Which term refers to an endpoint agent that tries to join an 802 1X-enabled network?
A user misplaces a personal phone and wants to blacklist the device from accessing the company network. The company uses Cisco ISE for corporate and BYOD device authentication. Which action must the user take in Cisco ISE?
If a user reports a device lost or stolen, which portal should be used to prevent the device from accessing the network while still providing information about why the device is blocked?
What is an advantage of using EAP-TLS over EAP-MS-CHAPv2 for client authentication?
An engineer is working with a distributed deployment of Cisco ISE and needs to configure various network probes to collect a set of attributes from the endpoints on the network. Which node should be used to accomplish this task?
An administrator needs to allow guest devices to connect to a private network without requiring usernames and passwords. Which two features must be configured to allow for this? (Choose two.)
The IT manager wants to provide different levels of access to network devices when users authenticate using TACACS+. The company needs specific commands to be allowed based on the Active Directory group membership of the different roles within the IT department. The solution must minimize the number of objects created in Cisco ISE. What must be created to accomplish this task?
A Cisco ISE administrator must restrict specific endpoints from accessing the network while in closed mode. The requirement is to have Cisco ISE centrally store the endpoints to restrict access from. What must be done to accomplish this task''
A user is attempting to register a BYOD device to the Cisco ISE deployment, but needs to use the onboarding policy to request a digital certificate and provision the endpoint. What must be configured to accomplish this task?
A Cisco ISE administrator needs to ensure that guest endpoint registrations are only valid for 1 day. When testing the guest policy flow, the administrator sees that the Cisco ISE does not delete the endpoint in the Guest Endpoints identity store after one day and allows access to the guest network after that period. Which configuration is causing this problem?
A network engineer must configure a policy rule to check the endpoint. The policy must ensure disk encryption is enabled and the appropriate antivirus software version is installed. Which configuration must the engineer apply to the rule?
An administrator made changes in Cisco ISE and needs to apply new permissions for endpoints that have already been authenticated by sending a CoA packet to the network devices. Which IOS command must be configured on the devices to accomplish this goal?
Which default endpoint identity group does an endpoint that does not match any profile in Cisco ISE become a member of?
A laptop was stolen and a network engineer added it to the block list endpoint identity group What must be done on a new Cisco ISE deployment to redirect the laptop and restrict access?
What is an advantage of TACACS+ versus RADIUS authentication when reviewing reports in Cisco ISE?
Which nodes are supported in a distributed Cisco ISE deployment?
Which three default endpoint identity groups does cisco ISE create? (Choose three)
Which two Cisco ISE deployment models require two nodes configured with dedicated PAN and MnT personas? (Choose two.)
An engineer is designing a new distributed deployment for Cisco ISE in the network and is considering failover options for the admin nodes. There is a need to ensure that an admin node is available for configuration of policies at all times. What is the requirement to enable this feature?
Which CLI command must be configured on the switchport to immediately run the MAB process if a non-802.1X capable endpoint connects to the port?
Which interface-level command is needed to turn on 802 1X authentication?
Which RADIUS attribute is used to dynamically assign the inactivity active timer for MAB users from the Cisco ISE node'?
What is a difference between RADIUS and TACACS+?
An administrator is configuring posture with Cisco ISE and wants to check that specific services are present on the workstations that are attempting to access the network. What must be configured to accomplish this goal?
An engineer is implementing network access control using Cisco ISE and needs to separate the traffic based on the network device ID and use the IOS device sensor capability. Which probe must be used to accomplish this task?
Which Cisco ISE deployment model is recommended for an enterprise that has over 50,000 concurrent active endpoints?
A new employee just connected their workstation to a Cisco IP phone. The network administrator wants to ensure that the Cisco IP phone remains online when the user disconnects their Workstation from the corporate network Which CoA configuration meets this requirement?
