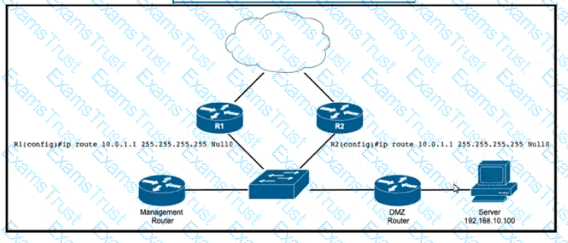

Refer to the exhibit. EIGRP a running across the core lo exchange Internal routes, and each router maintains 6GP adjacency with the other routers on the network. An operator has configured static routes on the edge routers R1 and R2 for IP address 10.0.1.1. which is used as a black hole route as shown. Which configuration should the operator Implement to me management rouler to create a route map that will redistribute lagged static routes into BGP and create a static route to blackhole traffic with tag 777 that Is destined to server at 192.168.10.100?

How do PE routers operate with the MDT in a multicast VPN?
What is the primary purpose of Secure ZTP?
Refer to the exhibit.
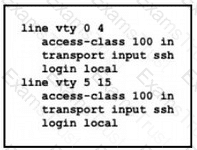
An engineer has started to configure a router for secure remote access as shown. All users who require network access need to be authenticated by the SSH Protocol.Which two actions must the engineer implement to complete the SSH configuration? (Choose two.)
A company is expanding its existing office space to a new floor of the building, and the networking team is installing a new set of switches. The new switches are running IGMPv2, and the engineers configured them for VLAN10 only. The rest of the existing network includes numerous Layer 2 switches in multiple other VLANs, all running IGMPv3. Which additional task must the team perform when deploying the new switches so that traffic is switched correctly through the entire network?
A network engineer is adding 10Gbps link to an existing 2X1Gbps LACP-based LAG to augment its capacity. Network standards require a bundle interface to be take out of service if one of its member links does down, and the new link must be added with minimal impact to the production network. Drag and drop the tasks that the engineer must perform from the left into the sequence on the right. Not all options are used.

Refer to the exhibit.

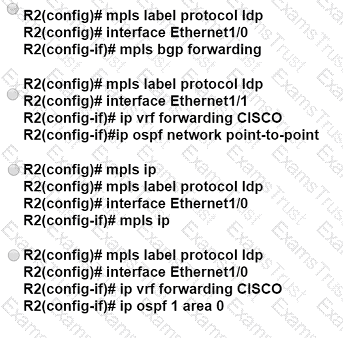
An engineer is configuring two routers to support MPLS LDP sessions between them. The R1 configuration is complete, and work has started on R2 as shown. Which additional configuration must the engineer apply to R2 to complete the task?
You are testing the capabilities of MPLS OAM ping.
Which statement is true?
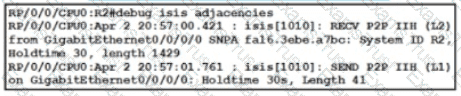
Refer to the exhibit. A network operator is attempting to configure an IS-IS adjacency between two routers, but the adjacency cannot be established. To troubleshoot the problem, the operator collects this debugging output. Which interface are misconfigured on these routers?

How is a telemetry session established for data analytics?
Which service is a VNF role?
A network team has failed to implement IS-IS multitopology. What is the reason for it?
Refer to the exhibit.

A network administrator is implementing IGMP to enable multicast feed transmission to the receiver. Which configuration must the administrator deploy on GW1 to permit IGMP Joins only to the assigned (S, G) feed?
A)
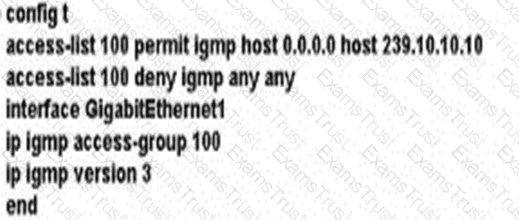
B)
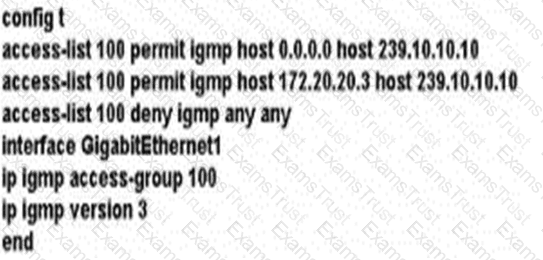
C)
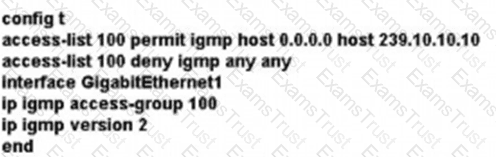
D)
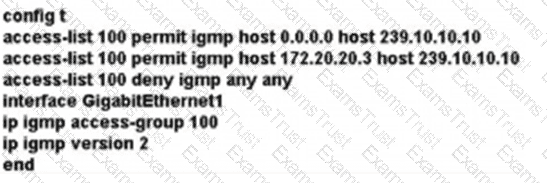
What is the difference between SNMP and model-driven telemetry?
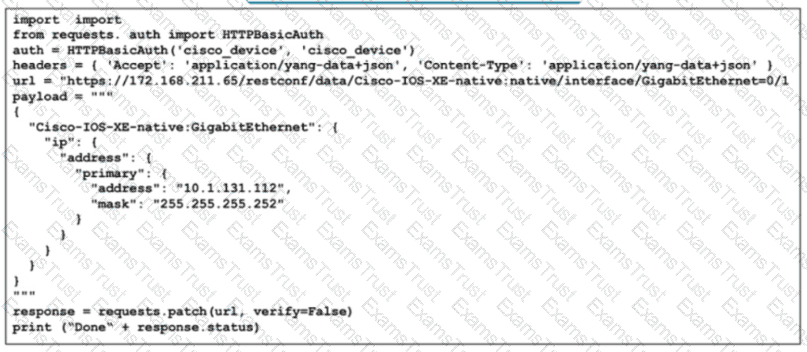
Refer for the exhibit. To optimize network operations, the senior architect created this Python 3.9 script for network automation tasks and to leverage Ansible 4.0 playbooks. Devices In the network support only RFC 2617-based authentication What does the script do?
Refer to the exhibit.

A network engineer must implement SNMPv3 on a Cisco IOS XR router running BGP. The engineer configures SNMPv3 to use SHA for authentication and AES for privacy on the routers, which are in a different data center in the same exchange as other routers. The engineer must also verify the associated MIB view family name, storage type, and status. Which set of actions meets these requirements?
Refer to the exhibit:
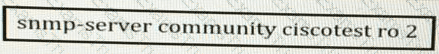
What is significant about the number 2 in the configuration?
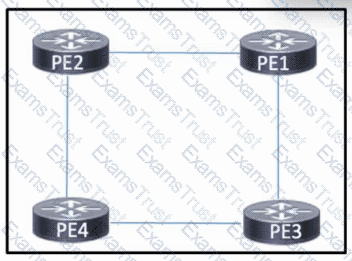
Refer to the exhibit. The four PE routers in the network are connected and running OSPF to share routes. MPLS is enabled on the four routers. The routers are connected and configured to use /30 networks. A network engineer must implement Layer 3 VPN support for traffic between customer sites.
Which task must the engineer perform?
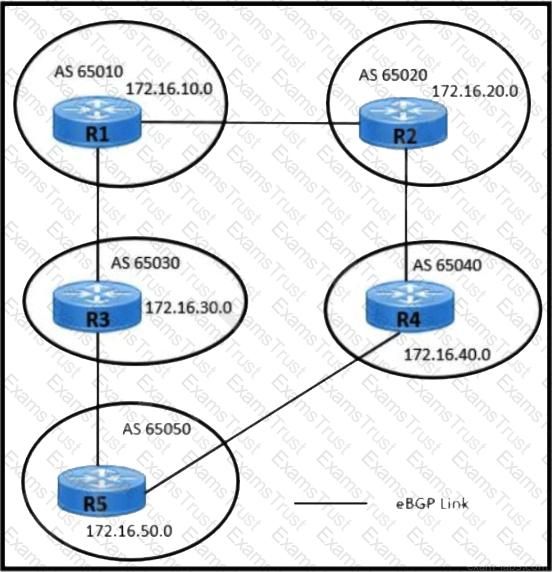
Refer to the exhibit. Users in AS 65010 are connected with the application server in AS 65050 with these requirements:
AS 65010 users are experiencing latency and congestion to connect with application server 172.16.50.10.
AS 65030 must be restricted to become Transient Autonomous System for traffic flow.
Links connected to AS 65020 and AS 65040 are underutilized and must be used efficiently for traffic.
Which two configurations must be implemented to meet these requirements? (Choose two.)
A network administrator must monitor network usage to provide optimal performance to the network end users when the network is under heavy load. The administrator asked the engineer to install a new server to receive SNMP traps at destination 192.168.1.2. Which configuration must the engineer apply so that all traps are sent to the new server?
Which feature will an operator use while implementing MPLS TE on customer's network, to prevent an LSP from using any overseas inks?
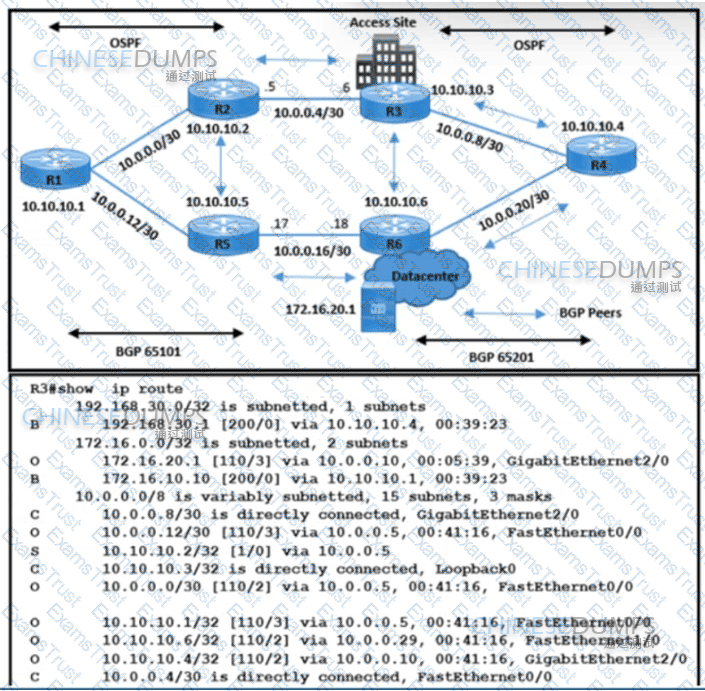
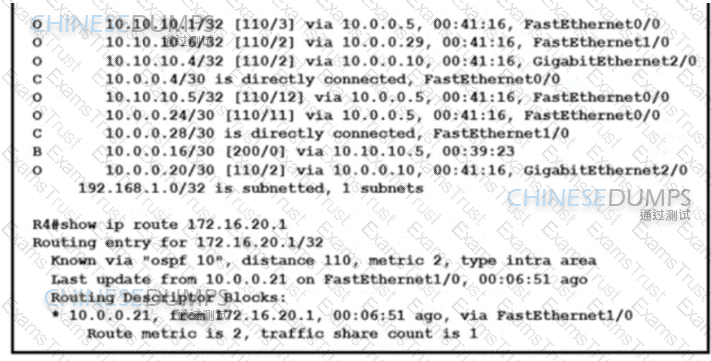
Refer to the exhibit. The network operations team reported that the access site that is connected to R3 is not connecting to the application server in the data center and that all packets that are sent from the application server to the access site are dropped. The team verified that OSPF and BGP peerings are up in BGP AS 65101 and BGP AS 65201. R4 is expected to receive traffic from the application server route via OSPF. Which action resolves this issue?
Refer to the exhibit.
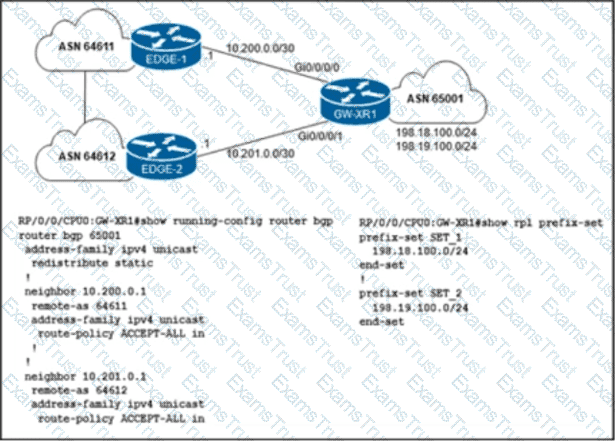
The network engineer who manages ASN 65001 must configure a BGP routing policy on GW-XR1 with these requirements:
• Advertise locally-originated routes and /24 prefixes assigned within the 198.18.0.0/15 range. All other prefixes must be dropped.
• Reachability to 198.18.100.0/24 must be preferred via the EDGE-1 connection.
• Reachability to 198.19.100.0/24 must be preferred via the EDGE-2 connection.
Which configuration must the network engineer implement on GW-XR1?
Refer to the exhibit.

