An application must pass a vulnerability assessment to move to the next gate. Consequently, any security issues that are found must be remediated prior to the next gate. Which of the following best describes the method for end-to-end vulnerability assessment?
When of the following techniques can be implemented to safeguard the confidentiality of sensitive information while allowing limited access to authorized individuals?
Legacy medical equipment, which contains sensitive data, cannot be patched. Which of the following is the best solution to improve the equipment's security posture?
A security analyst is deploying a new application in the environment. The application needs to be integrated with several existing applications that contain SPI Pnor to the deployment, the analyst should conduct:
A consultant evaluating multiple threat intelligence leads to assess potential risks for a client. Which of the following is the BEST approach for the consultant to consider when modeling the client's attack surface?
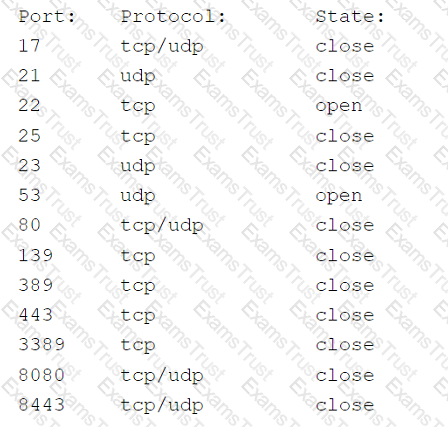
An organization has a policy that requires servers to be dedicated to one function and unneeded services to be disabled. Given the following output from an Nmap scan of a web server:

Which of the following ports should be closed?
An organization has the following policies:
*Services must run on standard ports.
*Unneeded services must be disabled.
The organization has the following servers:
*192.168.10.1 - web server
*192.168.10.2 - database server
A security analyst runs a scan on the servers and sees the following output:
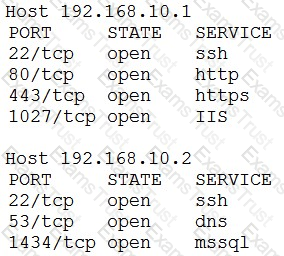
Which of the following actions should the analyst take?
While reviewing system logs, a network administrator discovers the following entry:
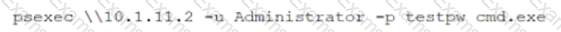
Which of the following occurred?
A company's security team recently discovered a number of workstations that are at the end of life. The workstation vendor informs the team that the product is no longer supported and patches are no longer available The company is not prepared to cease its use of these workstations Which of the following would be the BEST method to protect these workstations from threats?
A security analyst is attempting to resolve an incident in which highly confidential company pricing information was sent to clients. It appears this information was unintentionally sent by an employee who attached it to public marketing material. Which of the following configuration changes would work BEST to limit the risk of this incident being repeated?
An analyst reviews the most recent vulnerability management report and notices a firewall with 99.98% required uptime is reporting different firmware versions on scans than were reported in previous scans. The vendor released new firewall firmware a few months ago. Which of the following will the analyst most likely do next given the requirements?
The steering committee for information security management annually reviews the security incident register for the organization to look for trends and systematic issues. The steering committee wants to rank the risks based on past incidents to improve the security program for next year. Below is the incident register for the organization:
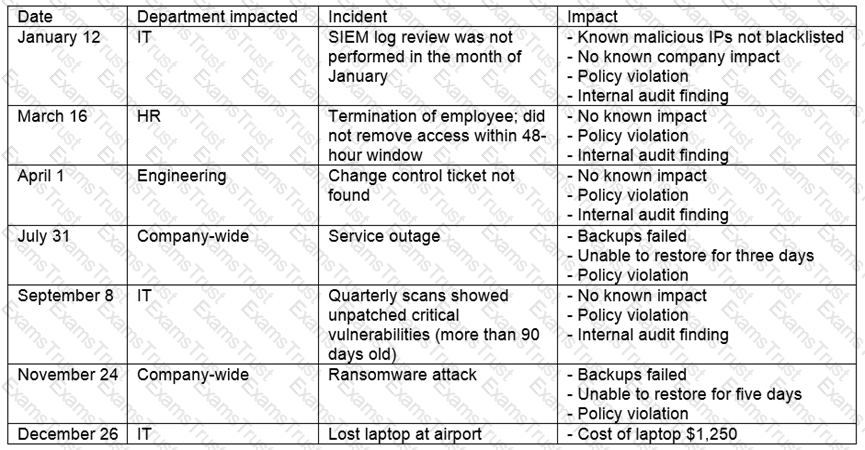
Which of the following should the organization consider investing in first due to the potential impact of availability?
