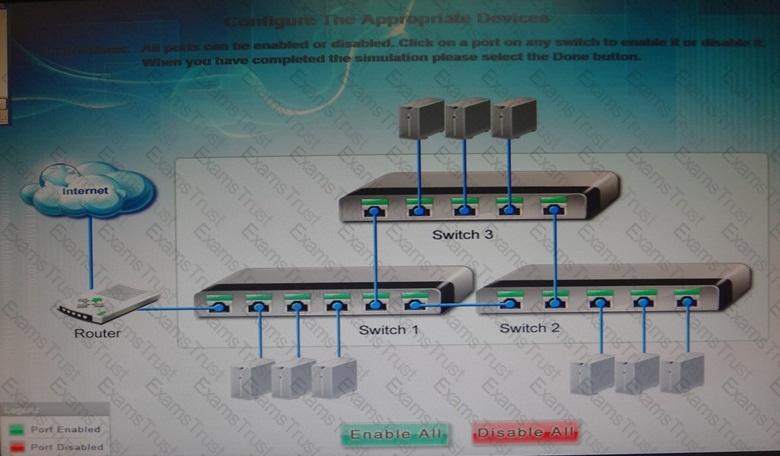
Workstations are unable to access the internet after a recent power outage. Configure the appropriate devices to ensure All workstations have internet connectivity.
A technician working for a company with a wireless network named WirelessA notices a second wireless network named WirelessB. WirelessB is MOST likely a:
A Linux-based workstation is unable to connect to an IP printer on the same network segment. The printer IP address settings have been verified. How would a network technician verify IP address settings on the Linux-based workstation?
A company has recently allowed its employees to telecommute two days a week. The employees MUST have a minimum of 1Mbps non-shared connection to the Internet. Which of the following MUST the employees have at their home in order to connect to the Internet?
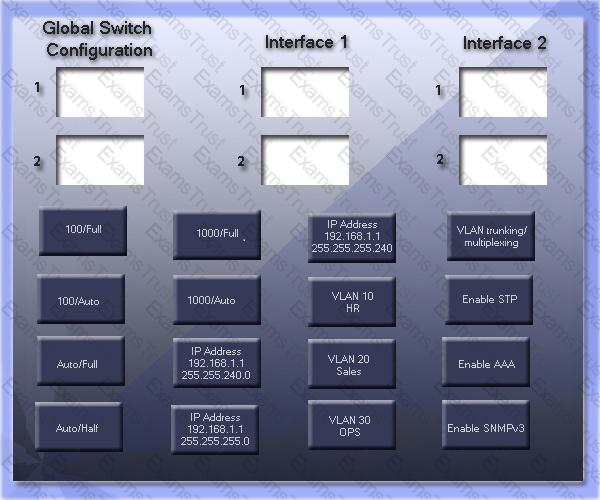
GigSwitch1 is currently configured with a speed of 100 and Duplex is set to Auto on all interfaces. Interface 2 will be connected to GigSwitch2 which is used for all departments. Interface 1 will be used for HR traffic only.
GigSwitch1 needs to be configured with the following parameters:
Configure the necessary protocol to prevent switching loops
Configure GigSwitch1 with a /24 IP address for management
Traffic across Interface 1 needs to be forced to accept and receive up to 100Mbps data at the same time
Traffic across Interface 2 needs to be forced to use Gigabit speeds and maximum performance
Drag and drop the appropriate configurations to their corresponding requirements. All placeholders must be filled. Not all configurations will be used.
A technician wants to configure multiple switches to support all of the corporate VLANs. Which of the following will allow configuration of the switches and have the information propagate automatically to the other switches?
A small business owner is setting up a SOHO office. The business owner needs one device that will allow for Internet access, trunk VLANs, translate multiple private IP addresses into public IP addresses, and filter packets. Which of the following network devices will allow for all functions?
Which of the following performance optimization techniques would be MOST beneficial for a network-wide VoIP setup? (Select TWO).
A client has just leased a new office space in a busy commercial building and would like to install a wireless network. Several other tenants are on the same floor. Multiple wireless networks are present in the building. Which of the following can be changed on the client’s wireless network to help ensure that interference from other wireless networks is at a minimum?
A network technician has just upgraded a switch. The new switch’s IP range and subnet mask correctly match other network devices. The technician cannot ping any device outside of the switch’s own IP subnet. The previous switch worked correctly with the same settings. Which of the following is MOST likely the problem?
A company has installed a wireless network for visitors to use. They wish to give the visitors easy access to that network. Based on the configurations below, which of the following should the administrator change?
Access Point 1Access Point 2
802.11g802.11b
Encryption: WPA2Encryption: WEP
Channel: 1Channel: 7
SSID. CompanyWiFiSSID. Visitor
A technician is configuring a new DSL router. The technician can communicate with the LAN, but not the WAN. Which of the following is the MOST likely cause?
