Which redundancy protocol must be implemented for IPsec stateless failover to work?
Refer to the exhibit.
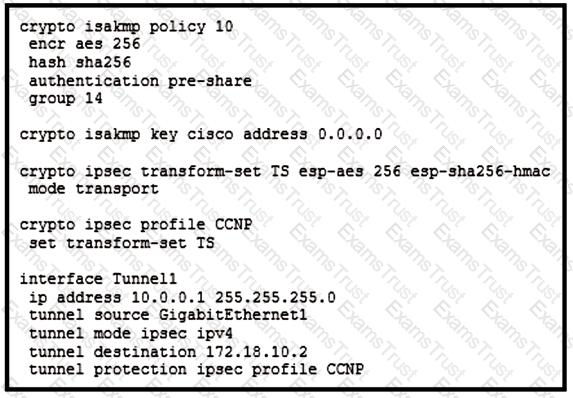
Which VPN technology is used in the exhibit?
Which VPN solution uses TBAR?
Which technology is used to send multicast traffic over a site-to-site VPN?
Which technology works with IPsec stateful failover?
Which VPN does VPN load balancing on the ASA support?
Which two remote access VPN solutions support SSL? (Choose two.)
Which two commands help determine why the NHRP registration process is not being completed even after the IPsec tunnel is up? (Choose two.)
Cisco AnyConnect clients need to transfer large files over the VPN sessions. Which protocol provides the best throughput?
Which benefit of FlexVPN is a limitation of DMVPN using IKEv1?
Refer to the exhibit.
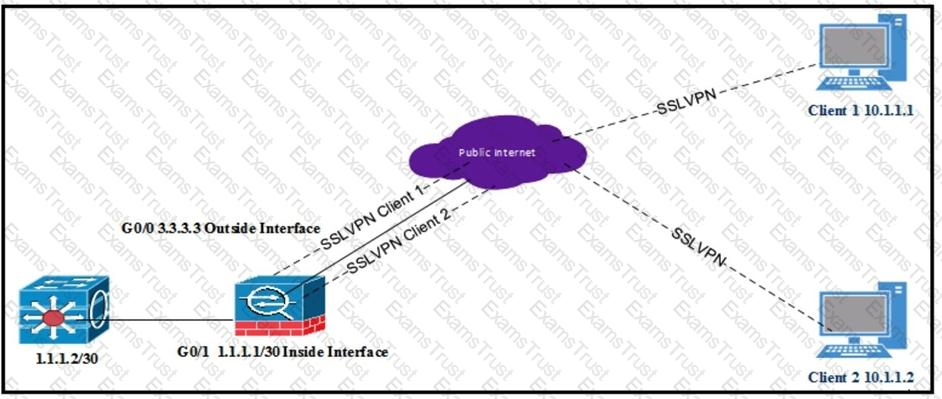
All internal clients behind the ASA are port address translated to the public outside interface that has an IP address of 3.3.3.3. Client 1 and client 2 have established successful SSL VPN connections to the ASA. What must be implemented so that "3.3.3.3" is returned from a browser search on the IP address?
Refer to the exhibit.
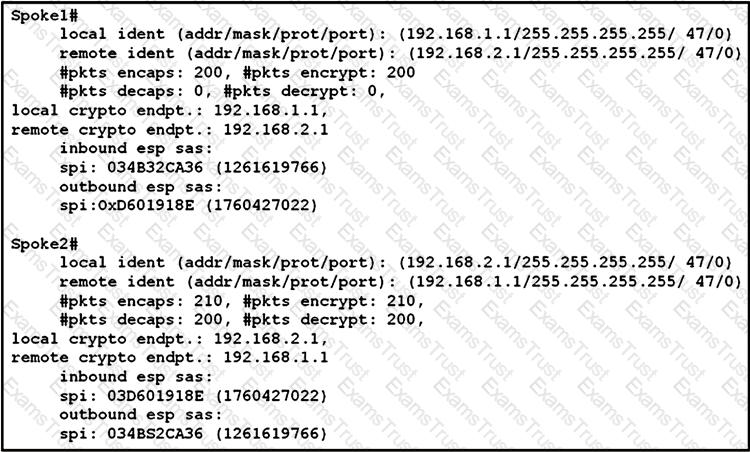
An engineer is troubleshooting a new GRE over IPsec tunnel. The tunnel is established but the engineer cannot ping from spoke 1 to spoke 2. Which type of traffic is being blocked?
