A company isolated its OT systems from other areas of the corporate network These systems are required to report usage information over the internet to the vendor Which oi the following b*st reduces the risk of compromise or sabotage' (Select two).
An IPSec solution is being deployed. The configuration files for both the VPN
concentrator and the AAA server are shown in the diagram.
Complete the configuration files to meet the following requirements:
• The EAP method must use mutual certificate-based authentication (With
issued client certificates).
• The IKEv2 Cipher suite must be configured to the MOST secure
authenticated mode of operation,
• The secret must contain at least one uppercase character, one lowercase
character, one numeric character, and one special character, and it must
meet a minimumlength requirement of eight characters,
INSTRUCTIONS
Click on the AAA server and VPN concentrator to complete the configuration.
Fill in the appropriate fields and make selections from the drop-down menus.
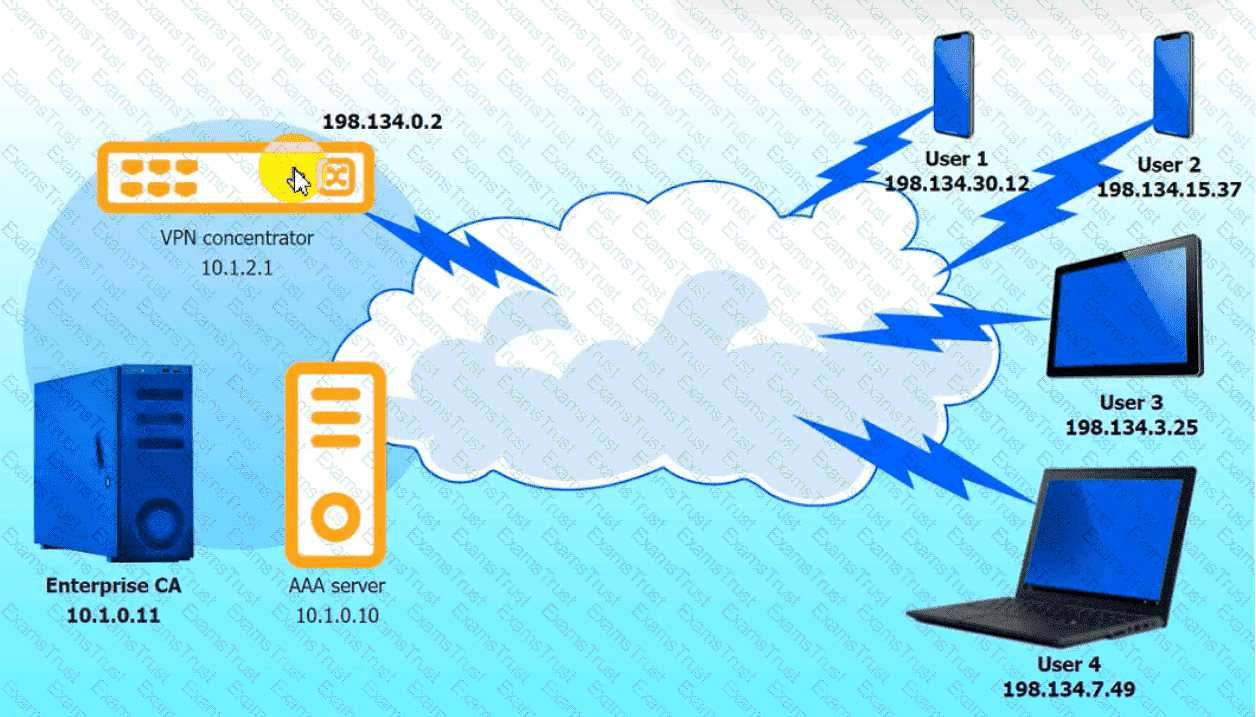
VPN Concentrator:
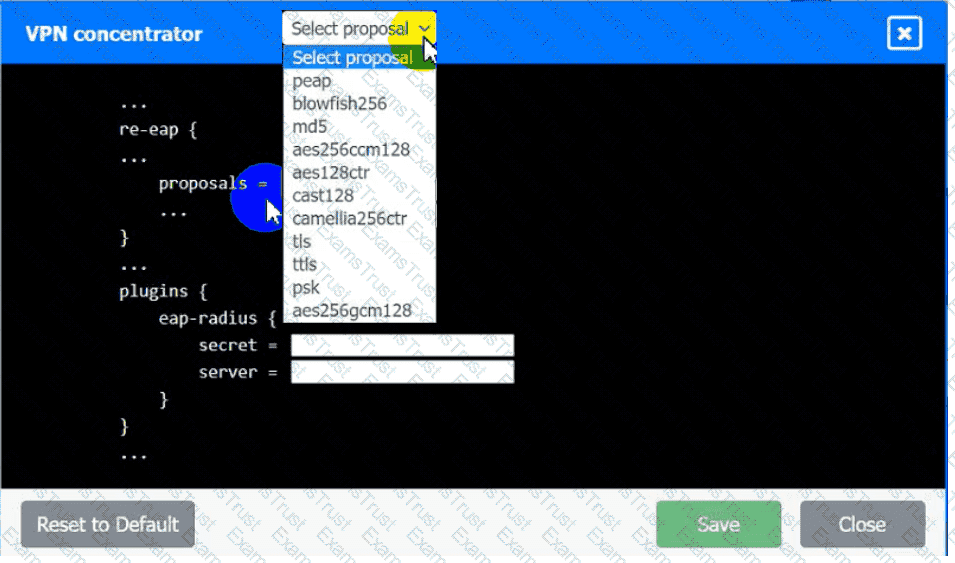
AAA Server:
An organization wants to manage specialized endpoints and needs a solution that provides the ability to
* Centrally manage configurations
* Push policies.
• Remotely wipe devices
• Maintain asset inventory
Which of the following should the organization do to best meet these requirements?
Which of the following best explains the business requirement a healthcare provider fulfills by encrypting patient data at rest?
An organization is required to
* Respond to internal andexternal inquiries in a timely manner
* Provide transparency.
* Comply with regulatory requirements
The organization has not experienced any reportable breaches but wants to be prepared if a breach occurs in the future. Which of the following is the best way for the organization to prepare?
A company wants to implement hardware security key authentication for accessing sensitive information systems The goal is to prevent unauthorized users from gaining access with a stolen password Which of the following models should the company implement to b«st solve this issue?
A threat hunter is identifying potentially malicious activity associated with an APT. When the threat hunter runs queries against the SIEM platform with a date range of 60 to 90 days ago, the involved account seems to be typically most active in the evenings. When the threat hunter reruns the same query with a date range of 5 to 30 days ago, the account appears to be most active in the early morning. Which of the following techniques is the threat hunter using to better understand the data?