A network administrator needs to implement a monitoring tool and be able to send log information to a server and receive log information from other clients. Which of the following should be implemented? (Select TWO).
A network administrator is replacing old switches to support a VoIP deployment. Based on this parameter, which of the following is MOST likely to be implemented on these new switches?
Which of the following cable types use pins 1 and 2 to transmit and 3 and 6 to receive?
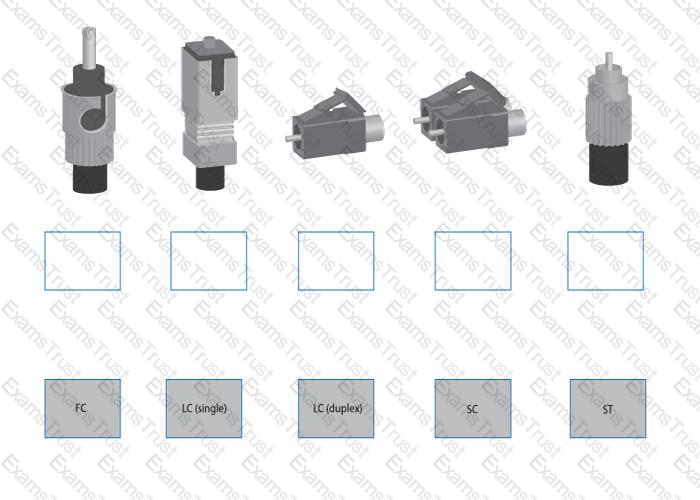
Drag and drop the fiber cable connection types to the appropriate image.
A consultant has been hired to wire a simple small office of ten computers to a layer 2 Ethernet 100BaseT switch. Which of the following cabling will be needed for the installation?
A technician is tasked with rewiring a CAT5e SOHO network with 10 existing computers. The users are currently running at 100 Mbps and would like to be upgraded to 1000 Mbps. Which of the following should the technician do FIRST?
A Chief Executive Officer (CEO) decided that only a limited number of authorized company workstations will be able to connect to the Internet. Which of the following would BEST accomplish this goal?
Which of the following network topologies is MOST likely used in remote access VPN?
Which of the following wiring distribution is used to connect wiring from equipment inside a company to carrier cabling outside a building?
A company recently added an addition to their office building. A technician runs new plenum network cables from the switch on one side of the company's gymnasium 80 meters (262 ft.) to the new offices on the other side, draping the wires across the light fixtures. Users working out of the new offices in the addition complain of intermittent network connectivity. Which of the following is MOST likely the cause of the connectivity issue?
Which of the following types of technologies should be used to provide a MAXIMUM 10 GB speed to a multi-mode fiber network?
An 802.11a wireless network is functioning at which of the following frequencies?
Which of the following is used to allow multiple sources on a single optical cable?
A technician is not getting a link light on two switches connected by a fiber cable. After the cable tests good, which of the following should the technician check NEXT?
Which of the following technologies allows multiple staff members to connect back to a centralized office?
A technician is troubleshooting a problem where data packets are being corrupted. Which of the following connectivity problems should the technician check?
Which of the following fiber types is MOST often used indoors?
Which of the following is a requirement for bridging with 802.11a?
Which of the following wireless standards has a maximum rate of less than 50 Mbps?
The network administrator just upgraded all of the WAPs to new ones with 2.4 GHz b/g/n support. The new WAPs reuse the same location and channel as the previous one and with no new external interference detected. However, performance issues are now occurring that did not exist before. Which of the following would correct the issue?
A VoIP system running over a wireless network link is continually being reported as choppy. Which of the following is the cause of this issue?
Which of the following is MOST commonly used with a fiber-optic network backbone?
Which of the following do 802.11 networks use to handle packet collisions from multiple nodes?
Which of the following WAN technologies has the highest latency?
Which of the following cable types is required to run through an air duct?
Which of the following 802.3 classifications has a MAXIMUM segment distance of 984 feet (300 meters)?
Which of the following 802.11 standards can operate at both 2.4Ghz and 5.0Ghz?
Which of the following is a public class C IP address?
Layers 5, 6, and 7 from the OSI model correspond to which of the following layers of the TCP/IP model?
Which of the following is an example of a Class C address?
Multiple servers’ IP addresses fall within the DHCP scope assigned by the administrator. Which of the following should be implemented to ensure these static IP addresses are not assigned to workstations?
Which of the following can be configured on a managed network switch to send real time alerts to a technician?
Which of the following is an advantage of dynamic routing?
A proxy server would MOST likely be installed to provide which of the following functions? (Select TWO).
A MAC address is a part of which of the following OSI model layers?
Which of the following would the telecommunications carrier use to segregate customer traffic over long fiber links?