During the threat modeling process for a new application that a company is launching, a security analyst needs to define methods and items to take into consideralion Wtiich of the following are part of a known threat modeling method?
A development team recently released a new version of a public-facing website for testing prior to production. The development team is soliciting the help of various teams to validate the functionality of the website due to its high visibility. Which of the following activities best describes the process the development team is initiating?
An organization is performing a risk assessment to prioritize resources for mitigation and remediation based on impact. Which of the following metrics, in addition to the CVSS for each CVE, would best enable the organization to prioritize its efforts?
A security analyst needs to provide the development team with secure connectivity from the corporate network to a three-tier cloud environment. The developers require access to servers in all three tiers in order to perform various configuration tasks. Which of the following technologies should the analyst implement to provide secure transport?
Some hard disks need to be taken as evidence for further analysis during an incident response. Which of the following procedures must be completed FIRST for this type of evidence acquisition?
A cybersecurity analyst inspects DNS logs on a regular basis to identify possible IOCs that are not triggered by known signatures. The analyst reviews the following log snippet:
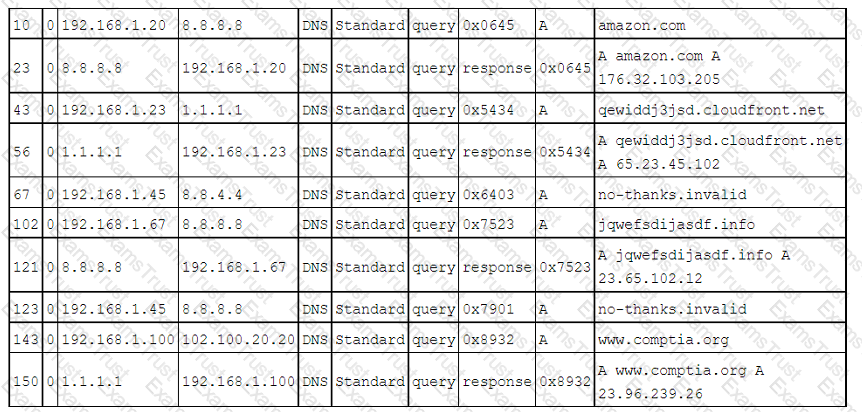
Which of the following should the analyst do next based on the information reviewed?
A security analyst scans the company's external IP range and receives the following results from one of the hosts:
Which of the following best represents the security concern?
A company's application development has been outsourced to a third-party development team. Based on the SLA. The development team must follow industry best practices for secure coding. Which of the following is the BEST way to verify this agreement?
An incident response plan requires systems that contain critical data to be triaged first in the event of a compromise. Which of the following types of data would most likely be classified as critical?
During a company’s most recent incident, a vulnerability in custom software was exploited on an externally facing server by an APT. The lessons-learned report noted the following:
• The development team used a new software language that was not supported by the security team's automated assessment tools.
• During the deployment, the security assessment team was unfamiliar with the new language and struggled to evaluate the software during advanced testing. Therefore, the vulnerability was not detected.
• The current IPS did not have effective signatures and policies in place to detect and prevent runtime attacks on the new application.
To allow this new technology to be deployed securely going forward, which of the following will BEST address these findings? (Choose two.)
A company has Detected a large number of tailed login attempts on its network A security analyst is investigating the network's activity logs to establish a pattern of behavior. Which of the following techniques should the analyst use to analyze the increase in failed login attempts?
A company frequently expenences issues with credential stuffing attacks Which of the following is the BEST control to help prevent these attacks from being successful?
As part of an Intelligence feed, a security analyst receives a report from a third-party trusted source. Within the report are several detrains and reputational information that suggest the company's employees may be targeted for a phishing campaign. Which of the following configuration changes would be the MOST appropriate for Mergence gathering?
Which of the following is an advantage of SOAR over SIEM?
A code review reveals a web application is using lime-based cookies for session management. This is a security concern because lime-based cookies are easy to:
Which of me following are reasons why consumer IoT devices should be avoided in an enterprise environment? (Select TWO)
Several operator workstations are exhibiting unusual behavior, including applications loading slowly, temporary files being overwritten, and reboot notifications to apply antivirus signatures. During an investigation, an analyst finds evidence of Bitcoin mining. Which of the following is the first step the analyst should take to prevent further spread of the mining operation?