An engineer is unable to use SSH to connect to a switch after adding the required CLI commands to the device to enable TACACS+. The device administration license has been added to Cisco ISE, and the required policies have been created. Which action is needed to enable access to the switch?
Which two features are available when the primary admin node is down and the secondary admin node has not been promoted? (Choose two.)
An administrator is configuring the Native Supplicant Profile to be used with the Cisco ISE posture agents and needs to test the connection using wired devices to determine which profile settings are available. Which two configuration settings should be used to accomplish this task? (Choose two.)
An engineer is creating a new authorization policy to give the endpoints access to VLAN 310 upon successful authentication The administrator tests the 802.1X authentication for the endpoint and sees that it is authenticating successfully What must be done to ensure that the endpoint is placed into the correct VLAN?
An engineer needs to configure a Cisco ISE server to issue a CoA for endpoints already authenticated to access the network. The CoA option must be enforced on a session, even if there are multiple active sessions on a port. What must be configured to accomplish this task?
An organization is adding nodes to their Cisco ISE deployment and has two nodes designated as primary and secondary PAN and MnT nodes. The organization also has four PSNs An administrator is adding two more PSNs to this deployment but is having problems adding one of them What is the problem?
An administrator is configuring a new profiling policy within Cisco ISE The organization has several endpoints that are the same device type and all have the same Block ID in their MAC address. The profiler does not currently have a profiling policy created to categorize these endpoints. therefore a custom profiling policy must be created Which condition must the administrator use in order to properly profile an ACME Al Connector endpoint for network access with MAC address
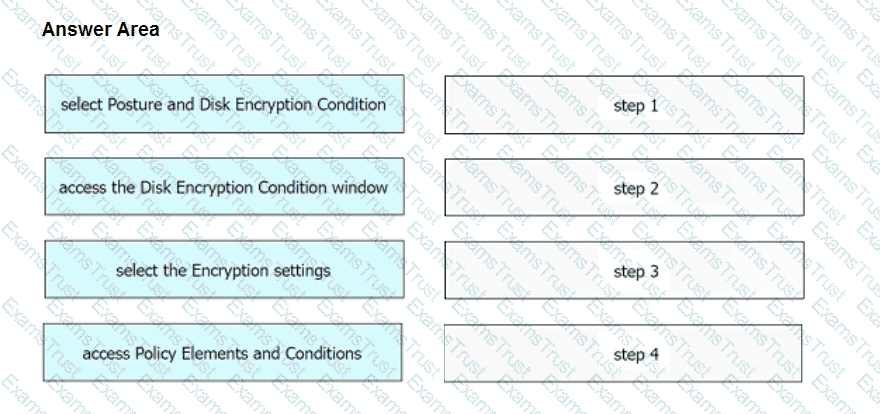
An engineer needs to configure a compliance policy on Cisco ISE to ensure that the latest encryption software is running on the C drive of all endpoints. Drag and drop the configuration steps from the left into the sequence on the right to accomplish this task.
An engineer is migrating users from MAB to 802.1X on the network. This must be done during normal business hours with minimal impact to users. Which CoA method should be used?
What does the dot1x system-auth-control command do?
A network engineer must enable a profiling probe. The profiling must take details through the Active Directory. Where in the Cisco ISE interface would the engineer enable the probe?
NO: 37
In which two ways can users and endpoints be classified for TrustSec?
(Choose Two.)
The Cisco Wireless LAN Controller and guest portal must be set up in Cisco ISE. These configurations were performed:
• configured all the required Cisco Wireless LAN Controller configurations
• added the wireless controller to Cisco ISE network devices
• created an endpoint identity group
• configured credentials to be sent by email
• configured the SMTP server
• configured an authorization profile with redirection to the guest portal and redirected the access control list
• configured an authentication policy for MAB users
• created an authorization policy
Which two components would be required to complete the configuration? (Choose two.)