Two workstations are unable to communicate on the network despite having known good cables. When one device is unplugged from the network the other device functions properly. Which of the following could be the cause of this failure?
A technician has installed a group of layer 2 switches with multiple VLANs. The VLANs cannot talk to each other. Which of the following network devices could correct this problem? (Select TWO).
Which of the following protocols is the BEST choice for retrieving email on multiple devices?
A technician finds that the network card is no longer functioning. At which of the following OSI layers is the problem occurring?
192.168.0.7/8 notation denotes which of the following IPv4 subnet masks?
Which of the following TCP/IP model layers does the OSI model Data Link layer map to?
A company pays a third-party vendor a monthly fee to connect to offsite servers and desktops. Users connect to the desktops via RDP, and administrators connect to the servers via VPN. Servers and desktops are hardware-based. Which of the following is the third-party providing?
Which of the following is described by the MAC address FF:FF:FF:FF:FF:FF?
Users in several departments are reporting connectivity problems. The technician examines the computer and finds the following settings. The IP address is 10.0.1.0 with a subnet mask of 255.255.252.0. The default gateway is 10.0.1.1 and the DNS server is 10.0.0.15. A user can connect to the internet but not servers on other internal subnets. The technician is not able to connect with a server with an IP of 10.0.2.25. Which of the following is MOST likely the problem?
Standards such as JPEG and ASCII operate at which of the following OSI model layers?
At which layer of the OSI and TCP/IP model would HTTP and FTP be found?
Which of the following is a Class A IP address?
Which of the following is a link state routing protocol?
Which of the following protocols is used to transfer files over the Internet?
The Network Interface Layer of the TCP/IP model corresponds to which of the following layers of the OSI model? (Select TWO).
Which of the following provides secure access to a network device?
Which of the following are authentication methods that can use AAA authentication? (Select TWO).
Which of the following remote access types requires a certificate for connectivity?
A network administrator is responding to a statement of direction made by senior management to implement network protection that will inspect packets as they enter the network. Which of the following technologies would be used?
An attack used to find unencrypted information in network traffic is called:
A network administrator is implementing an IPS on VLAN 1 and wants the IPS to learn what to prevent on its own. Which of the following would MOST likely be installed?
A network technician has configured a new firewall with a rule to deny UDP traffic. Users have reported that they are unable to access Internet websites. The technician verifies this using the IP address of a popular website. Which of the following is the MOST likely cause of the error?
A network technician is configuring a new firewall for placement into an existing network infrastructure. The existing network is connected to the Internet by a broadband connection. Which of the following represents the BEST location for the new firewall?
Joe, a network technician, is implementing a wireless network and needs to support legacy devices. He has selected to use WPA mixed mode. WPA mixed mode is normally implemented with which of the following encryption factors? (Select TWO).
Users at a remote site are unable to establish a VPN to the main office. At which of the following layers of the OSI model does the problem MOST likely reside?
Which of the following features will a firewall MOST likely use to detect and prevent malicious traffic on the network?
A technician has configured a router to authenticate VPN users to an LDAP server on the network. In order to allow the authentication service, both UDP and TCP ports needed to be allowed on the router. Which of the following services was MOST likely used?
Several users are reporting connectivity issues with their laptops. Upon further investigation, the network technician identifies that their laptops have been attacked from a specific IP address outside of the network. Which of the following would need to be configured to prevent any further attacks from that IP address?
Many of the corporate users work from a coffee shop during their lunch breaks. The coffee shop only has an open wireless network. Which of the following should the administrator recommend to users to secure their wireless communications at the coffee shop?
Which of the following security methods is used to attract users attempting to gain unauthorized access to various systems within a single network?
A network administrator is implementing a wireless honeypot to detect wireless breach attempts. The honeypot must implement weak encryption to lure malicious users into easily breaking into the network. Which of the following should the network administrator implement on the WAP?
A company wants to secure its WAPs from unauthorized access. Which of the following is the MOST secure wireless encryption method?
An administrator would like to search for network vulnerabilities on servers, routers, and embedded appliances. Which of the following tools would MOST likely accomplish this?
A vendor releases an emergency patch that fixes an exploit on their network devices. The network administrator needs to quickly identify the scope of the impact to the network. Which of the following should have been implemented?
An organization only has a single public IP address and needs to host a website for its customers. Which of the following services is required on the network firewall to ensure connectivity?
A network technician has a RADIUS server IP address that must be included as part of the security settings for a WAP. Which of the following encryption types should the technician select?
A small company is looking to install a wireless network to enable its relatively old fleet of laptops to have limited internet access internally. The technician on the project knows that the units do not support modern encryption standards. If backwards compatibility is the greatest concern, which of the following is the MOST appropriate wireless security type to choose?