An analyst is reviewing the following output as part of an incident:
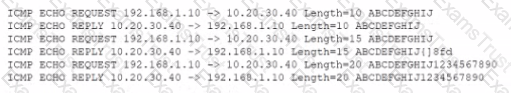
Which of the Wowing is MOST likely happening?
In SIEM software, a security analysis selected some changes to hash signatures from monitored files during the night followed by SMB brute-force attacks against the file servers Based on this behavior, which of the following actions should be taken FIRST to prevent a more serious compromise?
An analyst is performing a BIA and needs to consider measures and metrics. Which of the following would help the analyst achieve this objective? (Select two).
A security analyst identified some potentially malicious processes after capturing the contents of memory from a machine during incident response. Which of the following procedures is the NEXT step for further in investigation?
An analyst determines a security incident has occurred Which of the following is the most appropnate NEXT step in an incident response plan?
A security learn implemented a SCM as part for its security-monitoring program there is a requirement to integrate a number of sources Into the SIEM to provide better context relative to the events being processed. Which of the following B€ST describes the result the security learn hopes to accomplish by adding these sources?
An organization wants to collect loCs from multiple geographic regions so it can sell the information to its customers. Which of the following should the organization deploy to accomplish this task?
Which of the following is an advantage of continuous monitoring as a way to help protect an enterprise?
A security technician configured a NIDS to monitor network traffic. Which of the following is a condition in which harmless traffic is classified as a potential network attack?
An analyst is responding 10 an incident involving an attack on a company-owned mobile device that was being used by an employee to collect data from clients in the held. Maiware was loaded on the device via the installation of a third-party software package The analyst has baselined the device Which of the following should the analyst do to BEST mitigate future attacks?
A security analyst needs to recommend the best approach to test a new application that simulates abnormal user behavior to find software bugs. Which of the following would best accomplish this task?
While conoXicting a cloud assessment, a security analyst performs a Prowler scan, which generates the following within the report:
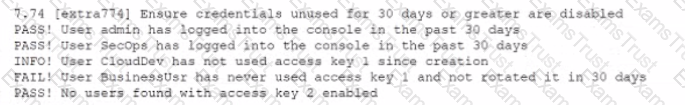
Based on the Prowler report, which of the following is the BEST recommendation?
A security analyst is looking at the headers of a few emails that appear to be targeting all users at an organization:
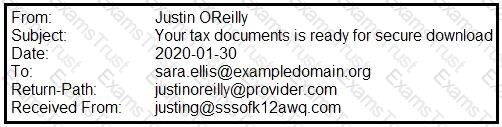
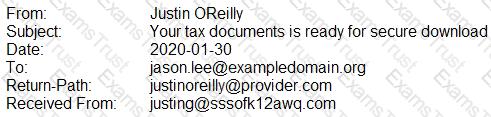
Which of the following technologies would MOST likely be used to prevent this phishing attempt?
Which of the following is the BEST way to gather patch information on a specific server?
A new government regulation requires that organizations only retain the minimum amount of data on a person to perform the organization's necessary activities. Which of the following techniques would help an organization comply with this new regulation?
A security analyst is investigating a reported phishing attempt that was received by many users throughout the company The text of one of the emails is shown below:
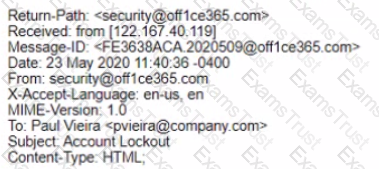
Office 365 User.
It looks like you account has been locked out Please click this and follow the pfompts to restore access
Regards.
Security Team
Due to the size of the company and the high storage requirements, the company does not log DNS requests or perform packet captures of network traffic, but rt does log network flow data Which of the following commands will the analyst most likely execute NEXT?
Which of the following BEST identifies the appropriate use of threat intelligence as a function of detection and response?
A security analyst is monitoring a company's network traffic and finds ping requests going to accounting and human resources servers from a SQL server. Upon investigation, the analyst discovers a technician responded to potential network connectivity issues. Which of the following is the best way for the security analyst to respond?