A security architect is troubleshooting an issue with an OIDC implementation. The architect reviews the following configuration and errors:
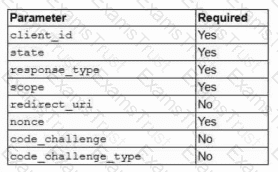
Error: Invalid authentication request code
Which of the following is the most likely cause of the error?
After an organization met with its ISAC, the organization decided to test the resiliency of its security controls against a small number of advanced threat actors. Which of the following will enable the security administrator to accomplish this task?
A developer makes a small change to a resource allocation module on a popular social media website and causes a memory leak. During a peak utilization period, several web servers crash, causing the website to go offline. Which of the following testing techniques is the most efficient way to prevent this from reoccurring?
Which of the following are the best ways to mitigate the threats that are the highest priority? (Select two).
An external SaaS solution user reports a bug associated with the role-based access control module. This bug allows users to bypass system logic associated with client segmentation in the multitenant deployment model. When assessing the bug report, the developer finds that the same bug was previously identified and addressed in an earlier release. The developer then determines the bug was reintroduced when an existing software component was integrated from a prior version of the platform. Which of the following is the best way to prevent this scenario?
A company needs to define a new roadmap for improving secure coding practices in the software development life cycle and implementing better security standards. Which of the following is the best way for the company to achieve this goal?
An application requires the storage of PII. A systems engineer needs to implement a solution that uses an external device for key management. Which of the following is the best solution?
An organization determines existing business continuity practices are inadequate to support critical internal process dependencies during a contingency event. A compliance analyst wants the Chief Information Officer (CIO) to identify the level of residual risk that is acceptable to guide remediation activities. Which of the following does the CIO need to clarify?
