You have been asked to design a high-density wireless network for a university campus. Which two principles would you apply in order to maximize the wireless network capacity? (Choose two.)
Company ABC uses IPv4-only. Recently they started deploying new endpoint devices. For operational reasons, IPv6 cannot be disabled on these new endpoint devices. Which security measure prevents the new endpoint from learning an IPv6 prefix from an attacker?
A small organization of 20 employees is looking to deliver a network design service for modernizing customer networks to support advanced solutions.
Project scope and weekly progress should be visualized by the management.
Always consider feedback and make changes accordingly during the project.
Should consider flexibility to change scope at any point in time.
Which project methodology meets the requirements and has the least impact on the outcome?
You are designing the QoS policy for a company that is running many TCP-based applications. The company is experiencing tail drops for these applications. The company wants to use a congestion avoidance technique for these applications. Which QoS strategy can be used?
A key to maintaining a highly available network is building in the appropriate redundancy to protect against failure. This redundancy is carefully balanced with the inherent complexity of redundant systems. Which design consideration is relevant for enterprise WAN use cases when it comes to resiliency?
What best describes the difference between Automation and Orchestration?
Which two actions must be taken when assessing an existing wireless network implementation for its readiness to support voice traffic? (Choose two.)
Refer to the exhibit.
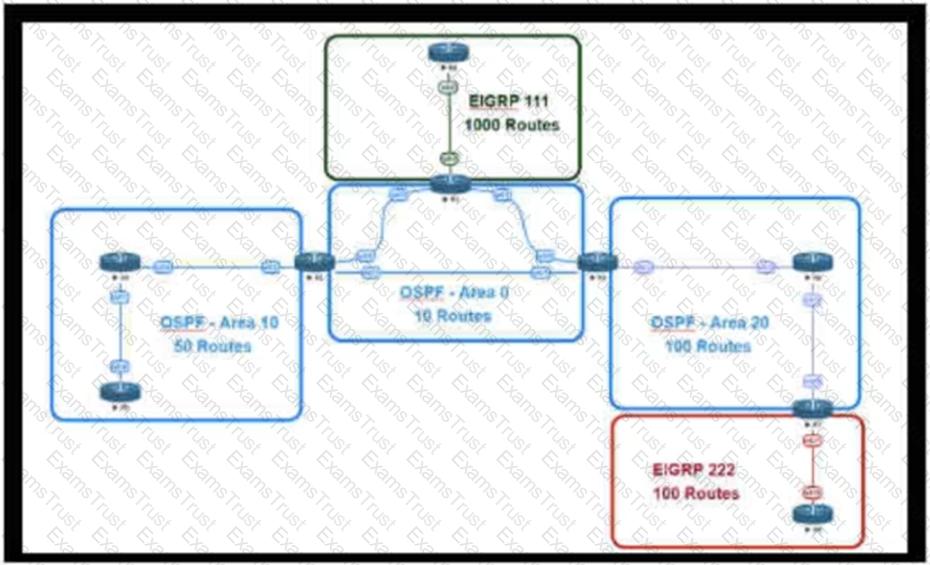
This network is running OSPF and EIGRP as the routing protocols. Mutual redistribution of the routing protocols has been configured on the appropriate ASBRs. The OSPF network must be designed so that flapping routes in EIGRP domains do not affect the SPF runs within OSPF. The design solution must not affect the way EIGRP routes are propagated into the EIGRP domains. Which technique accomplishes the requirement?
Various teams in different organizations within an enterprise are preparing low-level design documents using a Waterfall project model. Input from relevant stakeholders was captured at the start of the project, and the scope has been defined. What impact will it have if stakeholders ask for changes before documentation is complete?
A healthcare provider discovers that protected health information of patients was altered without patient consent. The healthcare provider is subject to HIPAA compliance and is required to protect PHI data. Which type of security safeguard should be implemented to resolve this issue?
A customer migrates from a traditional Layer 2 data center network into a new SDN-based spine-and-leaf VXLAN EVPN data center within the same location. The networks are joined to enable host migration at Layer 2. What is the final migration step after hosts have physically migrated to have traffic flowing through the new network without changing any host configuration?
An enterprise wants to provide low-cost delivery of network systems that can be scaled on business demand, followed by an initiative to reduce capital expenses for new IT equipment. Which technology meets these goals?
In an OSPF network with routers connected together with Ethernet cabling, which topology typically takes the longest to converge?
Which two design options are available to dynamically discover the RP in an IPv6 multicast network? (Choose two)
Refer to the exhibit.
