Which two statements about bridge-group interfaces in Cisco FTD are true? (Choose two.)
An engineer is integrating Cisco Secure Endpoint with Cisco Secure Firewall Management Center in high availability mode. Malware events detected by Secure Endpoint must also be
received by Secure Firewall Management Center and public cloud services are used. Which two configurations must be selected on both high availability peers independently? (Choose two.)
A network administrator is configuring a site-to-site IPsec VPN to a router sitting behind a Cisco FTD. The administrator has configured an access policy to allow traffic to this device on UDP 500, 4500, and ESP VPN traffic is not working. Which action resolves this issue?
A security engineer must configure a Cisco FTD appliance to inspect traffic coming from the internet. The Internet traffic will be mirrored from the Cisco Catalyst 9300 Switch. Which configuration accomplishes the task?
What is the purpose of the IRB feature in next-generation firewall?
Upon detecting a flagrant threat on an endpoint, which two technologies instruct Cisco Identity Services Engine to contain the infected endpoint either manually or automatically? (Choose two.)
What is the maximum bit size that Cisco FMC supports for HTTPS certificates?
An engineer is reviewing a ticket that requests to allow traffic for some devices that must connect to a server over 8699/udp. The request mentions only one IP address, 172.16.18.15, but the requestor asked for the engineer to open the port for all machines that have been trying to connect to it over the last week. Which action must the engineer take to troubleshoot this issue?
An engineer must build redundancy into the network and traffic must continuously flow if a redundant switch in front of the firewall goes down. What must be configured to accomplish this task?
An organization is migrating their Cisco ASA devices running in multicontext mode to Cisco FTD devices. Which action must be taken to ensure that each context on the Cisco ASA is logically separated in the Cisco FTD devices?
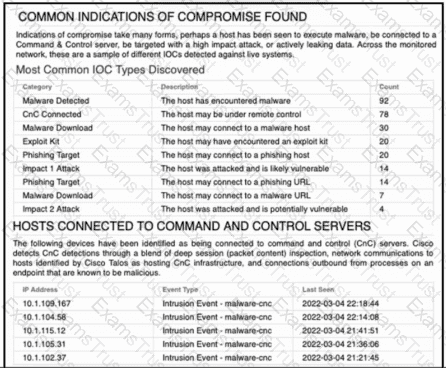
Refer to the exhibit. An engineer analyzes a Network Risk Report from Cisco Secure Firewall Management Center. What should the engineer recommend implementing to mitigate the risk?
A security engineer must create a malware and file policy on a Cisco Secure Firewall Threat Defense device. The solution must ensure that PDF. DOCX, and XLSX files are not sent lo Cisco Secure Malware analytics. What must do configured to meet the requirements''
The administrator notices that there is malware present with an .exe extension and needs to verify if any of the systems on the network are running the executable file. What must be configured within Cisco AMP for Endpoints to show this data?
An administrator needs to configure Cisco FMC to send a notification email when a data transfer larger than 10 MB is initiated from an internal host outside of standard business hours. Which Cisco FMC feature must be configured to accomplish this task?
An engineer has been tasked with performing an audit of network projects to determine which objects are duplicated across the various firewall models (Cisco Secure Firewall Threat Defense Cisco Secure firewall ASA, and Meraki MX Series) deployed throughout the company Which tool will assist the engineer in performing that audit?
An engineer wants to perform a packet capture on the Cisco FTD to confirm that the host using IP address 192 168.100.100 has the MAC address of 0042 7734.103 to help troubleshoot aconnectivity issue What is the correct tcpdump command syntax to ensure that the MAC address appears in the packet capture output?
Which two actions can be used in an access control policy rule? (Choose two.)
A network engineer must configure IPS mode on a Cisco Secure firewall Threat Defense device to inspect traffic and act as an IDS. The engineer already configured the passive-interface on the secure firewall threat Defence device and SPAN on the switch. What must be configured next by the engineer?
Which command-line mode is supported from the Cisco Firepower Management Center CLI?
Which Cisco Firepower rule action displays an HTTP warning page?

