Which role is a default guest type in Cisco ISE?
Which characteristic is unique to a Cisco WSAv as compared to a physical appliance?
Which two application layer preprocessors are used by Firepower Next Generation Intrusion Prevention
System? (Choose two)
What does the Cloudlock Apps Firewall do to mitigate security concerns from an application perspective?
How does Cisco Umbrella archive logs to an enterprise owned storage?
Which algorithm is an NGE hash function?
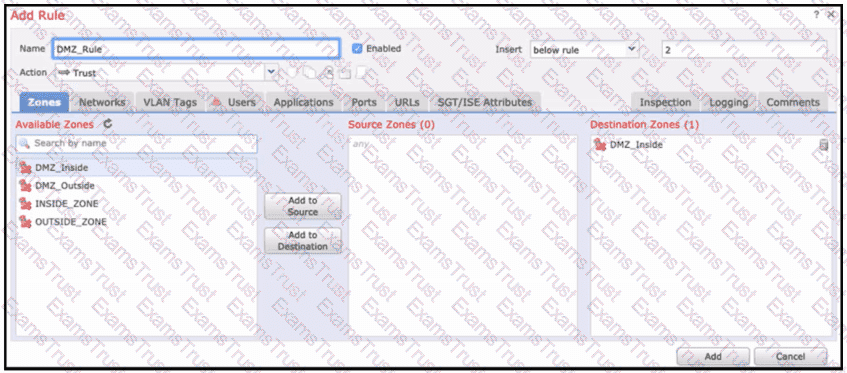
Refer to the exhibit. When configuring this access control rule in Cisco FMC, what happens with the traffic destined to the DMZ_inside zone once the configuration is deployed?
Which method must be used to connect Cisco Secure Workload to external orchestrators at a client site when the client does not allow incoming connections?
How does DNS Tunneling exfiltrate data?
Which action controls the amount of URI text that is stored in Cisco WSA logs files?
What is the purpose of the Decrypt for Application Detection feature within the WSA Decryption options?
Which attack is commonly associated with C and C++ programming languages?
What is provided by the Secure Hash Algorithm in a VPN?
In which two customer environments is the Cisco Secure Web Appliance Virtual connector traffic direction method selected? (Choose two.)
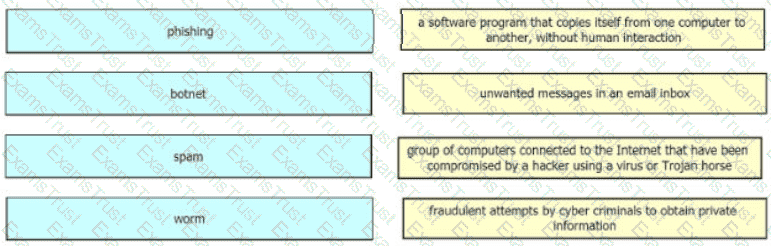
Drag and drop the common security threats from the left onto the definitions on the right.
Which Cisco Secure Client module is integrated with Splunk Enterprise to provide monitoring capabilities to administrators to allow them to view endpoint application usage?
Which solution combines Cisco IOS and IOS XE components to enable administrators to recognize
applications, collect and send network metrics to Cisco Prime and other third-party management tools, and prioritize application traffic?
How does Cisco Umbrella protect clients when they operate outside of the corporate network?
An engineer is deploying a Cisco Secure Email Gateway and must ensure it reaches the Cisco update servers to retrieve new rules. The engineer must now manually configure the Outbreak Filter rules on an AsyncOS for Cisco Secure Email Gateway. Only outdated rules must be replaced. Up-to-date rules must be retained. Which action must the engineer take next to complete the configuration?
Drag and drop the VPN functions from the left onto the descriptions on the right.
An engineer is deploying a Cisco Secure Email Gateway and must configure a sender group that decides which mail policy will process the mail. The configuration must accept incoming mails and relay the outgoing mails from the internal server. Which component must be configured to accept the connection to the listener and meet these requirements on a Cisco Secure Email Gateway?
Which two configurations must be made on Cisco ISE and on Cisco TrustSec devices to force a session to be adjusted after a policy change is made? (Choose two)
What is the difference between a vulnerability and an exploit?
A small organization needs to reduce the VPN bandwidth load on their headend Cisco ASA in order to
ensure that bandwidth is available for VPN users needing access to corporate resources on the10.0.0.0/24 local HQ network. How is this accomplished without adding additional devices to the
network?
Refer to the exhibit. Which task is the Python script performing by using the Cisco Umbrella API?