An engineer implemented OSPF neighbor relationship on an IOS device. Which configuration must be applied to get the OR/BOR election removed from interfaces running OSPF?
Refer to the exhibit:

Which statement describes the effect of this configuration?

Refer to the exhibit. Customers report occasional forwarding issues from hosts connected to R6 to hosts connected to R1. A network engineer has just updated the MPLS configuration on the network, and a targeted LDP session has been established between R1 and R5. Which additional task must the engineer perform so that the team can identify the path from R6 to R1 in case the forwarding issues continue?
Company A must increase throughput between two non-IEEE 802.3ad switches located in the access and distribution layers. A network engineer must create a link group with the same speed and duplex. The STP protocol must not block any of the group ports. Which action completes the implementation?
A network operator working for a private outsourcing company with an employee id: 4261:72:778 needs to limit the malicious traffic on their network. Which configuration must the engineer use to implement URPF loose mode on the GigabitEthernet0/1 interface?
Which statement about Network Services Orchestrator (NSO) is true?
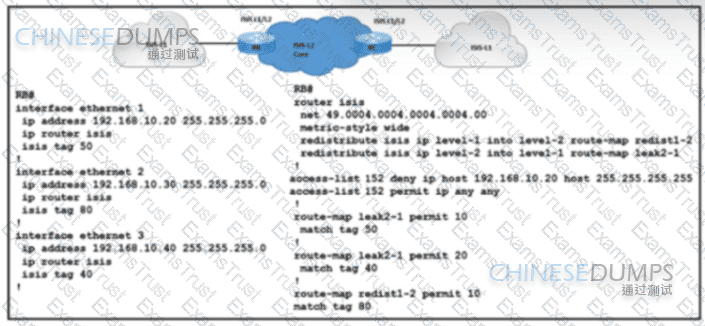
Refer to the exhibit. A network engineer with an employee ID 4379:43:595 is setting up an IS-IS network with these requirements:
Routes with a tag of 80 and IP prefixes other than 192.168.10.20/24 must be redistributed from Level 1 into Level 2.
Route leaking must be configured from Level 2 into the Level 1 domain for routes that are tagged with only 50 or 40.
Which configuration must be implemented on RB to meet the requirements?
Refer to the exhibit.
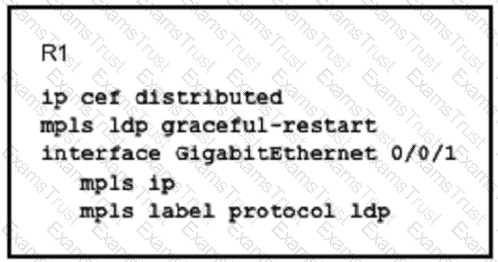
What is the effect of this configuration?
Refer to the exhibit.
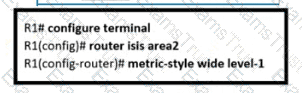
An engineer is configuring multitopology IS-IS for IPv6 on router R1. Which additional configuration must be applied to the router to complete the task?

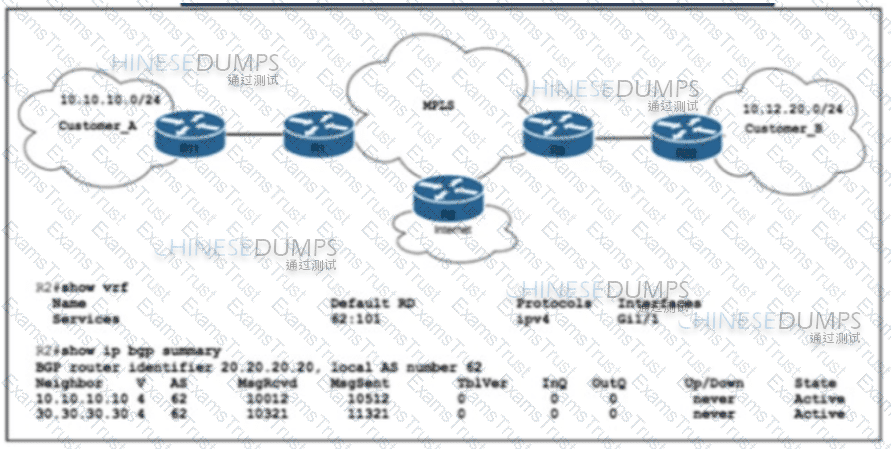
Refer to the exhibit. ISP_A is about to launch a new internet service. ISP_A is already providing MPLS VPN Layer 3 services to Customer_A and Customer_B, which are connected to ISP_A via OSPF. A network engineer completed the BGP and VRF configurations on R2 to support the new internet service. Which additional action completed the launch?
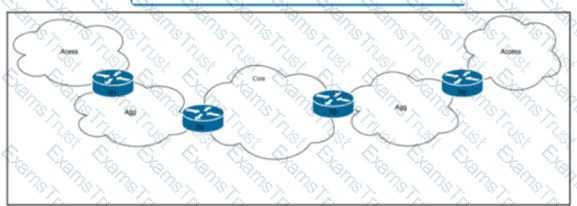
Refer to the exhibit. Tier 1 ISP A purchased several Tier 2 ISPs to increase their customer base and provide more regional coverage. ISP A plans to implement MPLS services in the access layer, with scalability up to 100.000 devices In one packet network and service recovery up to 50 ms. The network architect decided to use different independent IGP and LDP domains and interconnect LSPs that are based on RFC 3107. Which two actions must the network engineer perform to meet the requirements? (Choose two.)
Which module refers to the network automation using Ansible?
Refer to the exhibit.
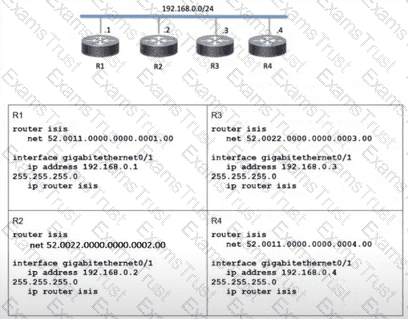
Which two topology changes happen to the IS-IS routers? (Choose two.)
What is a primary benefit of IPoATM or MPLS over ATM backbone service provider networks?
Why do Cisco MPLS TE tunnels require a link-state routing protocol?
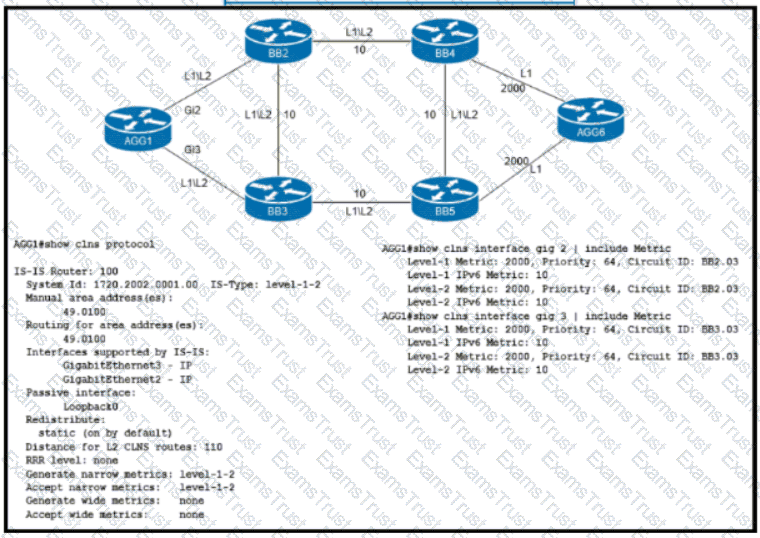
Refer to the exhibit. An engineer is configuring IS-IS on ISP network. Which IS-IS configuration must an engineer implement on router AGG1 so that it establishes connectivity to router AGG6 via the BB3 core router?
Refer to the exhibit.
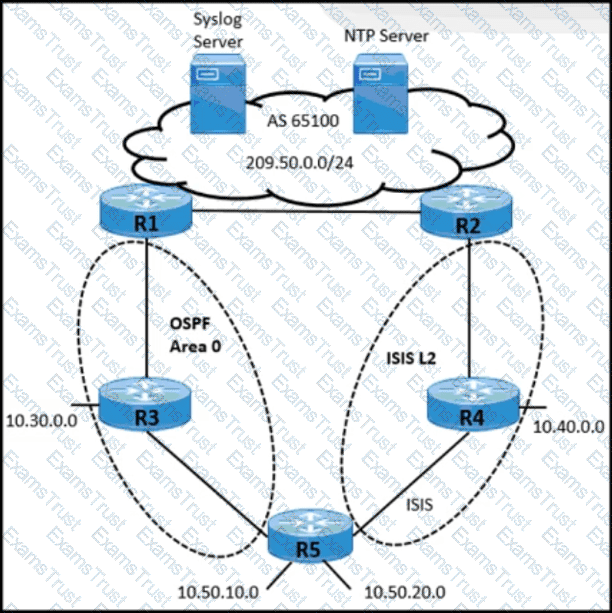
A network operator working for a telecommunication company with an employee ID: 4350:47:853 must implement an IGP solution based on these requirements:
• Subnet 10.50.10.0 traffic must exit through the R1 router to connect with the Syslog server.
• Subnet 10.50.20.0 traffic must exit through the R2 router to connect with the NTP server.
• In case of link failure between R2 and R4, traffic must be routed via R1 and R3.
Which two configurations must be implemented on R5 to meet these requirements? (Choose two.)
Refer to the exhibit.
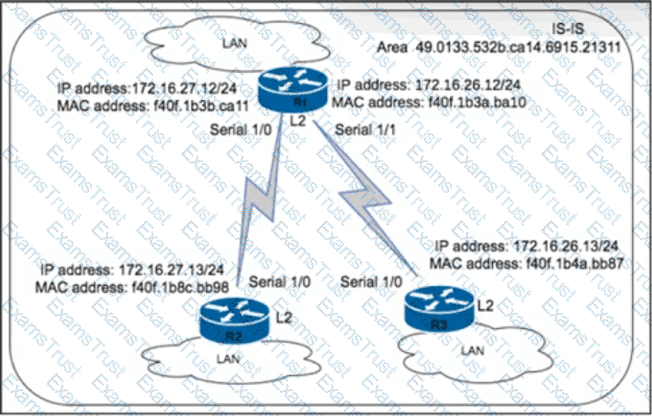
An engineer with an employee 10:4350:47:853 is implementing IS-IS as the new routing protocol in the network. All routers in the network operate as Level 2 routers in the same private autonomous system, and the three branches are connected via dark fibre. The engineer has already implemented IS-IS on router R1 with NET address 49.0133.532b.ca14.6915.21311.F40F.1B3a.ba10.00. Which IS-IS NET address configuration must be implemented on R3 to establish IS-IS connectivity?
Refer to the exhibit:

Which statement supports QPPB implementation?
What do Ansible and Salt Stack have in common?
Refer to the exhibit.
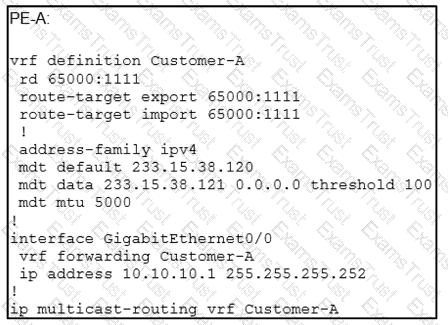
An engineer is implementing Auto-RP and reviewing the configuration of the PE-A. Which configuration permits Auto-RP messages to be forwarded over this interface?
Refer to the exhibit.
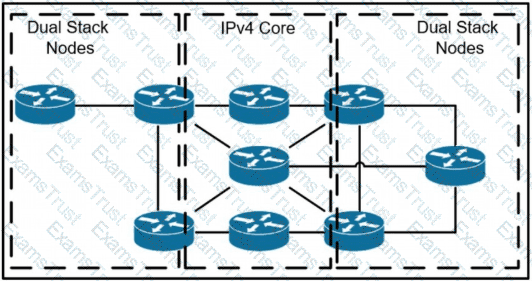
A network operator has two IPv4 and IPv6 dual-stacked network on each side of the IPv4 core network. The operator must be able to provide connectivity between them while using specific assigned IPv6 space provided from the company IP administrator team. Which technology should the network operator use to accomplish this goal?
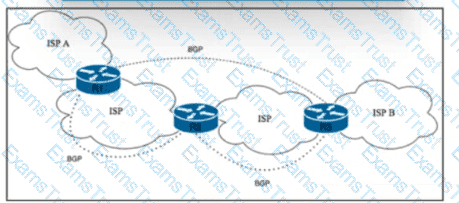
Refer to the exhibit. Tier 1 ISP A is connected to small Tier 3 ISP B. The EBGP routing protocol is used for route exchange. The networking team at ISP A noticed the flapping of BGP sessions with ISP B. The team decides to Improve stability on the network by suppressing the subnet for 30 minutes when a session begins to flap. Which action must the team perform to meet this goal?
Refer to the exhibit.
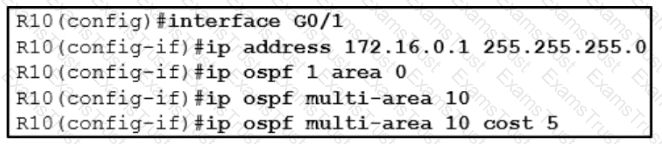
A network engineer is implementing OSPF multiarea. Which command on interface GO/1 resolves adjacency issues in the new area?
What are the two uses of the YANG data modeling language? (Choose two.)
Refer to the exhibit:

Which statement describes this configuration?
Refer to the exhibit.
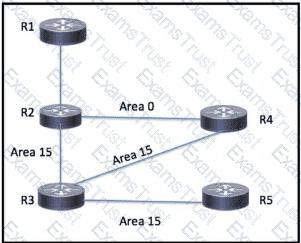
An engineer has started to configure a router for OSPF, as shown Which configuration must an engineer apply on the network so that area 15 traffic from R5 to R1 will prefer the route through R4?
What are two characteristics of MPLS TE turrets? (Choose two)
After recent network outages and customer complaints, a large Tier 1 service provider has asked a network engineer to implement MPLS OAM policy on all Provider Edge devices in the MPLS network. To improve network performance and reliability, the policy must be able to detect 2% packet drops and a delay of 0.05 seconds. The solution must be based on RFC 6374 and RFC 4379 standards for MPLS OAM. The CCM to detect connectivity issues has already been configured with interval 1000. Which two actions must the engineer take to achieve the goal? (Choose two.)
Refer to the exhibit:
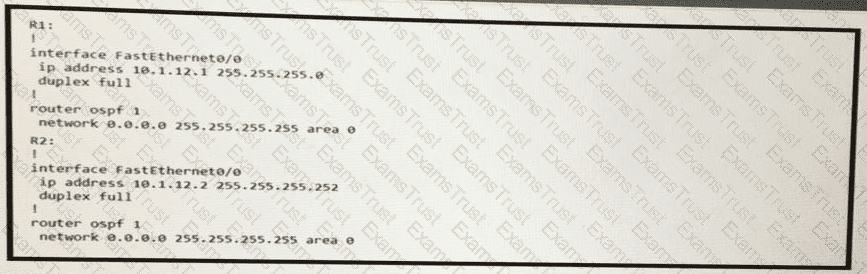
R1 and R2 are directly connected with Fast Ethernet interfaces and have the above configuration applied OSPF adjacency is not formed. When the debug ip ospf hello command is issued on R1. these log messages are seen.

Which command can be configured on routers R1 and R2 on fO/O interfaces to form OSPF adjacency?
Refer to the exhibit.
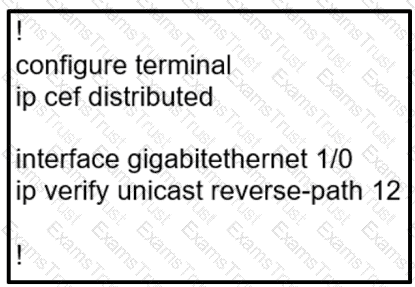
Which show command should be implemented to display per-interface statistics about uRPF drops and suppressed drops?

Refer to the exhibit. A network operator working for a private telecommunication company with an employee id: 7138: 13:414 just added new users to the network, which resides in VLANs connected to routers R1 and R4. The engineer now must configure the network so that routers R1 and R4 share routes to the VLANs, but routers R2 and R3 are prevented from including the routes in their routing tables. Which configuration must the engineer apply to R4 to begin implementing the request?
Simulation 5
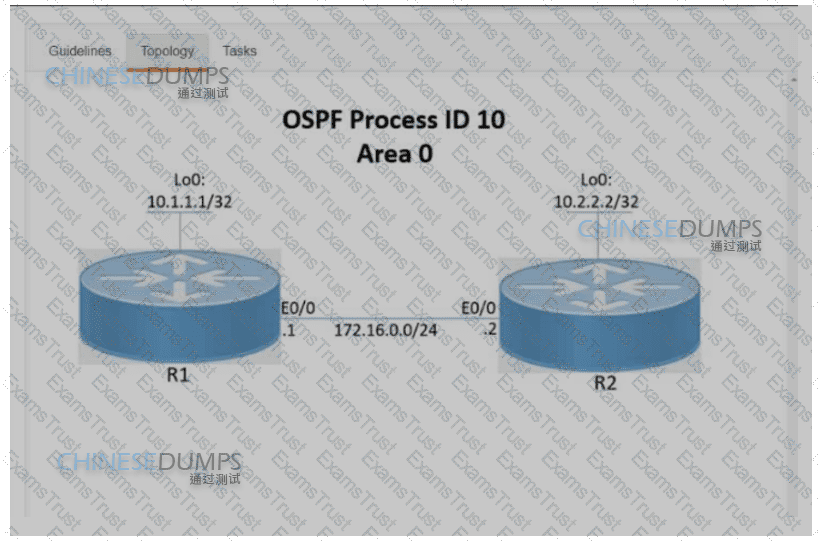

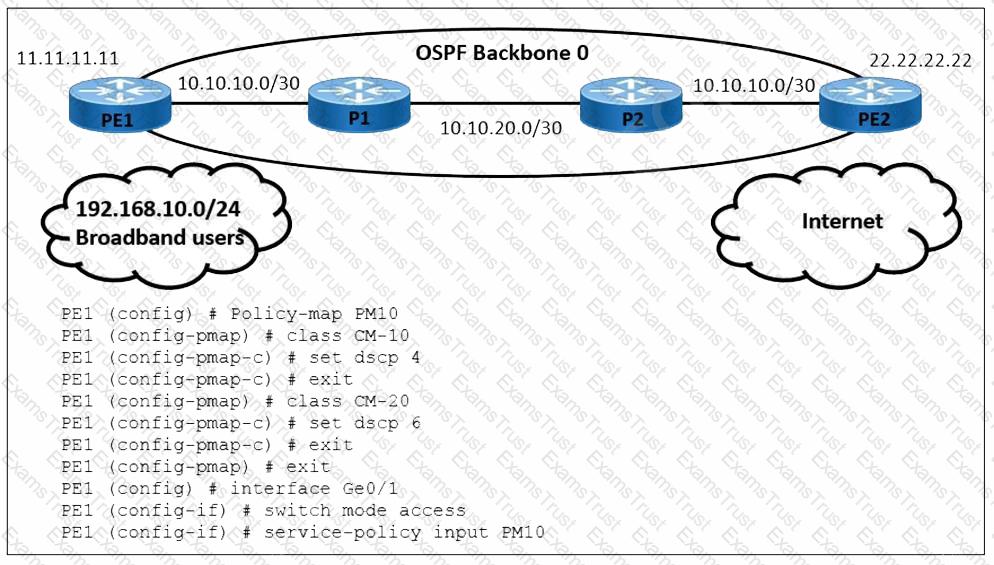
Refer to the exhibit A user is performing QoS marking on internet traffic and sending it with IPv4 and IPv6 headers on the provider edge device PE1. IPv4 traffic is classified with DSCP 4 and IPv6 traffic is classified with DSCP 6. Which action must the engineer take to begin implementing a QoS configuration on PE1 for the IPv6 traffic?
How does SR policy operate in Segment Routing Traffic Engineering?
A network operator working for a telecommunication company with an employee Id: 4065 96080 it trying to implement BFD configuration on an existing network of Cisco devices Which task must the engineer perform to enable BFD on the interfaces?
How can shared services in an MPLS Layer 3 VPN provide Internet access to the customers of a central service provider?
A network engineer must enable multicast on the network to support a new series of webcasts. The PIM protocol has been enabled on the LAN side, with PIM and MSDP capabilities on edge router R1. The multicast source has been configured with IP address FF3A:121, and IP protocol 58 has been enabled and successfully tested in the network. Due to the limitations of some devices on the network, the data flow should take the most efficient path.
Which task must the engineer perform to achieve the goal?
Which function does orchestrated fulfillment perform under the Cisco Network Services Orchestrator model?
In an EVPN operation, how does the PE determine and advertise Ethernet segment reachability?
Refer to the exhibit.
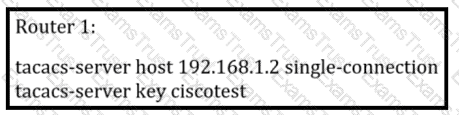
What is the result of this configuration?
An engineer is trying to implement BGP in a multihomed architecture. What must the engineer configure to influence inbound path selection?
An engineer working for telecommunication company with an employee id: 3715 15 021 needs to secure the LAN network using a prefix list Which best practice should the engineer follow when he implements a prefix list?
Refer to the exhibit.
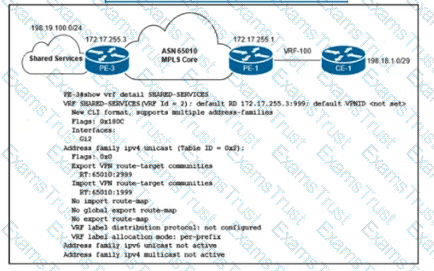
Refer to the exhibit. An ISP provides shared VoIP Extranet services to a customer in VRF-100 with these settings:
The VoIP services are hosted in the 198.19.100.0/24 space.
The customer has been assigned the 198.18.1.0/29 IP address block.
VRF-100 is assigned import and export route target 65010:100.
Which configuration must the engineer apply to PE-1 to provision VRF-100 and provide access to the shared services?
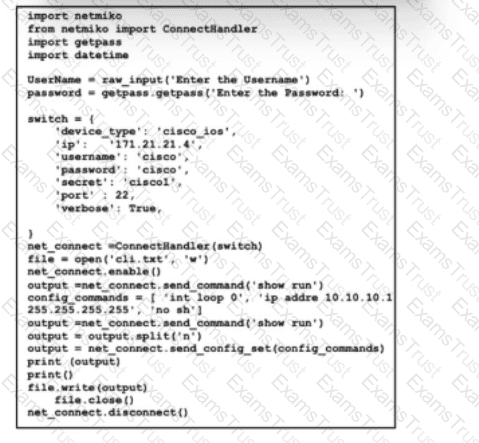
Refer to the exhibit. A junior engineer must update a group of scripts to use on a newly deployed subnet. However, one of the scripts is not documented or commented. What are the two effects of this script? (Choose two.)