A security officer received several complaints from usersabout excessive MPA push notifications at night The security team investigates and suspects malicious activities regarding user account authentication Which of the following is the best way for the security officer to restrict MI~A notifications''
A company must meet the following security requirements when implementing controls in order to be compliant with government policy:
• Access to the system document repository must be MFA enabled.
• Ongoing risk monitoring must be displayed on a system dashboard.
• Staff must receive email notifications about periodic tasks.
Which of the following best meets all of these requirements?
Company A and Company D ate merging Company A's compliance reports indicate branchprotections are not in place A security analyst needs to ensure that potential threats to the software development life cycle are addressed. Which of the following should me analyst cons
A software development team requires valid data for internal tests. Company regulations, however do not allow the use of this data in cleartext. Which of the following solutions best meet these requirements?
A user from the sales department opened a suspicious file attachment. The sales department then contacted the SOC to investigate a number of unresponsive systems, and the team successfully identified the file and the origin of the attack. Which of the following is the next step of the incident response plan?
A security administrator is reviewing the following code snippet from a website component:

A review of the inc.tmp file shows the following:
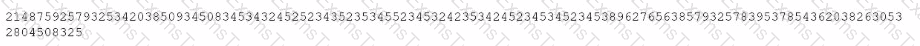
Which of the following is most likely the reason for inaccuracies?
A senior security engineer flags me following log file snippet as hawing likely facilitated an attacker's lateral movement in a recent breach:
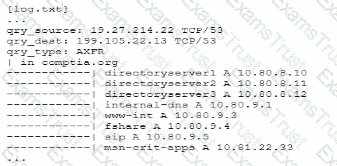
Which of the following solutions, if implemented, would mitigate the nsk of this issue reoccurnnp?
A security analyst is using data provided from a recent penetration test to calculate CVSS scores to prioritize remediation. Which of the following metric groups would the analyst need to determine to get the overall scores? (Select three).
Operational technology often relies upon aging command, control, and telemetry subsystems that were created with the design assumption of:
An organization is planning for disaster recovery and continuity ofoperations, and has noted the following relevant findings:
1. A natural disaster may disrupt operations at Site A, which would then cause an evacuation. Users are
unable to log into the domain from-their workstations after relocating to Site B.
2. A natural disaster may disrupt operations at Site A, which would then cause the pump room at Site B
to become inoperable.
3. A natural disaster may disrupt operations at Site A, which would then cause unreliable internet
connectivity at Site B due to route flapping.
INSTRUCTIONS
Match each relevant finding to the affected host by clicking on the host name and selecting the appropriate number.
For findings 1 and 2, select the items that should be replicated to Site B. For finding 3, select the item requiring configuration changes, then select the appropriate corrective action from the drop-down menu.