What is a benefit of using GET VPN over FlexVPN within a VPN deployment?
What is a characteristic of Firepower NGIPS inline deployment mode?
A network engineer is configuring DMVPN and entered the crypto isakmp key cisc0380739941 address 0.0.0.0 command on hostA. The tunnel is not being established to hostB. What action is needed to authenticate the VPN?
Due to a traffic storm on the network, two interfaces were error-disabled, and both interfaces sent SNMP traps.
Which two actions must be taken to ensure that interfaces are put back into service? (Choose two)
Which two authentication protocols are supported by the Cisco WSA? (Choose two.)
Which system performs compliance checks and remote wiping?
An organization has a requirement to collect full metadata information about the traffic going through their AWS cloud services They want to use this information for behavior analytics and statistics Which two actions must be taken to implement this requirement? (Choose two.)
What is the recommendation in a zero-trust model before granting access to corporate applications and
resources?
Which statement about the configuration of Cisco ASA NetFlow v9 Secure Event Logging is true?
Which Cisco Advanced Malware protection for Endpoints deployment architecture is designed to keep data
within a network perimeter?
What are two benefits of using Cisco Duo as an MFA solution? (Choose two.)
Drag and drop the Cisco CWS redirection options from the left onto the capabilities on the right.
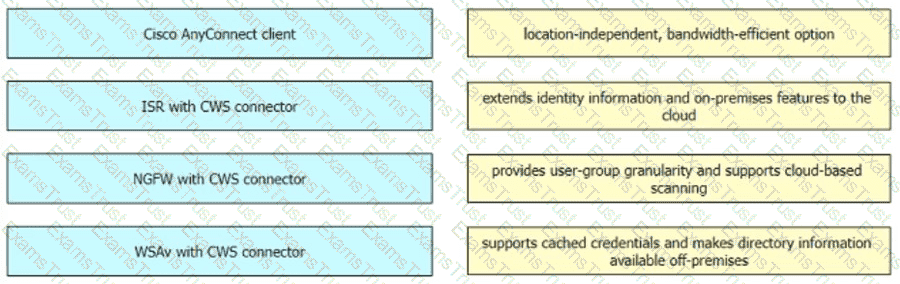
Which Cisco command enables authentication, authorization, and accounting globally so that CoA is supported on the device?
A network security engineer must export packet captures from the Cisco FMC web browser while troubleshooting an issue. When navigating to the address
What are the components of endpoint protection against social engineering attacks?
Which technology must De used to Implement secure VPN connectivity among company branches over a private IP cloud with any-to-any scalable connectivity?
A customer has various external HTTP resources available including Intranet. Extranet, and Internet, with a proxy configuration running in explicit mode Which method allows the client desktop browsers to be configured to select when to connect direct or when to use the proxy?
Which policy is used to capture host information on the Cisco Firepower Next Generation Intrusion Prevention
System?

Refer to the exhibit. An engineer must configure a new Cisco ISE backend server as a RADIUS server to provide AAA for all access requests from the client to the ISE-Frontend server.
Which Cisco ISE configuration must be used?
When using Cisco AMP for Networks which feature copies a file to the Cisco AMP cloud for analysis?
Which CLI command is used to register a Cisco FirePower sensor to Firepower Management Center?
Which security solution uses NetFlow to provide visibility across the network, data center, branch
offices, and cloud?
Which CLI command is used to enable URL filtering support for shortened URLs on the Cisco ESA?
What is an advantage of using a next-generation firewall compared to a traditional firewall?
What are two benefits of workload security? (Choose two.)
When MAB is configured for use within the 802.1X environment, an administrator must create a policy that allows the devices onto the network. Which information is used for the username and password?
Which command enables 802.1X globally on a Cisco switch?
On which part of the IT environment does DevSecOps focus?
On Cisco Firepower Management Center, which policy is used to collect health modules alerts from managed
devices?
An administrator is configuring N I P on Cisco ASA via ASDM and needs to ensure that rogue NTP servers cannot insert themselves as the authoritative time source Which two steps must be taken to accomplish this task? (Choose two)
Which two features of Cisco DNA Center are used in a Software Defined Network solution? (Choose two)
Which API method and required attribute are used to add a device into Cisco DNA Center with the native API?
Which endpoint solution protects a user from a phishing attack?
Which two deployment modes does the Cisco ASA FirePower module support? (Choose two)
How is data sent out to the attacker during a DNS tunneling attack?