An analyst is reviewing registry keys for signs of possible compromise. The analyst observes the following entries:
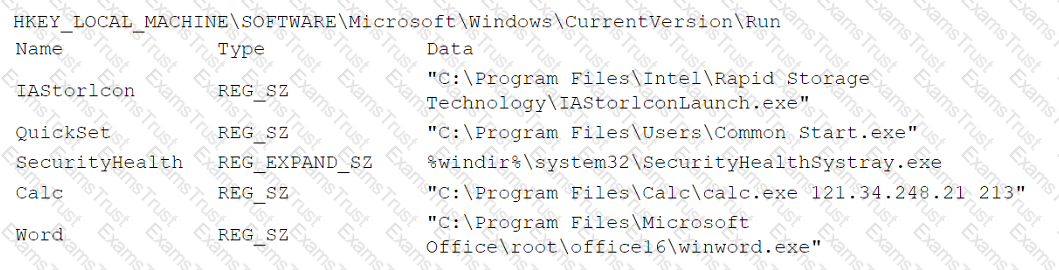
Which of the following entries should the analyst investigate first?
Which of the following data exfiltration discoveries would most likely require communicating a breach to regulatory agencies?
A security manager has asked an analyst to provide feedback on the results of a penetration test. After reviewing the results, the manager requests
information regarding the possible exploitation of vulnerabilities. Which of the following information data points would be MOST useful for the analyst
to provide to the security manager, who would then communicate the risk factors to the senior management team? (Select TWO).
A company is required to monitor for unauthorized changes to baselines on all assets to comply with industry regulations. Two of the remote units did not recover after scans were performed on the assets. An analyst needs to recommend a solution to prevent recurrence. Which of the following is the best way to satisfy the regulatory requirement without impacting the availability to similar assets and creating an unsustainable process?
After examine a header and footer file, a security analyst begins reconstructing files by scanning the raw data bytes of a hard disk and rebuilding them. Which of the following techniques is the analyst using?
Which of the following is the software development process by which function, usability, and scenarios are tested against a known set of base requirements?
A user reports a malware alert to the help desk. A technician verities the alert, determines the workstation is classified as a low-severity device, and uses network controls to block access. The technician then assigns the ticket to a security analyst who will complete the eradication and recovery processes. Which of the following should the security analyst do next?