Refer to the exhibit. An engineer started to configure a router for OSPF. Which configuration must the engineer perform on the router without changing any interface configuration so that the router establishes an OSPF neighbor relationship with its peer?
When implementing a REST API, how does an engineer mitigate security risks?
Refer to the exhibit.

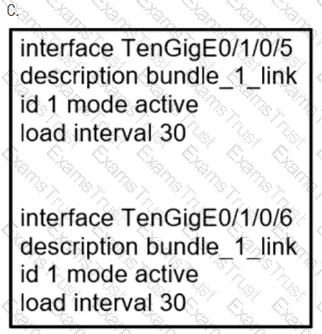
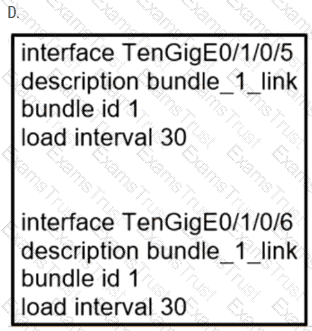
Which the link aggregation configuration router is running on Cisco IOS XR software, which LACP interface configuration is needed to add the interface to the bundle?


Refer to the exhibit. Routers R1 and R2 are connected over the internet, with the connection passing over four different autonomous systems. The company must mitigate potential DDoS attacks and protect the CPUs of the routers. A network engineer must secure all external connections on edge router R1 based on RFC 5082. R2 has already been secured. Which task should the engineer perform on R1 to achieve the goal?
Simulation 8

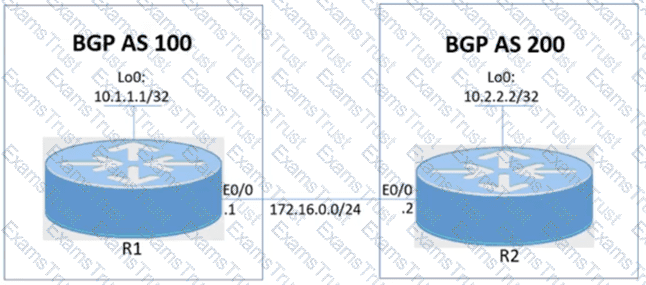
A network engineer is implementing NetFlow to observe traffic patterns on the network. The engineer is planning to review the patterns to help plan future strategies for monitoring and preventing congestion as the network grows. If the captures must include BGP next-hop flows, which configuration must the engineer apply to the router?
Refer to the exhibit. A network engineer observed congestion between routers R1 and R4, which are connected on a point-to-point link. Two servers that reside on networks on R1 and R4 generate heavy traffic between them with most traffic going from R4 to R1. To improve overall performance, the engineer wants to drop inbound packets that exceed a configured threshold, without disrupting traffic that passes from R4 to R3. Which action must the engineer take to resolve the issue?
An engineer must extend Layer 2 Between two campus sites connected through an MPLS backbone that encapsulates Layer 2 and Layer 3 data Which action must the engineer perform on the routers to accomplish this task?

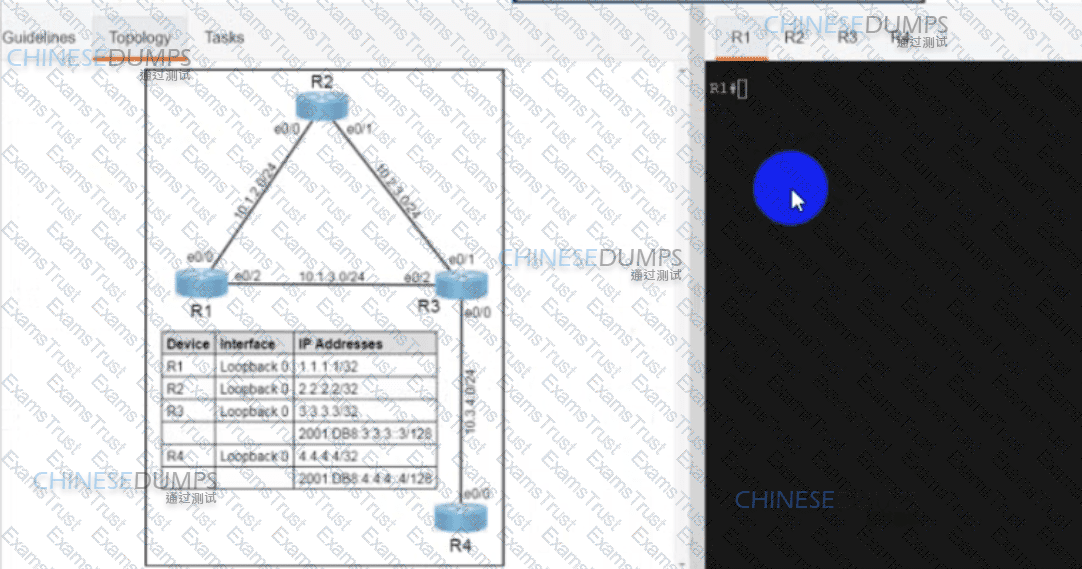
Guidelines
-
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
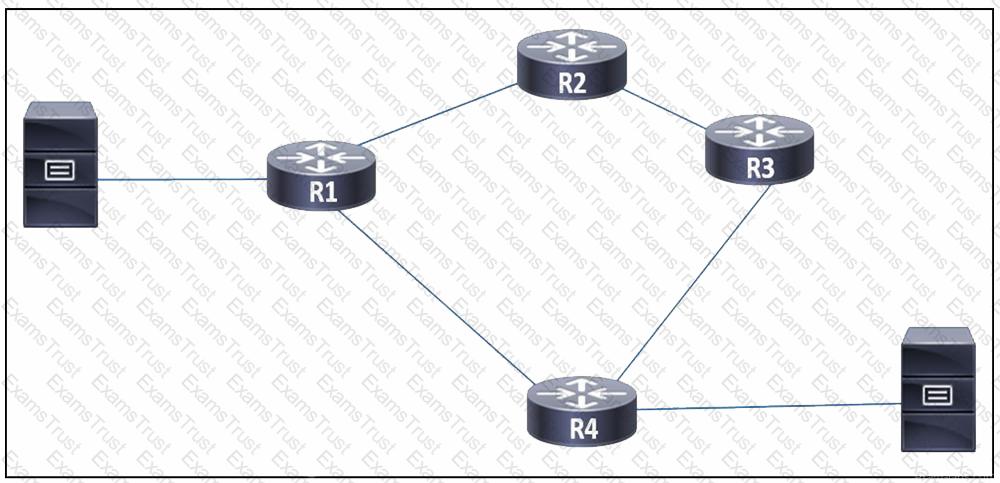
Topology
Tasks
-
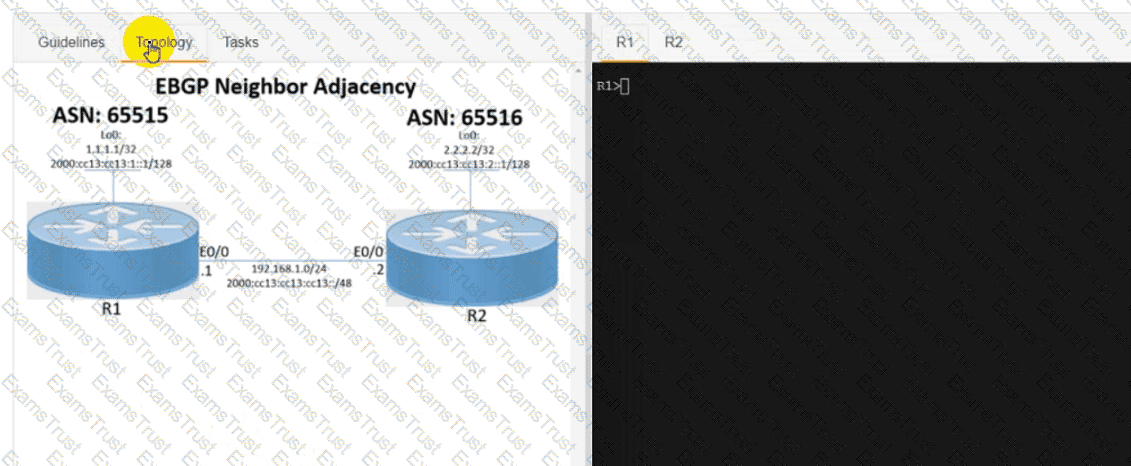
R1 and R2 are having issues forming an eBGP neighbor relationship. Troubleshoot and resolve the issue to achieve these goals:
1. Configure R1 and R2 to form a BGP neighborship using their Loopback interfaces.
2. Form the neighbor relationship using a BGP multihop mechanism. Use minimal values to solve the issue.
Refer to the exhibit.
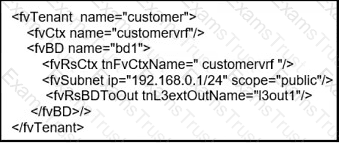
What does this REST API script configure?
Refer to the exhibit.
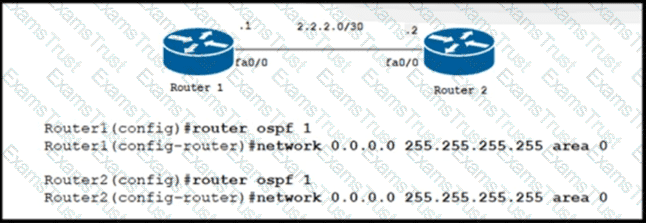
A network engineer must configure an LDP neighborship between two newly installed routers that are located in two different offices. Router 1 is the core router in the network and it has already established OSPF adjacency with router 2. On router 1 and router 2. interface fa0/0 is configured for BFD. Which additional configuration must the engineer apply to the two devices to meet the requirement?
How do intent APIs make it easier for network engineers to deploy and manage networks?