Refer to the exhibit. Users attempt to connect to numerous external resources on various TCP ports. If the users mistype the port, their connection closes immediately, and it takes more than one minute before the connection is torn down. An engineer manages to capture both types of connections as shown in the exhibit. What must the engineer configure to lower the timeout values for the second group of connections and resolve the user issues?
What is the result of specifying of QoS rule that has a rate limit that is greater than the maximum throughput of an interface?
Which action should be taken after editing an object that is used inside an access control policy?
What is a valid Cisco AMP file disposition?
An engineer is attempting to add a new FTD device to their FMC behind a NAT device with a NAT ID of ACME001 and a password of Cisco388267669. Which command set must be used in order to accomplish this?
With Cisco Firepower Threat Defense software, which interface mode must be configured to passively receive traffic that passes through the appliance?
An engineer is setting up a new Firepower deployment and is looking at the default FMC policies to start the implementation During the initial trial phase, the organization wants to test some common Snort rules while still allowing the majority of network traffic to pass Which default policy should be used?
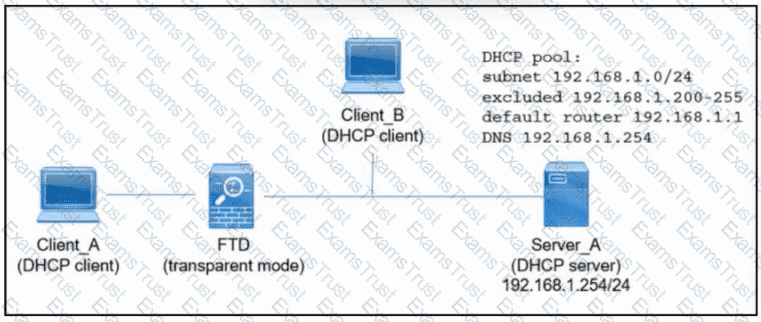
Refer to the exhibit. An engineer is deploying a new instance of Cisco Secure Firewall Threat Defense. Which action must the engineer take next so that Client_A and Client_B receive an IP address via DHCP from Server_A?
An engineer is configuring a Cisco IPS to protect the network and wants to test a policy before deploying it. A copy of each incoming packet needs to be monitored while traffic flow remains constant. Which IPS mode should be implemented to meet these requirements?
What is the role of realms in the Cisco ISE and Cisco Secure Firewall Management Center integration?
When a Cisco FTD device is configured in transparent firewall mode, on which two interface types can an IP address be configured? (Choose two.)
An analyst using the security analyst account permissions is trying to view the Correlations Events Widget but is not able to access it. However, other dashboards are accessible. Why is this occurring?
An organization is installing a new Cisco FTD appliance in the network. An engineer is tasked with configuring access between two network segments within the same IP subnet. Which step is needed to accomplish this task?
A network engineer must configure the cabling between a Cisco Secure Firewall Threat Defense appliance and a network so the Secure Firewall Threat Defense appliance performs inline to analyze and tune generated intrusion events before going live. Which Secure Firewall Threat Defense interface mode must the engineer use?
A network administrator is concerned about (he high number of malware files affecting users' machines. What must be done within the access control policy in Cisco FMC to address this concern?
Which command is typed at the CLI on the primary Cisco FTD unit to temporarily stop running high- availability?
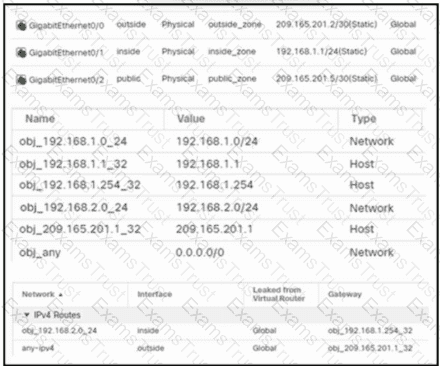
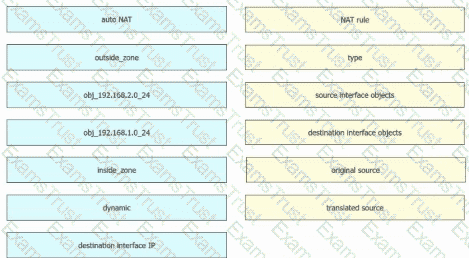
Refer to the exhibit. An engineer configures a NAT rule allowing clients to use the internet only if clients are located on the directly connected internal network. Dynamic auto PAT must be configured. Drag and drop the NAT rules from the left onto the corresponding targets on the right. Not all options are used.