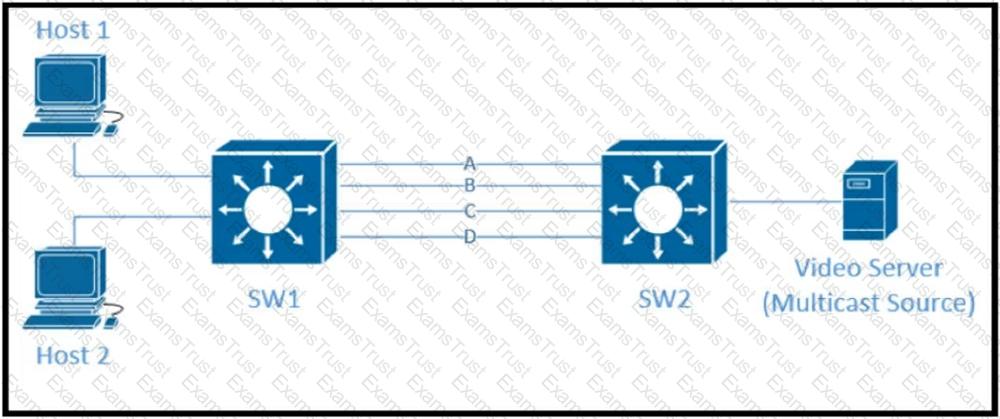
Traffic was equally balanced between Layer 3 links on core switches SW1 and SW2 before an introduction of the new video server in the network. This video server uses multicast to send video streams to hosts and now one of the links between core switches is overutilized. Which design solution solves this issue?
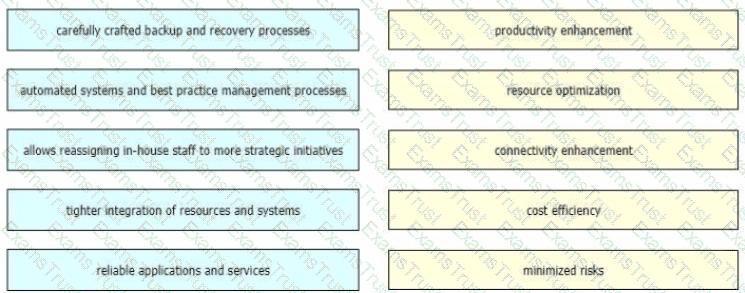
As technologies such as big data, cloud, and loT continue to grow, so will the demand for network bandwidth Business strategies must be flexible to accommodate these changes when it comes to priorities and direction and the network design strategy also must be agile and adaptable Drag and drop the benefits from the left onto the corresponding strategic approaches on the right as they relate to network design and management.
Which three Cisco products are used in conjunction with Red Hat to provide an NFVi solution? (Choose three.)
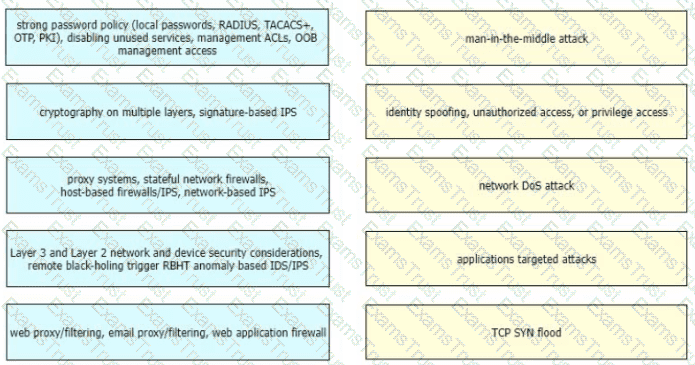
Drag and drop the correct mitigation methods from the left onto the corresponding types of attack on the right
Cost is often one of the motivators for a business to migrate from a traditional network to a software-defined network. Which design decision is directly influenced by CAPEX drivers?
Retef to the exhibit.
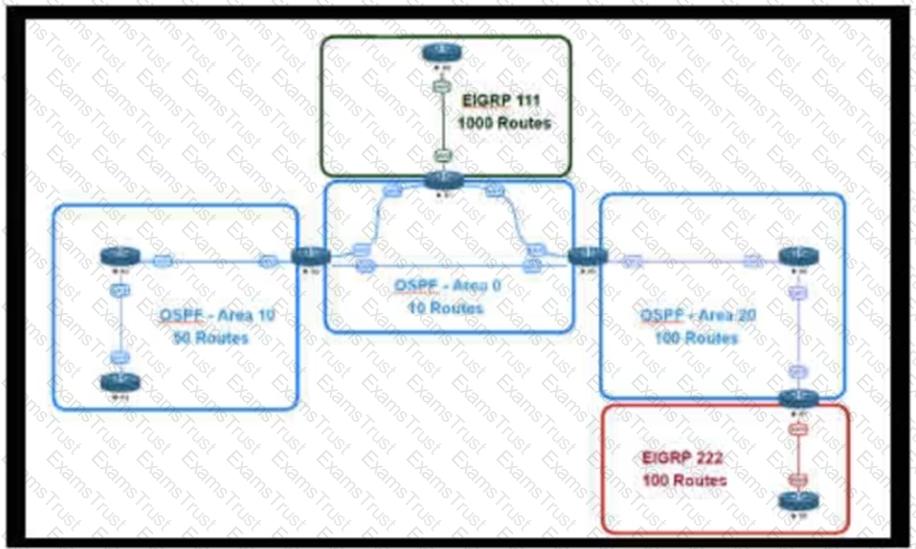
An engineer is designing a multiarea OSPF network for a client who also has a large EIGRP domain. EIGRP routes are getting redistributed into OSPF. OSPF area 20 has routers with limited memory and CPU resources. The engineer wants to block routes from EIGRP 111 from propagating into area 20 and allow EIGRP 222 routes to flow in. Which OSPF area type fulfills this design requirement?