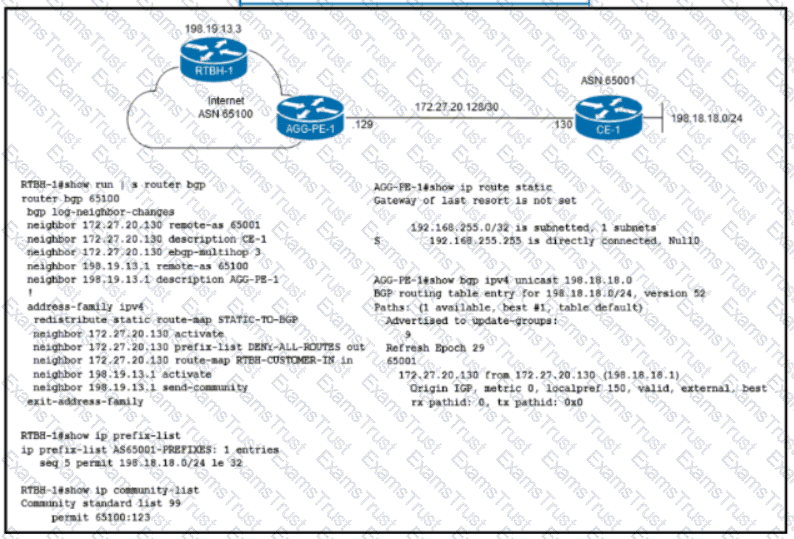
Refer to the exhibit. ISP ASN 65100 provides Internet services to router CE-1 and receives customer prefix 198.18.18.0/24 via eBGP. An administrator for the ISP is now provisioning RTBH services to provide on-demand data-plane security for the customer’s IP space. Which route-map configuration must the administrator apply to router RTBH-1 to complete the implementation of RTBH services to CE-1?
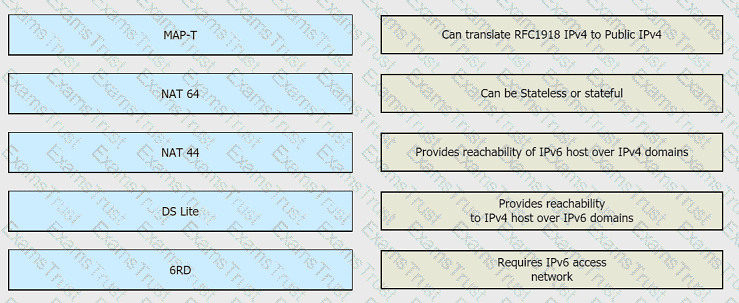
Drag and drop the functionalities from the left onto the correct target fields on the right.
Refer To the exhibit.
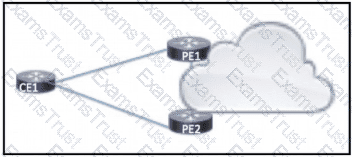
Which BGP attribute should be manipulated to have CE1 use PE1 as the primary path to the Internet?
Refer to the exhibit.
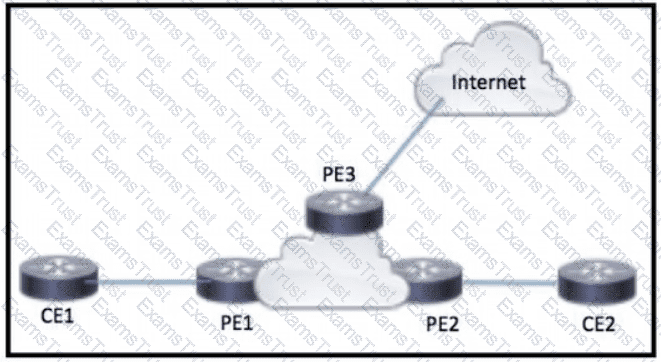
CE1 and CE2 require connectivity to the internet through the ISP connected to PE3 What should an engineer configure to complete this task?
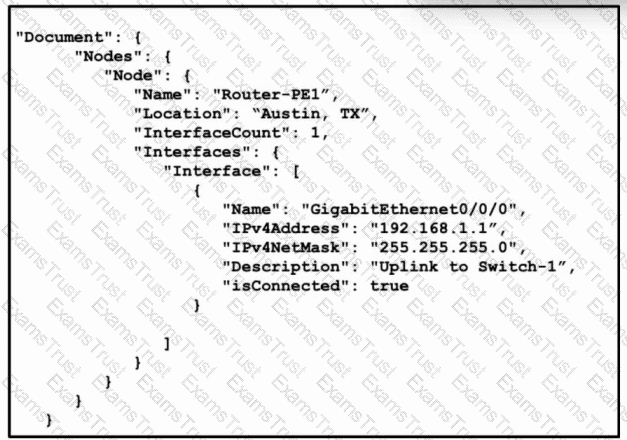
Refer to the exhibit. PE1 is a router connected to a major ISP that provides connectivity for multiple enterprises in several different geographic locations. The ISP networking team uses REST APIs to configure the network devices. A senior engineer retrieved the given script from the library and provided it to a junior engineer to deploy. What effect does the script produce when deployed?
Refer to the exhibit:
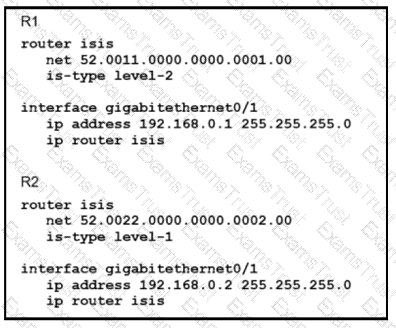
Which statement about the status of the neighbor relationship between R1 and R2 is true?
What is a role of NSO?
Refer to the exhibit.

A network engineer at a large ISP Is configuring telemetry streams to monitor the health status of PE routers on the network using gRPC dial-out. The PE routers are located at several data centers in different physical locations, and they are using IS-IS and BGP for routing. Which additional configuration must the engineer implement on the PE routers to meet the goal?
Why do packet loops occur during the configuration of BlDlR-PIM?
Refer to the exhibit.
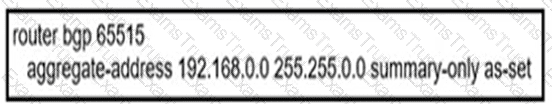
An engineer configured BGP summarization on a customer's network. Which route is advertised to BGP peers?
Which benefit is provided by FRR?
Refer to me exhibit.
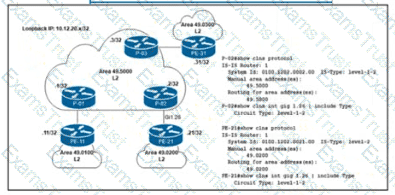
Refer to the exhibit. A network engineer notices PE-21 convergence degradation due to the growing LSDB size of Level 2 areas in the network. The engineer decides to migrate router PE-21 from an inter-area design to an intra-area implementation. Inter-area routing must be accomplished via an ATT-bit set by the Level 1/Level 2 router. Which configuration must the engineer implement on PE-21 to complete the migration?
Refer to the exhibit.
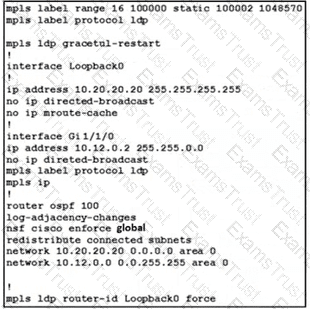
A network administrator implemented MPLS LDP changes on PE-A LSR device. The engineer must ensure there are no LDP peer are fully operational. Which LDP feature must the engineer apply to the existing configuration to eliminate the problem?
Refer to the exhibit.

An engineer is configuring multitiopology IS-IS for IPv6 on router R1. Which additional configuration must be applied to complete the task?
A)

B)

C)

D)

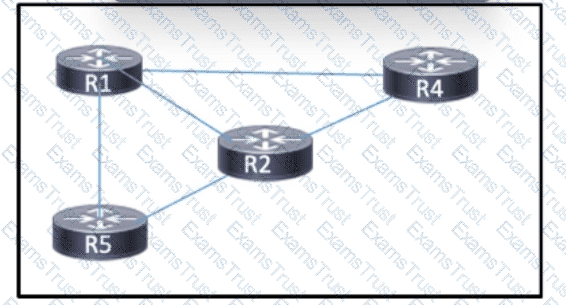
Refer to the exhibit. MPLS is running in the network with OSPF as the IGP. Full routes are shared between the routers, and each connected link has an MPLS neighbor relationship. A network engineer must update the network configuration so that it will maintain LDP neighbor relationships if a directly connected link goes down. Which action must the engineer take as part of the process?
What is the characteristic of the Tl-LFA?
Exhibit:
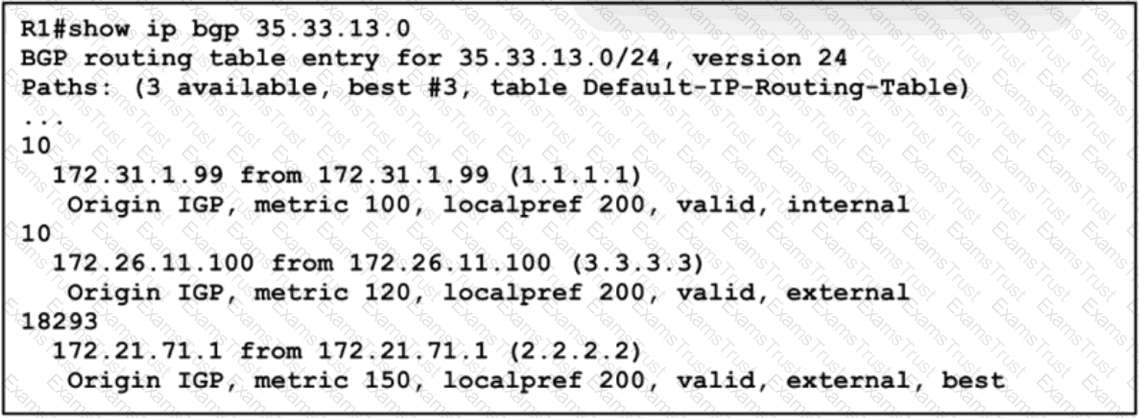
A network engineer must update the routing toward the web server with IP address 35.22.13.1. The primary path must be configured via the neighbor router with ID 1.1.1.1. However, local-preference configuration is not permitted on R1. Which task must the engineer perform on R1 to complete the implementation?
What is a characteristic of data modeling language?
Refer to the exhibit:
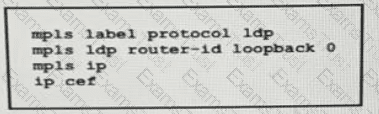
A network operator working for service provider with an employee id 3715 15:021 applied this configuration to a router.
Which additional step should the engineer use to enable LDP?
An engineer is configuring IEEE 802.1 ad on the access port on a new Cisco router. The access port handles traffic from multiple customer VLANs, and it is expected to mark all customer traffic to the same VLAN without dropping any traffic. Which configuration must the engineer apply?
A)

B)

C)

D)

A network engineer is deploying VPLS configuration between multiple PE routers so that customer's remote offices have end-to-end LAN connectivity. Which additional configuration should the engineer perform on the PE routers to enable the virtual switch instance?
A)

B)

C)

