A network administrator receives a ticket from one of the company's offices about video calls that work normally for one minute and then get very choppy. The network administrator pings the video server from that site to ensure that it is reachable:
(Ping output shows responses with varying latency times, including spikes: 11ms, 672ms, 849ms, 92ms, etc.)
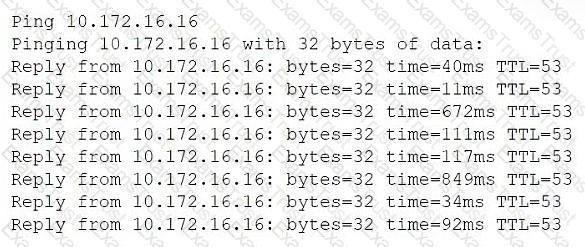
Which of the following is most likely the cause of the video call issue?
Throughout the day, a sales team experiences videoconference performance issues when the accounting department runs reports. Which of the following is the best solution?
Which of the following helps the security of the network design to align with industry best practices?
An administrator must ensure that credit card numbers are not contained in any outside messaging or file transfers from the organization. Which of the following controls meets this requirement?
A network architect must design a new branch network that meets the following requirements:
No single point of failure
Clients cannot be impacted by changes to the underlying medium
Clients must be able to communicate directly to preserve bandwidth
Which of the following network topologies should the architect use?
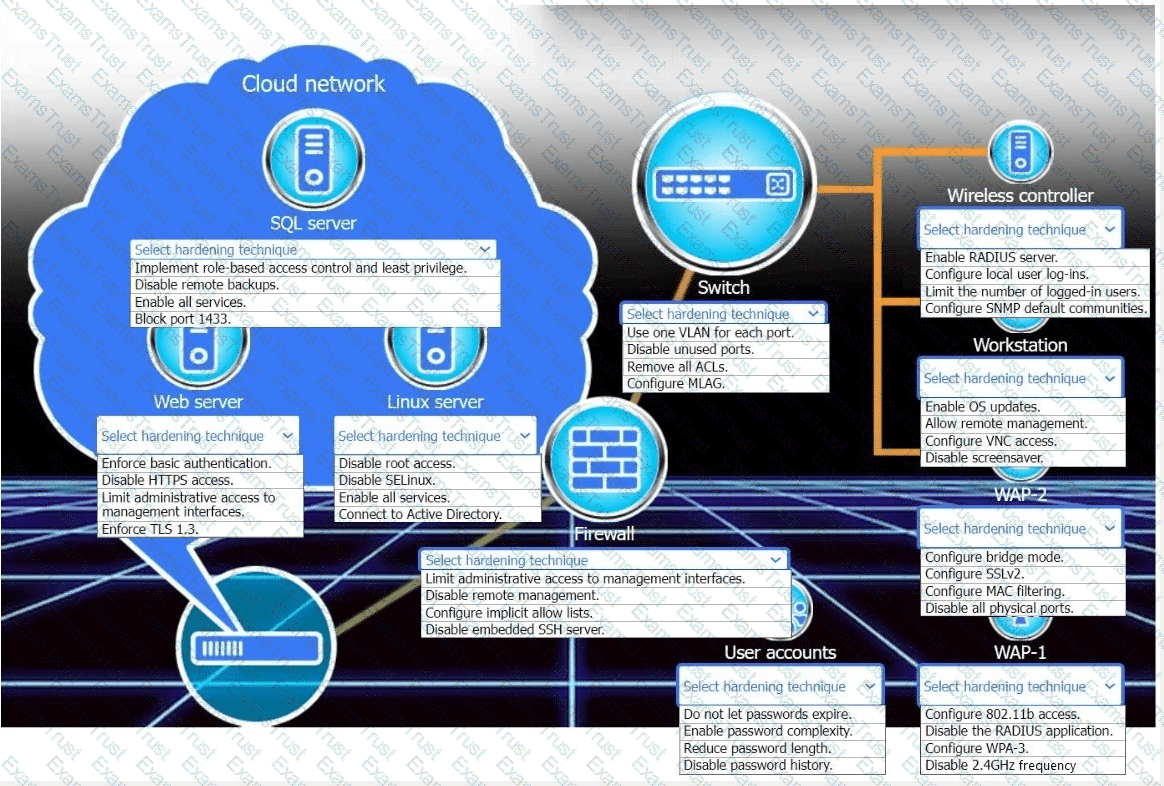
New devices were deployed on a network and need to be hardened.
INSTRUCTIONS
Use the drop-down menus to define the appliance-hardening techniques that provide themostsecure solution.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A partner is migrating a client from on-premises to a hybrid cloud. Given the following project status information, the initial project timeline estimates need to be revised:
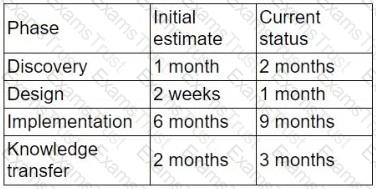
(Refer to image: Phases like Discovery, Design, Implementation, and Knowledge Transfer have all exceeded their initial estimated timelines.)