Which two statements about deleting and re-adding a device to Cisco FMC are true? (Choose two.)
Cisco Security Analytics and Logging SaaS licenses come with how many days of data retention by default?
A network engineer is logged into the Cisco AMP for Endpoints console and sees a malicious verdict for an identified SHA-256 hash. Which configuration is needed to mitigate this threat?
After using Firepower for some time and learning about how it interacts with the network, an administrator is trying to correlate malicious activity with a user Which widget should be configured to provide this visibility on the Cisco Firepower dashboards?
What is a feature of Cisco AMP private cloud?
An engineer has been asked to show application usages automatically on a monthly basis and send the information to management What mechanism should be used to accomplish this task?
An administrator is adding a QoS policy to a Cisco FTD deployment. When a new rule is added to the policy and QoS is applied on 'Interfaces in Destination Interface Objects", no interface objects are available What is the problem?
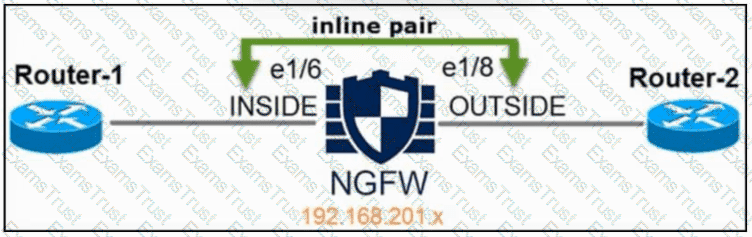
Refer to the exhibit. An engineer is configuring an instance of Cisco Secure Firewall Threat Defense with interfaces in IPS Inline Pair mode. What must be configured on interface e1/6 to accomplish the requirement?
An engineer is investigating connectivity problems on Cisco Firepower that is using service group tags. Specific devices are not being tagged correctly, which is preventing clients from using the proper policies when going through the firewall How is this issue resolved?
A Cisco FTD device is running in transparent firewall mode with a VTEP bridge group member ingress interface. What must be considered by an engineer tasked with specifying a destination MAC address for a packet trace?
A network engineer must provide redundancy between two Cisco FTD devices. The redundancy configuration must include automatic configuration, translation, and connection updates. After the initial configuration of the two appliances, which two steps must be taken to proceed with the redundancy configuration? (Choose two.)
Which firewall mode is Cisco Secure Firewall Threat Defense in when two physical interfaces are assigned to a named BVI?
An engineer is configuring a Cisco Secure Firewall Threat Defence device managed by Cisco Secure Firewall Management Centre. The device must have SSH enabled and the accessible from the inside interface for remote administration. Which type of policy must the engineer configure to accomplish this?
Which protocol establishes network redundancy in a switched Firepower device deployment?
An engineer is configuring Cisco Security Devices by using Cisco Secure Firewall Management Center. Which configuration command must be run to compare the CA certificate bundle on the local system to the latest CA bundle from the Cisco server?
A software development company hosts the website http:dev.company.com for contractors to share code for projects they are working on with internal developers. The web server is on premises and is protected by a Cisco Secure Firewall Threat Defense appliance. The network administrator is worried about someone trying to transmit infected files to internal users via this site. Which type of policy must be able associated with an access control policy to enable Cisco Secure Firewall Malware Defense to detect and block malware?
Which group within Cisco does the Threat Response team use for threat analysis and research?
What is the benefit of selecting the trace option for packet capture?
An administrator is setting up Cisco Firepower to send data to the Cisco Stealthwatch appliances. The NetFlow_Set_Parameters object is already created, but NetFlow is not being sent to the flow collector. What must be done to prevent this from occurring?
A network administrator is trying to configure an access rule to allow access to a specific banking site over HTTPS. Which method must the administrator use to meet the requirement?