D)
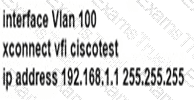
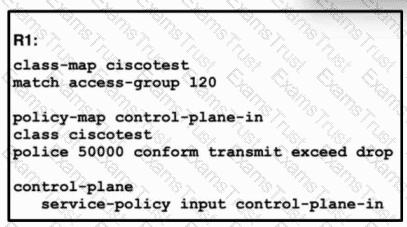
Refer to the exhibit. A network engineer installed router R1 as the new core router and must secure the control plane. The configuration has been applied, and now the engineer is creating ACL 120. Only hosts 192.168.1.1 and 192.168.2.2 should be allowed to access the router using Telnet. All other hosts should be rate-limited, with excess traffic dropped. Which configuration accomplishes this goal?
Refer to the exhibit:
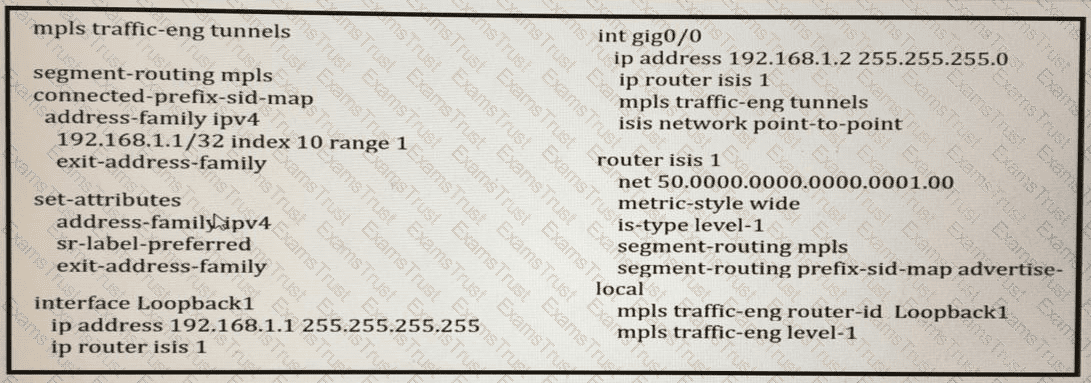
Which statement about this configuration is true"?
While an engineer deploys a new Cisco device to redistribute routes from OSPF to BGP, they notice that not all OSPF routes are getting advertised into BGP. Which action must the engineer perform so that the device allows O, OIA, OE1, and OE2 OSPF routes into other protocols?
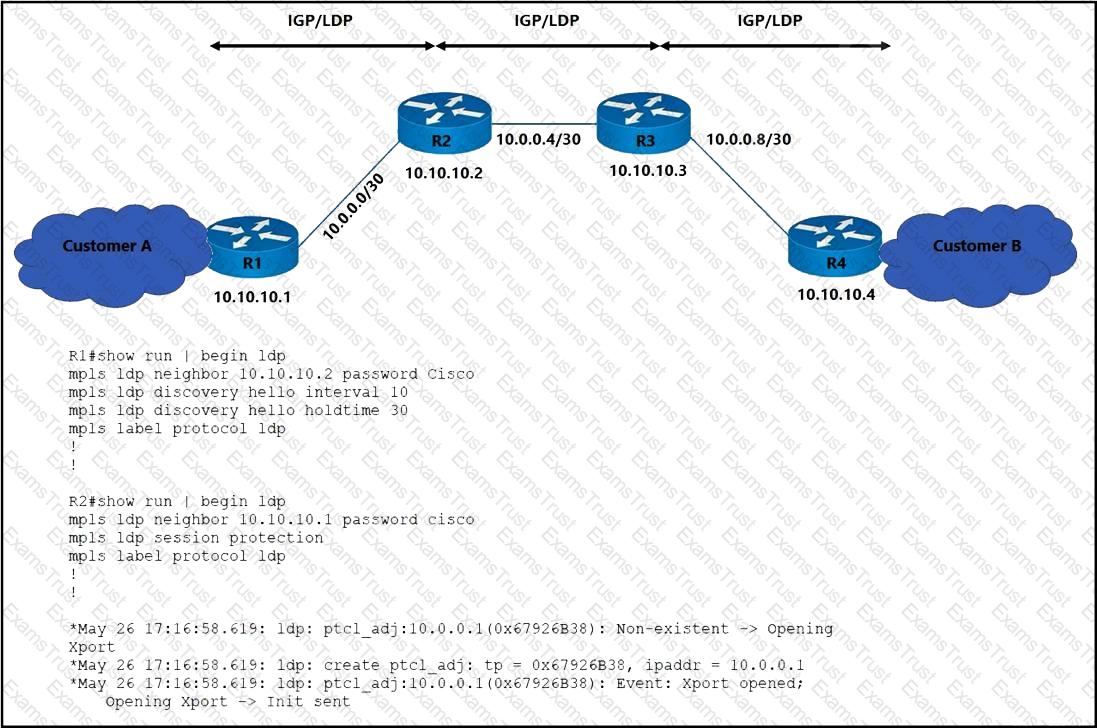
Refer to the exhibit. The operations team is implementing an LDP-based configuration in the service provider core network with these requirements:
R1 must establish LDP peering with the loopback IP address as its Router-ID.
Session protection must be enabled on R2.
How must the team update the network configuration to successfully enable LDP peering between R1 and R2?
How does an untrusted interface at the boundary of an administrative domain handle incoming packets?
Refer to the exhibit.
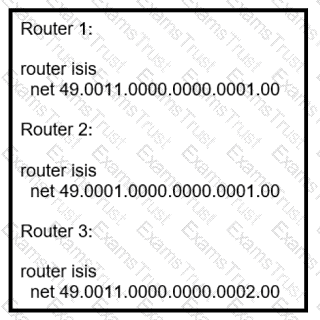
Router 4 is added to the network and must be in the same area as router 1. Which NET should the engineer assign?
Refer to the exhibit.
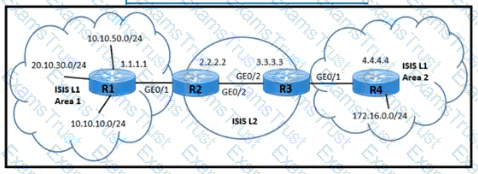
A network engineer must meet these requirements to provide a connects, solution:
The customer connected to Area 2 needs to access the application in Area 1 on the 10.10.10.0/24 subnet
The Customer must not have access to the 20.10 30.0/24 subnet.
The service provider must make sure that the Area 2 routing database limits the number of IP addresses in the routing table
Which two configurations must be implemented to meet the requirements? (Choose two)
An engineer is moving all of an organization’s Cisco IOS XE BGP routers to the address-family identifier format. Which command should be used to perform this upgrade quickly with the minimum service disruption?
What happens when a segment-routing TE tunnel loses the link and there is no secondary path in place?
A regional MPLS VPN provider operates m two regions and wants to provide MPLS L 3VPN service for a customer with two sites in these separate locations. The VPN provider approaches another organization to provide backbone carrier services so that the provider can connect to these two locations.
Which statement about this scenario is true?
The NOC engineer in a service provider network must configure an SNMP community on switch SW with these security attributes:
* Event messages must be authenticated with the MD5 algorithm and encrypted.
* The remote user name for the SNMP server at 172.16.10.1 is AuthNocUser.
Which configuration must the engineer apply to the switch?
SIMULATION 4
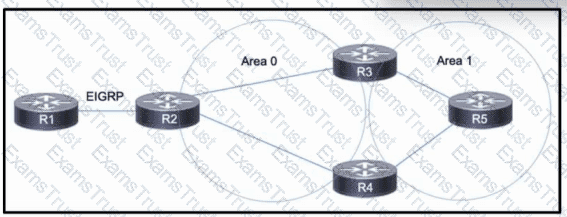
Refer to the exhibit. Company A is running OSPF within its network, comprised of routers R2, R3, R4, and R5 and consisting of two areas. Company A just acquired Company B, which uses EIGRP on its own R1. R1 has several routes in its routing table. The network engineering team at Company A needs access to the Company B network to manage network devices there, but each company will otherwise operate independently. R2 will serve as the ASBR between the two networks. Which action must the team take to reduce the number of EIGRP routes received on R2 and include only the necessary routes in the routing table?
Which type of attack is a Protocol attack?
A network operator needs to implement PIM-SSM multicast configuration on customer's network so that users in different domains are able to access and stream live traffic. Which two actions must the engineer perform on the network
to make the streaming work? (Choose two.)
What is one of the main functions of 6RD?
Refer to the exhibit.
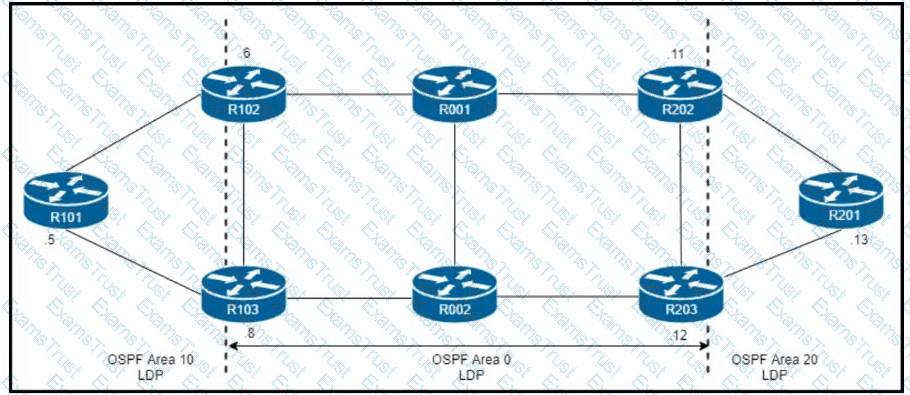
R101 is peering with R102 and R103, and R201 is peering with R202 and R203 using iBGP Labeled Unicast address families. The OSPF area 0 border routers are in a full iBGP Labeled Unicast mesh, and VPNv4 routes are exchanged directly between PE routers R101 and R201 through iBGP Which address family-level configuration must be applied on ABR R102 on ABR R102 to support a Unified MPLS routing architecture with partitioned IGP domains?
A)

B)
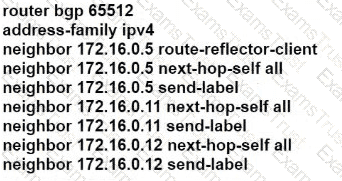
C)
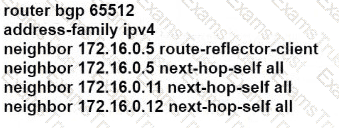
D)
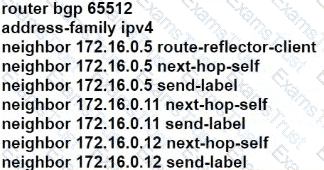
An organization with big data requirements is implementing NETCONF as part of its migration to a new cloud-based environment. The organization has multiple offices across widespread geography. A network engineer is configuring NETCONF on one of the border routers. Which configuration must the engineer apply to save the running configuration?
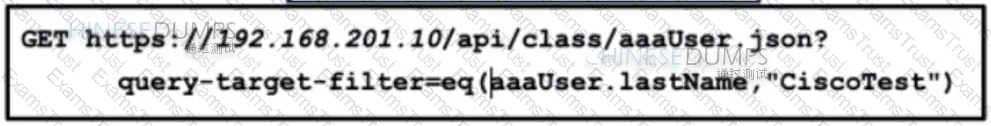
Refer to the exhibit. An engineer configured several network devices to run REST APIs. After testing, the organization plans to use REST APIs throughout the network to manage the network more efficiently. What is the effect if this script?
Which control plane protocol is used between Cisco SD-WAN routers and vSmart controllers?
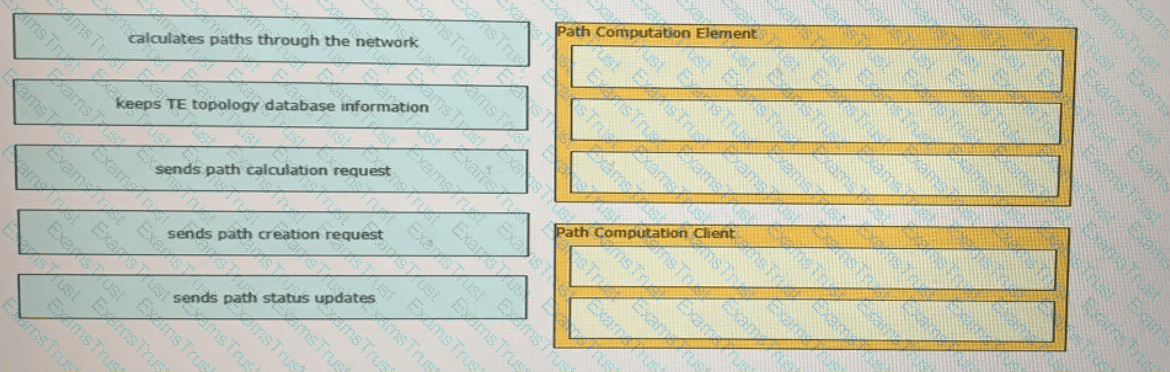
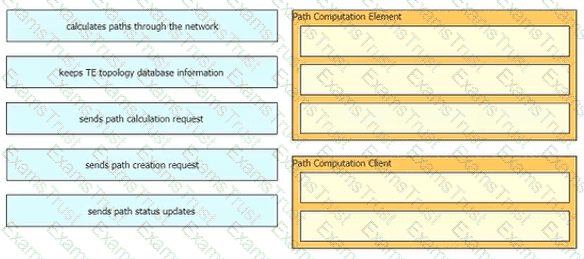
Drag and drop the functions from the left onto the correct Path Computation Element Protocol roles on the right
The NOC team must update the BGP forwarding configuration on the network with these requirements:
BGP peers must establish a neighborship with NSF capability and restart the session for the capability to be exchanged after 120 seconds.
BGP peers must delete routes after 360 seconds of inactivity.
Which action meets these requirements?
Refer to the exhibit.
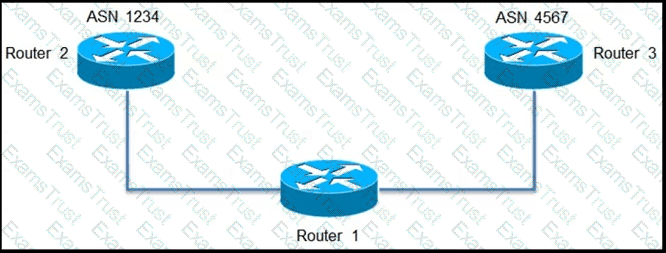
An engineer is configuring path selection on router R1 for two ASNs as shown. Which additional task must the engineer perform on Router 1 so that all outbound traffic utilizes the link between R1 and R3 to reach ASN 4567?
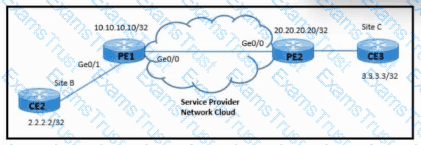
Refer to the exhibit. A network engineer is configuring Ethernet Layer 2 service to connect CE2 and CE3 for video and data application sharing with these requirements:
A point-to-point cross-connect service must be established between 10.10.10.10 and 20.20.20.20.
PE1 and PE2 must learn neighbors dynamically in PW 10.
Which configuration must be implemented on PE1 to meet the requirements?
Refer to the exhibit.