An engineer must use Cisco ISE profiler services to provide network access to Cisco IP phones that cannot support 802.1X. Cisco ISE is configured to use the access switch device sensor information — system-description and platform-type — to profile Cisco IP phones and allow access.
Which two protocols must be configured on the switch to complete the configuration? (Choose two.)
An engineer must configure Cisco ISE to provide internet access for guests in which guests are required to enter a code to gain network access. Which action accomplishes the goal?
Which two probes must be enabled for the ARP cache to function in the Cisco ISE profile service so that a user can reliably bind the IP address and MAC addresses of endpoints? (Choose two.)
An engineer is configuring web authentication using non-standard ports and needs the switch to redirect traffic to the correct port. Which command should be used to accomplish this task?
What are the minimum requirements for deploying the Automatic Failover feature on Administration nodes in a distributed Cisco ISE deployment?
An administrator has added a new Cisco ISE PSN to their distributed deployment. Which two features must the administrator enable to accept authentication requests and profile the endpoints correctly, and add them to their respective endpoint identity groups? (Choose two )
Which protocol must be allowed for a BYOD device to access the BYOD portal?
An engineer is configuring static SGT classification. Which configuration should be used when authentication is disabled and third-party switches are in use?
Refer to the exhibit.
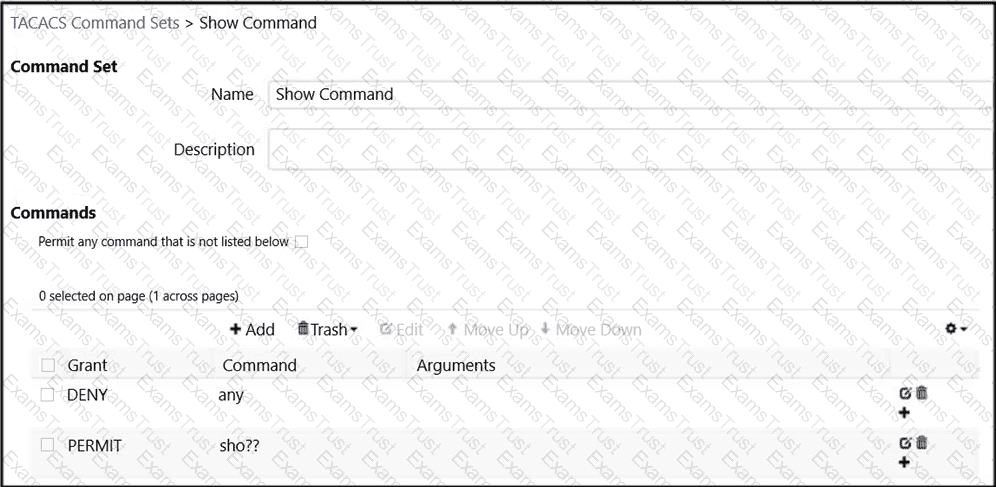
An engineer is creating a new TACACS* command set and cannot use any show commands after togging into the device with this command set authorization Which configuration is causing this issue?
An administrator replaced a PSN in the distributed Cisco ISE environment. When endpoints authenticate to it, the devices are not getting the right profiles or attributes and as a result, are not hitting the correct policies. This was working correctly on the previous PSN. Which action must be taken to ensure the endpoints get identified?
An administrator is attempting to replace the built-in self-signed certificates on a Cisco ISE appliance. The CA is requesting some information about the appliance in order to sign the new certificate. What must be done in order to provide the CA this information?
An engineer is configuring posture assessment for their network access control and needs to use an agent that supports using service conditions as conditions for the assessment. The agent should be run as a background process to avoid user interruption but when it is run. the user can see it. What is the problem?
An administrator is configuring a Cisco ISE posture agent in the client provisioning policy and needs to ensure that the posture policies that interact with clients are monitored, and end users are required to comply with network usage rules Which two resources must be added in Cisco ISE to accomplish this goal? (Choose two)
What is needed to configure wireless guest access on the network?