An engineer must deploy a Cisco FTD appliance via Cisco FMC to span a network segment to detect malware and threats. When setting the Cisco FTD interface mode, which sequence of actions meets this requirement?
Refer to the exhibit.
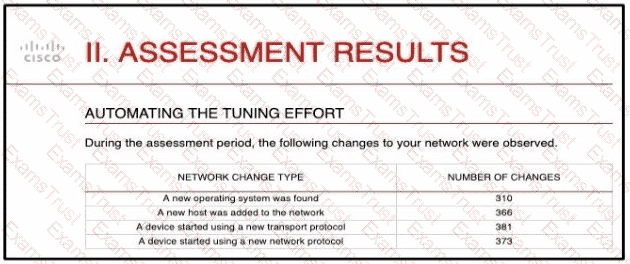
And engineer is analyzing the Attacks Risk Report and finds that there are over 300 instances of new operating systems being seen on the network How is the Firepower configuration updated to protect these new operating systems?
IT management is asking the network engineer to provide high-level summary statistics of the Cisco FTD appliance in the network. The business is approaching a peak season so the need to maintain business uptime is high. Which report type should be used to gather this information?
A consultant Is working on a project where the customer is upgrading from a single Cisco Firepower 2130 managed by FDM to a pair of Cisco Firepower 2130s managed oy FMC tor nigh availability. The customer wants the configures of the existing device being managed by FDM to be carried over to FMC and then replicated to the additional: device being added to create the high availability pair. Which action must the consultant take to meet this requirement?
An engineer is deploying Cisco Secure Endpoint for the first time and on endpoint with MAC address 50:54:15:04:0:AB. The engineer must make sure that during the testing phase no files are isolated and network connections must not be blocked. Which policy type must be configured to accomplish the task?
When using Cisco Threat Response, which phase of the Intelligence Cycle publishes the results of the investigation?
Which protocol is needed to exchange threat details in rapid threat containment on Cisco FMC?
An engineer is monitoring network traffic from their sales and product development departments, which are on two separate networks What must be configured in order to maintain data privacy for both departments?
What is the advantage of having Cisco Firepower devices send events to Cisco Threat response via the security services exchange portal directly as opposed to using syslog?
A network administrator is configuring a Cisco AMP public cloud instance and wants to capture infections and polymorphic variants of a threat to help detect families of malware. Which detection engine meets this requirement?
Network users experience issues when accessing a server on a different network segment. An engineer investigates the issue by performing packet capture on Cisco Secure Firewall Threat Defense. The engineer expects more data and suspects that not all the traffic was collected during a 15-minute can’t captured session. Which action must the engineer take to resolve the issue?
How many report templates does the Cisco Firepower Management Center support?
A company is deploying Cisco Secure Endpoint private cloud. The Secure Endpoint private cloud instance has already been deployed by the server administrator. The server administrator provided the hostname of the private cloud instance to the network engineer via email. What additional information does the network engineer require from the server administrator to be able to make the connection to Secure Endpoint private cloud in Cisco Secure Firewall Management Centre?
An engineer currently has a Cisco FTD device registered to the Cisco FMC and is assigned the address of 10 10.50.12. The organization is upgrading the addressing schemes and there is a requirement to convert the addresses to a format that provides an adequate amount of addresses on the network What should the engineer do to ensure that the new addressing takes effect and can be used for the Cisco FTD to Cisco FMC connection?
An analyst is reviewing the Cisco FMC reports for the week. They notice that some peer-to-peer applications are being used on the network and they must identify which poses the greatest risk to the environment. Which report gives the analyst this information?
Which connector is used to integrate Cisco ISE with Cisco FMC for Rapid Threat Containment?
Which two considerations must be made when deleting and re-adding devices while managing them via Cisco FMC (Choose two).
Refer to the exhibit.
What must be done to fix access to this website while preventing the same communication to all other websites?
An administrator is attempting to remotely log into a switch in the data centre using SSH and is unable to connect. How does the administrator confirm that traffic is reaching the firewall?
Which two OSPF routing features are configured in Cisco FMC and propagated to Cisco FTD? (Choosetwo.)