A network engineer has entered the snmp-server user andy myv3 auth sha cisco priv aes 256
cisc0380739941 command and needs to send SNMP information to a host at 10.255.254.1. Which command achieves this goal?
With Cisco AMP for Endpoints, which option shows a list of all files that have been executed in your
environment?
A switch with Dynamic ARP Inspection enabled has received a spoofed ARP response on a trusted interface.
How does the switch behave in this situation?
Which two activities are performed using Cisco Catalyst Center? (Choose two.)
Which component of Cisco umbrella architecture increases reliability of the service?
What is a difference between a zone-based firewall and a Cisco Adaptive Security Appliance firewall?
Which public cloud provider supports the Cisco Next Generation Firewall Virtual?
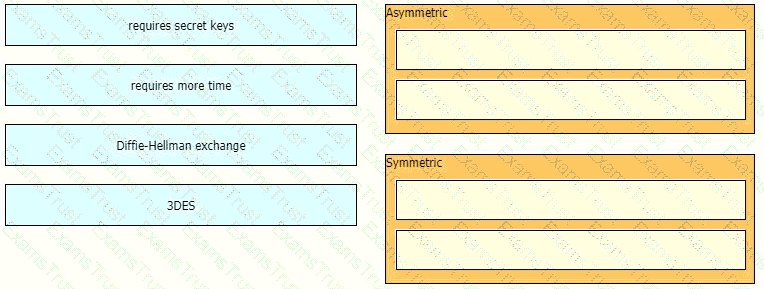
Which algorithm provides asymmetric encryption?
An engineer is configuring Cisco Secure Endpoint to enhance security by preventing the execution of certain files by users. The engineer needs to ensure that the specific executable file name Cisco_Software_0505446151.exe is blocked from running while never being quarantined. What must the engineer configure to meet the requirement?
An organization plans to upgrade its current email security solutions, and an engineer must deploy Cisco Secure Email. The requirements for the upgrade are:
Implement Data Loss Prevention
Implement mail encryption
Integrate with an existing Cisco IronPort Secure Email Gateway solution
Which Cisco Secure Email license is needed to accomplish this task?
An engineer must implement a file transfer solution between a company's data center and branches. The company has numerous servers hosted in a hybrid cloud implementation. The file transfer protocol must support authentication, protect the data against unauthorized access, and ensure that users cannot list directories or remove files remotely. Which protocol must be used?
Which Cisco security solution stops exfiltration using HTTPS?
Which type of data exfiltration technique encodes data in outbound DNS requests to specific servers
and can be stopped by Cisco Umbrella?
A user has a device in the network that is receiving too many connection requests from multiple machines.
Which type of attack is the device undergoing?
An engineer is implementing Cisco CES in an existing Microsoft Office 365 environment and must route inbound email to Cisco CE.. record must be modified to accomplish this task?
Which technology should be used to help prevent an attacker from stealing usernames and passwords of users within an organization?
Which factor must be considered when choosing the on-premise solution over the cloud-based one?
What limits communication between applications or containers on the same node?
Which two descriptions of AES encryption are true? (Choose two)
The Cisco ASA must support TLS proxy for encrypted Cisco Unified Communications traffic. Where must the
ASA be added on the Cisco UC Manager platform?
What is a benefit of an endpoint patch management strategy?
Which technology limits communication between nodes on the same network segment to individual applications?
What is the primary benefit of deploying an ESA in hybrid mode?
An engineer must modify a policy to block specific addresses using Cisco Umbrella. The policy is created already and is actively u: of the default policy elements. What else must be done to accomplish this task?
Refer to the exhibit.
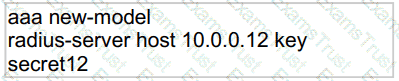
Which statement about the authentication protocol used in the configuration is true?
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
What are two security benefits of an MDM deployment? (Choose two.)
What is an attribute of the DevSecOps process?
Which two statements about a Cisco WSA configured in Transparent mode are true? (Choose two)
Which two products are used to forecast capacity needs accurately in real time? (Choose two.)
How does Cisco AMP for Endpoints provide next-generation protection?
An engineer adds a custom detection policy to a Cisco AMP deployment and encounters issues with the
configuration. The simple detection mechanism is configured, but the dashboard indicates that the hash is not 64 characters and is non-zero. What is the issue?
Which two mechanisms are used to control phishing attacks? (Choose two)
What is the benefit of integrating Cisco ISE with a MDM solution?
Which exfiltration method does an attacker use to hide and encode data inside DNS requests and queries?