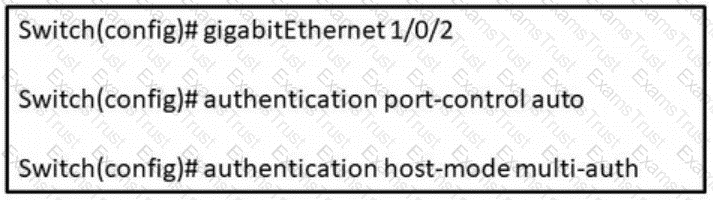
Refer to the exhibit. In which scenario does this switch configuration apply?
An engineer is configuring Cisco ISE for guest services They would like to have any unregistered guests redirected to the guest portal for authentication then have a CoA provide them with full access to the network that is segmented via firewalls Why is the given configuration failing to accomplish this goal?
An adminístrator is migrating device administration access to Cisco ISE from the legacy TACACS+ solution that used only privilege 1 and 15 access levels. The organization requires more granular controls of the privileges and wants to customize access levels 2-5 to correspond with different roles and access needs. Besides defining a new shell profile in Cisco ISE. what must be done to accomplish this configuration?
Refer to the exhibit.
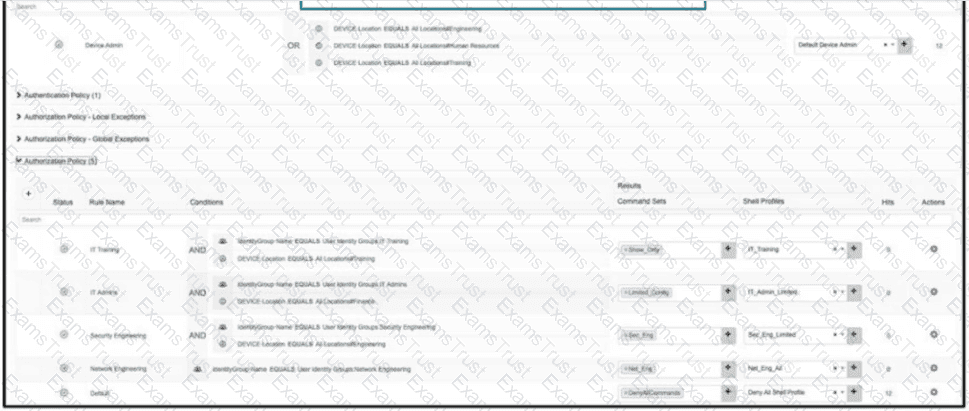
An organization recently implemented network device administration using Cisco ISE. Upon testing the ability to access all of the required devices, a user in the Cisco ISE group IT Admins is attempting to login to a device in their organization's finance department but is unable to. What is the problem?
An engineer needs to configure Cisco ISE Profiling Services to authorize network access for IP speakers that require access to the intercom system. This traffic needs to be identified if the ToS bit is set to 5 and the destination IP address is the intercom system. What must be configured to accomplish this goal?
Which Cisco ISE service allows an engineer to check the compliance of endpoints before connecting to the network?
An engineer is assigned to enhance security across the campus network. The task is to enable MAB across all access switches in the network. Which command must be entered on the switch to enable MAB?
Which two actions occur when a Cisco ISE server device administrator logs in to a device? (Choose two)
Which compliance status is set when a matching posture policy has been defined for that endpomt. but all the mandatory requirements during posture assessment are not met?
Which two fields are available when creating an endpoint on the context visibility page of Cisco IS? (Choose two)
An employee logs on to the My Devices portal and marks a currently on-boarded device as ‘Lost’.
Which two actions occur within Cisco ISE as a result oí this action? (Choose two)
What should be considered when configuring certificates for BYOD?
An endpoint certificate is mandatory for the Cisco ISE BYOD
An administrator is responsible for configuring network access for a temporary network printer. The administrator must only use the printer MAC address 50:89:65: 18:8: AB for authentication. Which authentication method will accomplish the task?