An engineer is configuring URL filtering for a Cisco FTD device in Cisco FMC. Users must receive a warning when they access http:/' 'additstte.corn with the option of continuing to the website if they choose to. No other websites should be blacked. Which two actions must the engineer lake to meet these requirements? (Choose two.)
Which interface type allows packets to be dropped?
Which feature issupportedby IRB on Cisco FTD devices?
A network administrator has converted a Cisco FTD from using LDAP to LDAPS for VPN authentication. The Cisco FMC can connect to the LDAPS server, but the Cisco FTD is not connecting. Which configuration must be enabled on the Cisco FTD?
A network engineer wants to add a third-party threat feed into the Cisco FMC for enhanced threat detectionWhich action should be taken to accomplish this goal?
An engineer is setting up a remote access VPN on a Cisco FTD device and wants to define which traffic gets sent over the VPN tunnel. Which named object type in Cisco FMC must be used to accomplish this task?
When do you need the file-size command option during troubleshooting with packet capture?
An engineer is implementing a new Cisco Secure Firewall. The firewall must filler traffic between the three subnets:
• LAN 192.168.101.0724
• DMZ 192.168 200.0/24
• WAN 10.0.0.0/30
Which firewall mode must the engineer implement?
Which report template field format is available in Cisco FMC?
The event dashboard within the Cisco FMC has been inundated with low priority intrusion drop events, which are overshadowing high priority events. An engineer has been tasked with reviewing the policies and reducing the low priority events. Which action should be configured to accomplish this task?
A network engineer is tasked with minimising traffic interruption during peak traffic limes. When the SNORT inspection engine is overwhelmed, what must be configured to alleviate this issue?
An administrator is attempting to add a new FTD device to their FMC behind a NAT device with a NAT ID of NAT001 and a password of Cisco0420l06525. The private IP address of the FMC server is 192.168.45.45. which is being translated to the public IP address of 209.165.200.225/27. Which command set must be used in order to accomplish this task?
An engineer is investigating connectivity problems on Cisco Firepower for a specific SGT. Which command allows the engineer to capture real packets that pass through the firewall using an SGT of 64?
Which component is needed to perform rapid threat containment with Cisco FMC?
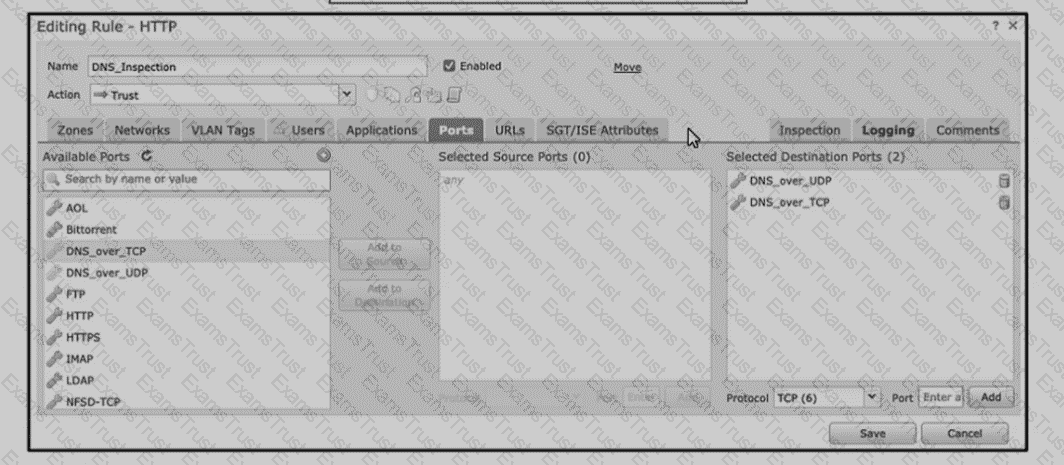
Refer to the exhibit An engineer is modifying an access control pokey to add a rule to inspect all DNS traffic that passes through the firewall After making the change and deploying thepokey they see that DNS traffic is not bang inspected by the Snort engine What is the problem?