Refer to the exhibit.
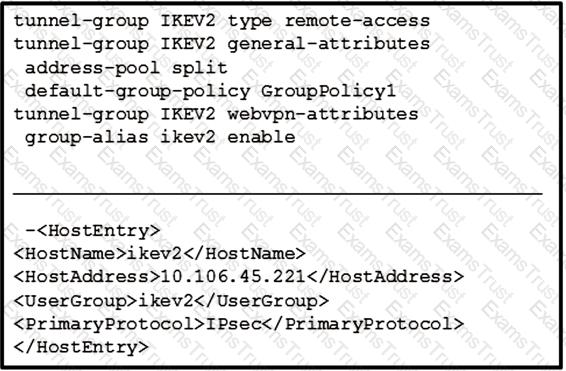
The customer can establish a Cisco AnyConnect connection without using an XML profile. When the host "ikev2" is selected in the AnyConnect drop down, the connection fails. What is the cause of this issue?
Refer to the exhibit.
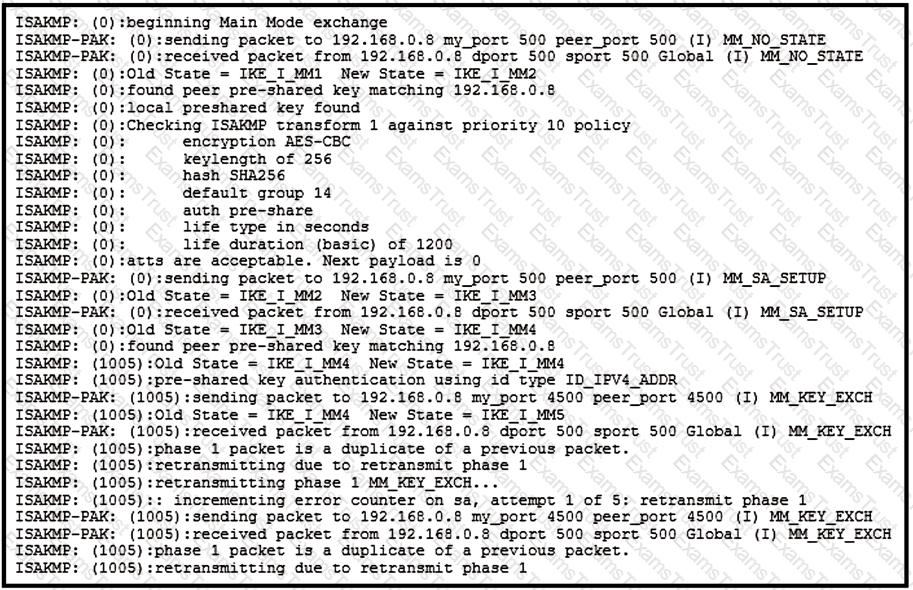
A site-to-site tunnel between two sites is not coming up. Based on the debugs, what is the cause of this issue?
Refer to the exhibit.
