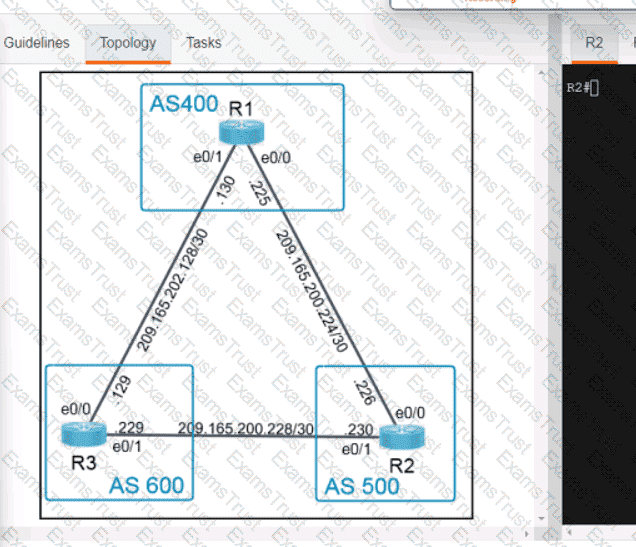

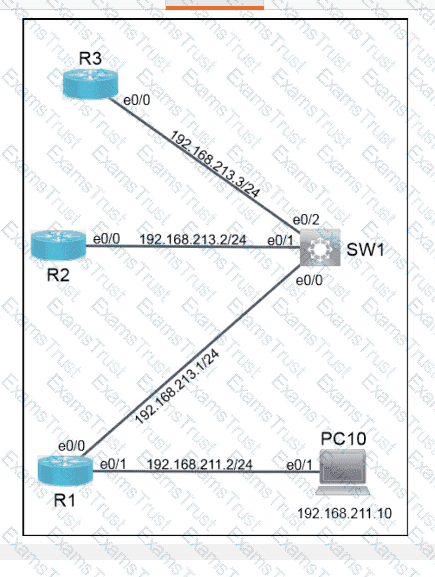
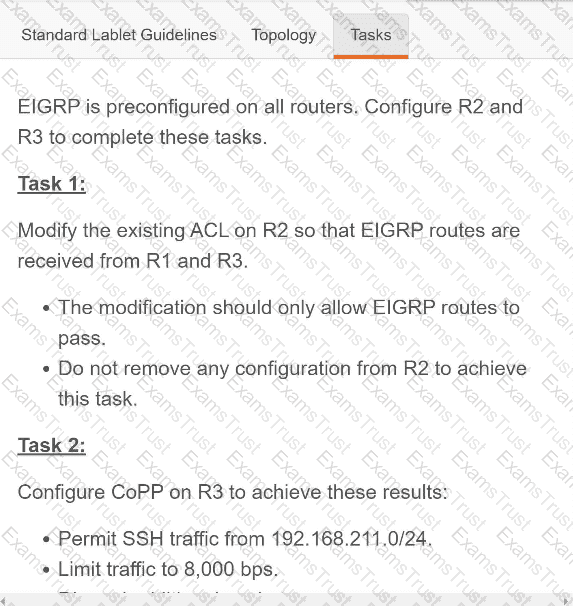

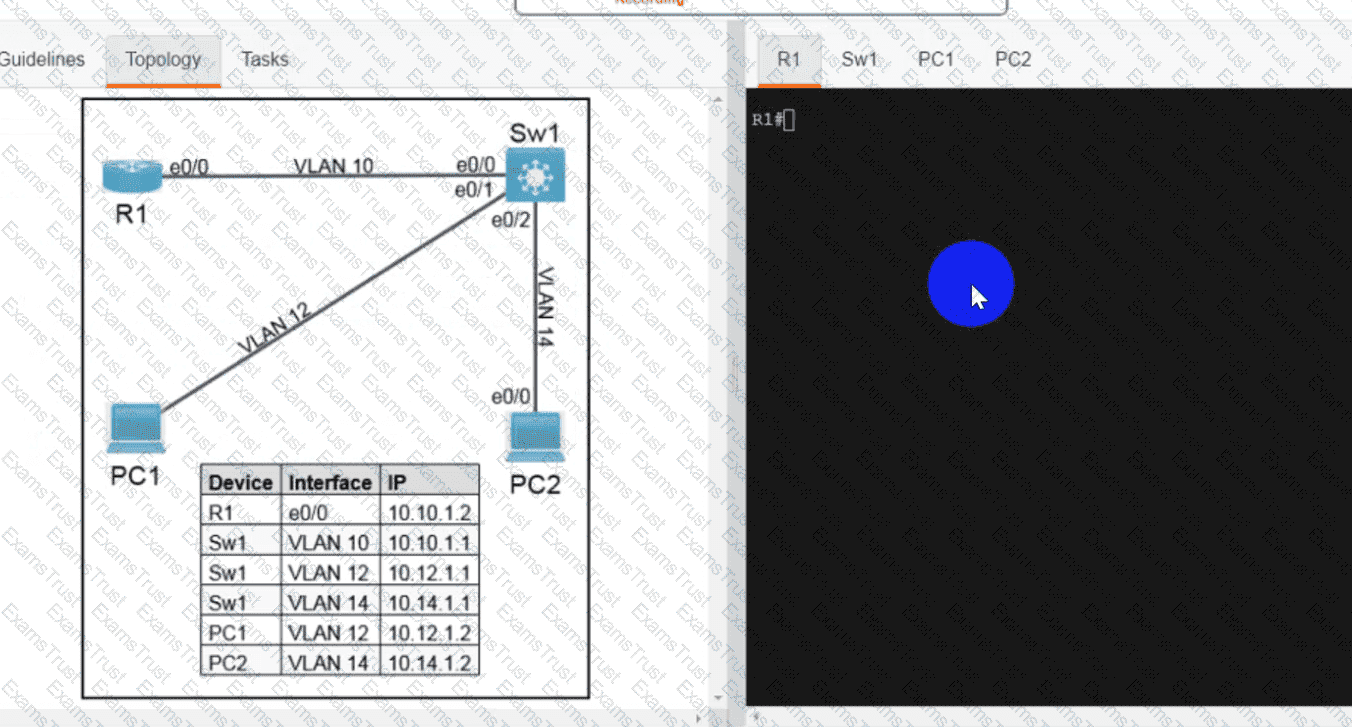
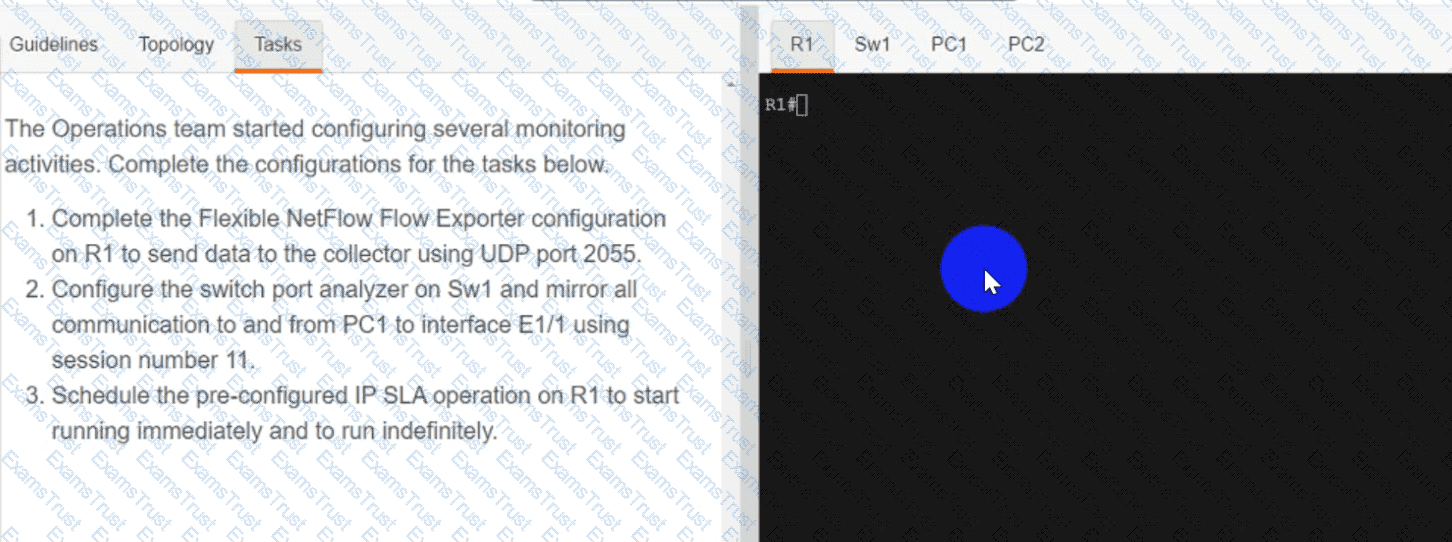
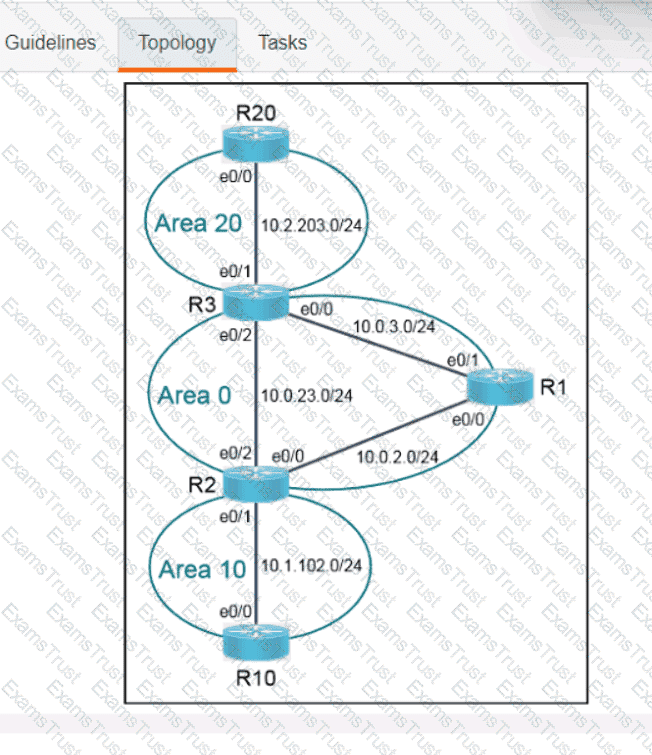

