Which switch type is discovered first in the Cisco ACI fabric discovery process?
An engineer must configure a service graph for the policy-based redirect to redirect traffic to a transparent firewall. The policy must be vendor-agnostic to support any firewall appliance, Which two actions accomplish these goals? (Choose two.)
As part of a migration, legacy non-ACI switches must be connected to the Cisco ACI fabric. All non-ACI switches run per-VLAN RSTP. After the non-ACI switches are connected to Cisco ACI, the STP convergence caused a microloop and significant CPU spike on all switches. Which configuration on the interfaces of the external switches that face the Cisco ACI fabric resolves the problem?
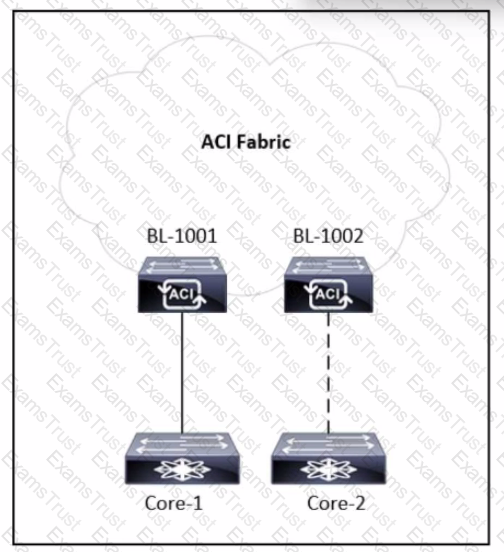
Refer to the exhibit. A tenant is configured with a single L30ut and a single-homed link to the core router called Core-1. An engineer must add a second link to the L30ut that connects to Core-2 router. Which action allows the traffic from Core-2 to BL-1002 to have the same connectivity as the traffic from Core-1 to BL-1001?
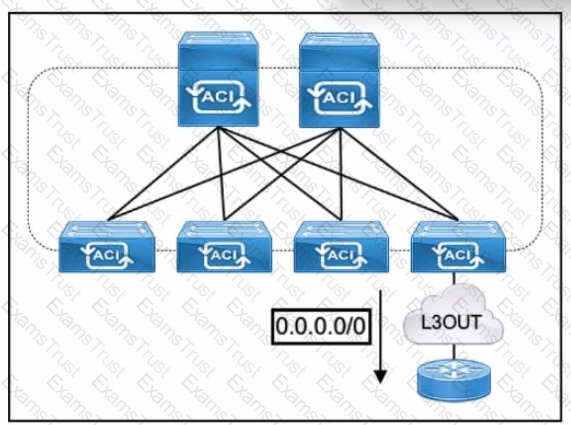
Refer to the exhibit. The default route is not present in the routing tables of the Cisco ACI leaf switches. All static and direct routes are currently being redistributed and advertised. Which jn must be taken to advertise a default route on the eBGP L30ut?
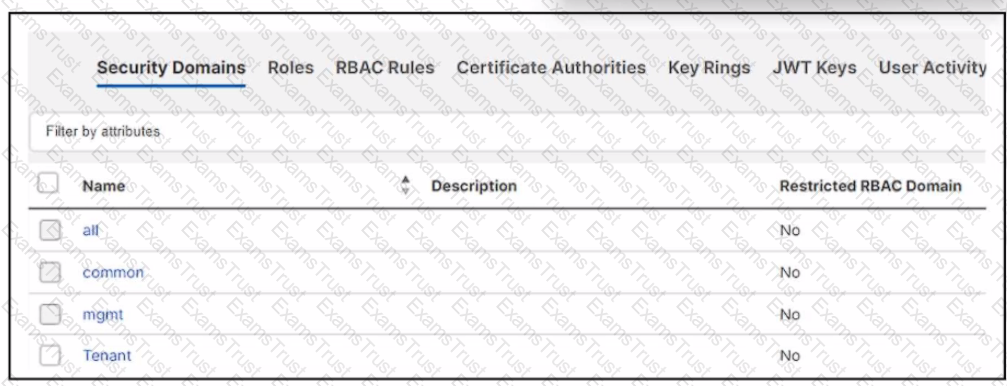
Refer to the exhibit. An engineer created a local user named User on Cisco ACI. The engineer must configure the fabric so that the User can access only common and PROD tenants, ch set of actions accomplishes the goal?