During a review of recent network traffic, an analyst realizes the team has seen this same traffic multiple times in the past three weeks, and it resulted in confirmed malware activity The analyst also notes there is no other alert in place for this traffic After resolving the security incident, which of the following would be the BEST action for the analyst to take to increase the chance of detecting this traffic in the future?
A company is setting up a small, remote office to support five to ten employees. The company's home office is in a different city, where the company uses a cloud service provider for its business applications and a local server to host its data. To provide shared access from the remote office to the local server and the business applications, which of the following would be the easiest and most secure solution?
Company A is m the process of merging with Company B As part of the merger, connectivity between the ERP systems must be established so portent financial information can be shared between the two entitles. Which of the following will establish a more automated approach to secure data transfers between the two entities?
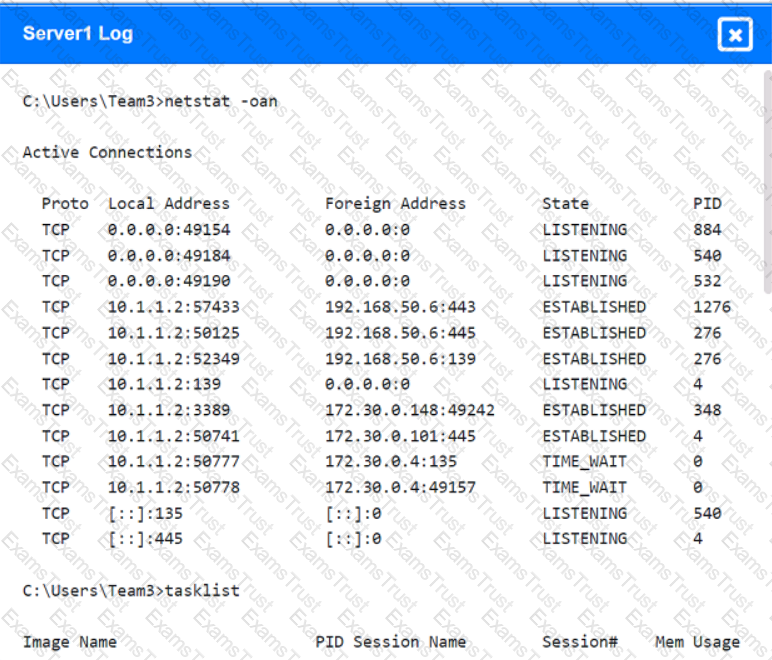
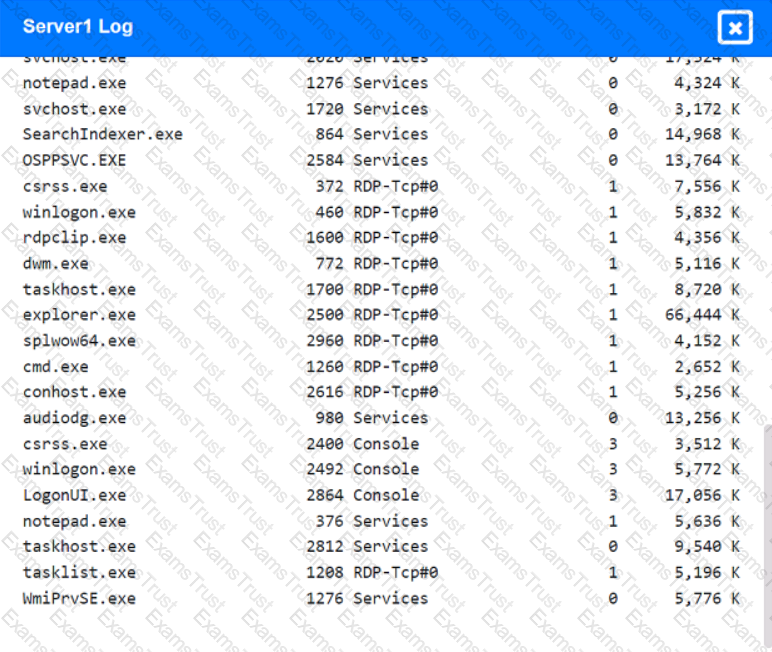
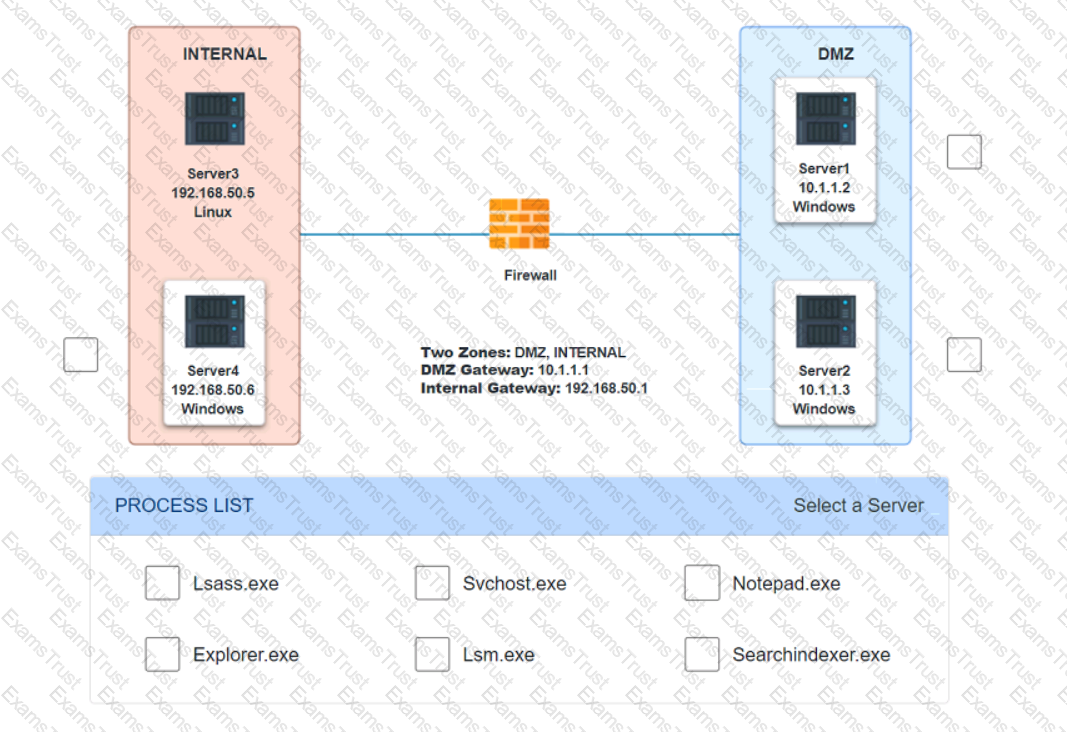
Malware is suspected on a server in the environment.
The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one Of the servers may be malware.
INSTRUCTIONS
Servers 1 , 2, and 4 are clickable. Select the Server and the process that host the malware.
Which of the following best explains why it is important for companies to implement both privacy and security policies?
Which of the following should a database administrator for an analytics firm implement to best protect PII from an insider threat?
An analyst receives artifacts from a recent Intrusion and is able to pull a domain, IP address, email address, and software version. When of the following points of the Diamond Model of Intrusion Analysis does this intelligence represent?