An engineer Is configuring a Cisco FTD device to place on the Finance VLAN to provide additional protection tor company financial data. The device must be deployed without requiring any changes on the end user workstations, which currently use DHCP lo obtain an IP address. How must the engineer deploy the device to meet this requirement?
An engineer must create an access control policy on a Cisco Secure Firewall Threat Defense device. The company has a contact center that utilizes VoIP heavily, and it is critical that this traffic is not …. by performance issues after deploying the access control policy Which access control Action rule must be configured to handle the VoIP traffic?
An engineer must configure high availability for the Cisco Firepower devices. The current network topology does not allow for two devices to pass traffic concurrently. How must the devices be implemented in this environment?
In which two places can thresholding settings be configured? (Choose two.)
An engineer attempts to pull the configuration for a Cisco FTD sensor to review with Cisco TAC but does not have direct access to the CU for the device. The CLl for the device is managed by Cisco FMC to which the engineer has access. Which action in Cisco FMC grants access to the CLl for the device?
Which policy rule is included in the deployment of a local DMZ during the initial deployment of a Cisco NGFW through the Cisco FMC GUI?
An organization created a custom application that is being flagged by Cisco Secure Endpoint. The application must be exempt from being flagged. What is the process to meet the requirement?
An engineer must export a packet capture from Cisco Secure Firewall Management Center to assist in troubleshooting an issue an a Secure Firewall Threat Defense device. When the engineer navigates to URL for Secure Firewall Management Center at:
..
An engineer receives a 403: Forbidden error instead of being provided with the PCAP file. Which action resolves the issue?
An engineer is using the configure manager add
An engineer must define a URL object on Cisco FMC. What is the correct method to specify the URL without performing SSL inspection?

A security engineer must improve security in an organization and is producing a risk mitigation strategy to present to management for approval. Which action must the security engineer take based on this Attacks Risk Report?
An engineer has been tasked with using Cisco FMC to determine if files being sent through the network are malware. Which two configuration tasks must be performed to achieve this file lookup? (Choose two).
Which process should be checked when troubleshooting registration issues between Cisco FMC and managed devices to verify that secure communication is occurring?
Which communication is blocked from the bridge groups when multiple are configured in transparent mode on a Cisco Secure Firewall Threat Defense appliance?
A company is deploying intrusion protection on multiple Cisco FTD appliances managed by Cisco FMC. Which system-provided policy must be selected if speed and detection are priorities?
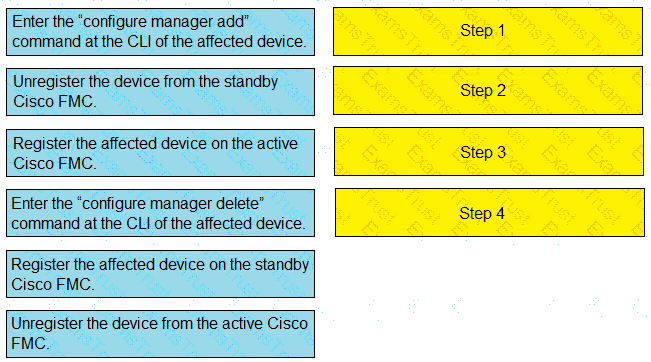
Drag and drop the steps to restore an automatic device registration failure on the standby Cisco FMC from the left into the correct order on the right. Not all options are used.
Which command should be used on the Cisco FTD CLI to capture all the packets that hit an interface?
Refer to the exhibit.

An engineer generates troubleshooting files in Cisco Secure Firewall Management Center (FMC). A successfully completed task Is removed before the files are downloaded. Which two actions must be taken to determine the filename and obtain the generated troubleshooting files without regenerating them? (Choose two.)
An engineer is troubleshooting HTTP traffic to a web server using the packet capture tool on Cisco FMC. When reviewing the captures, the engineer notices that there are a lot of packets that are not sourced from or destined to the web server being captured. How can the engineer reduce the strain of capturing packets for irrelevant traffic on the Cisco FTD device?