An engineer is implementing Cisco ACI at a large platform-as-a-service provider using APIC controllers, 9396PX leaf switches, and 9336PQ spine switches. The leaf switch ports are configured as IEEE 802.1p ports. Where does the traffic exit from the EPG in IEEE 802.1p mode in this configuration?
In the context of VMM, which protocol between ACI leaf and compute hosts ensures that the policies are pushed to the leaf switches for immediate and on demand resolution immediacy?
Which type of port is used for in-band management within ACI fabric?
An Cisco ACI leaf switch learns the source IP address of a packet that enters the front panel port of the switch. Which bridge domain setting is used?
An engineer must limit management access to me Cisco ACI fabric that originates from a single subnet where the NOC operates. Access should be limited to SSH and HTTPS only. Where should the policy be configured on the Cisco APIC to meet the requirements?
An engineer is implementing a connection that represents an external bridged network. Which two configurations are used? (Choose two.)
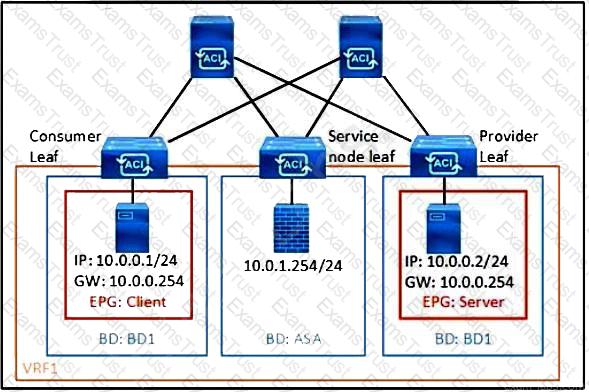
Refer to the exhibit. What must be configured in the service graph to redirect HTTP traffic between the EPG client and EPG server to go through the Cisco ASA firewall?
The unicast routing feature is enabled on the bridge domain. Which two conditions enable the Cisco ACI leaf to learn a source IP as a local endpoint? (Choose two.)
An engineer is extending EPG connectivity to an external network. The external network houses the Layer 3 gateway and other end hosts. Which ACI bridge domain configuration should be used?
An engineer must deploy Cisco ACI across 10 geographically separated data centers. Which ACI site deployment feature enables the engineer to control which bridge domains contain Layer 2 flooding?
A Cisco ACI endpoint group must have its gateway address migrated out of the ACI fabric. An engineer configures EPG-TEST with a static port binding and configures the encap VLAN with the required VLAN. Which configuration set must be used on the bridge domain to meet these requirements?
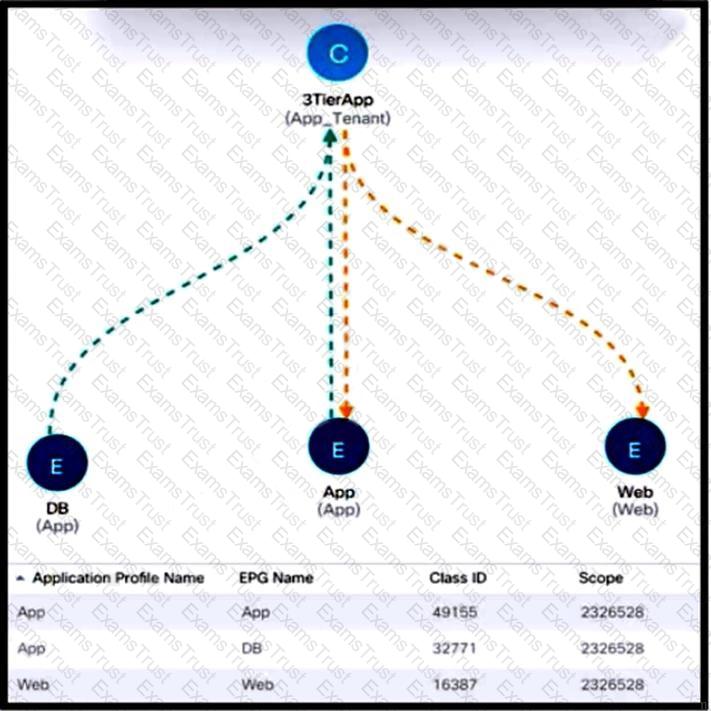
Refer to the exhibit. New e-commerce software is deployed on Cisco ACI fabric. The environment must meet these requirements:
The overall number of contracts must be reduced by reusing the existing contracts within a VRF when possible.