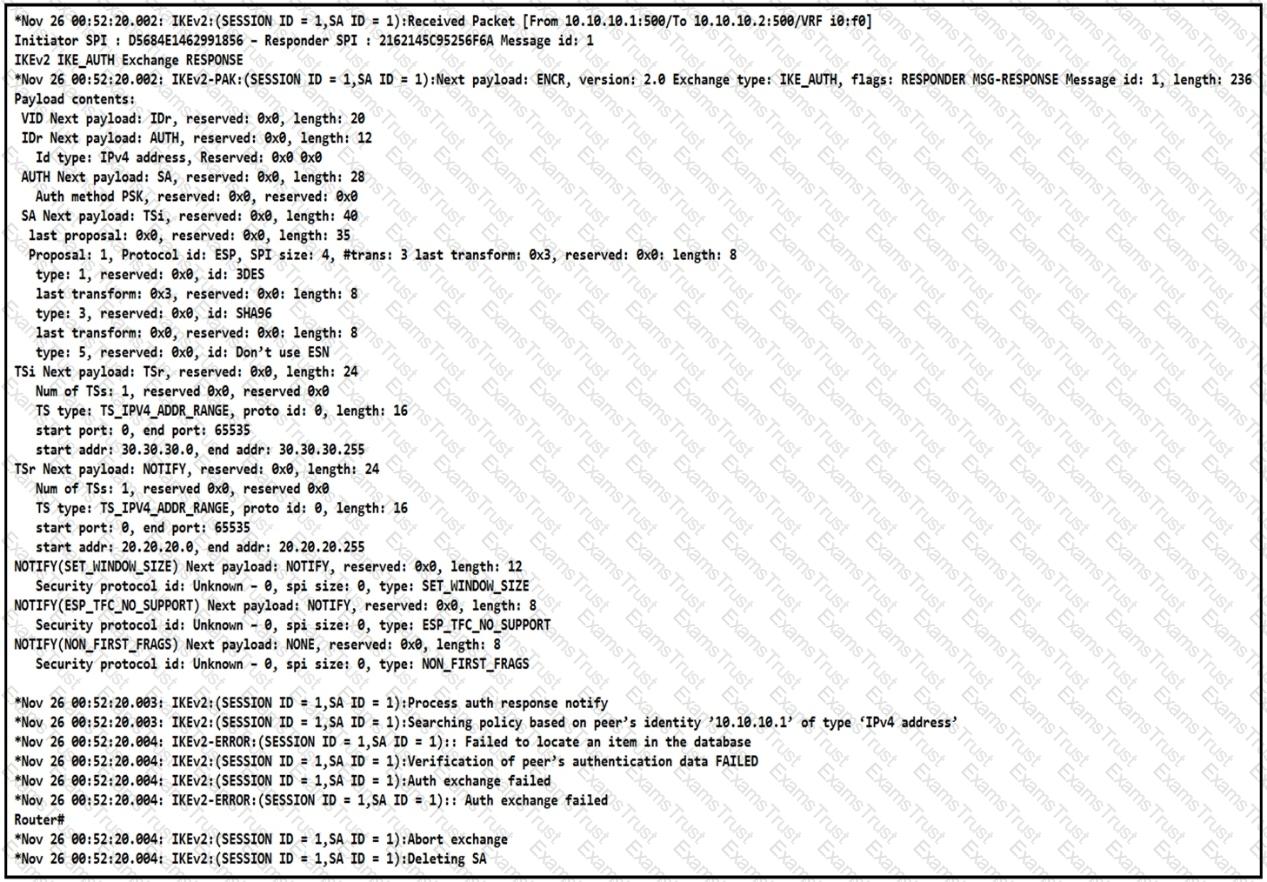
The IKEv2 site-to-site VPN tunnel between two routers is down. Based on the debug output, which type of mismatch is the problem?
An engineer is troubleshooting a new DMVPN setup on a Cisco IOS router. After the show crypto isakmp sa command is issued, a response is returned of "MM_NO_STATE." Why does this failure occur?
Which command is used to troubleshoot an IPv6 FlexVPN spoke-to-hub connectivity failure?
In a FlexVPN deployment, the spokes successfully connect to the hub, but spoke-to-spoke tunnels do not form. Which troubleshooting step solves the issue?
Refer to the exhibit.