Which of the following documents needs to be revised to best reflect the current status of the project?
A network engineer adds a large group of servers to a screened subnet and configures them to use IPv6 only. The servers need to seamlessly communicate with IPv4 servers on the internal networks. Which of the following actions is the best way to achieve this goal?
Security policy states that all inbound traffic to the environment needs to be restricted, but all external outbound traffic is allowed within the hybrid cloud environment. A new application server was recently set up in the cloud. Which of the following would most likely need to be configured so that the server has the appropriate access set up? (Choose two.)
A company is transitioning from on-premises to a hybrid environment. Due to regulatory standards, the company needs to achieve a high level of reliability and high availability for the connection between its data center and the cloud provider. Which of the following solutions best meets the requirements?
A network architect must ensure only certain departments can access specific resources while on premises. Those same users cannot be allowed to access those resources once they have left campus. Which of the following would ensure access is provided according to these requirements?
A company is expanding operations and opening a new facility. The executive leadership team decides to purchase an insurance policy that will cover the cost of rebuilding the facility in case of a natural disaster. Which of the following describes the team's decision?
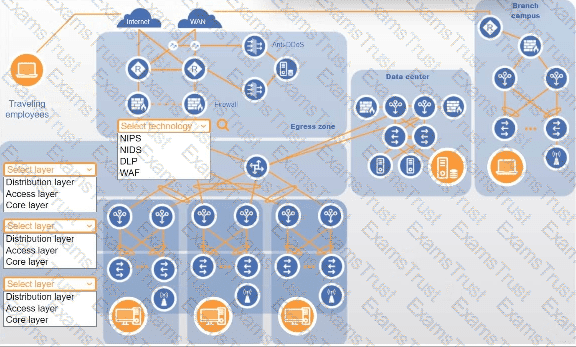
You are designing a campus network with a three-tier hierarchy and need to ensure secure connectivity between locations and traveling employees.
INSTRUCTIONS
Review the command output by clicking on the server, laptops, and workstations on the network.
Use the drop-down menus to determine the appropriate technology and label for each layer on the diagram. Options may only be used once.
Click on the magnifying glass to make additional configuration changes.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A cloud engineer is planning to build VMs in a public cloud environment for a cloud migration. A cloud security policy restricts access to the console for new VM builds. The engineer wants to replicate the settings for each of the VMs to ensure the network settings are preconfigured. Which of the following is the best deployment method?
A security architect needs to increase the security controls around computer hardware installations. The requirements are:
Auditable access logs to computer rooms
Alerts for unauthorized access attempts
Remote visibility to the inside of computer rooms
Which of the following controls best meet these requirements? (Choose two.)
A network administrator recently deployed new Wi-Fi 6E access points in an office and enabled 6GHz coverage. Users report that when they are connected to the new 6GHz SSID, the performance is worse than the 5GHz SSID. The network administrator suspects that there is a source of 6GHz interference in the office. Using the troubleshooting methodology, which of the following actions should the network administrator do next?
A cloud architect needs to change the network configuration at a company that uses GitOps to document and implement network changes. The Git repository uses main as the default branch, and the main branch is protected. Which of the following should the architect do after cloning the repository?
A company just launched a cloud-based application. Some users are reporting the application will not load. A cloud engineer investigates the issues and reports the following:
Not all users are experiencing the issue
The application infrastructure is optimal
Users experiencing the issue belong to the company's remote sales team
Which of the following is most likely misconfigured?
A company is expanding its network and needs to ensure improved stability and reliability. The proposed solution must fulfill the following requirements:
Detection and prevention of network loops
Automatic configuration of ports
Standard protocol (not proprietary)
Which of the following protocols is the most appropriate?
A cloud network engineer needs to enable network flow analysis in the VPC so headers and payload of captured data can be inspected. Which of the following should the engineer use for this task?
A company provides an API that runs on the public cloud for its customers. A fixed number of VMs host the APIs. During peak hours, the company notices a spike in usage that results in network communication speeds slowing down for all customers. The management team has decided that access for all customers should be fair and accessible at all times. Which of the following is the most cost-effective way to address this issue?
An organization's Chief Technical Officer is concerned that changes to the network using IaC are causing unscheduled outages. Which of the following best mitigates this risk?
A company hosts its applications on the cloud and is expanding its business to Europe. Thecompany must comply with General Data Protection Regulation (GDPR) to limit European customers' access to data. The network team configures the firewall rules but finds that some customers in the United States can access data hosted in Europe. Which of the following is the best option for the network team to configure?
A global company has depots in various locations. A proprietary application was deployed locally at each of the depots, but issues with getting the consolidated data instantly occurred. The Chief Information Officer decided to centralize the application and deploy it in the cloud. After the cloud deployment, users report the application is slow. Which of the following is most likely the issue?
A network architect is creating a network topology for a global SD-WAN deployment. The business has offices in Asia, Europe, and the United States and makes use of data centers in theUnited States and Europe. Most traffic between sites must have the lowest latency possible. Which of the following topologies best meets this requirement?