
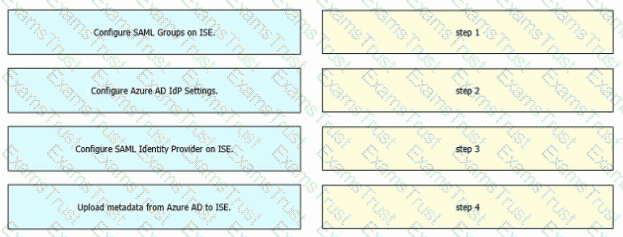
Refer to the exhibit. An engineer must configure SAML single sign-on in Cisco ISE to use Microsoft Azure AD as an identity provider. Drag and drop the steps from the left into the sequence on the right to configure Cisco ISE with SAML single sign-on.
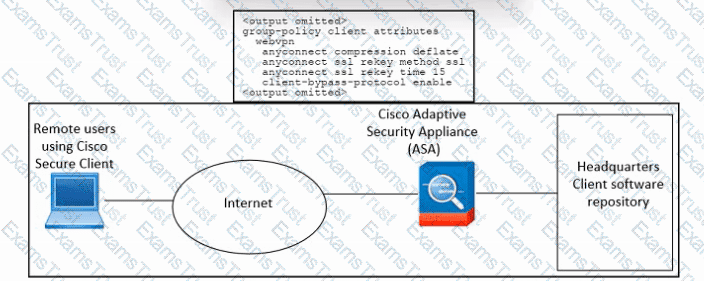
Refer to the exhibit. An engineer must configure Cisco ASA so that the Secure Client deployment is removed when the user laptop disconnects from the VPN. The indicated configuration was applied to the Cisco ASA firewall. Which command must be run to meet the requirement?
According to Cisco Security Reference Architecture, which solution provides threat intelligence and malware analytics?

Refer to the exhibit. An engineer must configure SAML SSO in Cisco ISE to use Microsoft Azure AD as an identity provider. These configurations were performed:
Configure a SAML IdP in ISE.
Configure the Azure AD IdP settings.
Which two actions must the engineer take in Cisco ISE? (Choose two.)

Refer to the exhibit. An engineer must configure a remote access IPsec/IKEv2 VPN that will use SHA-512 on a Cisco ASA firewall. The indicated configuration was applied to the firewall; however, the tunnel fails to establish. Which command must be run to meet the requirement?
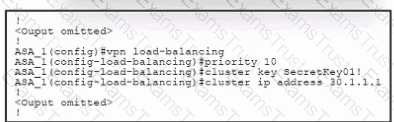
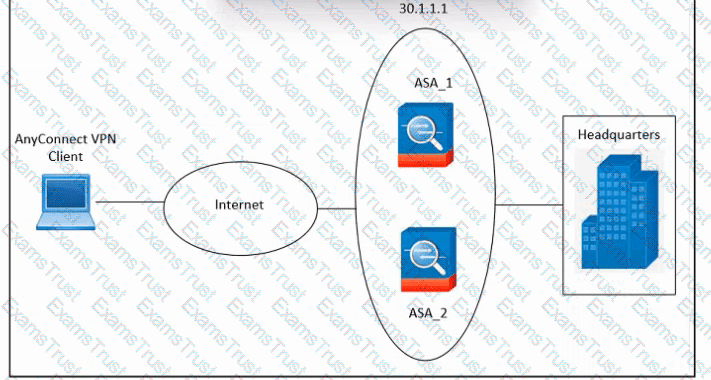
Refer to the exhibit. An engineer must configure VPN load balancing across two Cisco ASA. The indicated configuration was applied to each firewall; however, the load-balancing encryption scheme fails to work. Which two commands must be run on each firewall to meet the requirements? (Choose two.)
Which attack mitigation must be in place to prevent an attacker from authenticating to a service using a brute force attack?
An engineer is configuring multifactor authentication using Duo. The implementation must use Duo Authentication Proxy and the Active Directory as an identity source. The company uses Azure and a local Active Directory. Which configuration is needed to meet the requirement?