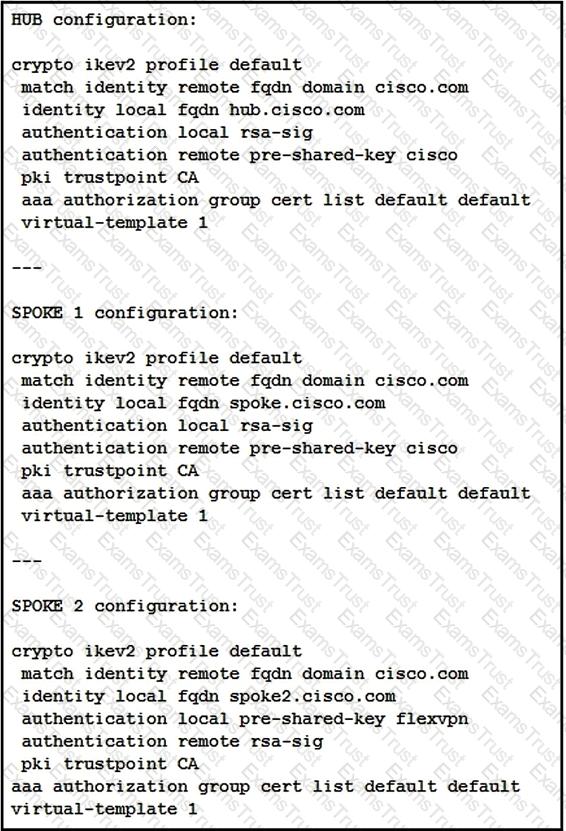
What is a result of this configuration?
Refer to the exhibit.
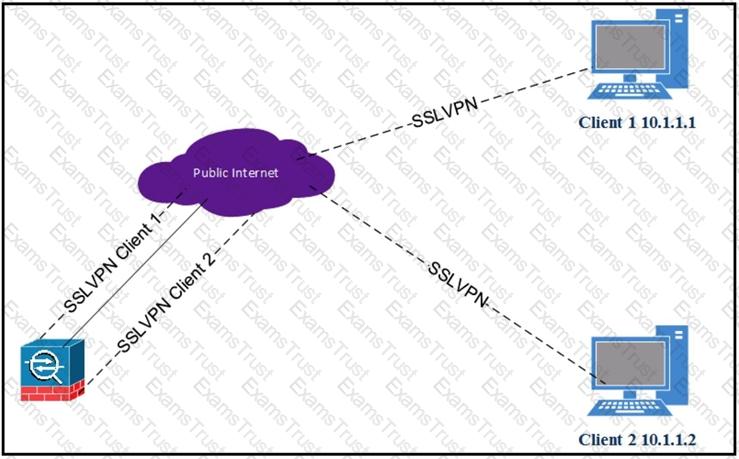
Client 1 cannot communicate with client 2. Both clients are using Cisco AnyConnect and have established a successful SSL VPN connection to the hub ASA. Which command on the ASA is missing?
Refer to the exhibit.
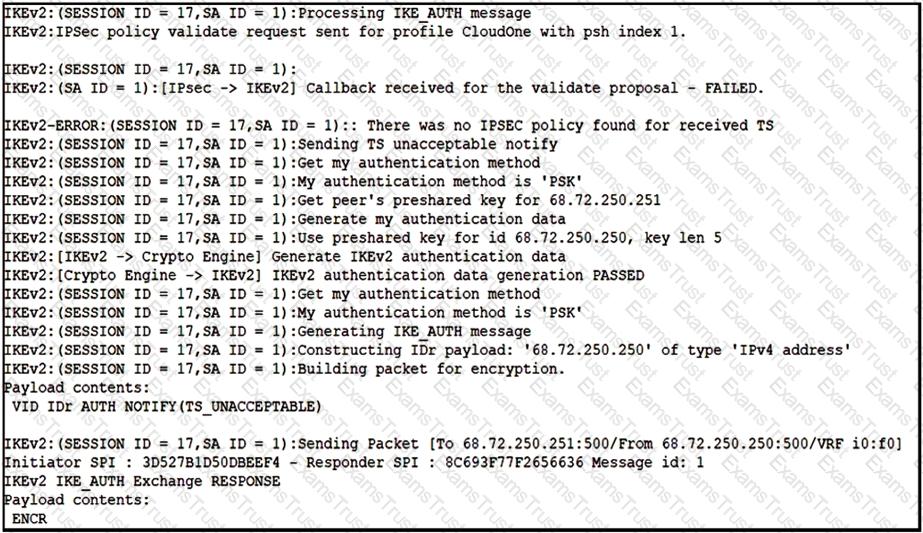
Based on the debug output, which type of mismatch is preventing the VPN from coming up?