A security analyst is analyzing the following output from the Spider tab of OWASP ZAP after a vulnerability scan was completed:
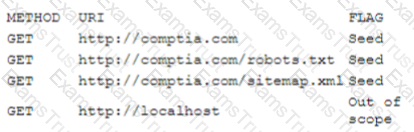
Which of the following options can the analyst conclude based on the provided output?
A company's blocklist has outgrown the current technologies in place. The ACLs are at maximum, and the IPS signatures only allow a certain amount of space for domains to be added, creating the need for multiple signatures. Which of the following configuration changes to the existing controls would be the MOST appropriate to improve performance?
A current, validated DLP solution Is now in place because of a previous data breach However, a new data breach has taken place The following symptoms were observed shorty after a recent sales meeting:
* Sensitive corporate documents appeared on the dark web.
* Unusually large packets of data were being sent out.
Which of the following is most likely occurring?
A security analyst discovers suspicious activity going to a high-value corporate asset. After reviewing the traffic, the security analyst identifies that
malware was successfully installed on a machine. Which of the following should be completed first?
A technician working at company.com received the following email:
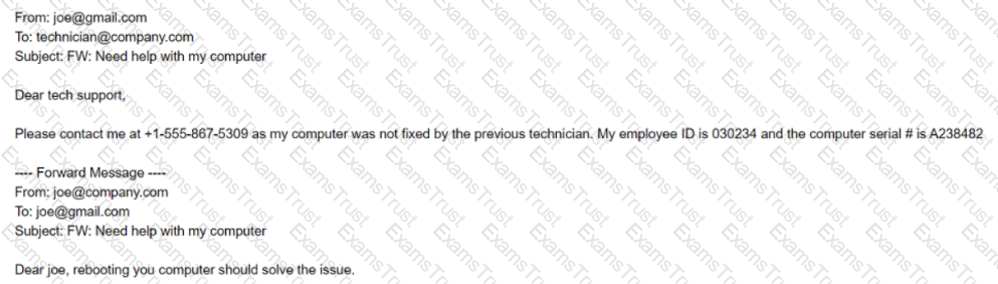
After looking at the above communication, which of the following should the technician recommend to the security team to prevent exposure of sensitive information and reduce the risk of corporate data being stored on non-corporate assets?
While investigating reports or issues with a web server, a security analyst attempts to log in remotely and recedes the following message:
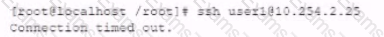
The analyst accesses the server console, and the following console messages are displayed:
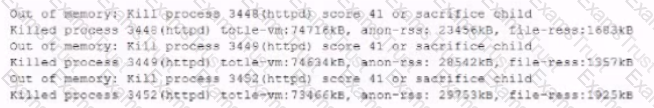
The analyst is also unable to log in on the console. While reviewing network captures for the server, the analyst sees many packets with the following signature:
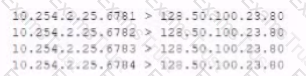
Which of the following is the BEST step for the analyst to lake next in this situation?
A company wants to configure the environment to allow passive network monitonng. To avoid disrupting the sensitive network, which of the following must be supported by the scanner's NIC to assist with the company's request?
A security analyst is reviewing the following log entries to identify anomalous activity:
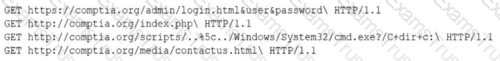
Which of the following attack types is occurring?
A security analyst is handling an incident in which ransomware has encrypted the disks of several company workstations. Which of the following would work BEST to prevent this type of Incident in the future?
A customer notifies a security analyst that a web application is vulnerable to information disclosure The analyst needs to indicate the seventy of the vulnerability based on its CVSS score, which the analyst needs to calculate When analyzing the vulnerability the analyst realizes that tor the attack to be successful, the Tomcat configuration file must be modified Which of the following values should the security analyst choose when evaluating the CVSS score?
A security analyst is researching ways to improve the security of a company's email system to mitigate emails that are impersonating company executives. Which of the following would be BEST for the analyst to configure to achieve this objective?
A security analyst is reviewing WAF alerts and sees the following request:

Which of the following BEST describes the attack?
During an incident response procedure, a security analyst acquired the needed evidence from the hard drive of a compromised machine. Which of the following actions should the analyst perform next to ensure the data integrity of the evidence?