II
An engineer musí set up 200 new laptops on a network and wants to prevent the users from moving their laptops around to simplify administration Which switch port MAC address security setting must be used?
Drag and drop the features of Cisco ASA with Firepower from the left onto the benefits on the right.
Which type of algorithm provides the highest level of protection against brute-force attacks?
Email security has become a high-priority task for a security engineer at a large multi-national organization due to ongoing phishing campaigns. To help control this, the engineer has deployed an Incoming Content Filter with a URL reputation of (-10.00 to -6.00) on the Cisco Secure Email Gateway. Which action will the system perform to disable any links in messages that match the filter?
An engineer is configuring web filtering for a network using Cisco Umbrella Secure Internet Gateway.
The requirement is that all traffic needs to be filtered. Using the SSL decryption feature, which type of
certificate should be presented to the end-user to accomplish this goal?
Refer to the exhibit.
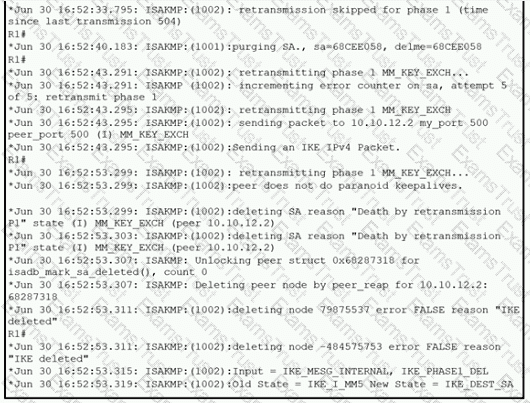
A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output?
Which feature is leveraged by advanced antimalware capabilities to be an effective endpomt protection platform?
When planning a VPN deployment, for which reason does an engineer opt for an active/active FlexVPN
configuration as opposed to DMVPN?
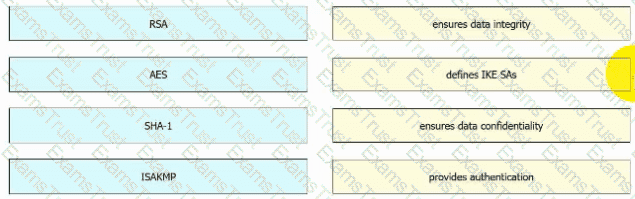
Drag and drop the descriptions from the left onto the encryption algorithms on the right.
What are two functionalities of SDN Northbound APIs? (Choose two.)
Which form of attack is launched using botnets?
What is a feature of an endpoint detection and response solution?
What is the purpose of the Trusted Automated exchange cyber threat intelligence industry standard?
Which two methods are available in Cisco Secure Web Appliance to process client requests when configured in Transparent mode? (Choose two.)
What is a benefit of using Cisco Tetration?
An engineer is configuring Dropbox integration with Cisco Cloudlock. Which action must be taken before granting API access in the Dropbox admin console?
Which two components do southbound APIs use to communicate with downstream devices? (Choose two.)
An administrator has been tasked with configuring the Cisco Secure Email Gateway to ensure there are no viruses before quarantined emails are delivered. In addition, delivery of mail from known bad mail servers must be prevented. Which two actions must be taken in order to meet these requirements? (Choose two.)
An MDM provides which two advantages to an organization with regards to device management? (Choose two)
A network engineer is deciding whether to use stateful or stateless failover when configuring two Cisco ASAs for high availability. What is the connection status in both cases?
An engineer notices traffic interruption on the network. Upon further investigation, it is learned that broadcast
packets have been flooding the network. What must be configured, based on a predefined threshold, to
address this issue?
Which function is included when Cisco AMP is added to web security?
Which command is used to log all events to a destination colector 209.165.201.107?
What are two characteristics of the RESTful architecture used within Cisco DNA Center? (Choose two.)
An organization must add new firewalls to its infrastructure and wants to use Cisco ASA or Cisco FTD.
The chosen firewalls must provide methods of blocking traffic that include offering the user the option to bypass the block for certain sites after displaying a warning page and to reset the connection. Which solution should the organization choose?
An organization has DHCP servers set up to allocate IP addresses to clients on the LAN. What must be done to ensure the LAN switches prevent malicious DHCP traffic while also distributing IP addresses to the correct endpoints?
An administrator configures a new destination list in Cisco Umbrella so that the organization can block specific domains for its devices. What should be done to ensure that all subdomains of domain.com are blocked?
Which functions of an SDN architecture require southbound APIs to enable communication?
Which process is used to obtain a certificate from a CA?