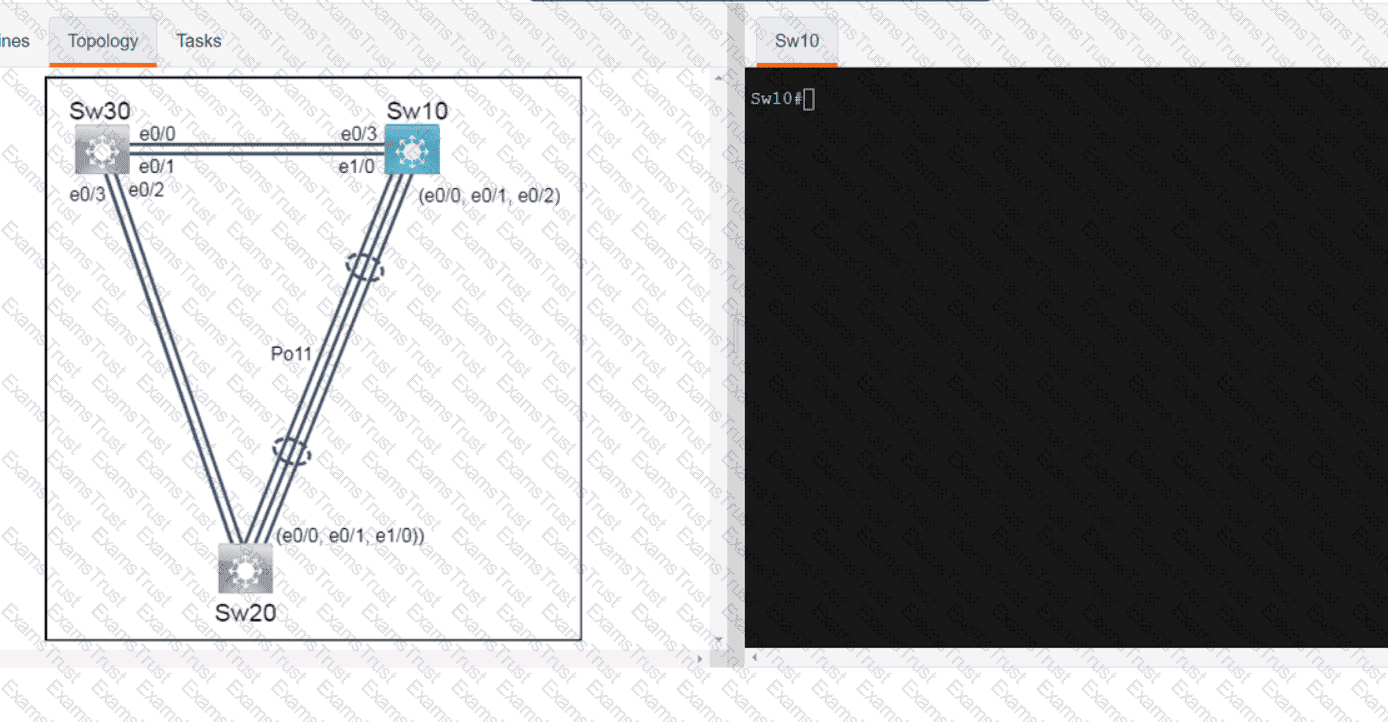
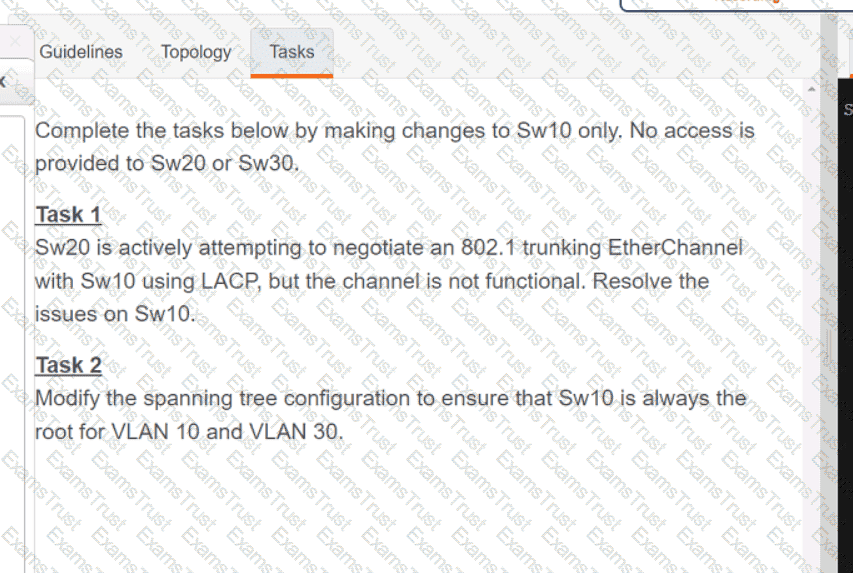

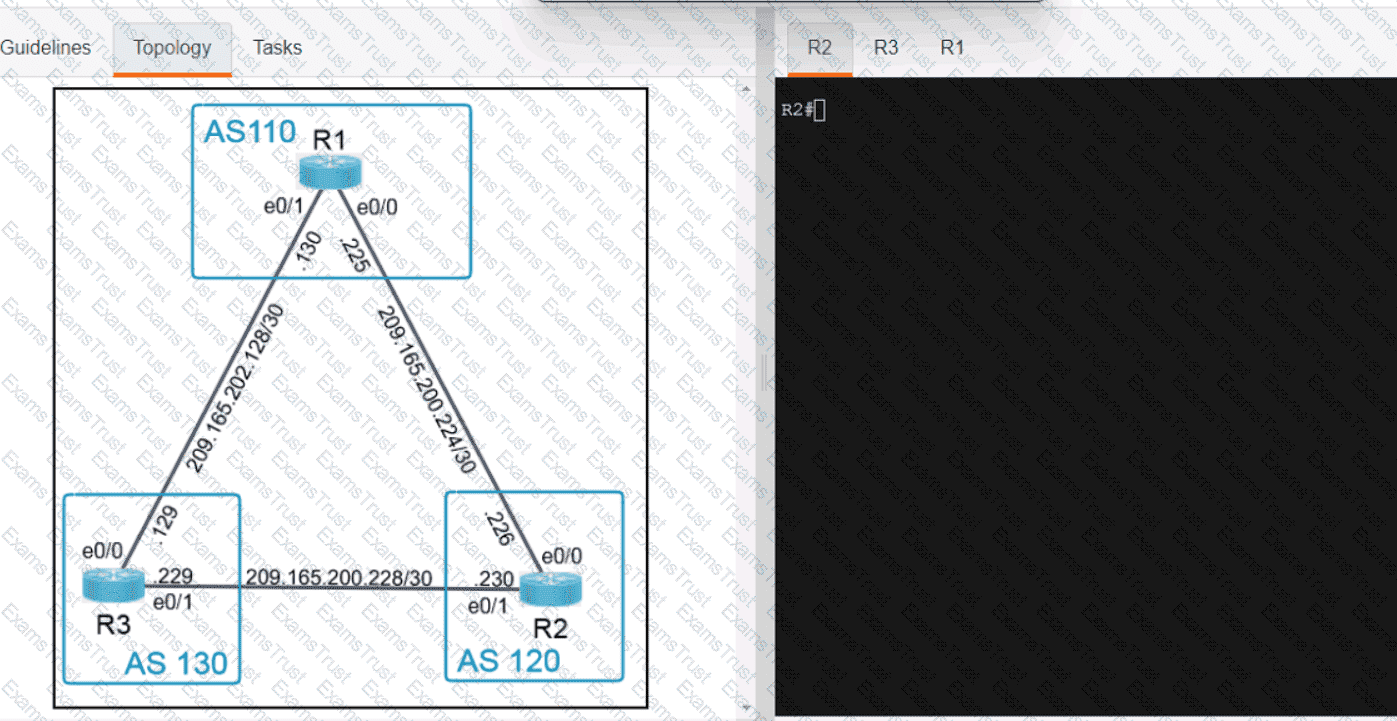
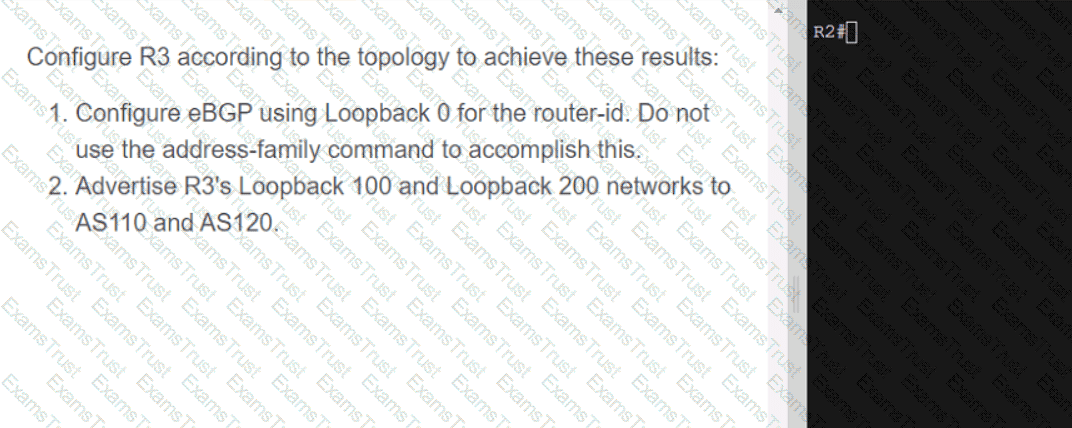
OR