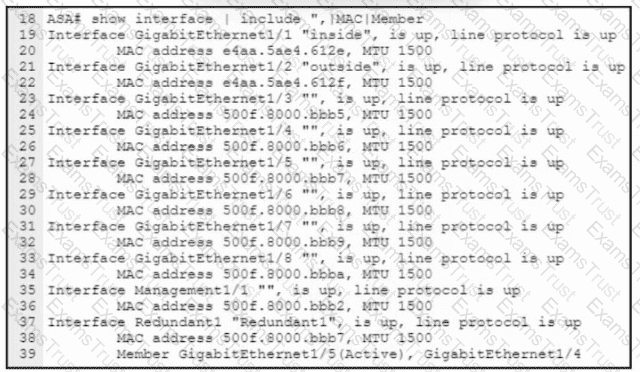
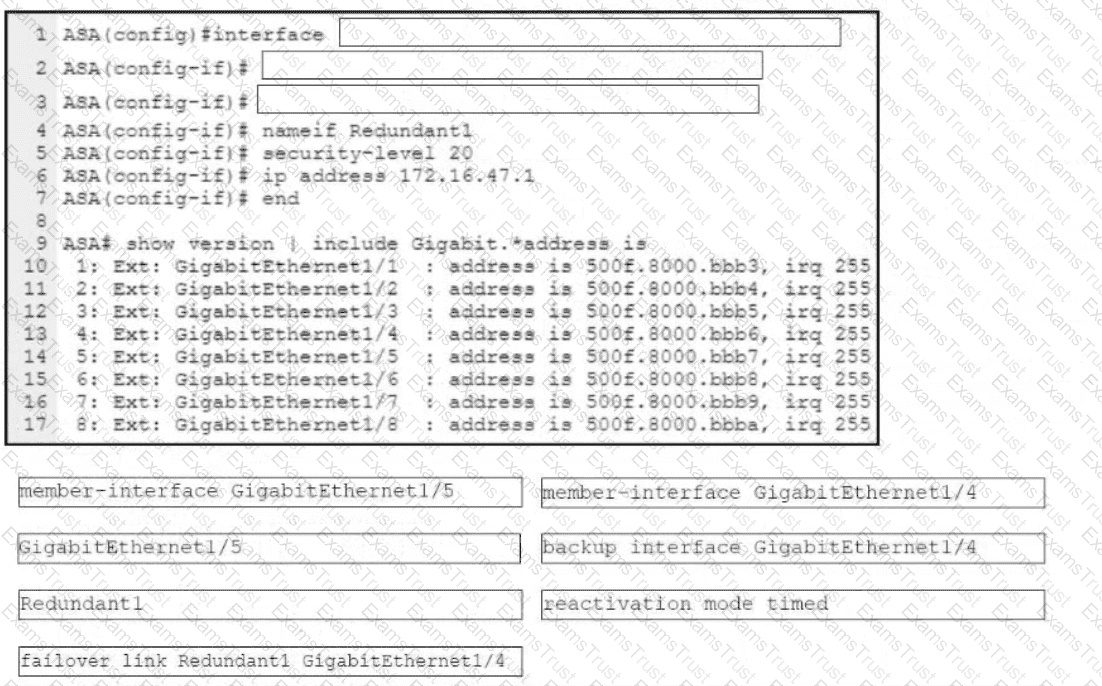
Refer to the exhibit. An engineer must configure a connection on a Cisco ASA Firewall with a Cisco Secure Firewall Services Module to ensure that the secondary interface takes over all the functions of the primary interface if the primary interface fails. Drag and drop the code snippets from the bottom onto the boxes in the CLI commands to configure the failover. Not all options are used.
What is a method used by Cisco Rapid Threat Containment to contain the threat in the network?
An engineer must change the mode of a Cisco Secure Firewall Threat Defense (FTD) firewall in the Cisco Secure Firewall Management Center (FMC) inventory. The engineer must take these actions:
• Register Secure FTD with Secure FMC.
• Change the firewall mode.
• Deregister the Secure FTD device from Secure FMC.
How must the engineer take FTD take the actions?
A network engineer is logged into the Cisco AMP for Endpoints console and sees a malicious verdict for an identified SHA-256 hash. Which configuration is needed to mitigate this threat?