Refer to the table.
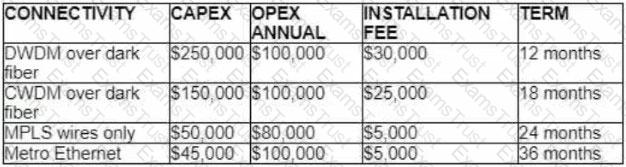
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The solution must provide a single 10G connection between locations and be able to run its own varying QoS profiles without service provider interaction based on the migration stages. All connectivity methods are at 10 Gbps. Which transport technology costs the least if the connectivity is required for just one year?
Which two statements about MLD snooping are true? (Choose two)
Which two design solutions ensure sub-50 msec of the convergence time after a link failure in the network? (Choose two)
A European national bank considers migrating its on-premises systems to a private cloud offering in a non-European location to significantly reduce IT costs. What is a primary factor prior to migration?
Which two application requirements are mandatory for traffic to receive proper treatment when placed in the priority queue? (Choose two.)
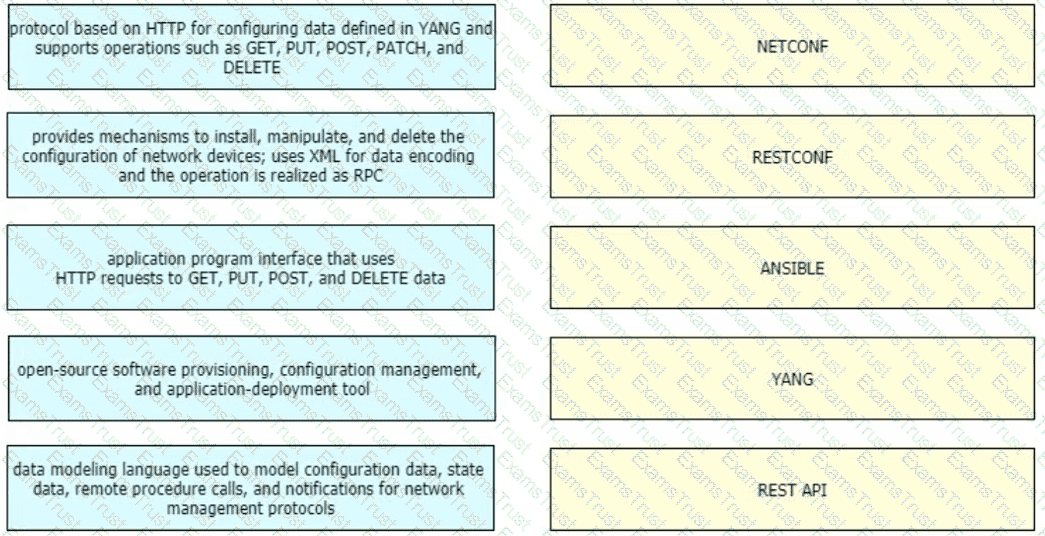
Which feature is supported by NETCONF but is not supported by SNMP?
Refer to the exhibit.
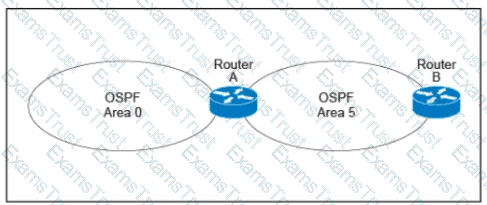
A customer runs OSPF with Area 5 between its aggregation router and an internal router. When a network change occurs in the backbone, Area 5 starts having connectivity issues due to the SPF algorithm recalculating an abnormal number of times in Area 5. You are tasked to redesign this network to increase resiliency on the customer network with the caveat that Router B does not support the stub area. How can you accomplish this task?
What are two examples of components that are part of an SDN architecture? (Choose two.)
An architect designs a multi-controller network architecture with these requirements:
Achieve fast failover to control traffic when controllers fail.
Yield a short distance and high resiliency in the connection between the switches and the controller.
Reduce connectivity loss and enable smart recovery to improve the SDN survivability.
Improve connectivity by adding path diversity and capacity awareness for controllers.
Which control plane component of the multi-controller must be built to meet the requirements?
Refer to the table.