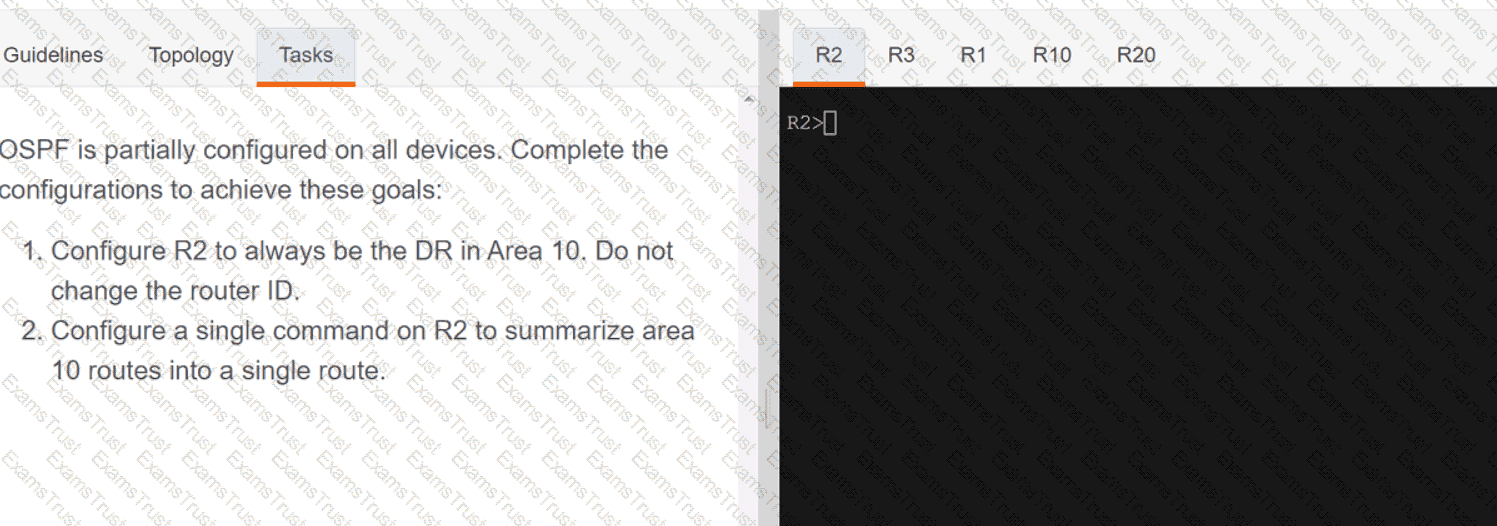
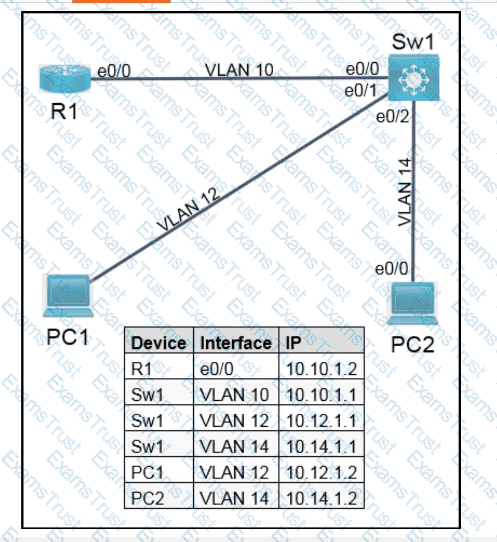

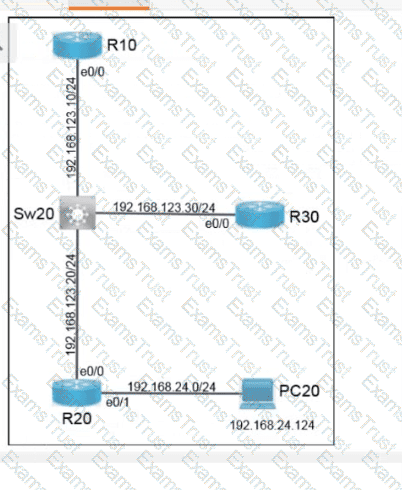
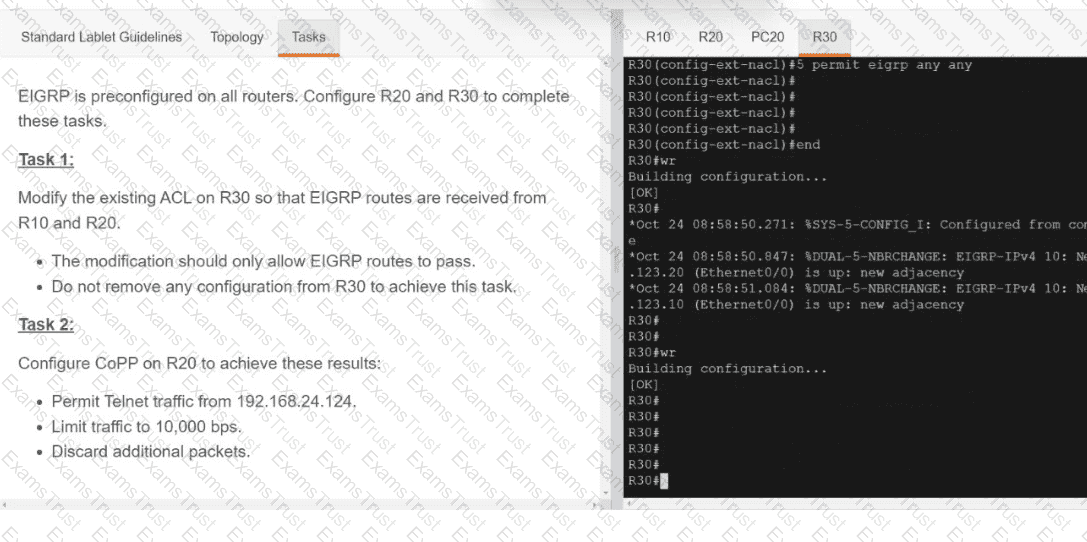