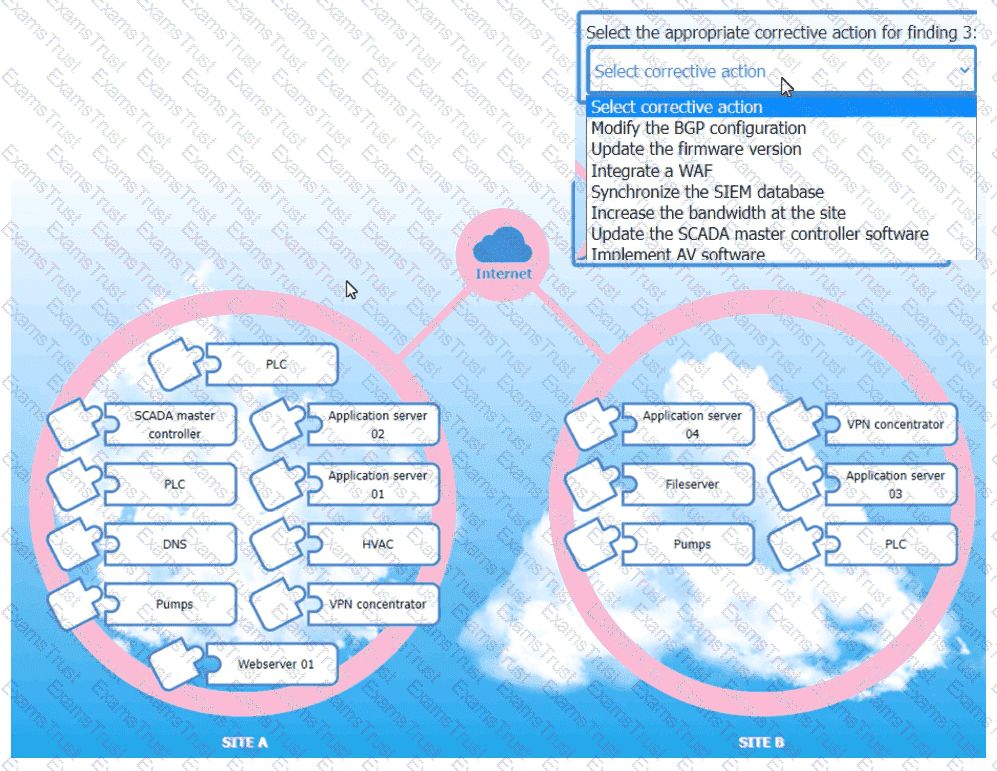
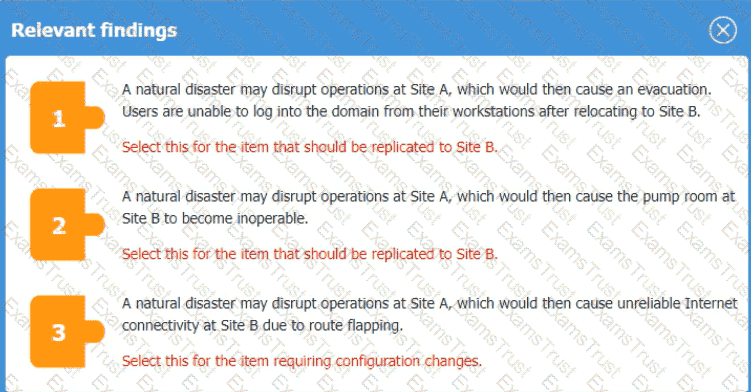
A security engineer wants to reduce the attack surface of a public-facing containerized application Which of the following will best reduce the application's privilege escalation attack surface?
A company receives several complaints from customers regarding its website. An engineer implements a parser for the web server logs that generates the following output:
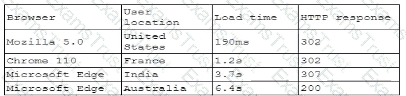
which of the following should the company implement to best resolve the issue?
A security engineer receives an alert from the SIEM platform indicating a possible malicious action on the internal network. The engineer generates a report that outputs the logs associated with the incident:

Which of the following actions best enables the engineer to investigate further?
An incident response analyst finds the following content inside of a log file that was collected from a compromised server:
.2308464678 ... whoami ..... su2032829%72%322/// ...... /etc/passwd .... 2087031731467478432 ...
$6490/90/./ ..< XML ?.. .... nty.
Which of the following is the best action to prevent future compromise?
An organization would like to increase the effectiveness of its incident response process across its multiplatform environment. A security engineer needs to implement the improvements using the organization's existing incident response tools. Which of the following should the security engineer use?
An organization is implementing Zero Trust architecture A systems administrator must increase the effectiveness of the organization's context-aware access system. Which of the following is the best way to improve the effectiveness of the system?
Which of the following most likely explains the reason a security engineer replaced ECC with a lattice-based cryptographic technique?
A company undergoing digital transformation is reviewing the resiliency of a CSP and is concerned about meeting SLA requirements in the event of a CSP incident. Which of the following would be best to proceed with the transformation?
After a company discovered a zero-day vulnerability in its VPN solution, the company plans to deploy cloud-hosted resources to replace its current on-premises systems. An engineer must find an appropriate solution to facilitate trusted connectivity. Which of the following capabilities is the most relevant?
After remote desktop capabilities were deployed in the environment, various vulnerabilities were noticed.
• Exfiltration of intellectual property
• Unencrypted files
• Weak user passwords
Which of the following is the best way to mitigate these vulnerabilities? (Select two).
An engineer wants to automate several tasks by running commands daily on a UNIX server. The engineer has only built-in, default tools available. Which of the following should the engineer use to best assist with this effort? (Select Two).
A security engineer receives the following findings from a recent security audit:
• Data should be protected based on user permissions and roles.
• User action tracking should be implemented across the network.
• Digital identities should be validated across the data access workflow.