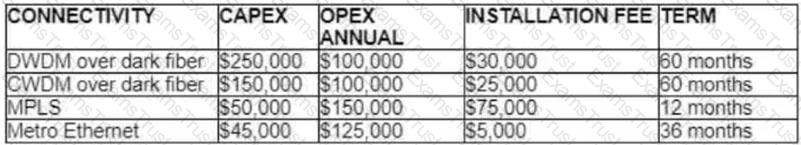
A customer investigates connectivity options for a DCI between two production data centers. The solution must provide dual 10G connections between locations with no single points of failure for Day 1 operations. It must also include an option to scale for up to 20 resilient connections in the second year to accommodate isolated SAN over IP and isolated, dedicated replication IP circuits. All connectivity methods are duplex 10 Gbps. Which transport technology costs the least over two years, in the scenario?
The controller has a global view of the network, and it can easily ensure that the network is in a consistent and optimal configuration. Which two statements describe a centralized SDN control path? (Choose two.)
Sometimes SDN leverages various overlay networking technologies to create layer(s) of network abstraction. What describes an overlay network?
A network security team uses a purpose-built tool to actively monitor the campus network, applications, and user activity. The team also analyzes enterprise telemetry data from IPFIX data records that are received from devices in the campus network. Which action can be taken based on the augmented data?
The Company XYZ network is experiencing attacks against their router. Which type of Control Plane Protection must be used on the router to protect all control plane IP traffic that is destined directly for one of the router interfaces?
What is an architectural framework created by ETSI that defines standards to decouple network functions from proprietary hardware-based appliances and have them run in software on standard x86 servers?
You are designing an Out of Band Cisco Network Admission Control Layer 3 Real-IP Gateway deployment for a customer. Which VLAN must be trunked back to the Clean Access Server from the access switch?
You were tasked to enhance the security of a network with these characteristics:
A pool of servers is accessed by numerous data centers and remote sites
The servers are accessed via a cluster of firewalls
The firewalls are configured properly and are not dropping traffic
The firewalls occasionally cause asymmetric routing of traffic within the server data center.
Which technology should you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers?
Which undesired effect of increasing the jitter compensation buffer is true?
A business wants to centralize services via VDI technology and to replace remote WAN desktop PCs with thin client-type machines to reduce operating costs. Which consideration supports the new business requirement?
Which three items do you recommend for control plane hardening of an infrastructure device? (Choose three.)
Which three tools are used for ongoing monitoring and maintenance of a voice and video environment? (Choose three.)
A banking customer determines that it is operating POS and POI terminals that are noncompliant with PCI DSS requirements, as it is running TLSv1.0. The customer plans to migrate the terminals to TLSv1.2. What are two requirements to complete the migration? (Choose two.)
Which effect of using ingress filtering to prevent spoofed addresses on a network design is true?
Which two types of planning approaches are used to develop business-driven network designs and to facilitate the design decisions? (Choose two)
Which main IoT migration aspect should be reviewed for a manufacturing plant?
If the desire is to connect virtual network functions together to accommodate different types of network service connectivity, what must be deployed?
A network engineering team is in the process of designing a lab network for a customer demonstration. The design engineer wants to show that the resiliency of the MPLS Traffic Engineering Fast Reroute solution has the same failover/failback times as a traditional SONET/SDH network (around 50 msec). In order to address both link failure and node failure within the lab topology network, which type of the MPLS TE tunnels must be considered for this demonstration?
You are designing a large-scale DMVPN network with more than 500 spokes using EIGRP as the IGP protocol. Which design option eliminates potential tunnel down events on the spoke routers due to the holding time expiration?
Company XYZ asks for design recommendations for Layer 2 redundancy. The company wants to prioritize fast convergence and resiliency elements. In the design, which two technologies are recommended? (Choose two.)
A multinational enterprise integrates a cloud solution with these objectives:
• Achieve seamless connectivity across different countries and regions
• Extend data center and private clouds into public clouds and provider-hosted clouds
What are two outcomes of deploying data centers and fabrics that interconnect different cloud networks? (Choose two.)
Which best practice ensures data security in the private cloud?
Company XYZ wants to prevent switch loops caused by unidirectional point-to-point link conditions on Rapid PVST+ and MST. Which technology can be used in the design to meet this requirement?
A company uses equipment from multiple vendors in a data center fabric to deliver SDN, enable maximum flexibility, and provide the best return on investment. Which YANG data model should be adopted for comprehensive features to simplify and streamline automation for the SDN fabric?
Which two features are advantages of SD-WAN compared to MPLS-based connectivity? (Choose two.)