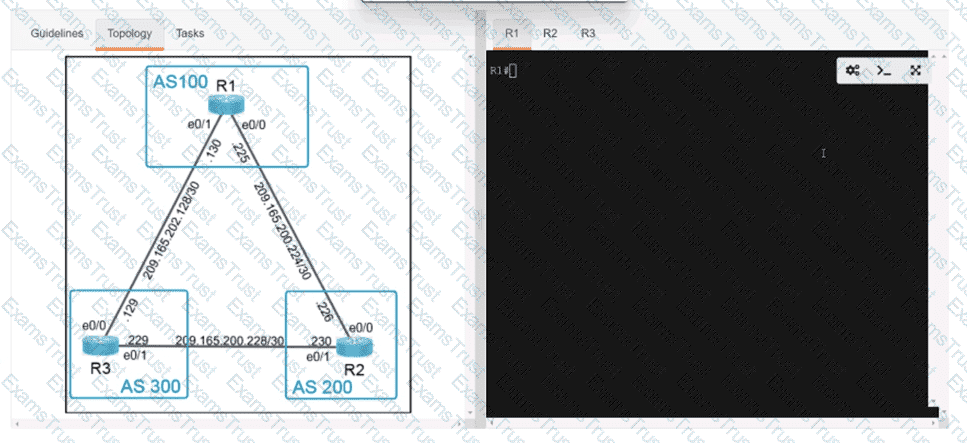
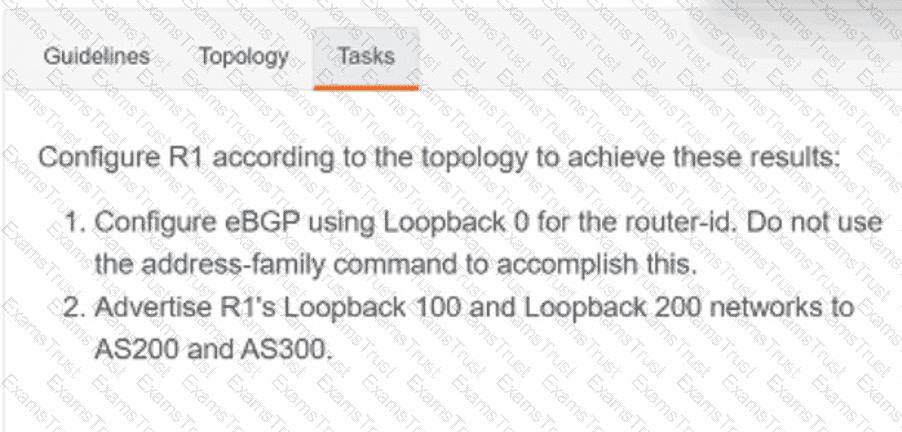
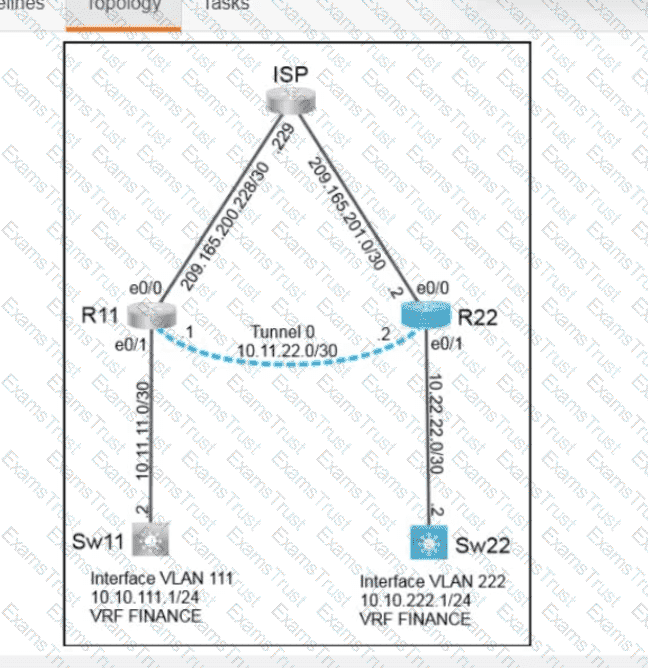
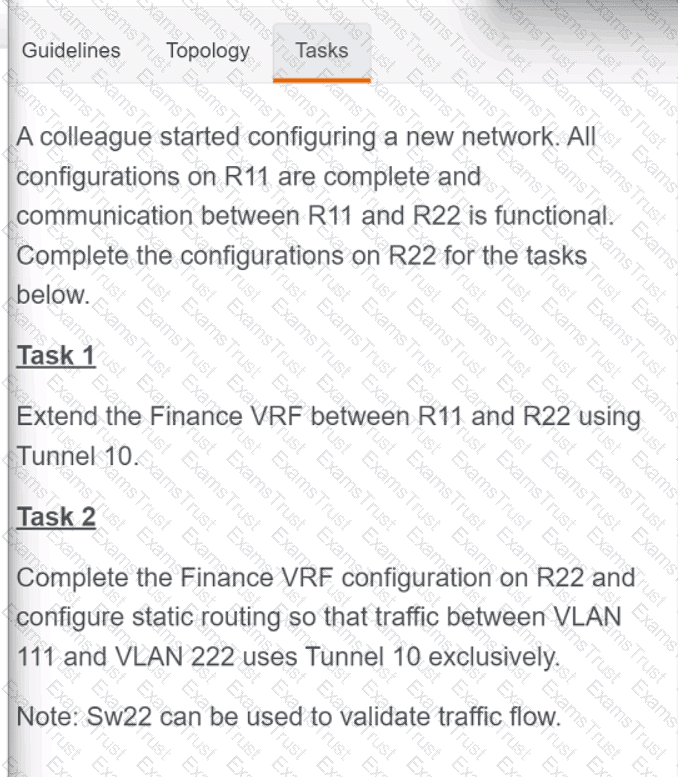
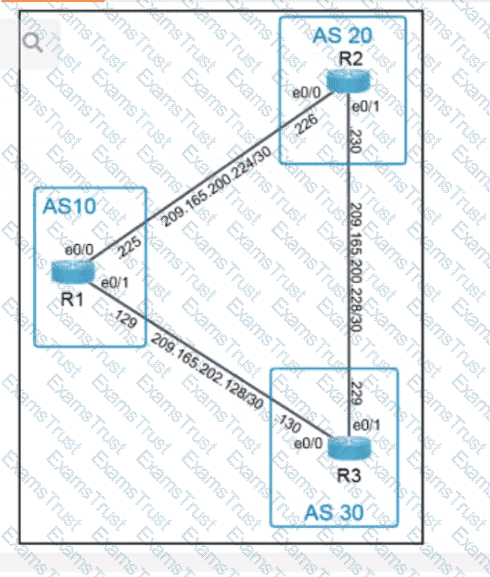
Which two new security capabilities are introduced by using a next-generation firewall at the Internet edge? (Choose two.)
Which NGFW mode block flows crossing the firewall?

What is the JSON syntax that is formed the data?
A)

B)
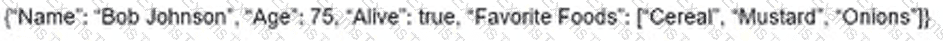
C)

D)