Which two global commands must the network administrator implement to limit the attack surface of an internet-facing Cisco router? (Choose two.)
What is a language format designed to exchange threat intelligence that can be transported over the TAXII
protocol?
What are the two types of managed Intercloud Fabric deployment models? (Choose two.)
What does Cisco ISE use to collect endpoint attributes that are used in profiling?
Client workstations are experiencing extremely poor response time. An engineer suspects that an attacker is eavesdropping and making independent connections while relaying messages between victims to make them think they are talking to each other over a private connection. Which feature must be enabled and configured to provide relief from this type of attack?
What are two Detection and Analytics Engines of Cognitive Threat Analytics? (Choose two)
What does Cisco AMP for Endpoints use to help an organization detect different families of malware?
What is the purpose of a denial-of-service attack?
Which encryption algorithm provides highly secure VPN communications?
Refer to the exhibit.
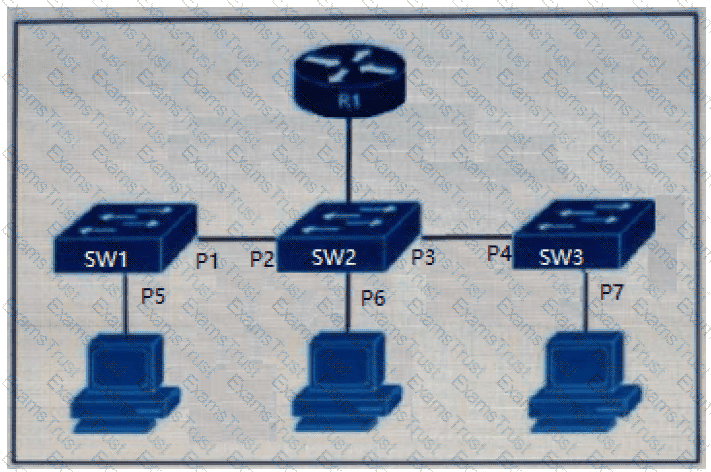
The DHCP snooping database resides on router R1, and dynamic ARP inspection is configured only on switch SW2. Which ports must be configured as untrusted so that dynamic ARP inspection operates normally?
A company identified a phishing vulnerability during a pentest What are two ways the company can protect employees from the attack? (Choose two.)
Refer to the exhibit. A network engineer must configure a Cisco router to send traps using SNMPv3. The engineer configures a remote user to receive traps and sets the security level to use authentication without privacy. Which command completes the configuration?
Which VMware platform does Cisco ACI integrate with to provide enhanced visibility, provide policy integration and deployment, and implement security policies with access lists?
Which two characteristics of messenger protocols make data exfiltration difficult to detect and prevent?
(Choose two)
An organization wants to improve its cybersecurity processes and to add intelligence to its data The organization wants to utilize the most current intelligence data for URL filtering, reputations, and vulnerability information that can be integrated with the Cisco FTD and Cisco WSA What must be done to accomplish these objectives?
Email security has become a high priority task for a security engineer at a large multi-national organization due to ongoing phishing campaigns. To help control this, the engineer has deployed an Incoming Content Filter with a URL reputation of (-10 00 to -6 00) on the Cisco ESA Which action will the system perform to disable any links in messages that match the filter?
Which Cisco security solution determines if an endpoint has the latest OS updates and patches installed on the system?
An engineer is configuring IPsec VPN and needs an authentication protocol that is reliable and supports ACK
and sequence. Which protocol accomplishes this goal?
An engineer is configuring Cisco Umbrella and has an identity that references two different policies. Which action ensures that the policy that the identity must use takes precedence over the second one?
Which Cisco AMP file disposition valid?
Which Cisco ISE feature helps to detect missing patches and helps with remediation?
What is the result of the ACME-Router(config)#login block-for 100 attempts 4 within 60 command on a Cisco IOS router?
Which interface mode does a Cisco Secure IPS device use to block suspicious traffic?
A network engineer is tasked with configuring a Cisco ISE server to implement external authentication against Active Directory. What must be considered about the authentication requirements? (Choose two.)
A network administrator needs a solution to match traffic and allow or deny the traffic based on the type of application, not just the source or destination address and port used. Which kind of security product must the network administrator implement to meet this requirement?
What are two ways a network administrator transparently identifies users using Active Directory on the Cisco WSA? (Choose two.) The eDirectory client must be installed on each client workstation.
Which Cisco security solution protects remote users against phishing attacks when they are not connected to
the VPN?
Which Talos reputation center allows you to track the reputation of IP addresses for email and web traffic?