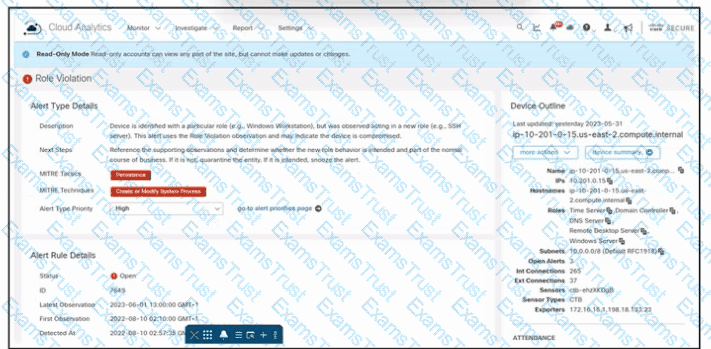
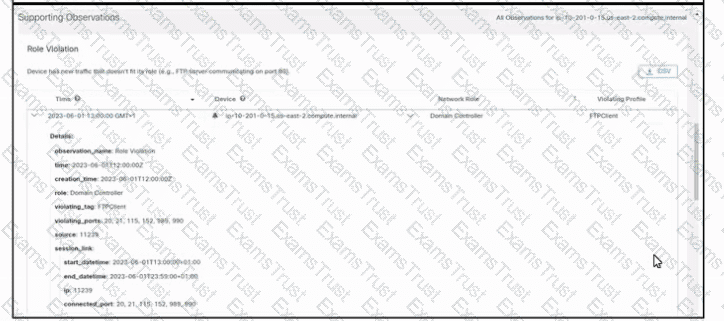
Refer to the exhibit. An engineer is troubleshooting an incident by using Cisco Secure Cloud Analytics. What is the cause of the issue?
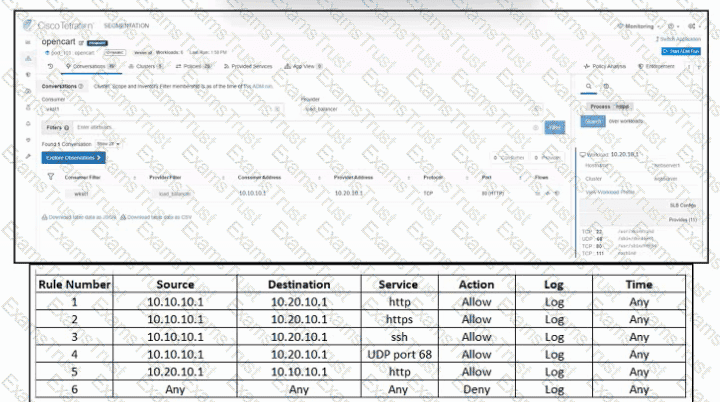
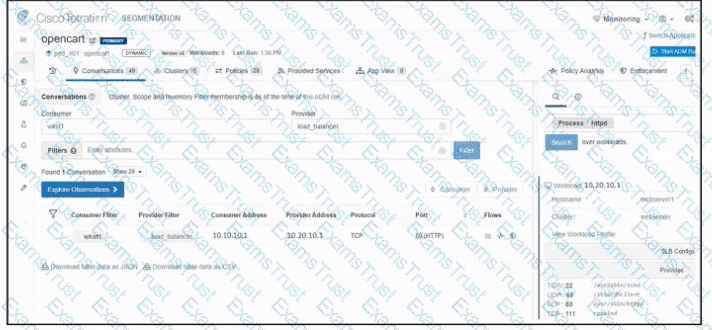
Refer to the exhibit. An engineer must create a firewall policy to allow web server communication only. The indicated firewall policy was applied; however, a recent audit requires that all firewall policies be optimized. Which set of rules must be deleted?
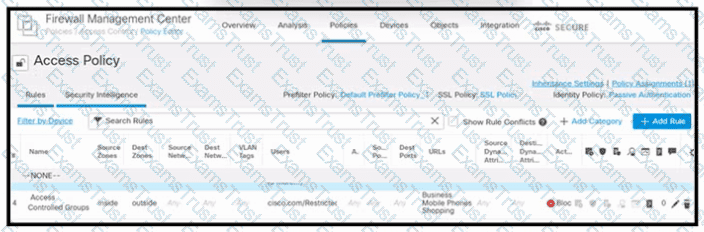
Refer to the exhibit. An engineer must create a policy in Cisco Secure Firewall Management Center to prevent restricted users from being able to browse any business or mobile phone shopping websites. The indicated policy was applied; however, the restricted users still can browse on the mobile phone shopping websites during business hours. What should be done to meet the requirement?