Refer to the exhibit.
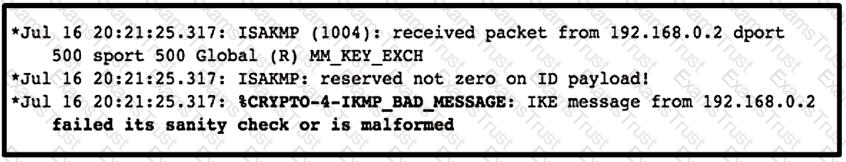
Which type of mismatch is causing the problem with the IPsec VPN tunnel?
A second set of traffic selectors is negotiated between two peers using IKEv2. Which IKEv2 packet will contain details of the exchange?
Which two changes must be made in order to migrate from DMVPN Phase 2 to Phase 3 when EIGRP is configured? (Choose two.)
Which statement about GETVPN is true?
On a FlexVPN hub-and-spoke topology where spoke-to-spoke tunnels are not allowed, which command is needed for the hub to be able to terminate FlexVPN tunnels?
Refer to the exhibit.
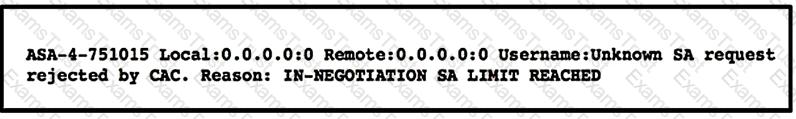
A customer cannot establish an IKEv2 site-to-site VPN tunnel between two Cisco ASA devices. Based on the syslog message, which action brings up the VPN tunnel?
Drag and drop the correct commands from the night onto the blanks within the code on the left to implement a design that allow for dynamic spoke-to-spoke communication. Not all comments are used.
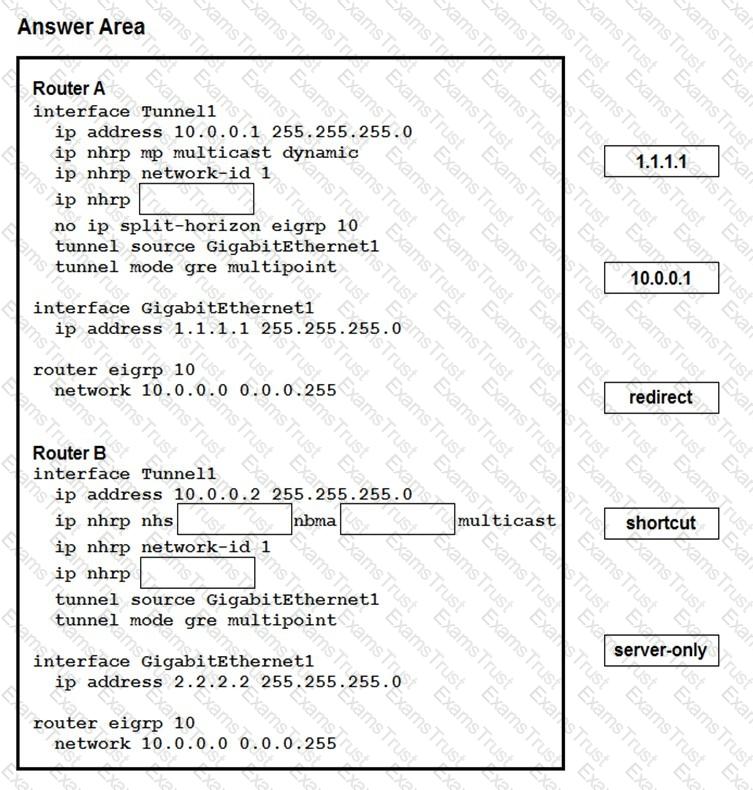
Which method dynamically installs the network routes for remote tunnel endpoints?