An incident response team is responding to a breach of multiple systems that contain Pll and PHI Disclosure of the incident to external entities should be based on:
A new variant of malware is spreading on the company network using TCP 443 to contact its command-and-control server The domain name used for callback continues to change, and the analyst is unable to predict future domain name variance Which of the following actions should the analyst take to stop malicious communications with the LEAST disruption to service?
A security analyst is reviewing malware files without running them. Which of the following analysis types is the security analyst using?
An analyst receives an alert from the continuous-monitoring solution about unauthorized changes to the firmware versions on several field devices. The asset owners confirm that no firmware version updates were performed by authorized technicians, and customers have not reported any performance issues or outages. Which Of the following actions would be BEST for the analyst to recommend to the asset owners to secure the devices from further exploitation?
Which of the following solutions is the BEST method to prevent unauthorized use of an API?
A manufacturing company uses a third-party service provider for Tier 1 security support. One of the requirements is that the provider must only source talent from its own country due to geopolitical and national security interests. Which of the following can the manufacturing company implement to ensure the third-party service provider meets this requirement?
Which of the following is a vulnerability associated with the Modbus protocol?
A security analyst notices the following entry while reviewing the server togs
OR 1=1' ADD USER attacker' PW 1337password' ----
Which of the following events occurred?
The IT department is concerned about the possibility of a guest device infecting machines on the corporate network or taking down the company's singe internet connection. Which of the following should a security analyst recommend to BEST meet the requirements outlined by the IT Department?
An IT security analyst has received an email alert regarding vulnerability within the new fleet of vehicles the company recently purchased. Which of the following attack vectors is the vulnerability MOST likely targeting?
A help desk technician inadvertently sent the credentials of the company's CRM n clear text to an employee's personal email account. The technician then reset the employee's account using the appropriate process and the employee's corporate email, and notified the security team of the incident According to the incident response procedure, which of the following should the security team do NEXT?
An organization is focused on restructuring its data governance programs and an analyst has been Tasked with surveying sensitive data within the organization. Which of the following is the MOST accurate method for the security analyst to complete this assignment?
An organization has the following risk mitigation policies
• Risks without compensating controls will be mitigated first it the nsk value is greater than $50,000
• Other nsk mitigation will be pnontized based on risk value.
The following risks have been identified:
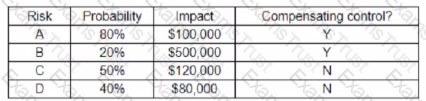
Which of the following is the ordei of priority for risk mitigation from highest to lowest?
Given the output below:
#nmap 7.70 scan initiated Tues, Feb 8 12:34:56 2022 as: nmap -v -Pn -p 80,8000,443 --script http-* -oA server.out 192.168.220.42 Which of the following is being performed?
Forming a hypothesis, looking for indicators of compromise, and using the findings to proactively improve detection capabilities are examples of the value of:
Which of the following, BEST explains the function of TPM?
Which of the following BEST describes what an organizations incident response plan should cover regarding how the organization handles public or private disclosures of an incident?
An analyst reviews a legacy Windows XP system and concludes an attacker executed code that modified the contents of the system's memory. Which of the following attack techniques did the attacker use?
A company is aiming to test a new incident response plan. The management team has made it clear that the initial test should have no impact on the environment. The company has limited
resources to support testing. Which of the following exercises would be the best approach?
A company has alerted planning the implemented a vulnerability management procedure. However, to security maturity level is low, so there are some prerequisites to complete before risk calculation and prioritization. Which of the following should be completed FIRST?
A cybersecurity analyst is researching operational data to develop a script that will detect the presence of a threat on corporate assets. Which of the following contains the most useful information to produce this script?
Which of the following is MOST important when developing a threat hunting program?
An organization discovers motherboards within the environment that appear to have been physically altered during the manufacturing process. Which of the following is the BEST course of action to mitigate the risk of this reoccurring?
A security analyst is reviewing the output of tcpdump to analyze the type of activity on a packet capture:
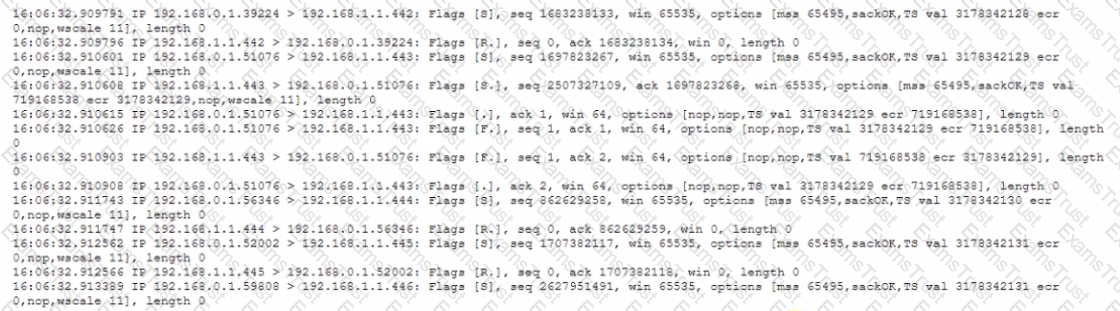
Which of the following generated the above output?