Which two features of Cisco Email Security can protect your organization against email threats? (Choose two)
Which problem Is solved by deploying a multicontext firewall?
What Cisco command shows you the status of an 802.1X connection on interface gi0/1?
Which two preventive measures are used to control cross-site scripting? (Choose two)
Which Cisco Umbrella package supports selective proxy for Inspection of traffic from risky domains?
What is the function of SDN southbound API protocols?
Which solution stops unauthorized access to the system if a user's password is compromised?
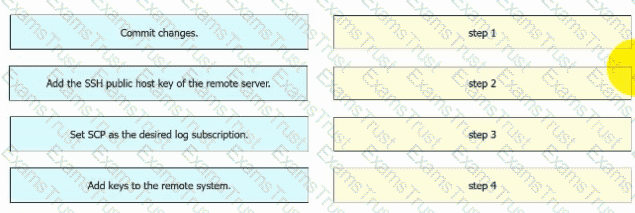
An engineer must configure AsyncOS for Cisco Secure Web Appliance to push log files to a syslog server using the SCP retrieval method. Drag and drop the steps from the left into the sequence on the right to complete the configuration.
A networking team must harden an organization's network from VLAN hopping attacks. The team disables Dynamic Trunking Protocol and puts any unused ports in an unused VLAN. A trunk port is used as a trunk link. What must the team configure next to harden the network against VLAN hopping attacks?
What are two benefits of using an MDM solution? (Choose two.)
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.
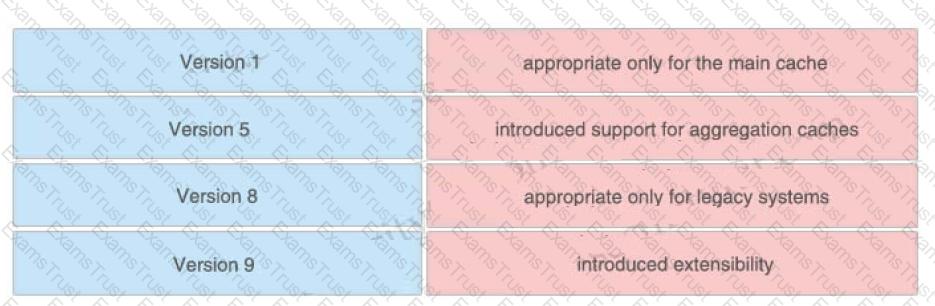
For Cisco IOS PKI, which two types of Servers are used as a distribution point for CRLs? (Choose two)
A company recently discovered an attack propagating throughout their Windows network via a file named abc428565580xyz exe The malicious file was uploaded to a Simple Custom Detection list in the AMP for Endpoints Portal and the currently applied policy for the Windows clients was updated to reference the detection list Verification testing scans on known infected systems shows that AMP for Endpoints is not detecting the presence of this file as an indicator of compromise What must be performed to ensure detection of the malicious file?
Which type of API is being used when a security application notifies a controller within a software-defined network architecture about a specific security threat?
An engineer is implementing NTP authentication within their network and has configured both the client and server devices with the command ntp authentication-key 1 md5 Cisc392368270. The server at 1.1.1.1 is attempting to authenticate to the client at 1.1.1.2, however it is unable to do so. Which command is required to enable the client to accept the server’s authentication key?
A customer has various external HTTP resources available including Intranet Extranet and Internet, with a
proxy configuration running in explicit mode. Which method allows the client desktop browsers to be configured
to select when to connect direct or when to use the proxy?
Which type of attack is MFA an effective deterrent for?
An organization is implementing AAA for their users. They need to ensure that authorization is verified for every command that is being entered by the network administrator. Which protocol must be configured in order to provide this capability?
For which type of attack is multifactor authentication an effective deterrent?
Which two actions does the Cisco ISE posture module provide that ensures endpoint security? (Choose two.)
Drag and drop the Firepower Next Generation Intrusion Prevention System detectors from the left onto the correct definitions on the right.
Which Cisco security solution integrates with cloud applications like Dropbox and Office 365 while protecting data from being exfiltrated?
Refer to the exhibit.