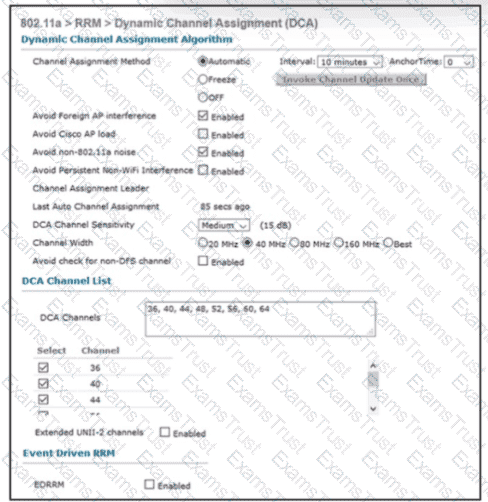
Refer to the exhibit An engineer is troubleshooting an issue with non-Wi-Fi interference on the 5-GHz band The engineer has enabled Cisco CleanAir and set the appropriate traps, but the AP does not change the channel when it detects significant interference Which action will resolve the issue?
Which location tracking method is used when locating client devices using Cisco hyperlocation?
Which data format can be used for an API request?
In a fabric-enabled wireless network, which device is responsible for maintaining the endpoint ID database?
Which component transports data plane traffic across a Cisco SD-WAN network?
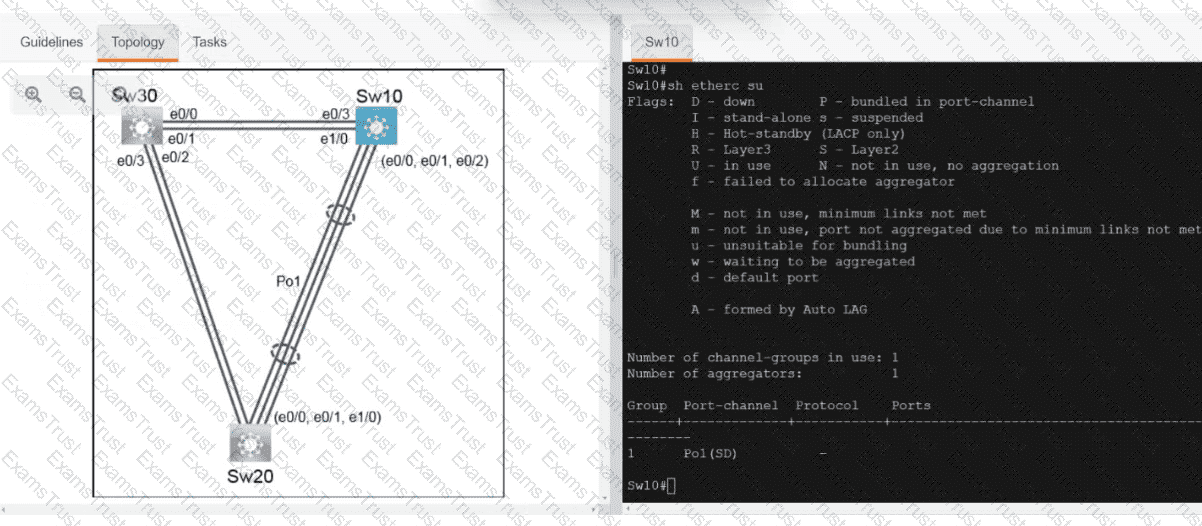
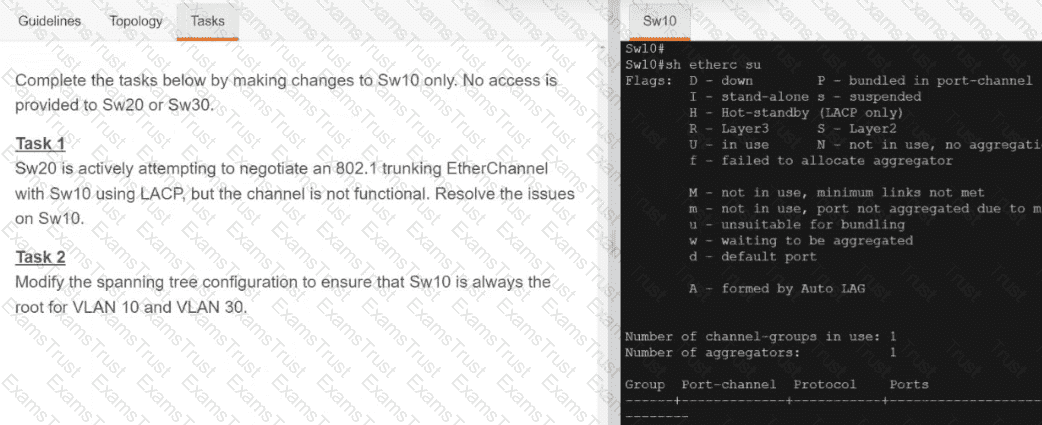
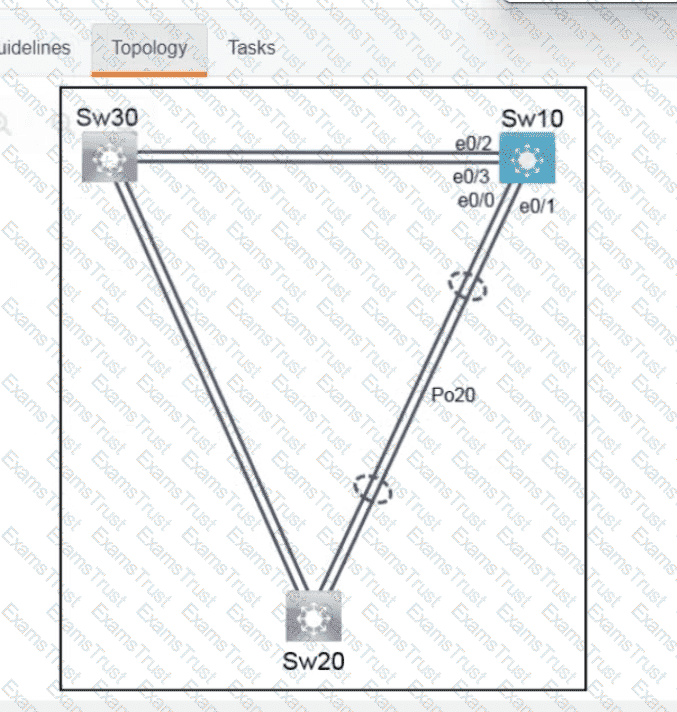
Which technology reduces the implementation of STP and leverages both unicast and multicast?
What is a characteristic of VRRP?
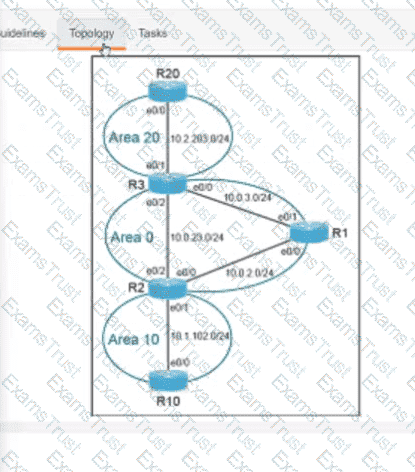
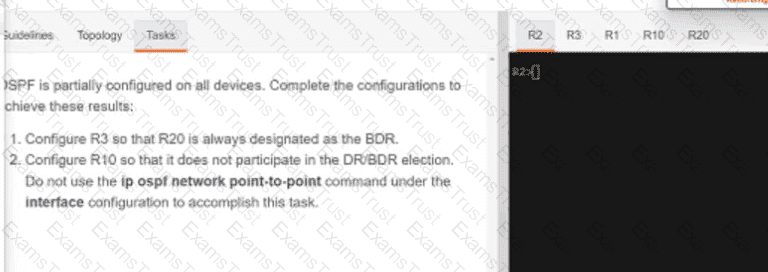
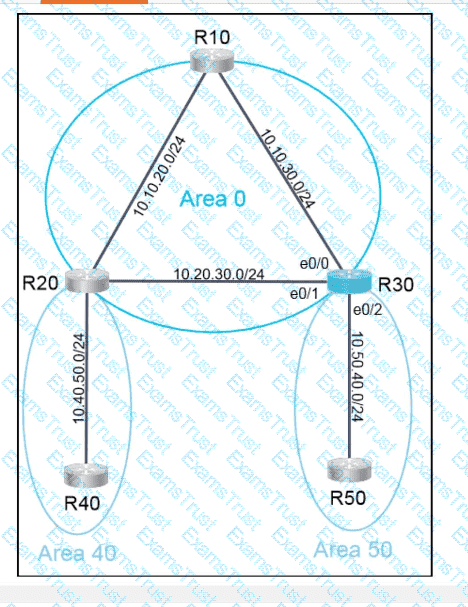
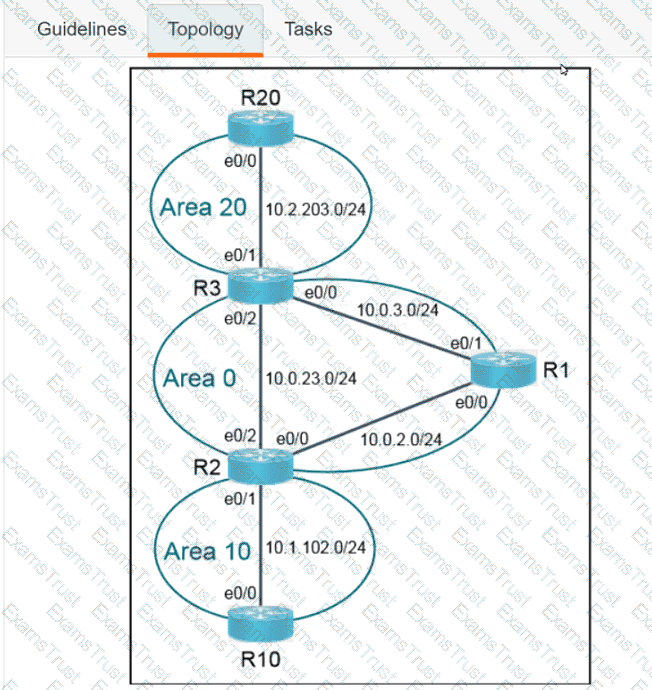
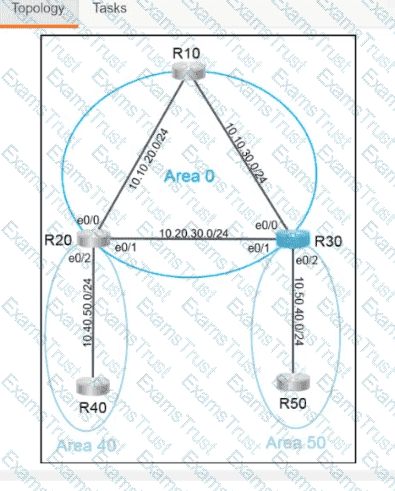
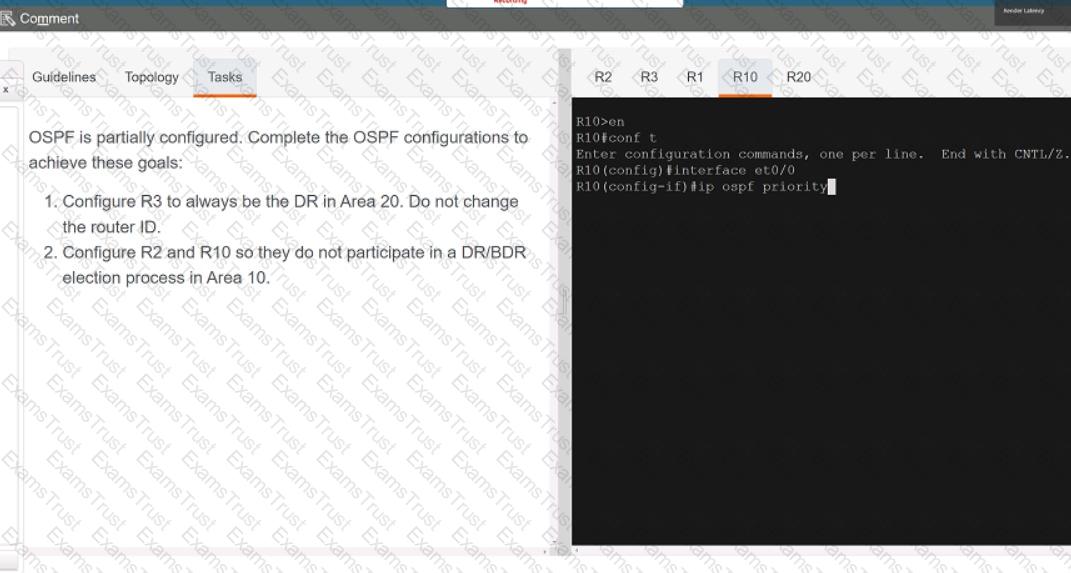