Refer to the exhibit.
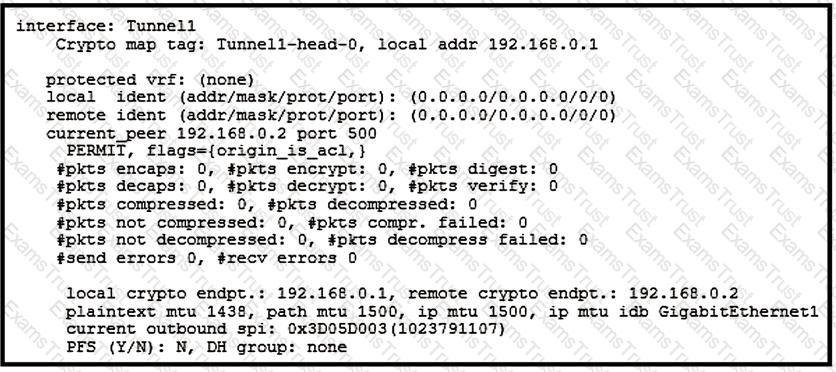
Which two tunnel types produce the show crypto ipsec sa output seen in the exhibit? (Choose two.)
Refer to the exhibit.
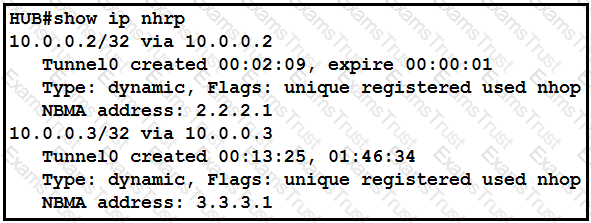
The DMVPN tunnel is dropping randomly and no tunnel protection is configured. Which spoke configuration mitigates tunnel drops?
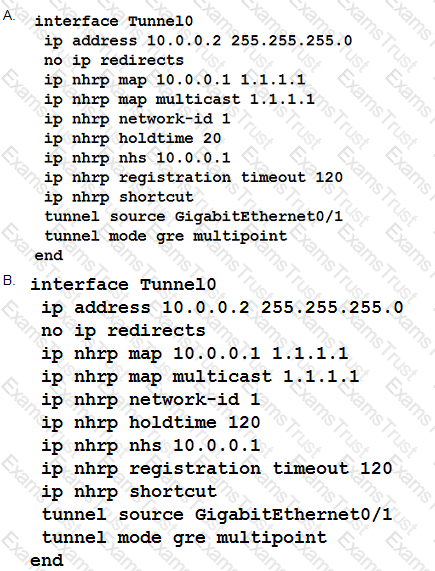
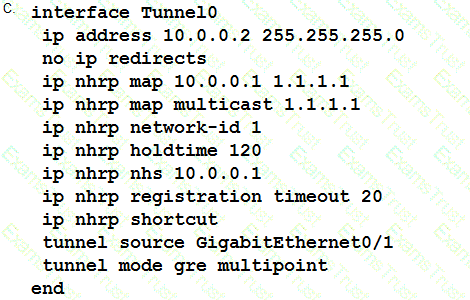
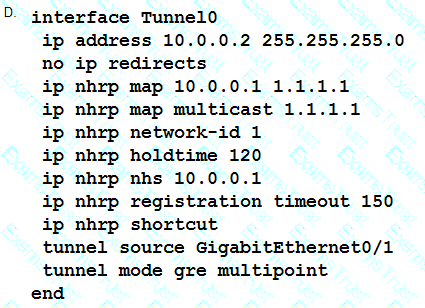
Which two parameters help to map a VPN session to a tunnel group without using the tunnel-group list? (Choose two.)