An engineer is securing a customer's network. Which command completes this configuration and the engineer must use to prevent a DoS attack?
Refer to the exhibit.
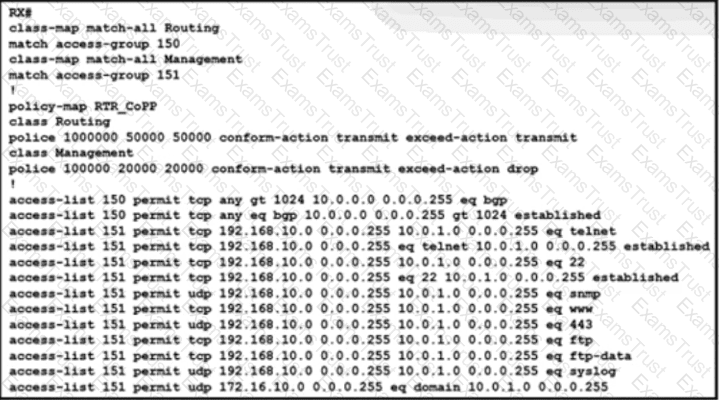
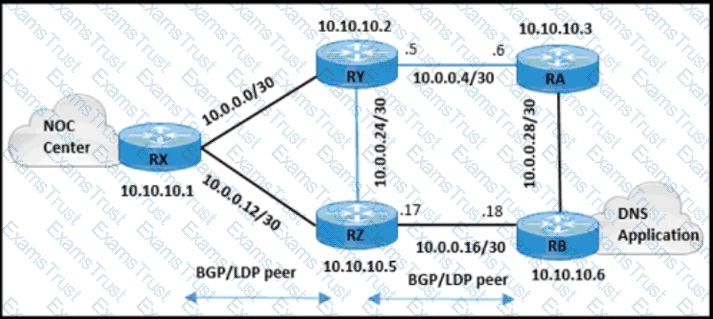
The engineering team wants to limit control traffic on router RX with the following IP address assignments:
• Accepted traffic for router: 10.0.0.0/24
• NOC users IP allocation: 192.168.10.0/24
Which additional configuration must be applied to RX to apply the policy for MSDP?
What is the primary purpose of Terraform in the network?
Refer to the exhibit.
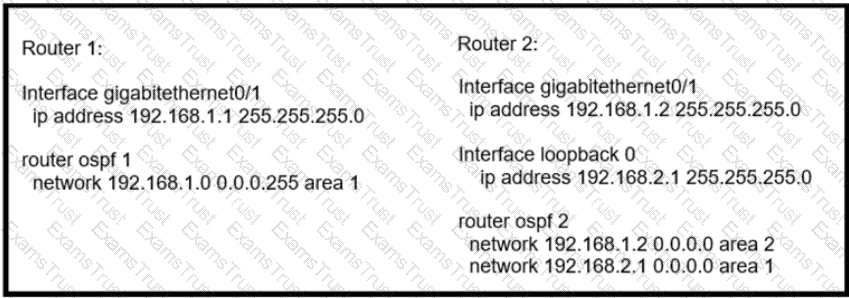
Router 1 is missing the route for the router 2 loopback 0. What should the engineer change to fix the problem?
An engineer working for a private telecommunication company with an employe id:3948:613 needs to limit the malicious traffic on their network. Which configuration must the engineer use to implement URPF loose mode on the GigabitEthernet0/1 interface?
A)

B)

C)

D)

Refer to the exhibit:
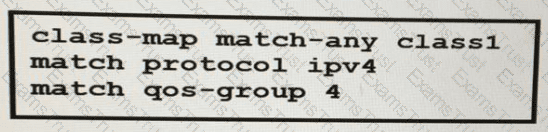
A network engineer is implementing QoS services. Which two statements about the QoS-group keyword on Cisco IOS XR 3re true? (Choose two )
R1 serves as a route reflector on a BGP-enabled network and has dual RPs installed. To ensure that all routes have been processed when an RP fails over, R1 must send the router request to all peers configured with NSR to refresh the route database. Which action completes the implementation?
Refer to the exhibit.

Which type of DDoS attack will be mitigated by this configuration?
Refer to the exhibit.
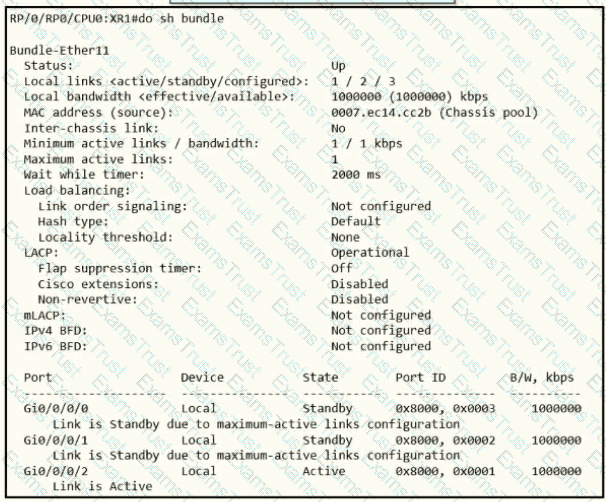
A network operator needs to shut down interface Gi0/0/0/2 for maintenance. What occurs to the interface states of Gi0/0/0/0 and Gi0/0/0/1?
Company A is implementing VoIP services across the company. The network architect designed a QoS policy to allow only specific IP subnets and mark the signaling flow with DSCP 36. The solution should be as secure as possible. Phones receive their IP addresses from the 172.184.12.0/24 pool and are assigned by the RADIUS server to VLAN 1021. Skinny Client Control Protocol is used as a signaling protocol in the network. For security reasons, switchport port-security maximum 1 vlan voice has been preconfigured on the switch side. Which two tasks must an engineer perform on SW_1 to achieve this goal? (Choose two.)
A mid-size service provider uses L2VPN as its standard for connectivity between offices. A small company wants the service provider to connect the company's two sites across the service provider core. To meet service requirements, the service provider must extend the Layer 2 domain between the company's two locations.
Which configuration must the engineer apply to implement an attachment circuit between the two sites using a VLAN tag of 12?
Refer to the exhibit:
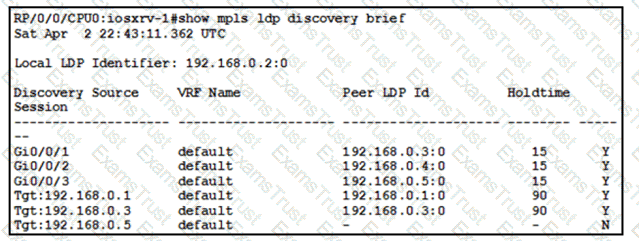
With which router does IOSXRV-1 have LDP session protection capability enabled but session hold up is not active?
Refer to the exhibit.
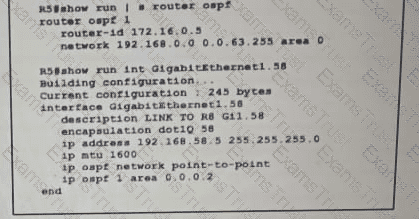
Which configuration must be implemented on router R8 so that it will establish OSPF adjacency with R5?
A)
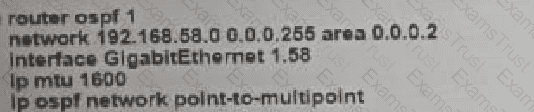
B)
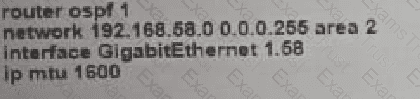
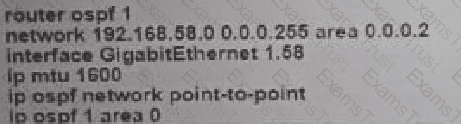
C)

D)
Drag and drop the functions from the path computation element protocol roles on the right.
You are writing an RPL script to accept routes only from certain autonomous systems Consider this code.
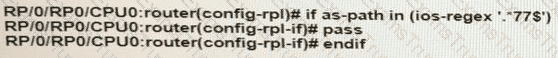
If you apply this code to BGP filters, which effect does the code have on your router?
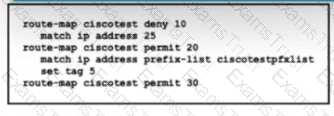
Refer to the exhibit. A client wants to filter routes to a BGP peer to limit access to restricted areas within the network. The engineer configures the route map ciscotest to filter routes from the BGP neighbor. The engineer also sets a tag that will be used for QoS in the future. Which task must be performed to complete the Implementation?
After a possible security breach, the network administrator of an ISP must verify the times that several different users logged into the network. Which command must the administrator enter to display the login time of each user that activated a session?
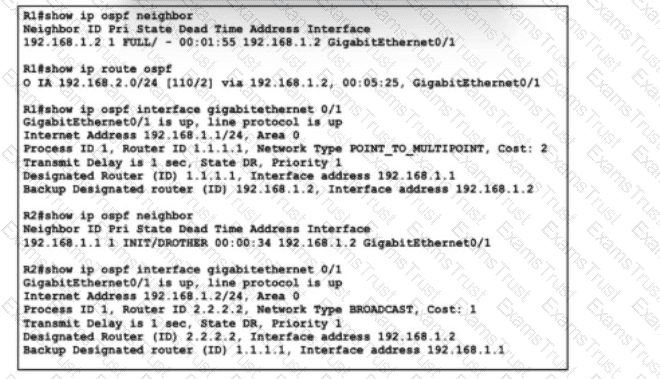
Refer to the exhibit. A junior network engineer has been configuring OSPF on two directly connected routers, R1 and R2, to establish a neighbor adjacency. The engineer also configured ip route 10.1.1.0 255.255.255.0 GigabitEthernet 0/1 10.10.10.1 on R1 to allow inbound management. After the initial configuration, the adjacency failed to form. The engineer changed the cost and area type under the OSPF configuration on R1, but the problem persists. Which action must the engineer take to resolve the issue?
Refer to the exhibit.
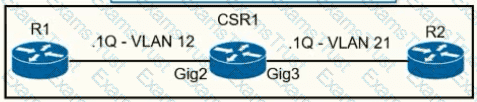
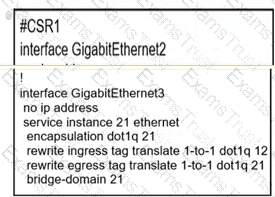
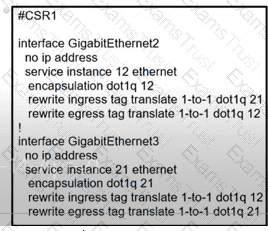
A network operator must configure CSR1 interlaces GigabitEihernet2 and GigabitEthemet to rewrite VLAN tags 12 and 21 for traffic between R1 and R2 respectively. Which configurator accomplishes this task?
A)

B)

C)
D)
Which feature describes the weight parameter for BGP path selection?