What occurs when a Cisco ISE distributed deployment has two nodes and the secondary node is deregistered?
An administrator is attempting to join a new node to the primary Cisco ISE node, but receives the error message "Node is Unreachable". What is causing this error?
An organization wants to split their Cisco ISE deployment to separate the device administration functionalities from the mam deployment. For this to work, the administrator must deregister any nodes that will become a part of the new deployment, but the button for this option is grayed out Which configuration is causing this behavior?
An administrator is configuring RADIUS on a Cisco switch with a key set to Cisc403012128 but is receiving the error “Authentication failed: 22040 Wrong password or invalid shared secret. “what must be done to address this issue?
An engineer is configuring Cisco ISE to reprofile endpoints based only on new requests of INIT-REBOOT and SELECTING message types. Which probe should be used to accomplish this task?
Which two endpoint compliance statuses are possible? (Choose two.)
An engineer must configure guest access on Cisco ISE for company visitors. Which step must be taken on the Cisco ISE PSNs before a guest portal is configured?
An administrator enables the profiling service for Cisco ISE to use for authorization policies while in closed mode. When the endpoints connect, they receive limited access so that the profiling probes can gather information and Cisco ISE can assign the correct profiles. They are using the default values within Cisco ISE. but the devices do not change their access due to the new profile. What is the problem'?
An engineer is configuring a virtual Cisco ISE deployment and needs each persona to be on a different node. Which persona should be configured with the largest amount of storage in this environment?
An engineer is configuring Central Web Authentication in Cisco ISE to provide guest access. When an authentication rule is configured in the Default Policy Set for the Wired_MAB or Wireless_MAB conditions, what must be selected for the "if user not found" setting?
What gives Cisco ISE an option to scan endpoints for vulnerabilities?
What is the purpose of the ip http server command on a switch?
Which configuration is required in the Cisco ISE authentication policy to allow Central Web Authentication?
Which two methods should a sponsor select to create bulk guest accounts from the sponsor portal? (Choose two )
A Cisco ISE administrator must authenticate users against Microsoft Active Directory. The solution must meet these requirements:
Users and computers must be authenticated.
User groups must be retrieved during authentication.
Which protocol must be added to the allowed protocols on the policy to authenticate the users?
An administrator is configuring TACACS+ on a Cisco switch but cannot authenticate users with Cisco ISE. The configuration contains the correct key of Cisc039712287. but the switch is not receiving a response from the Cisco ISE instance What must be done to validate the AAA configuration and identify the problem with the TACACS+ servers?
An administrator adds a new network device to the Cisco ISE configuration to authenticate endpoints to the network. The RADIUS test fails after the administrator configures all of the settings in Cisco ISE and adds the proper configurations to the switch. What is the issue"?
A network engineer is in the predeployment discovery phase o! a Cisco ISE deployment and must discover the network. There is an existing network management system in the network. Which type of probe must be configured to gather the information?
An administrator is configuring a new profiling policy in Cisco ISE for a printer type that is missing from the profiler feed The logical profile Printers must be used in the authorization rule and the rule must be hit. What must be done to ensure that this configuration will be successful^
An engineer must use Cisco ISE to provide network access to endpoints that cannot support 802.1X. The endpoint MAC addresses must be allowlisted by configuring an endpoint identity group. These configurations were performed:
Configured an identity group named allowlist
Configured the endpoints to use the MAC address of incompatible 802.1X devices
Added the endpoints to the allowlist identity group
Configured an authentication policy for MAB users
What must be configured?
MacOS users are complaining about having to read through wordy instructions when remediating their workstations to gam access to the network Which alternate method should be used to tell users how to remediate?
A network administrator must configure Cisco SE Personas in the company to share session information via syslog. Which Cisco ISE personas must be added to syslog receivers to accomplish this goal?