Which of the following is the first action the engineer should take to address the findings?
After some employees were caught uploading data to online personal storage accounts, a company becomes concerned about data leaks related to sensitive, internal documentation. Which of the following would the company most likely do to decrease this type of risk?
An ISAC supplied recent threat intelligence information about pictures used on social media that provide reconnaissance of systems in use in secure facilities. In response, the Chief Information Security Officer (CISO) wants several configuration changes implemented via the MDM to ensure the following:
• Camera functions and location services are blocked for corporate mobile devices.
• All social media is blocked on the corporate and guest wireless networks.
Which of the following is the CISO practicing to safeguard against the threat?
Which of the following is the main reason quantum computing advancements are leading companies and countries to deploy new encryption algorithms?
The material finding from a recent compliance audit indicate a company has an issue with excessive permissions. The findings show that employees changing roles or departments results in privilege creep. Which of the following solutions are the best ways to mitigate this issue? (Select two).
Setting different access controls defined by business area
A security analyst is reviewing the following log:
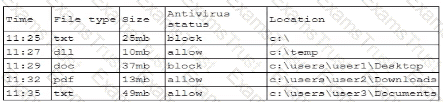
Which of the following possible events should the security analyst investigate further?
A company wants to perform threat modeling on an internally developed, business-critical application. The Chief Information Security Officer (CISO) is most concerned that the application should maintain 99.999% availability and authorized users should only be able to gain access to data they are explicitly authorized to view. Which of the following threat-modeling frameworks directly addresses the CISO's concerns about this system?
A security administrator needs to automate alerting. The server generates structured log files that need to be parsed to determine whether an alarm has been triggered Given the following code function:
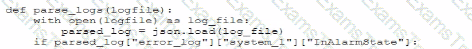
Which of the following is most likely the log input that the code will parse?
A)

B)

C)
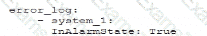
D)
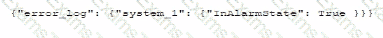
After discovering that an employee is using a personal laptop to access highly confidential data, a systems administrator must secure the company's data. Which of the following capabilities best addresses this situation?
A security engineer is assisting a DevOps team that has the following requirements for container images:
Ensure container images are hashed and use version controls.
Ensure container images are up to date and scanned for vulnerabilities.
Which of the following should the security engineer do to meet these requirements?
A company implements an Al model that handles sensitive and personally identifiable information. Which of the following threats is most likely the company's primary concern?
A company plans to deploy a new online application that provides video training for its customers. As part of the design, the application must be:
• Fast for all users
• Available for users worldwide
• Protected against attacks
Which of the following are the best components the company should use to meet these requirements? (Select two).
A security engineer wants to enhance the security posture of end-user systems in a Zero Trust environment. Given the following requirements:
. Reduce the ability for potentially compromised endpoints to contact command-and-control infrastructure.
. Track the requests that the malware makes to the IPs.
. Avoid the download of additional payloads.
Which of the following should the engineer deploy to meet these requirements?
A security review revealed that not all of the client proxy traffic is being captured. Which of the following architectural changes best enables the capture of traffic for analysis?
A systems administrator works with engineers to process and address vulnerabilities as a result of continuous scanning activities. The primary challenge faced by the administrator is differentiating between valid and invalid findings. Which of the following would the systems administrator most likely verify is properly configured?
A financial services organization is using Al lo fully automate the process of deciding client loan rates Which of the following should the organization be most concerned about from a privacy perspective?
An organization must provide access to its internal system data. The organization requires that this access complies with the following:
Access must be automated.
Data confidentiality must be preserved.
Access must be authenticated.
Data must be preprocessed before it is retrieved.
Which of the following actions should the organization take to meet these requirements?
A financial technology firm works collaboratively with business partners in the industry to share threat intelligence within a central platform This collaboration gives partner organizations the ability to obtain and share data associated with emerging threats from a variety of adversaries Which of the following should the organization most likely leverage to facilitate this activity? (Select two).
While performing threat-hunting functions, an analyst is using the Diamond Model of Intrusion Analysis. The analyst identifies the likely adversary, the infrastructure involved, and the target. Which of the following must the threat hunter document to use the model effectively?