Refer to the exhibit. A large organization is merging the network assets of a recently acquired competitor with one of its own satellite offices in the same geographic area. The newly acquired network is running different routing protocol than the company's primary network. As part of the merger a network engineer implemented this route map Which task must the engineer perform to complete the Implementation?
Refer to the exhibit:
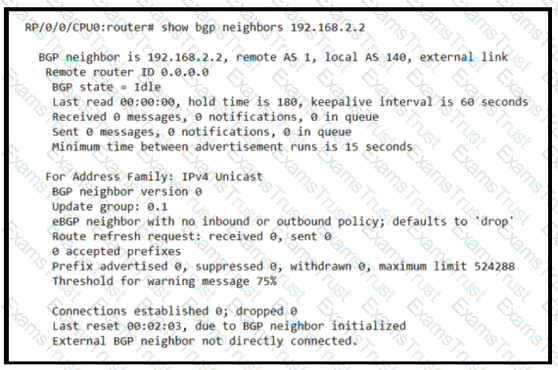
Based on the show/ command output, which result m true after BGP session is established?
What occurs when a high bandwidth multicast stream is sent over an MVPN using Cisco hardware?
What are two purposes of a data-modeling language such as YANG? (Choose two.)
Refer to the exhibit:

Router 1 was experiencing a DDoS attack that was traced to interface gjgabitethernet0/1.
Which statement about this configuration is true?
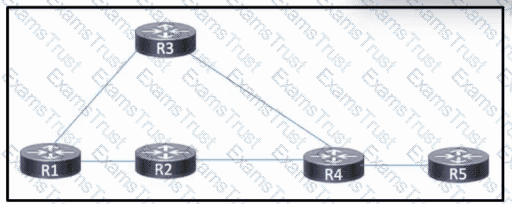
Refer to the exhibit. OSPF is running in the core, with MPLS configured on all links. A Cisco MPLS TE tunnel is configured with R1 as the headend and R4 as the tail-end router. As traffic on the network increases, the network engineering team is concerned about identifying failures between the tunnel endpoints.
Which action should the engineering team take that will allow them to identify and locate any faults in the path?
A router is configured to perform MPLS LDP graceful restart.
Which three steps are included when the RP sends an LDP initialization to a neighbor to establish an LDP session? (Choose three)
In an MPLS network, which protocol can be used to distribute a Segment Prefix?
Refer to the exhibit:
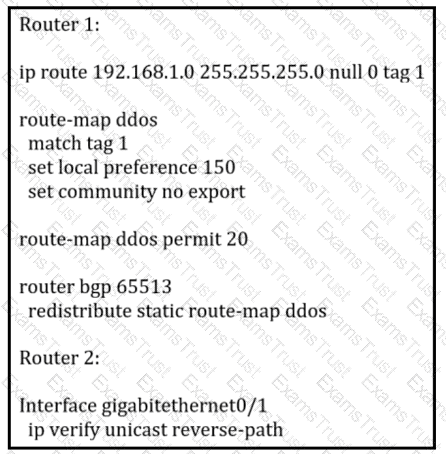
An engineer is preparing to implement data plane security configuration.
Which statement about this configuration is true?
Refer to the exhibit:

What does this value mean when it is received in XML?
What must a network engineer consider when designing a Cisco MPLS TE solution with OSPF?
Refer to the exhibit.
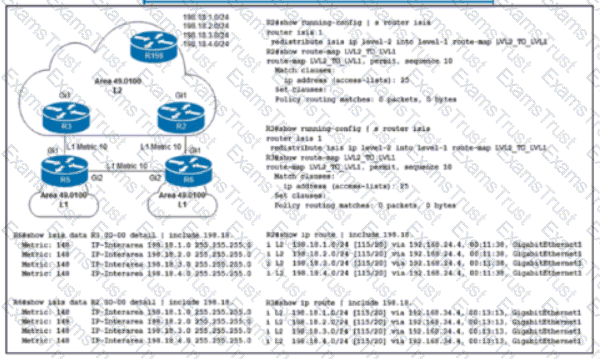
Routers R2 and R3 are Level 1/Level 2 IS-IS routers that redistribute 198 18.x.x/24 prefixes to routers R5 and R6 In the Level 1 area R2 Is to be the preferred router for all redistributed prefixes in the Level 1 area. Which configuration sets this preference?

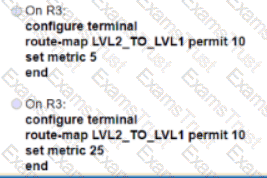
The network-engineering team of a service provider is integrating several recently acquired networks into a more scalable common Unified MPLS architecture. The new network architecture will support end-to-end VPNv4 and VPNv6 services with these requirements:
• The IGP of the core layer is IS-IS In Area 0.
• The IGP of the aggregation layers is OSPF in Area 0.
• The LDP protocol Is used to distribute label bindings within each IGP domain.
Which task must the network engineer perform when implementing this new architecture?
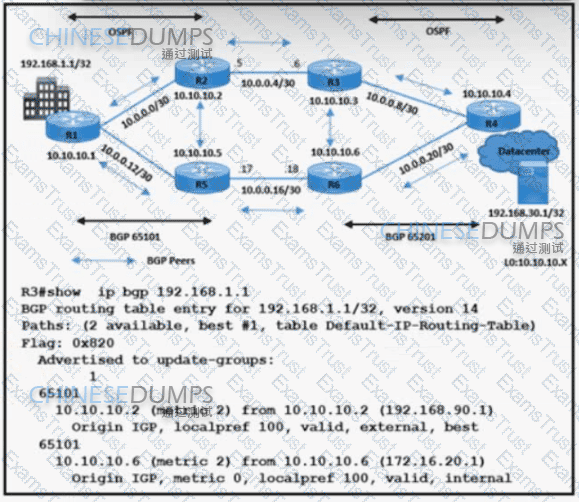
Refer to the exhibit. A network engineer is implementing BGP in AS 65101 and AS 65201. R3 sends data traffic to 192.168.1.1 /32 via the path R3-R2-R1. The traffic must travel via alternate path R6-R5 for prefix 192.168.1.1/32. Which action must be taken to meet the requirement?
Which task must be performed first to Implement BFD in an IS-IS environment?
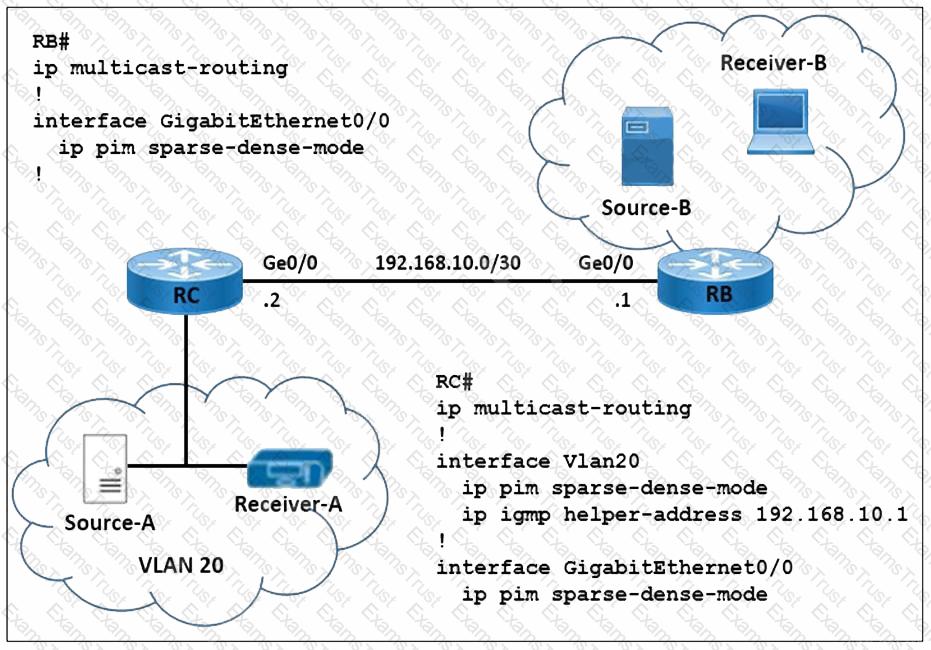
Refer to the exhibit. A network engineer is implementing multicast Source-A to send a multicast stream for Receiver-A, and multicast Source-B to send a multicast stream for Receiver-B. Router RC forwards the IGMP host a report and leaves messages to IP address 192.168.10.1. How must the multicast features be implemented to prevent RB from receiving multicast flooding from Source-A?
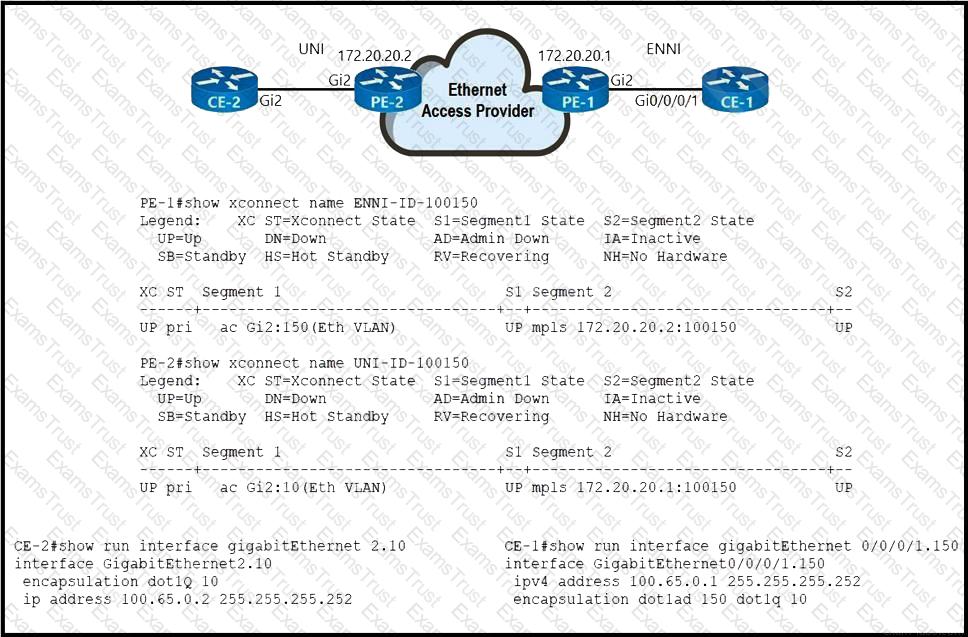
Refer to the exhibit. An Ethernet access provider is configuring routers PE-1 and PE-2 to provide E-Access EVPL service between UNI and ENNI. ENNI service multiplexing is based on 802.1ad tag 150, and service-multiplexed UNI is based on 802.1q tag 10. Which EFP configurations must the provider implement on PE-1 and PE-2 to establish end-to-end connectivity between CE-1 and CE-2?
An engineering team must implement Unified MPLS to scale an MPLS network. Devices in the core layer use different IGPs, so the team decided to split the network into different areas. The team plans to keep the MPLS services as they are and introduce greater scalability. Which additional action must the engineers take to implement the Unified MPLS?
Refer to the exhibit:
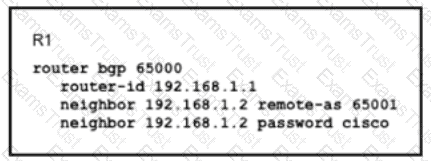
Router R1 and its peer R2 reside on the same subnet in the network, If does it make connections to R27