The CIA triad is foundational to information security, and one can be certain that one or more of the principles within the CIA triad has been violated when data is leaked or a system is attacked Drag and drop the countermeasures on the left to the appropriate principle section on the right in any order
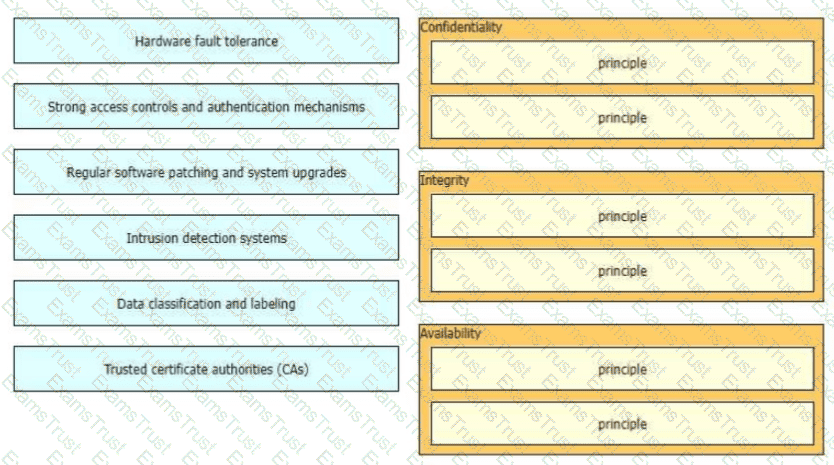
Which design principle improves network resiliency?
As network designer, which option is your main concern with regards to virtualizing multiple network zones into a single hardware device?
Which two actions must merchants do to be compliant with the Payment Card Industry Data Security Standard (PCI DSS)? (Choose two.)
Refer to the exhibit.
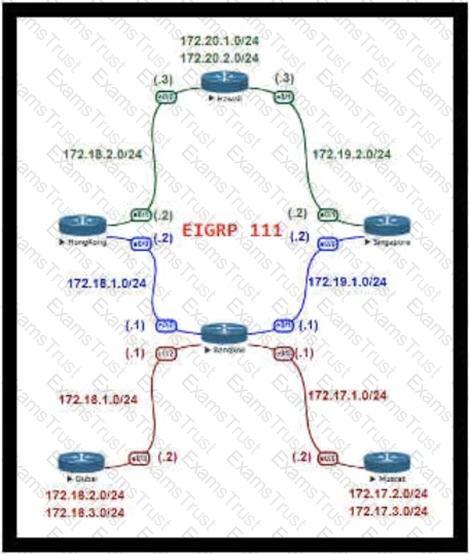
For Company XYZ, Bangkok is using ECMP to reach the 172.20.2.0/24 network. The company wants a design that would allow them to forward traffic from 172.16.2.0/24 toward 172.20.2.0/24 via the Singapore router as the preferred route. The rest of the traffic should continue to use ECMP. Which technology fulfills this design requirement?
What are two examples of business goals to be considered when a network design is built? (Choose two.)
Refer to the table.
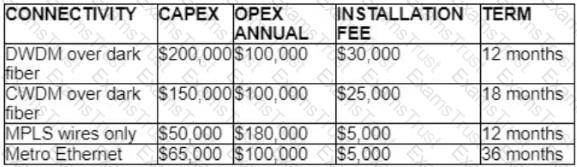
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The migration is estimated to take 20 months to complete but might extend an additional 10 months if issues arise. All connectivity options meet the requirements to migrate workloads. Which transport technology provides the best ROI based on cost and flexibility?
Company XYZ connects its sites over a private WAN. Their overlay network is running a DMVPN setup where the headquarters site is the hub. The company is planning on implementing multicast routing on the network. What should be used in the multicast routing design?
Which development model is closely associated with traditional project management?
Company XYZ has a multicast domain that spans across multiple autonomous systems. The company wants a simplified and controlled approach to interconnecting multicast domains. Which technology is the best fit?
A green data center is being deployed and a design requirement is to be able to readily scale server virtualization. Which IETF standard technology can provide this requirement?
In a redundant hub-and-spoke design with inter-spoke links, load oscillation and routing instability occur due to overload conditions. Which two design changes improve resiliency? (Choose two)
A network design includes a long signaling delay in notifying the Layer 3 control plane that an interface has failed. Which two of these actions would reduce that delay? (Choose two.)
When planning their cloud migration journey, what is crucial for virtually all organizations to perform?
When consumers that leverage IaaS reach 100% resource capacity, what can be used to redirect the overflow of traffic to the public cloud so there is no disruption to service?
Which three elements help network designers to construct secure systems that protect information and resources (such as devices, communication, and data) from unauthorized access, modification, inspection, or destruction? (Choose three.)