A company developed a new solution that needs to track any changes to the data, and the changes need to be quickly identified. If any changes are attempted without prior approval, multiple events must be triggered, such as:
Raising alerts
Blocking the unapproved changes
Quickly removing access to the data
Which of the following solutions best meets these requirements?
An organization is implementing advanced security controls associated with the execution of software applications on corporate endpoints. The organization must implement a deny-all, permit-by-exception approach to software authorization for all systems regardless of OS. Which of the following should be implemented to meet these requirements?
A security operations analyst is reviewing network traffic baselines for nightly database backups. Given the following information:
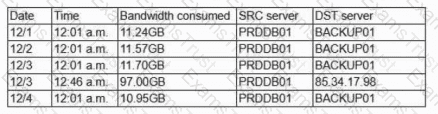
Which of the following should the security analyst do next?
A company is preparing to move a new version of a web application to production. No issues were reported during security scanning or quality assurance in the CI/CD pipeline. Which of the following actions should thecompany take next?
A security analyst is performing threat modeling for a new AI chatbot. The AI chatbot will be rolled out to help customers develop configuration information within the company's SaaS offering. Which of the following issues would require involvement from the company's internal legal team?
A company finds logs with modified time stamps when compared to other systems. The security team decides to improve logging and auditing for incident response. Which of the following should the team do to best accomplish this goal?
A company’s internal network is experiencing a security breach, and the threat actor is still active. Due to business requirements, users in this environment are allowed to utilize multiple machines at the same time. Given the following log snippet:
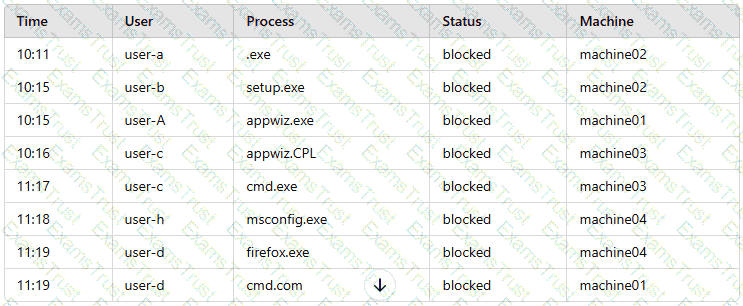
Which of the following accounts should a security analyst disable to best contain the incident without impacting valid users?
A security engineer is reviewing the following vulnerability scan report:
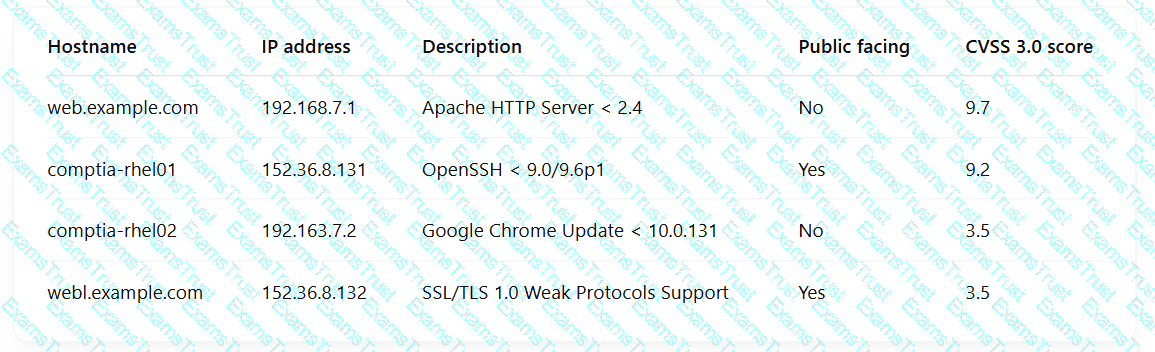
Which of the following should the engineer prioritize for remediation?
Employees use their badges to track the number of hours they work. The badge readers cannot be upgraded due to facility constraints. The software for the badge readers uses a legacy platform and requires connectivity to the enterprise resource planning solution. Which of the following is the best to ensure the security of the badge readers?
A security analyst is reviewing the following code in the public repository for potential risk concerns:
typescript
CopyEdit
include bouncycastle-1.4.jar;
include jquery-2.0.2.jar;
public static void main() {...}
public static void territory() { ... }
public static void state() { ... }
public static String code = "init";
public static String access_token = "spat-hfeiw-sogur-werdb-werib";
Which of the following should the security analyst recommend first to remediate the vulnerability?