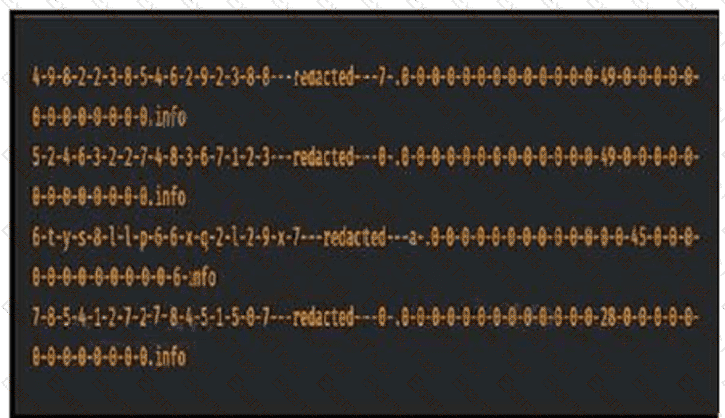
Consider that any feature of DNS requests, such as the length off the domain name
and the number of subdomains, can be used to construct models of expected behavior to which
observed values can be compared. Which type of malicious attack are these values associated with?
For which two conditions can an endpoint be checked using ISE posture assessment? (Choose two)
Refer to the exhibit,
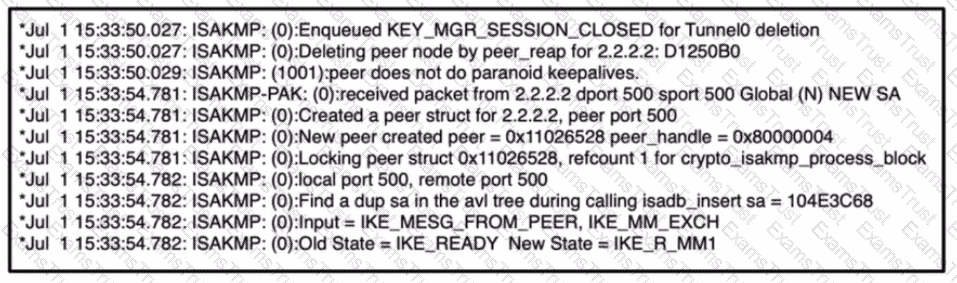
which command results in these messages when attempting to troubleshoot an iPsec VPN connection?
Which cloud model is a collaborative effort where infrastructure is shared and jointly accessed by several organizations from a specific group?
A network administrator is setting up Cisco FMC to send logs to Cisco Security Analytics and Logging (SaaS). The network administrator is anticipating a high volume of logging events from the firewalls and wants lo limit the strain on firewall resources. Which method must the administrator use to send these logs to Cisco Security Analytics and Logging?
Which risk is created when using an Internet browser to access cloud-based service?
A network administrator configures Dynamic ARP Inspection on a switch. After Dynamic ARP Inspection is applied, all users on that switch are unable to communicate with any destination. The network administrator checks the interface status of all interfaces, and there is no err-disabled interface. What is causing this problem?
Which two commands are required when configuring a flow-export action on a Cisco ASA? (Choose two.)
How does a Cisco Secure Firewall help to lower the risk of exfiltration techniques that steal customer data?
Which Secure Email Gateway implementation method segregates inbound and outbound email?
Which security solution uses NetFlow to provide visibility across the network, data center, branch offices, and cloud?
A Cisco AMP for Endpoints administrator configures a custom detection policy to add specific MD5 signatures The configuration is created in the simple detection policy section, but it does not work What is the reason for this failure?
A network administrator is using the Cisco ESA with AMP to upload files to the cloud for analysis. The network
is congested and is affecting communication. How will the Cisco ESA handle any files which need analysis?
Why is it important for the organization to have an endpoint patching strategy?
An organization is using Cisco Firepower and Cisco Meraki MX for network security and needs to centrally
manage cloud policies across these platforms. Which software should be used to accomplish this goal?
Which statement describes a serverless application?
An organization is implementing URL blocking using Cisco Umbrella. The users are able to go to some sites
but other sites are not accessible due to an error. Why is the error occurring?
Which threat involves software being used to gain unauthorized access to a computer system?
Which feature is used in a push model to allow for session identification, host reauthentication, and session termination?
When a Cisco Secure Web Appliance checks a web request, what occurs if it is unable to match a user-defined policy?
Which two are valid suppression types on a Cisco Next Generation Intrusion Prevention System? (Choose two)
Refer to the exhibit.