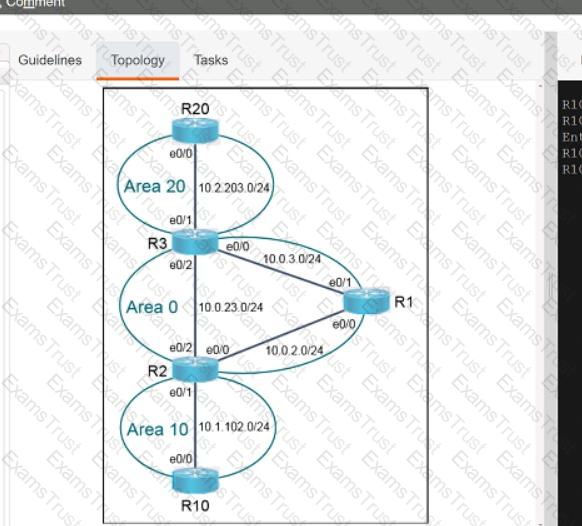
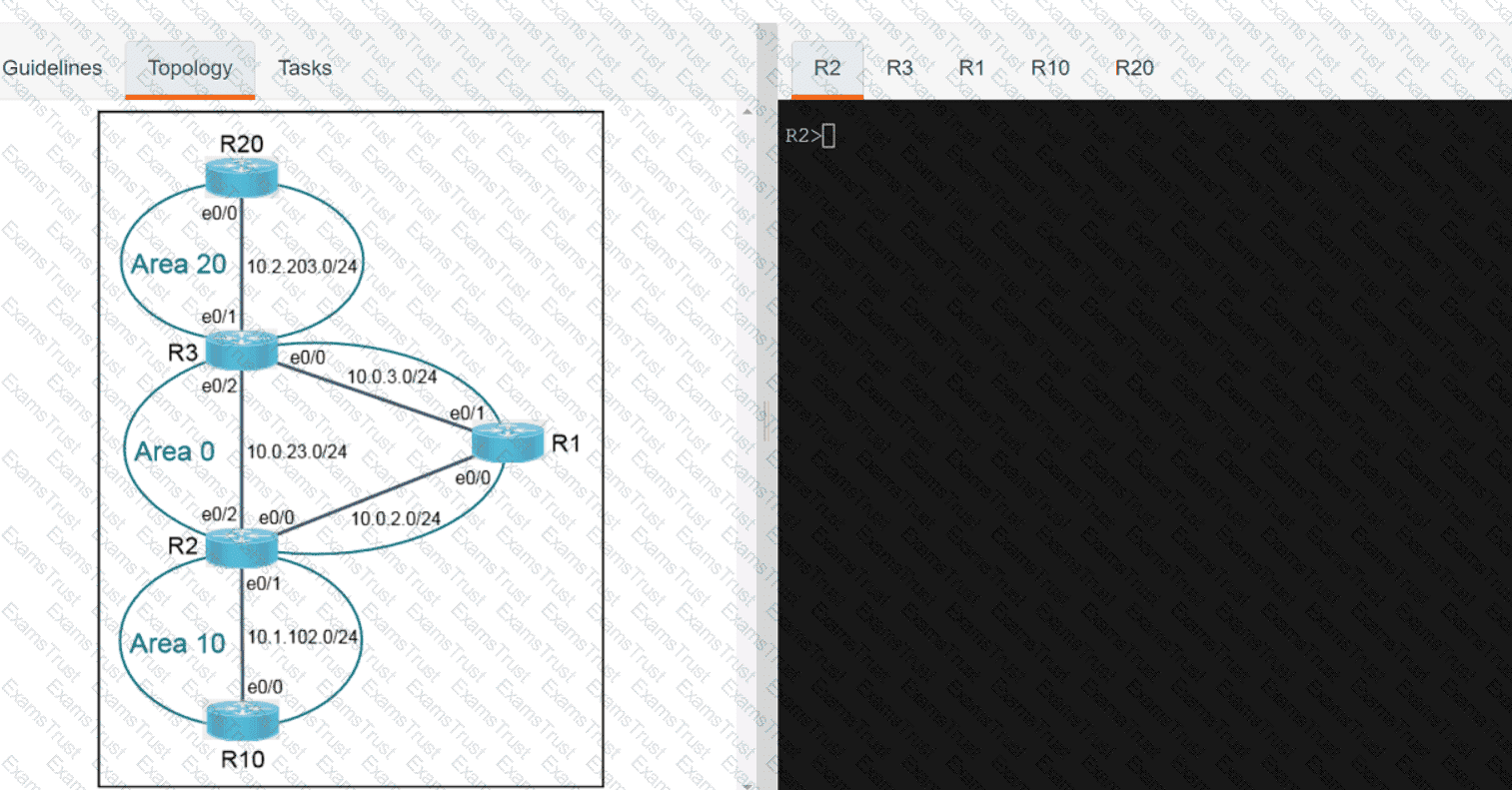
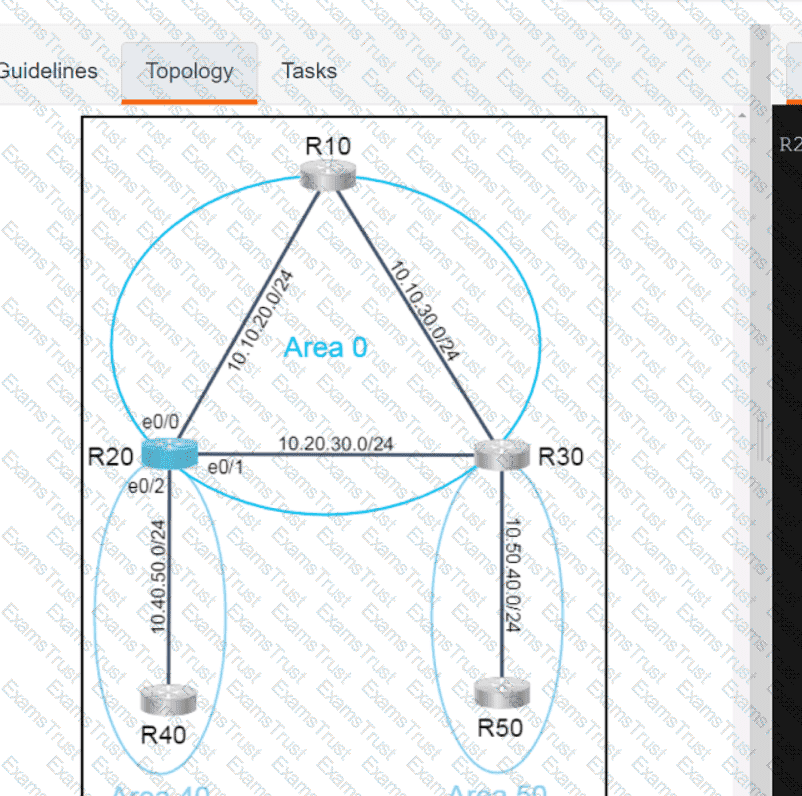
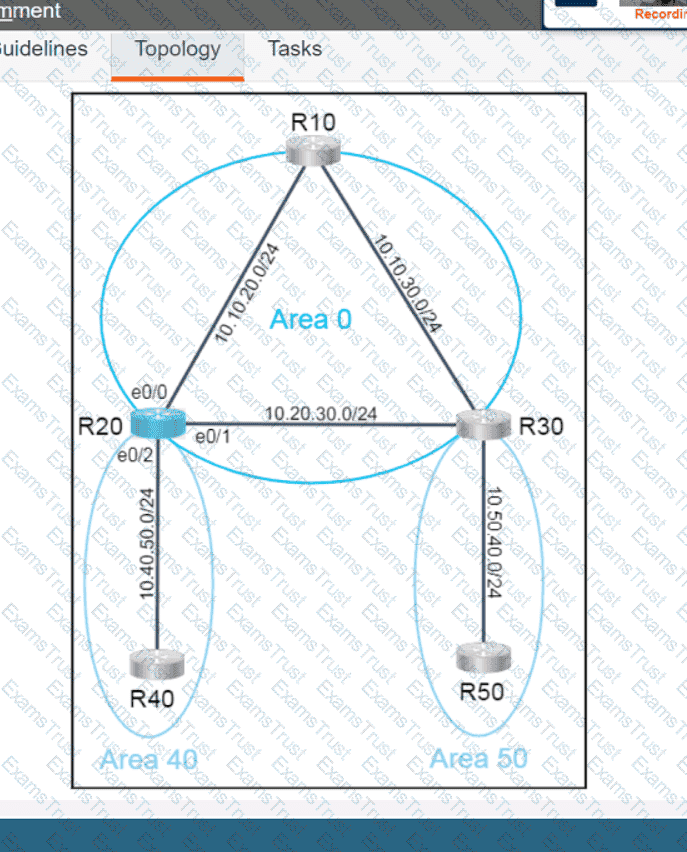
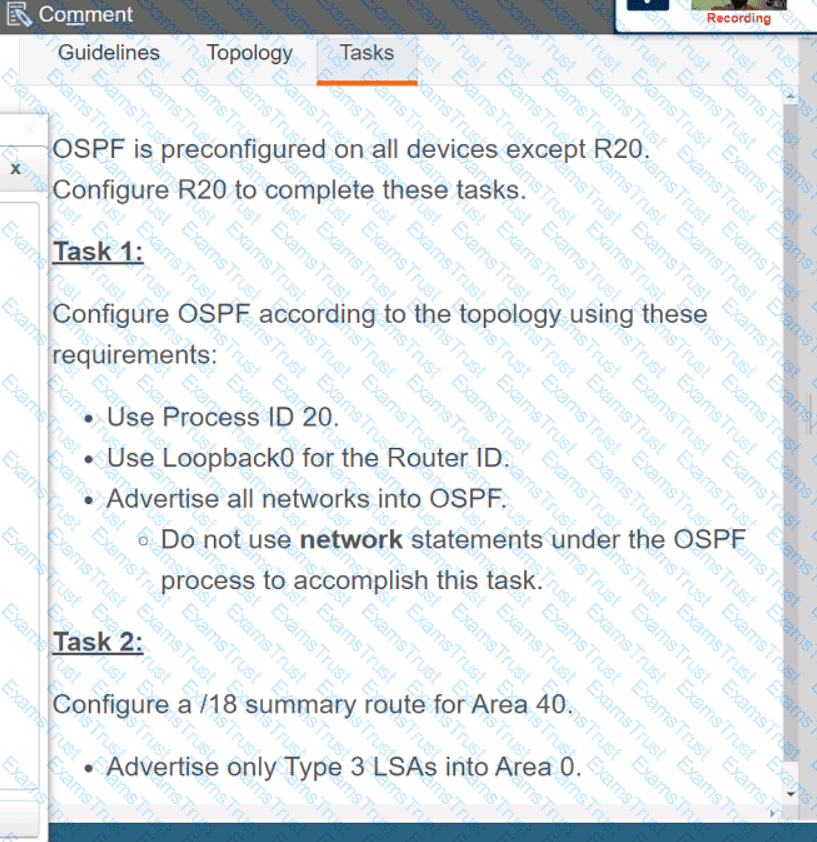
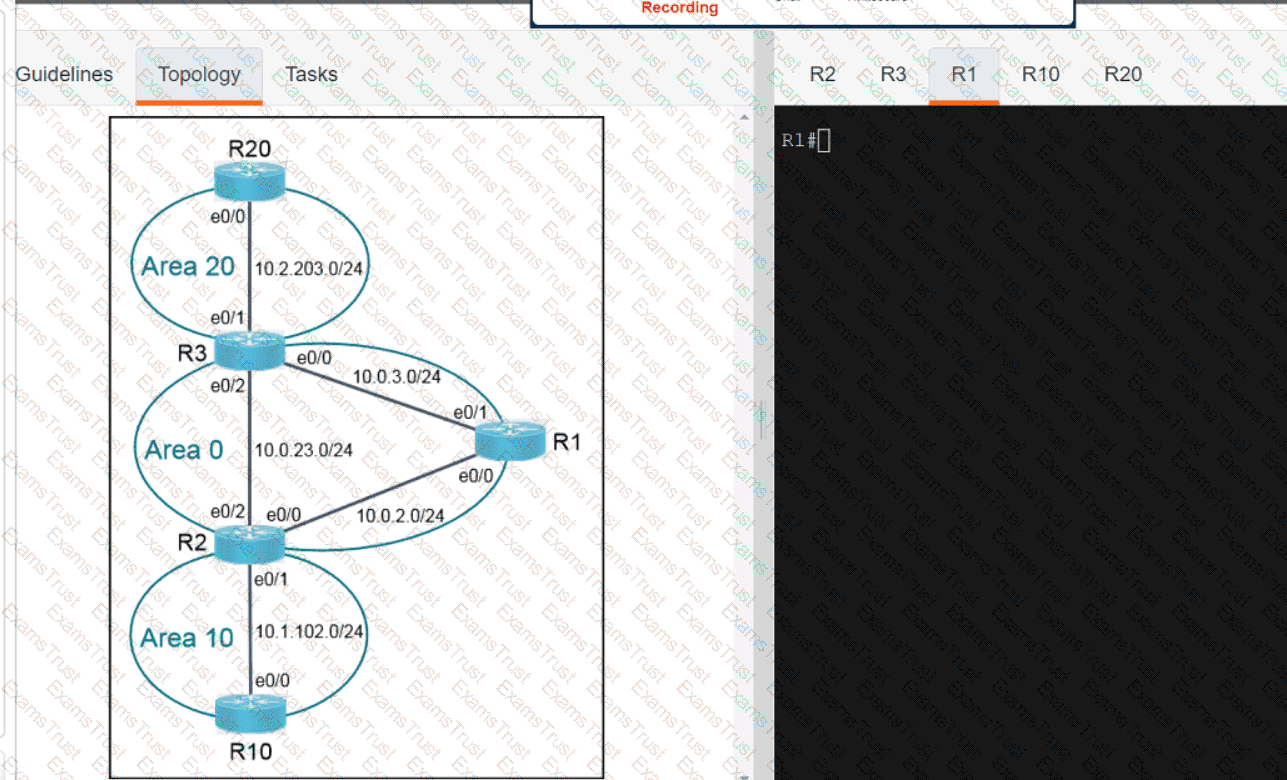
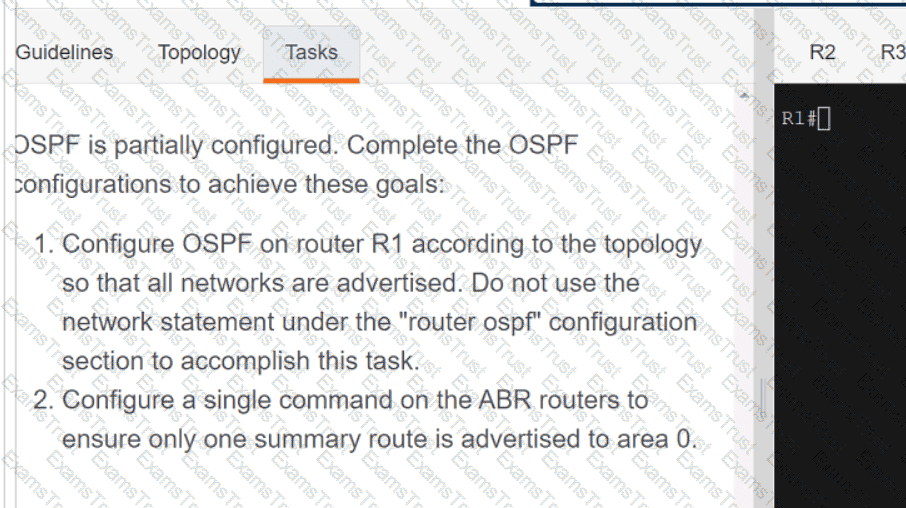
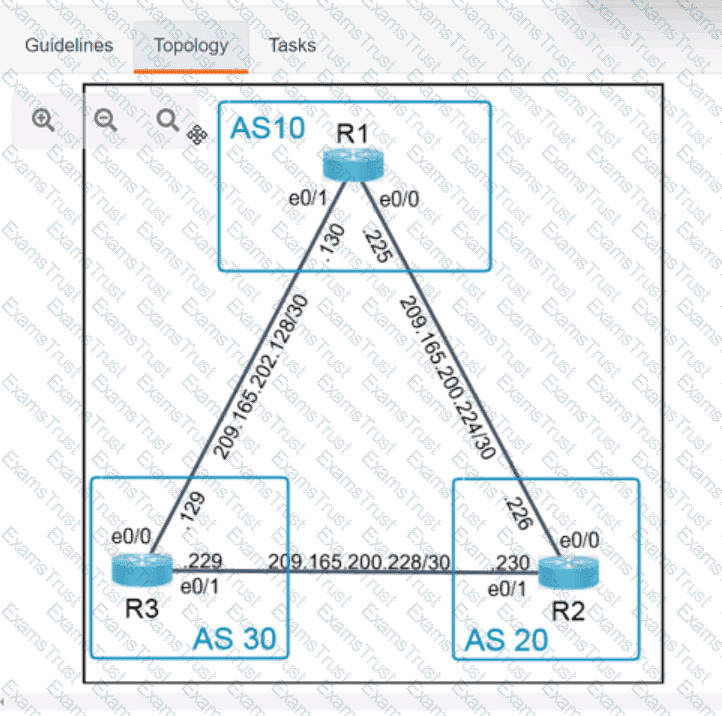
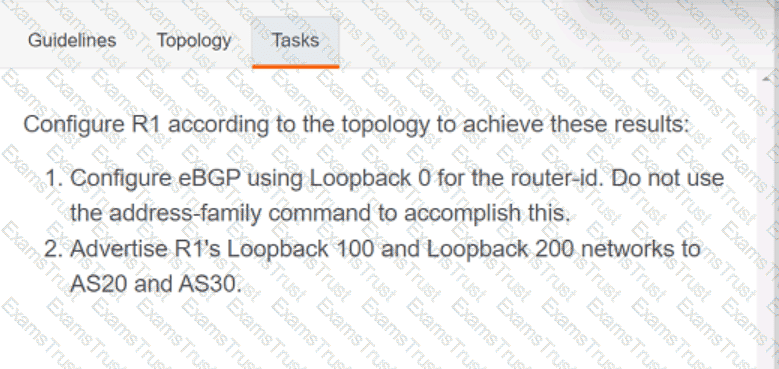
Why would an architect use an OSPF virtual link?
What is used by vManage to interact with Cisco SD-WAN devices in the fabric?
Refer to the exhibit. Which Python snippet stores the data structure of the device in JSON format?
A)