A company would like their technicians to be able to connect to employee desktops remotely via RDP. Which of the following default port numbers need to be opened on the firewall to support this?
Which of the following protocols can be implemented to provide encryption during transmission between email gateways?
Which of the following protocols is used to provide secure authentication and encryption over non-secure networks?
A network administrator has been tasked to deploy a new WAP in the lobby where there is no power outlet. Which of the following options would allow the network administrator to ensure the WAP is deployed correctly?
Users are reporting a large decrease in network performance. After further investigation, the network administrator notices large amounts of traffic coming from a specific IP address. The network administrator needs to identify the payload of the network traffic. Which of the following could be used to collect that information?
A company has gone through several upgrades on their network but unfortunately have no way of identifying who approved the upgrades. Which of the following should be implemented to track this type of work?
A network technician has been asked to look into a report from the IDS to determine why traffic is being sent from an internal FTP server to an external website. Which of the following tools can be used to inspect this traffic?
A technician sets up a network with multiple WAN connections, backup power sources, multiple firewalls, and a mesh configuration for network switching. All of the software and hardware has fault detection designed to provide a system with minimal down time. Which of the following is the BEST example of this optimization method?
A company needs to find a way to best route latency-sensitive traffic appropriately on an already congested network. Which of the following would be BEST suited for this purpose?
A user is having difficulty connecting a laptop to the company’s network via a wireless connection. The user can connect to the network via a wired NIC. The technician suspects the laptop’s wireless NIC has failed. The technician performs hardware diagnostics on the wireless NIC and discovers the hardware is working fine. Which of the following network troubleshooting methodology steps should the technician do NEXT?
Which of the following network performance optimization methods allows for frequently accessed sites to be housed locally, thereby reducing bandwidth requirements?
A new technician has been tasked with implementing a QoS policy for the Network. The technician decides it would be best to monitor the information traversing the network to gain statistical information on ports and protocols utilized. Which of the following tools should the technician use to complete this objective QUICKEST?
A technician suspects invalid information in the local DNS cache of a workstation. Which of the following commands can be used to clear this?
In order to discover the currently unknown IP address of the next-hop router, a network administrator would begin by using which of the following tools?
An IP camera has a failed PoE NIC. This is the third time in months that a PoE NIC has failed on this device. The technician suspects a possible power issue. Which of the following should be used to test the theory?
Which of the following should be installed to prevent inappropriate websites from being viewed?
Which of the following commands would be used to identify how many hops a data packet makes before reaching its final destination?
A technician needs to verify the time of a power outage. Which of the following may be used to determine this information?
A large company has experienced Internet slowdowns as users have increased their use of the Internet. Which of the following can the Network Administrator use to determine the amount of bandwidth used by type of application?
It has been suspected that one of the users is using the network inappropriately. As a preventive measure HR has authorized the IT department to enable port mirroring on the user’s network port. Which of the following devices would be used to monitor the network activity?
A technician has noticed that the RJ-45 connector on the end of a user’s patch cable was stripped too far back from the connector allowing for cross talk. Which of the following tools would a technician use to attach a new connector to eliminate this issue?
Which of the following switches is used with ARP to display the cache entry for a specific IP address?
An application is using port 2000 on a PC. Which of the following could an administrator do to determine what software is listening on that port?
Which of the following devices can be utilized to monitor and block websites accessible by a company?
A content filter is MOST likely installed on which of the following servers?
A technician is having trouble identifying a computer on a network. The technician has the IP address of the computer, but needs to find the hostname of the computer. Which of the following commands should the technician use?
A public website using round robin DNS is an example of:
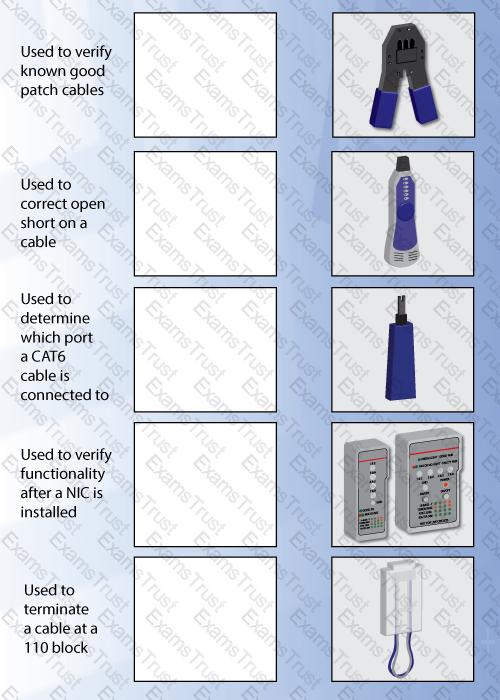
Drag and drop each networking tool to the MOST appropriate descriptor. Each tool may only be used once.