A company lined an email service provider called my-email.com to deliver company emails. The company stalled having several issues during the migration. A security engineer is troubleshooting and observes the following configuration snippet:
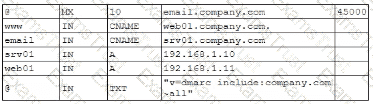
Which of the following should the security engineer modify to fix the issue? (Select two).
A Chief Information Security Officer (CISO) is concerned that a company's current data disposal procedures could result in data remanence. The company uses only SSDs. Which of the following would be the most secure way to dispose of the SSDs given the CISO's concern?
A company hosts a platform-as-a-service solution with a web-based front end, through which customer interact with data sets. A security administrator needs to deploy controls to prevent application-focused attacks. Which of the following most directly supports the administrator's objective'
After a cybersecurity incident, a security analyst was able to collect a binary that the attacker used on the compromised server. Then the analyst ran the following command:
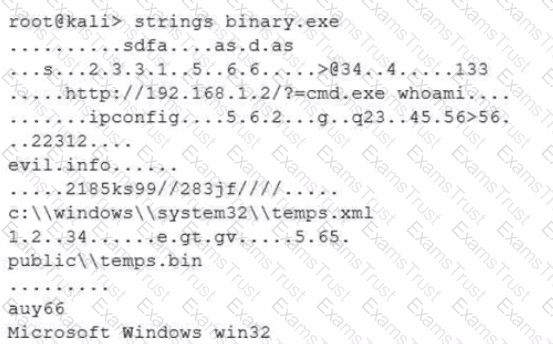
Which of the following options describes what the analyst is trying to do?
Previously intercepted communications must remain secure even if a current encryption key is compromised in the future. Which of the following best supports this requirement?
A company's help desk is experiencing a large number of calls from the finance department slating access issues to www bank com The security operations center reviewed the following security logs:
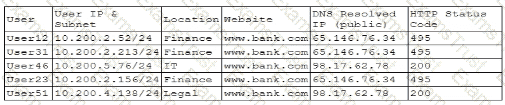
Which of the following is most likely the cause of the issue?
A company detects suspicious activity associated with external connections Security detection tools are unable tocategorize this activity. Which of the following is the best solution to help the company overcome this challenge?
Which of the following best describes a common use case for homomorphic encryption?
After an incident response exercise, a security administrator reviews the following table:
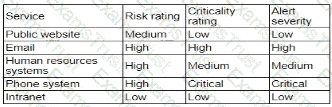
Which of the following should the administrator do to beat support rapid incident response in the future?
A developer receives feedback about code quality and efficiency. The developer needs to identify and resolve the following coding issues before submitting the code changes for peer review:
Indexing beyond arrays
Dereferencing null pointers
Potentially dangerous data type combinations
Unreachable code
Non-portable constructs
Which of the following would be most appropriate for the developer to use in this situation?
An incident response team is analyzing malware and observes the following:
• Does not execute in a sandbox
• No network loCs
• No publicly known hash match
• No process injection method detected
Which of thefollowing should the team do next to proceed with further analysis?
An analyst has prepared several possible solutions to a successful attack on the company. The solutions need to be implemented with the least amount of downtime. Which of the following should the analyst perform?
An enterprise is deploying APIs that utilize a private key and a public key to ensure the connection string is protected. To connect to the API, customers must use the private key. Which of the following would best secure the REST API connection to the database while preventing the use of a hard-coded string in the request string?
Which of the following key management practices ensures that an encryption key is maintained within the organization?
A user tried to access a web page at Previously the web page did not require authentication, and now the browser is prompting for credentials. Which of the following actions would best prevent the issue from reoccurring and reduce the likelihood of credential exposure?
Emails that the marketing department is sending to customers are going to the customers' spam folders. The security team is investigating the issue and discovers that the certificates used by the email server were reissued, but DNS records had not been updated. Which of the following should the security team update in order to fix this issue? (Select three).
A manufacturing plant is updating its IT services. During discussions, the senior management team created the following list of considerations:
• Staff turnover is high and seasonal.
• Extreme conditions often damage endpoints.
• Losses from downtime must be minimized.
• Regulatory data retention requirements exist.