B)

C)

D)

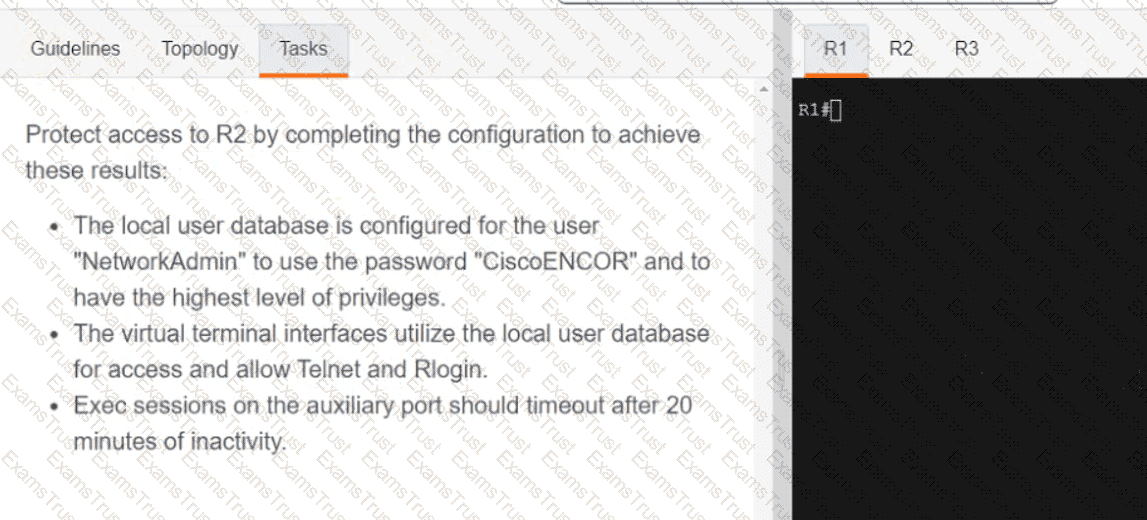
What is a fact about Cisco EAP-FAST?
Which language can be used to model configuration and state data?
What is required for a VXLAN tunnel endpoint to operate?
An engineer must protect their company against ransom ware attacks. Which solution allows the engineer to block the execution stage and prevent file encryption?
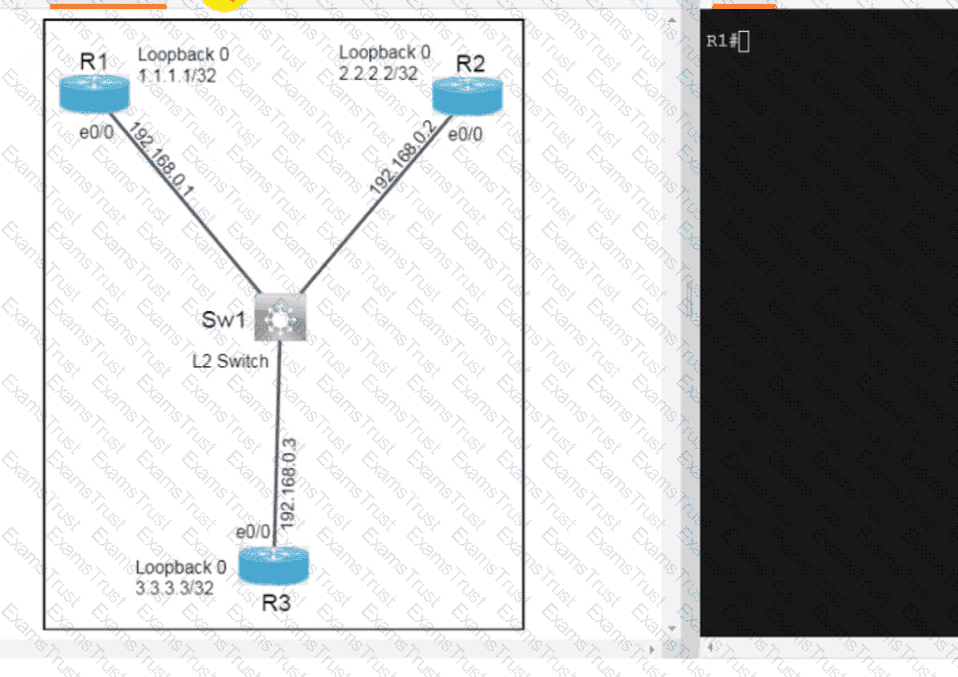
How do FHRPs differ from SSO?
What are two methods of ensuring that the multicast RPF check passes without changing the unicast routing table? (Choose two.)
Which message type is valid for IGMPv3?

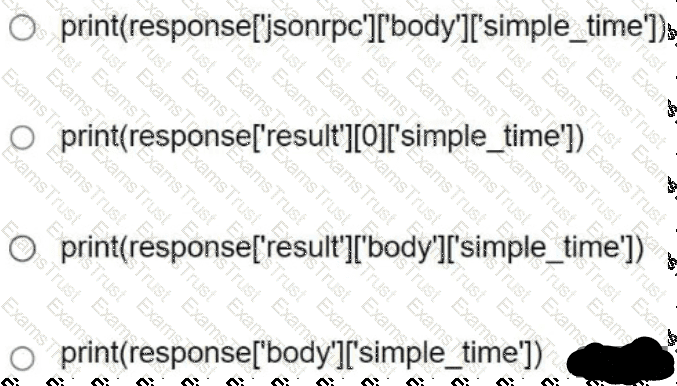
Refer to the exhibit. Based on this JSON response:

Which Python statement parses the response and prints "10:42:36.111 UTC Mon Jan 1 2024"?
Which consideration must be made when using BFD in a network design?
What is a TLOC in a Cisco SD-WAN deployment?
How does Cisco DNA Center perform a network discovery?
Which feature provides data-plane security for Cisco Catalyst SD-WAN networks'?
Which function is performed by vSmart in the Cisco Catalyst SD-WAN architecture?
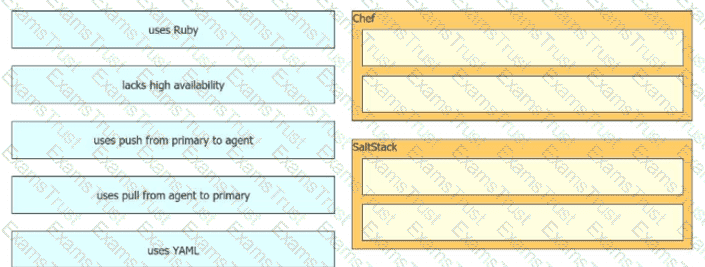
Drag and drop the automation characteristics from the left onto the appropriate tools on the right. Not all options are used.
What is one role of an AP join profile on a Cisco wireless network?