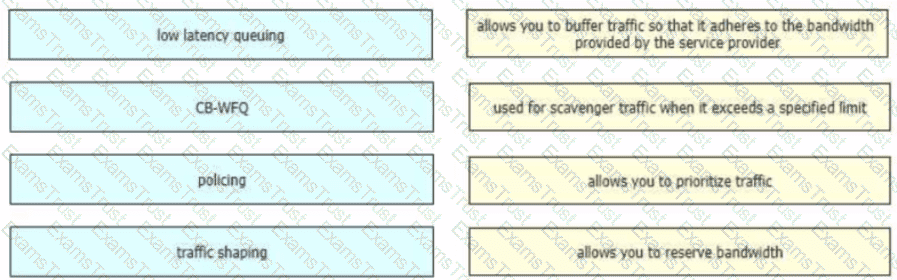
Drag and drop the QoS technologies from the left onto the correct capabilities on the right
Which two foundational aspects of IoT are still evolving and being worked on by the industry at large? (Choose two)
Which protocol does an SD-Access wireless Access Point use for its fabric data plane?
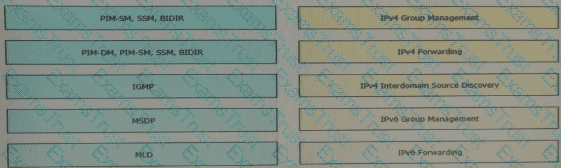
Drag and drop the multicast protocols from the left onto the current design situation on the right.
Company XYZ is running a redundant private WAN network using OSPF as the underlay protocol. The current design accommodates for redundancy in the network, but it is taking over 30 seconds for the network to reconverge upon failure. Which technique can be implemented in the design to detect such a failure in a subsecond?
A multicast network is using Bidirectional PIM. Which two combined actions achieve high availability so that two RPs within the same network can act in a redundant manner? (Choose two)
Company XYZ is migrating their existing network to IPv6. Some access layer switches do not support IPv6, while core and distribution switches fully support unicast and multicast routing. The company wants to minimize cost of the migration. Which migration strategy should be used?
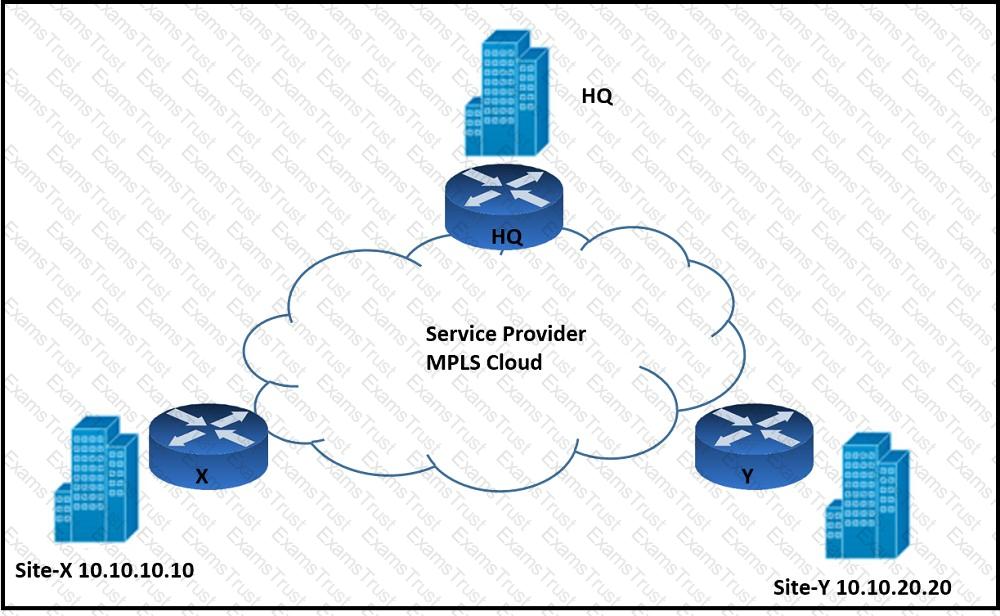
Refer to the exhibit. An architect must design an enterprise WAN that connects the headquarters with 22 branch offices. The number of remote sites is expected to triple in the next three years. The final solution must comply with these requirements:
Only the loopback address of each of the enterprise CE X and Y routers must be advertised to the interconnecting service provider cloud network.
The transport layer must carry the VPNv4 label and VPN payload over the MP-BGP control plane.
The transport layer must not be under service provider control.
Which enterprise WAN transport virtualization technique meets the requirements?
Refer to the exhibit.
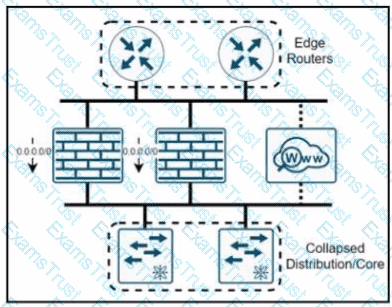
A company named XYZ needs to apply security policies for end-user browsing by installing a secure web proxy appliance. All the web traffic must be inspected by the appliance, and the remaining traffic must be inspected by an NGFW that has been upgraded with intrusion prevention system functionality. In which two ways must the routing be performed? (Choose two)
Backups and mirror copies of data are part of RPO (Recovery Point Objective) strategies. If a business wants to reduce their CAPEX for disaster recovery, which solution is most applicable?