Which of the following best addresses the considerations?
A security analyst wants to use lessons learned from a poor incident response to reduce dwell lime in the future The analyst is using the following data points
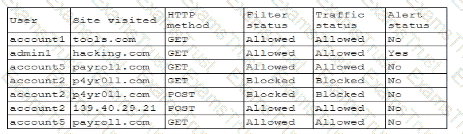
Which of the following would the analyst most likely recommend?
An engineering team determines the cost to mitigate certain risks is higher than the asset values The team must ensure the risks are prioritized appropriately. Which of the following is the best way to address the issue?
A security analyst Detected unusual network traffic related to program updating processes The analyst collected artifacts from compromised user workstations. The discovered artifacts were binary files with the same name as existing, valid binaries but. with different hashes which of the following solutions would most likely prevent this situation from reoccurring?
A security engineer reviews an after action report from a previous security breach and notes a long lag time between detection and containment of a compromised account. The engineer suggests using SOAR to address this concern. Which of the following best explains the engineer's goal?
A company sells a security appliance assembled from globally sourced hardware and software components. Installing the security appliance requires enabling administrative permissions for the service accounts on the appliance. Which of the following allows the company to reassure new and existing customers that the risk introduced by the appliance is minimal?
After a penetration test on the internal network, the following report was generated:
Attack Target Result
Compromised host ADMIN01S.CORP.LOCAL Successful
Hash collected KRBTGT.CORP.LOCAL Successful
Hash collected SQLSV.CORP.LOCAL Successful
Pass the hash SQLSV.CORP.LOCAL Failed
Domain control CORP.LOCAL Successful
Which of the following should be recommended to remediate the attack?
Company A acquired Company B. During an audit, a security engineer found Company B's environment was inadequately patched. In response, Company A placed a firewall between the two environments until Company B's infrastructure could be integrated into Company A's security program. Which of the following risk-handling techniques was used?
During a recentsecurity event, access from thenon-production environment to the production environmentenabledunauthorized usersto:
Installunapproved software
Makeunplanned configuration changes
During theinvestigation, the following findings were identified:
Several new users were added in bulkby theIAM team
Additionalfirewalls and routerswere recently added
Vulnerability assessmentshave been disabled formore than 30 days
Theapplication allow listhas not been modified intwo weeks
Logs were unavailablefor various types of traffic
Endpoints have not been patchedinover ten days
Which of the following actions would most likely need to be taken toensure proper monitoring?(Select two)
An organization recently implemented a new email DLP solution. Emails sent from company email addresses to matching personal email addresses generated a large number of alerts, but the content of the emails did not include company data. The security team needs to reduce the number of emails sent without blocking all emails to common personal email services. Which of the following should the security team implement first?
A company that uses containers to run its applications is required to identify vulnerabilities on every container image in a private repository The security team needs to be able to quickly evaluate whether to respond to a given vulnerability Which of the following, will allow the security team to achieve the objective with the last effort?
A company wants to protect against the most common attacks and rapidly integrate with different programming languages. Which of the following technologies is most likely to meet this need?
During a forensic review of a cybersecurity incident, a security engineer collected a portion of the payload used by an attacker on a comprised web server Given the following portion of the code:
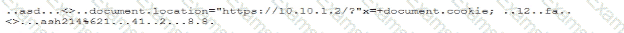
Which of the following best describes this incident?
A cloud engineer needs to identify appropriate solutions to:
• Provide secure access to internal and external cloud resources.
• Eliminate split-tunnel traffic flows.
•Enable identity and access management capabilities.
Which of the following solutions arc the most appropriate? (Select two).
A Chief Information Security Officer requests an action plan to remediate vulnerabilities. A security analyst reviews the output from a recent vulnerability scan and notices hundreds of unique vulnerabilities. The output includes the CVSS score, IP address, hostname, and the list of vulnerabilities. The analyst determines more information is needed in order to decide which vulnerabilities should be fixed immediately. Which of the following is the best source for this information?
A security architect is mitigating a vulnerability that previously led to a web application data breach. An analysis into the root cause of the issue finds the following:
An administrator’s account was hijacked and used on several Autonomous System Numbers within 30 minutes.
All administrators use named accounts that require multifactor authentication.
Single sign-on is used for all company applications.Which of the following should the security architect do to mitigate the issue?