Which of the following database structures is a type of NoSQL database?
Which of the following is a result of an on-path attack on a system?
Which of the following commands is part of DDL?
Which of the following resources is the best way to lock rows in SQL Server?
(A business analyst queries the same few tables every quarter and does not want to write new SQL code every time. Which of the following would best support the business analyst’s needs and allow the database administrator to optimize disk space?)
Which of the following firewall types allows an administrator to control traffic and make decisions based on factors such as connection information and data flow communications?
(Before installing a new database instance for an organization, a DBA needs to verify the amount of space, the hardware, and the network resources. Which of the following best describes this process?)
A server administrator wants to analyze a database server's disk throughput. Which of the following should the administrator measure?
(An analyst in the United States configured a database server so it could be accessed remotely by users in Brazil and Canada. Users in Brazil can connect to the server, but users in Canada cannot connect to the server. Which of the following is the reason for the issue?)
A database administrator needs to ensure continuous availability of a database in case the server fails. Which of the following should the administrator implement to ensure high availability of the database?
(Five minutes after a power failure occurred in a data center, a CO₂ system was automatically triggered. Which of the following caused the CO₂ system to start?)
(A database system crashed during a routine migration process. Which of the following should the systems administrator refer to for guidance in this situation?)
Which of the following statements contains an error?
A database administrator needs to aggregate data from multiple tables in a way that does not impact the original tables, and then provide this information to a department. Which of the following is the best way for the administrator to accomplish this task?
Which of the following describes a scenario in which a database administrator would use a relational database rather than a non-relational database?
Which of the following types of RAID, if configured with the same number and type of disks, would provide the best write performance?
(A healthcare company relies on contact forms and surveys on its website to properly communicate with patients. To which of the following attacks is the company’s data most vulnerable?)
Which of the following concepts applies to situations that require court files to be scanned for permanent reference and original documents be stored for ten years before they can be discarded?
(Which of the following best describes the function of PowerShell in a database environment?)
A database professional is considering denormalizing a database. Which of the following documents should be used to analyze the database's structure?
(Which of the following statements is TRUNCATE an example of?)
Which of the following tools is used for natively running a Linux system in Windows?
(New users at a company are reporting that the system is not accepting new credentials when the users are asked to change the credentials for the first time. Which of the following is the reason the credentials are being rejected?)
A company needs information about the performance of users in the sales department. Which of the following commands should a database administrator use for this task?
Which of the following is an attack in which an attacker hopes to profit from locking the database software?
Given the following customer table:
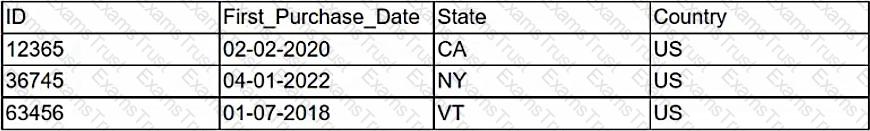
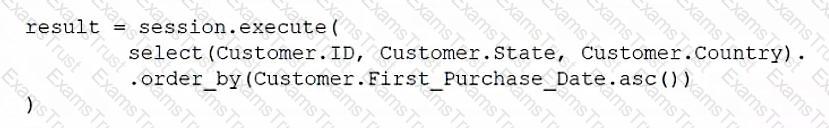
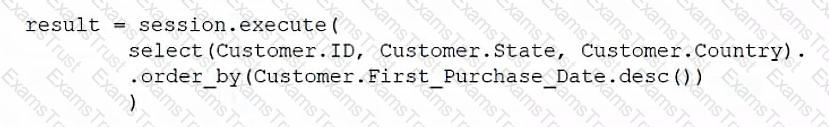
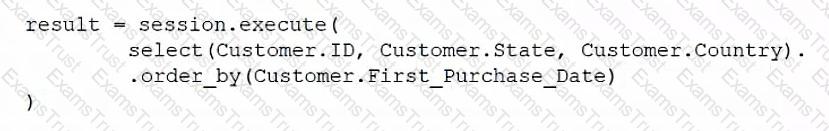
Which of the following ORM snippets would return the ID, state, and country of all customers with the newest customers appearing first?
A)
B)
C)

D)
(Which of the following would a database administrator monitor to gauge server health? Select two.)
Which of the following is the correct order of the steps in the database deployment process?
A)
1. Connect
2. Install
3. Configure
4. Confirm prerequisites
5. Validate
6. Test
7. Release
B)
1. Configure
2. Install
3. Connect
4. Test
5. Confirm prerequisites
6. Validate
7. Release
C)
1. Confirm prerequisites
2. Install
3. Configure
4. Connect
5. Test
6. Validate
7. Release
D)
1. Install
2. Configure
3. Confirm prerequisites
4. Connect
5. Test
6. Validate
7. Release
Which of the following best describes the category of SQL commands required to revoke access to database objects?
Which of the following constraints is used to enforce referential integrity?
(Which of the following types of scripting can be executed on a web browser?)
(Which of the following describes the method in which data is encrypted first with an encryption key and then wrapped by a managed root key?)
Which of the following have data manipulation and procedural scripting power? (Choose two.)
A developer is designing a table that does not have repeated values. Which of the following indexes should the developer use to prevent duplicate values from being inserted?
A DBA is reviewing the following logs to determine the current data backup plan for a primary data server:
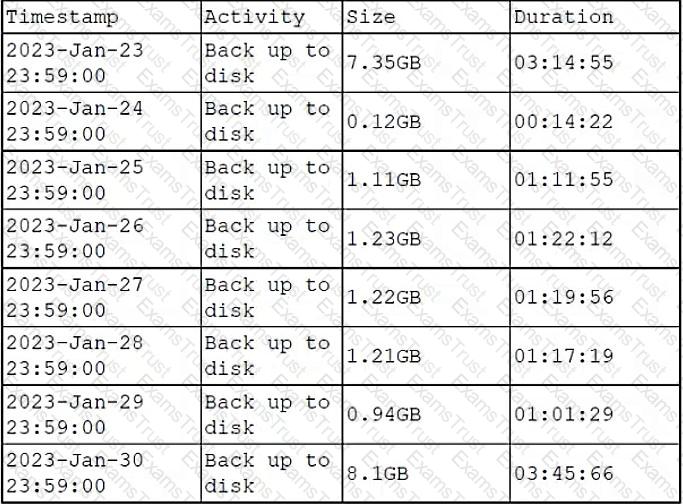
Which of the following best describes this backup plan?