A business customer deploys workloads in the public cloud but now faces governance issues related to IT traffic flow and data security. Which action helps identify the issue for further resolution?
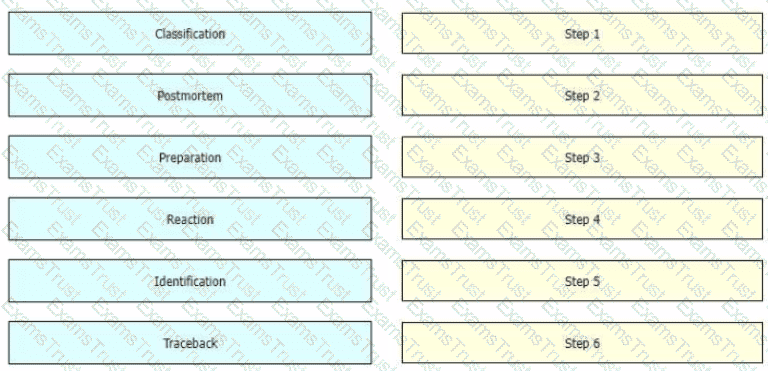
While computer networks and sophisticated applications have allowed individuals to be more productive the need to prepare for security threats has increased dramatically A six-step methodology on security incident handling has been adopted by many organizations including service providers enterprises, and government organizations to ensure that organizations are aware of significant security incidents and act quickly to stop the attacker, minimize damage caused, and prevent follow on attacks or similar incidents in the future Drag and drop the actions on the left to the targets on the right in the correct order.
Company XYZ wants to use the FCAPS ISO standard for network management design, focusing on minimizing outages through detection, isolation, and corrective actions. Which layer accomplishes this design requirement?
Which three components are part of the foundational information security principles of the CIA triad? (Choose three.)
According to the CIA triad principles for network security design, which principle should be priority for a Zero Trust network?
Company XYZ has two routing domains (EIGRP and OSPF). They want full reachability and need OSPF to see link costs added to external routes. How must redistribution be designed?
You want to split an Ethernet domain in two.
Which parameter must be unique in this design to keep the two domains separated?
Refer to the exhibit.
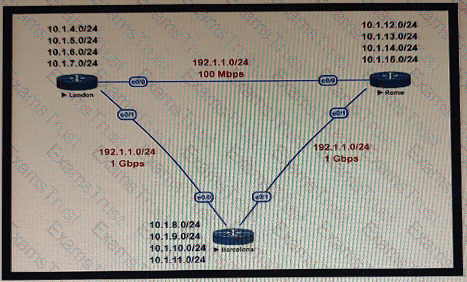
This network is running OSPF as the routing protocol. The internal networks are being advertised in OSPF. London and Rome are using the direct link to reach each other although the transfer rates are better via Barcelona. Which OSPF design change allows OSPF to calculate the proper costs?
Which network management framework can be used to develop a network architecture that contains business requirements analysis, gap analysis, and network diagrams as artifacts to be used for design and implementation later?
Refer to the exhibit.
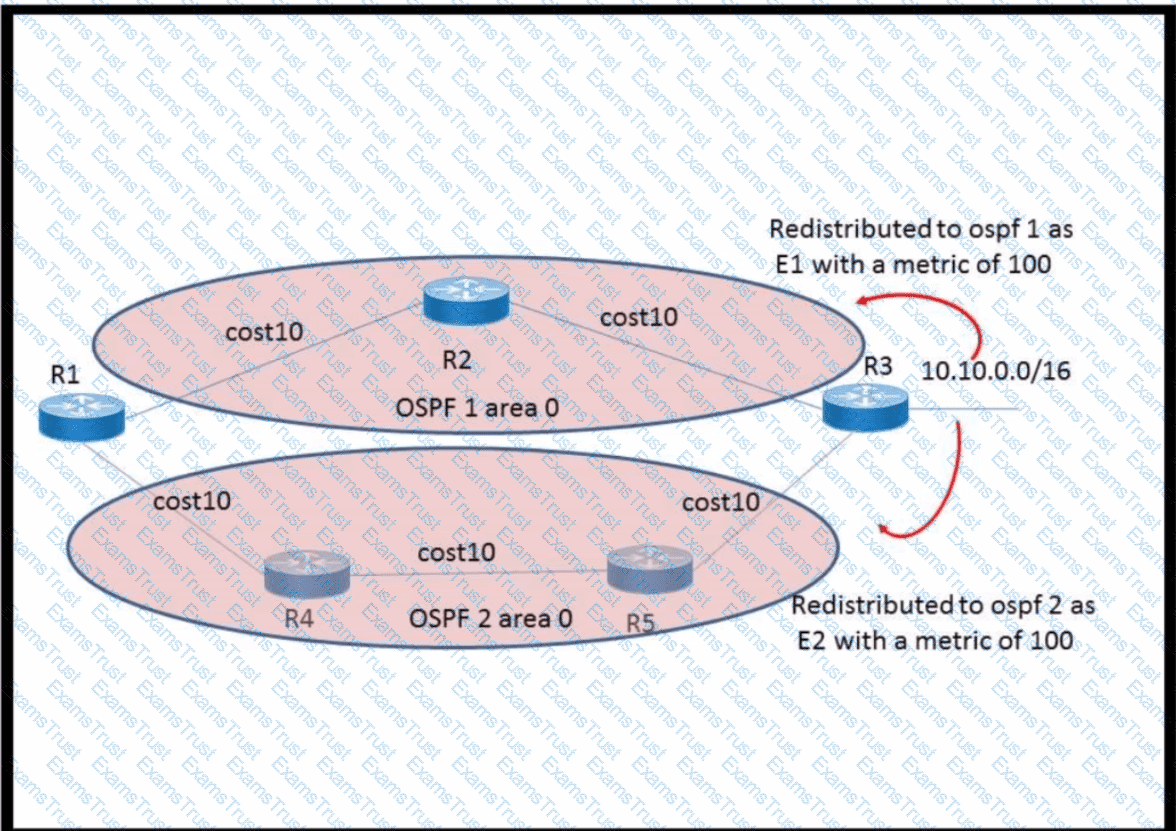
The network 10.10.0.0/16 has been redistributed to OSPF processes and the best path to the destination from R1 has been chosen as R1–R2–R3. A failure occurred on the link between R2 and R3 and the path was changed to R1–R4–R5–R3. What happens when the link between R2 and R3 is restored?
Which two features control multicast traffic in a VLAN environment? (Choose two)
Company XYZ is running BGP as their routing protocol. An external design consultant recommends that TCP Path MTU Discovery be enabled. Which effect will this have on the network?