Which two features provide headend resiliency for Cisco AnyConnect clients? (Choose two.)
Which clientless SSLVPN supported feature works when the http-only-cookie command is enabled?
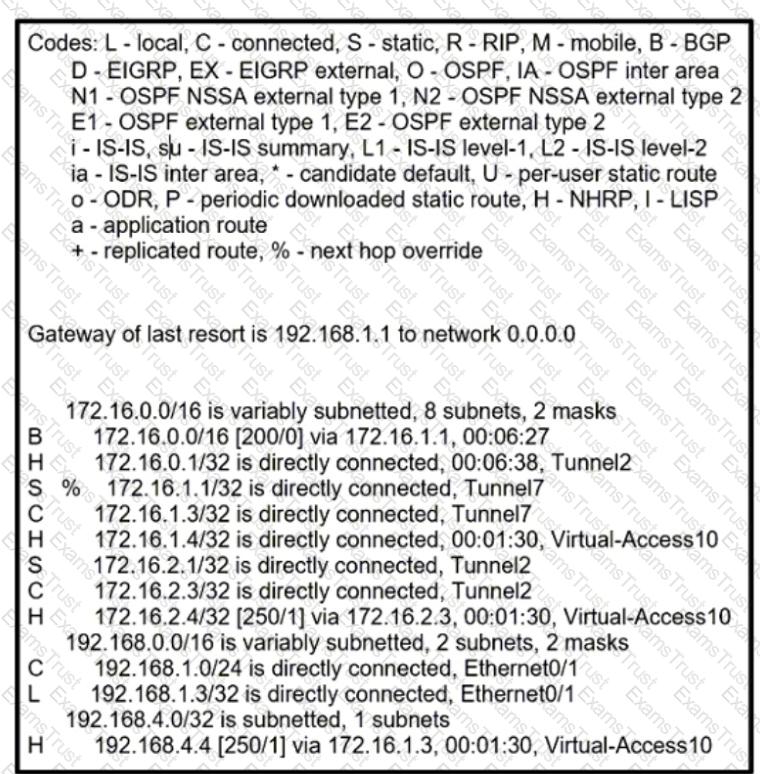
Given the output of the show ip route command, which remote access VPN technology is in use?
The corporate network security policy requires that all internet and network traffic must be tunneled to the corporate office. Remote workers have been provided with printers to use locally at home while they are remotely connected to the corporate network. Which two steps must be executed to allow printing to the local printers? (Choose two.)
A user is experiencing delays on audio calls over a Cisco AnyConnect VPN. Which implementation step resolves this issue?
A network administrator wants to block traffic to a known malware site at and all subdomains while ensuring no packets from any internal client are sent to that site. Which type of policy must the network administrator use to accomplish this goal?
An engineer has configured Cisco AnyConnect VPN using IKEv2 on a Cisco IOS router. The user cannot connect in the Cisco AnyConnect client, but receives an alert message "Use a browser to gain access." Which action does the engineer take to resolve this issue?
An organization wants to distribute remote access VPN load across 12 VPN headend locations supporting 25,000 simultaneous users. Which load balancing method meets this requirement?
A network engineer is setting up a clientless SSLVPN on a Cisco ASA. Remote users must be able to access an internal webserver via the URL example.com. Which two steps accomplish this task? (Choose two.)
Which two features are valid backup options for an IOS FlexVPN client? (Choose two.)
An organization wants to implement a site-to-site VPN solution that must be able to support 350 sites with direct communications between all sites, fully encrypt the packet header and payload, and support propagation of routing information over IPsec. Which solution meets these requirements?
Which two NHRP functions are specific to DMVPN Phase 3 implementation? (Choose two.)