A product security analyst has been assigned to evaluate and validate a new products security capabilities Part of the evaluation involves reviewing design changes at specific intervals tor security deficiencies recommending changes and checking for changes at the next checkpoint Which of the following BEST defines the activity being conducted?
During a review of the vulnerability scan results on a server, an information security analyst notices the following:
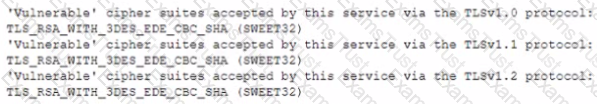
The MOST appropriate action for the analyst to recommend to developers is to change the web server so:
A security analyst needs to determine the best method for securing access to a top-secret datacenter Along with an access card and PIN code, which of the following additional authentication methods would be BEST to enhance the datacenter's security?
An organization wants to move non-essential services into a cloud computing environment. The management team has a cost focus and would like to achieve a recovery time objective of 12 hours. Which of the following cloud recovery strategies would work best to attain the desired outcome?
A cybersecurity analyst routinely checks logs, querying for login attempts. While querying for unsuccessful login attempts during a five-day period, the analyst produces the following report:
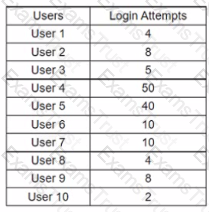
Which of the following BEST describes what the analyst Just found?
Which of the following is a reason for correctly identifying APTs that might be targeting an organization?
A systems administrator believes a user's workstation has been compromised. The workstation's performance has been lagging significantly for the past several hours. The administrator runs the task list
/ v command and receives the following output:
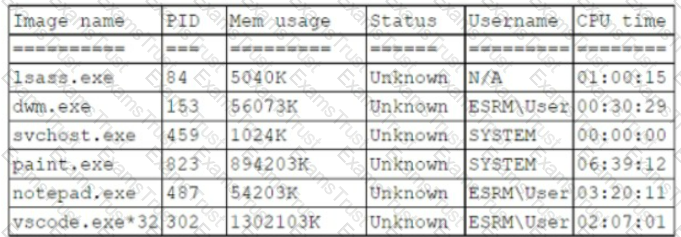
Which of the following should a security analyst recognize as an indicator of compromise?
A security analyst responds to a series of events surrounding sporadic bandwidth consumption from an endpoint device. The security analyst then identifies the following additional details:
• Bursts of network utilization occur approximately every seven days.
• The content being transferred appears to be encrypted or obfuscated.
• A separate but persistent outbound TCP connection from the host to infrastructure in a third-party cloud is in place.
• The HDD utilization on the device grows by 10GB to 12GB over the course of every seven days.
• Single file sizes are 10GB.
Which of the following describes the most likely cause of the issue?
A forensic examiner is investigating possible malware compromise on an active endpoint device. Which of the following steps should the examiner perform first?
While implementing a PKI for a company, a security analyst plans to utilize a dedicated server as the certAcate authority that is only used to sign intermediate certificates. Which of the following are the MOST secure states for the certificate authority server when it is not in use? (Select TWO)
A security analyst is concerned the number of security incidents being reported has suddenly gone down. Daily business interactions have not changed, and no following should the analyst review FIRST?
A company employee downloads an application from the internet. After the installation, the employee begins experiencing noticeable performance issues, and files are appearing on the desktop.
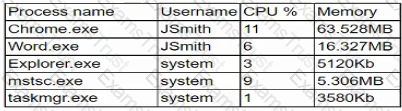
Which of the following processes will the security analyst Identify as the MOST likely indicator of system compromise given the processes running in Task Manager?
The help desk is having difficulty keeping up with all onboarding and offboarding requests. Managers often submit, requests for new users at the last minute. causing the help desk to scramble to create accounts across many different Interconnected systems. Which of the following solutions would work BEST to assist the help desk with the onboarding and offboarding process while protecting the company's assets?