A recent InfraGard news release indicates the need to establish a risk ranking for all on-premises and cloud services. The ACME Corporation already performs risk assessments for on-premises services and has applied a risk ranking to them. However, the cloud services that were used lack risk rankings. What Cisco Umbrella function should be used to meet the requirement?

Refer to the exhibit. An engineer must create a segmentation policy in Cisco Secure Workload to block HTTP traffic. The indicated configuration was applied; however, HTTP traffic is still allowed. What should be done to meet the requirement?
Which concept is used in the Cisco SAFE key reference model?
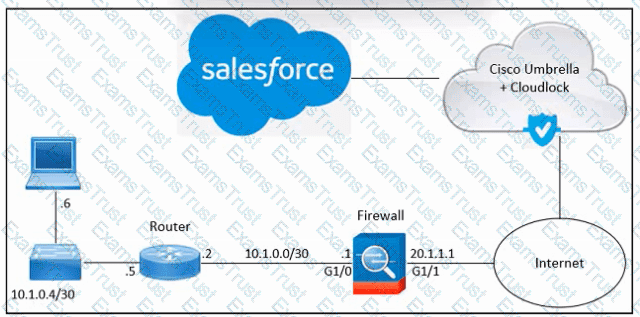
Refer to the exhibit. An engineer must integrate Cisco Cloudlock with Salesforce in an organization. Despite the engineer's successful execution of the Salesforce integration with Cloudlock, the administrator still lacks the necessary visibility. What should be done to meet the requirement?
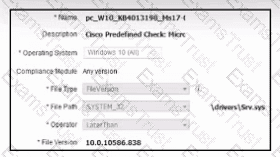
Refer to the exhibit. A security engineer must configure a posture policy in Cisco ISE to ensure that employee laptops have a critical patch for WannaCry installed before they can access the network. Which posture condition must the engineer configure?
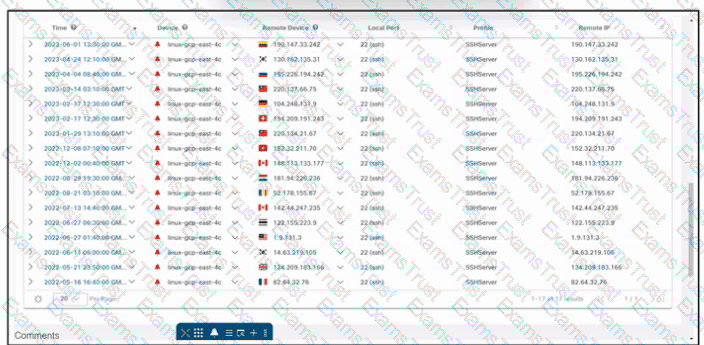
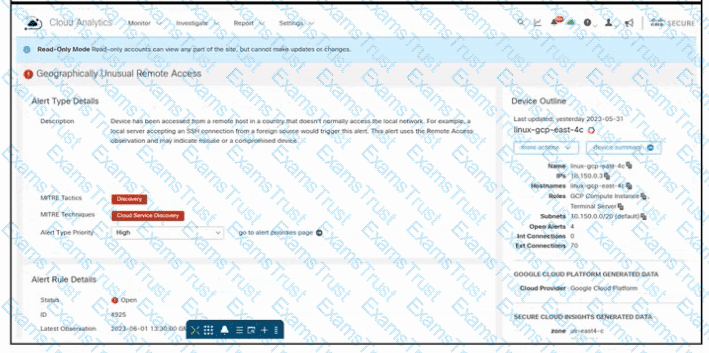
Refer to the exhibit. An engineer is investigating an issue by using Cisco Secure Cloud Analytics. The engineer confirms that the connections are unauthorized and informs the incident management team. Which two actions must be taken next? (Choose two.)
An engineer configures trusted endpoints with Active Directory with Device Health to determine if an endpoint complies with the policy posture. After a week, an alert is received by one user, reporting problems accessing an application. When the engineer verifies the authentication report, this error is found:
"Endpoint is not trusted because Cisco Secure Endpoint check failed, Check user's endpoint in Cisco Secure Endpoint."
Which action must the engineer take to permit access to the application again?