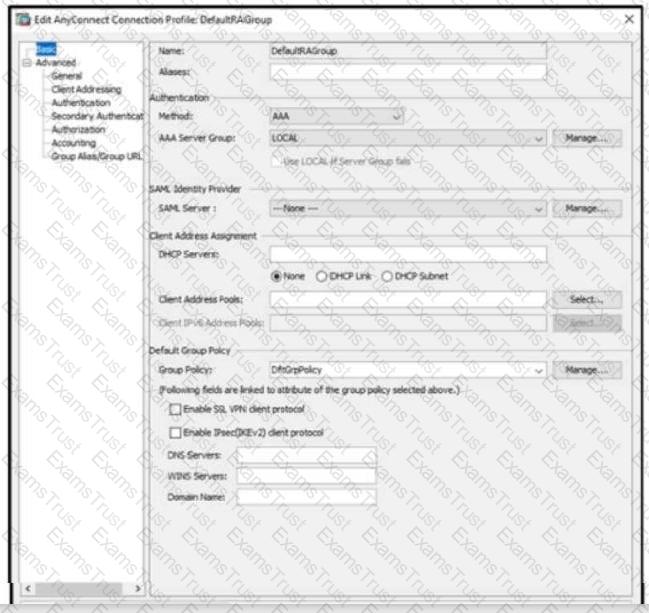
When configuring a remote access VPN solution terminating on the Cisco ASA, an administrator would like to utilize an external token authentication mechanism in conjunction with AAA authentication using machine
certificates. Which configuration item must be modified to allow this?
Which feature enables a Cisco ISR to use the default bypass list automatically for web filtering?
Which two risks is a company vulnerable to if it does not have a well-established patching solution for
endpoints? (Choose two)
An administrator is trying to determine which applications are being used in the network but does not want the
network devices to send metadata to Cisco Firepower. Which feature should be used to accomplish this?
An administrator configures a Cisco WSA to receive redirected traffic over ports 80 and 443. The organization requires that a network device with specific WSA integration capabilities be configured to send the traffic to the WSA to proxy the requests and increase visibility, while making this invisible to the users. What must be done on the Cisco WSA to support these requirements?
What is an attribute of Cisco Talos?
An engineer is configuring 802.1X authentication on Cisco switches in the network and is using CoA as a mechanism. Which port on the firewall must be opened to allow the CoA traffic to traverse the network?
Which feature requires that network telemetry be enabled?
A Cisco Secure Email Gateway network administrator has been tasked to use a newly installed service to help create policy based on the reputation verdict. During testing, it is discovered that the Secure Email Gateway is not dropping files that have an undetermined verdict. What is causing this issue?
In which type of attack does the attacker insert their machine between two hosts that are communicating with each other?
Which feature requires a network discovery policy on the Cisco Firepower Next Generation Intrusion Prevention
System?
What is a benefit of using Cisco AVC (Application Visibility and Control) for application control?
A company is experiencing exfiltration of credit card numbers that are not being stored on-premise. The
company needs to be able to protect sensitive data throughout the full environment. Which tool should be used
to accomplish this goal?
Which Cisco WSA feature supports access control using URL categories?
What is a prerequisite when integrating a Cisco ISE server and an AD domain?
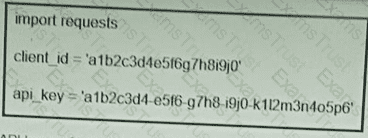
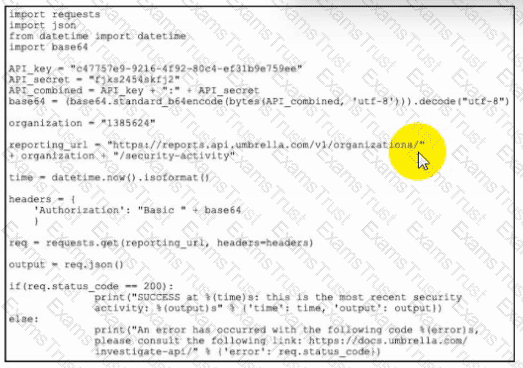
Refer to the exhibit. What function does the API key perform while working with
An engineer is trying to decide whether to use Cisco Umbrella, Cisco CloudLock, Cisco Stealthwatch, or Cisco AppDynamics Cloud Monitoring for visibility into data transfers as well as protection against data exfiltration Which solution best meets these requirements?
Which API technology with SDN architecture is used to communicate with a controller and network devices such as routers and switches?
An engineer must modify an existing remote access VPN using a Cisco AnyConnect Secure Mobility client solution and a Cisco Secure Firewall. Currently, all the traffic generate by the user Is sent to the VPN tunnel and the engineer must now exclude some servers and access them directly instead. Which element must be modified to achieve this goat?
What is a description of microsegmentation?
What is a description of microsegmentation?
With regard to RFC 5176 compliance, how many IETF attributes are supported by the RADIUS CoA feature?