QUESTION 69 Refer to the exhibit. AJI links are P2P Layer 3. A high availability application is synchronizing data between host A and host B. To increase chance of delivery the same data is sent twice from host A on two different NICs toward the two NICs on host B.
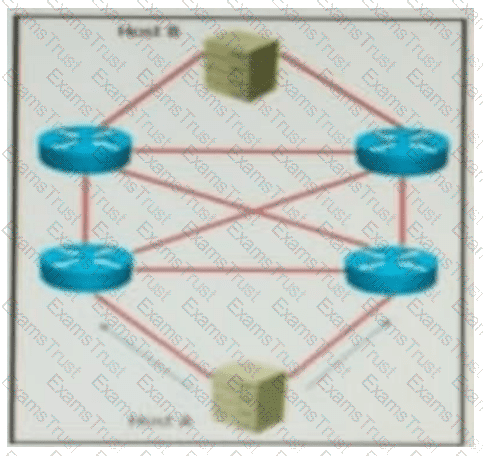
Refer to the exhibit. All links are P2P Layer 3. A high availability application is synchronizing data between Host A and Host B. To increase the chance of delivery, the same data is sent twice from Host A on two different NICs toward the two NICs on Host B.
Which solution must be deployed in the network to ensure that any failure in the network does not trigger data loss on Host B?
Which design benefit of bridge assurance is true?
You want to mitigate failures that are caused by STP loops that occur before UDLD detects the failure or that are caused by a device that is no longer sending BPDUs. Which mechanism do you use along with UDLD?
When designing a WAN that will be carrying real-time traffic, what are two important reasons to consider serialization delay? (Choose two.)
Drag and drop the characteristics from the left onto the corresponding network management options on the right.
You have been tasked with designing a data center interconnect as part of business continuity. You want to use FCoE over this DCI to support synchronous replication. Which two technologies allow for FCoE via lossless Ethernet or data center bridging? (Choose two.)
Which architecture does not require an explicit multicast signaling protocol, such as PIM or P2MP, to signal the multicast state hop-by-hop, but instead uses a link state protocol to advertise the multicast forwarding state?
Company XYZ is running SNMPv1 in their network and understands that it has some flaws. They want to change the security design to implement SNMPv3 in the network. Which network threat is SNMPv3 effective against?
Company XYZ is revisiting the security design for their data center because they now have a requirement to control traffic within a subnet and implement deep packet inspection. Which technology meets the updated requirements and can be incorporated into the design?
An MPLS service provider is offering a standard EoMPLS-based VPLS service to Customer A, providing Layer 2 connectivity between a central site and approximately 100 remote sites. Customer A wants to use the VPLS network to carry its internal multicast video feeds which are sourced at the central site and consist of 20 groups at Mbps each. Which service provider recommendation offers the most scalability?
Which two factors must be considered for high availability in campus LAN designs to mitigate concerns about unavailability of network resources? (Choose two.)
An architect prepares a network design for a startup company. The design must meet business requirements while the business grows and divests due to rapidly changing markets. What is the highest priority in this design?