The e-commerce software must communicate only with software EPGs that are part of the same ANP.
The e-commerce software must be prevented from communicating with applications in different ANPs.
Which scope must be selected to meet these requirements?
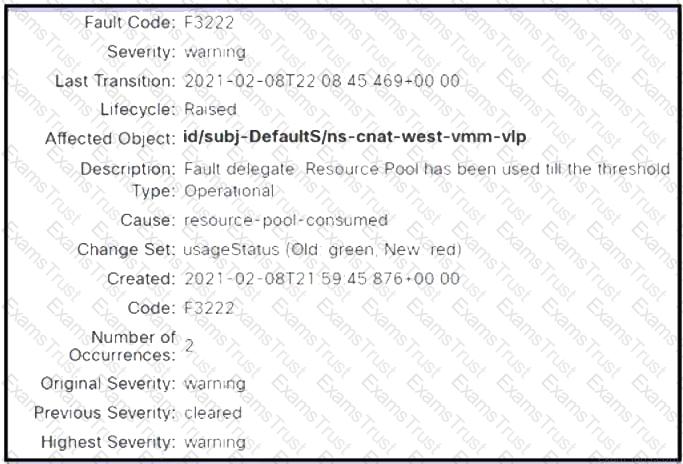
Refer to the exhibit. A Cisco APIC raises an error when the EPG must accept endpoints from a VMM domain created. Which action clears the fault?
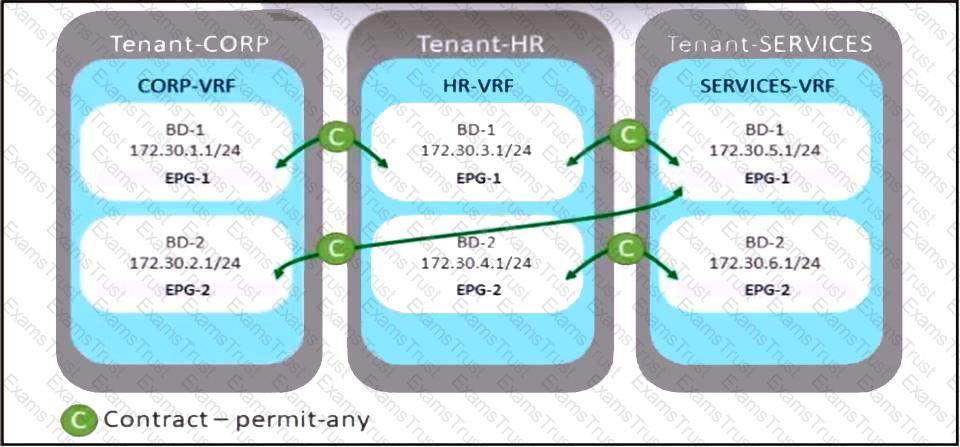
Refer to the exhibit. A company merges three of its departments: CORP, HR, and SERVICES, Currently, the connectivity between departments is achieved by using VRF route leaking. The requirement is to redesign the Cisco ACI networking architecture to communicate between EPGs and BDs from any tenant without configuring contracts or VRF route leaking. Which configuration meets these criteria?
A company must connect three Cisco ACI data centers by using Cisco ACI Multi-Site. An engineer must configure the Inter-Site Network (ISN) between the existing sites. Which two configuration steps must be taken to implement the ISN? (Choose two.)
An engineer configures SNMP for an ACI fabric and created an SNMP Monitoring Destination Group called snmp_dgroup1. Snmp_dgroup1 is configured with the server hostname and Community password. An SNMP policy called snmp_podpolicy1 is configured to enable SNMP and add an SNMP Client Group Profile called snmp_clgroup1. Snmp_podpolicy1 is associated default pod profile via a pod policy group named podl. Which configuration set must the engineer enable to complete the SNMP configuration?
An engineer wants to monitor all configuration changes, threshold crossing, and link-state transitions in a Cisco ACI fabric. Which action must be taken to receive the required messages?
What must be enabled in the bridge domain to have the endpoint table learn the IP addresses of endpoints?
The customer is looking for redundant interconnection of the existing network to the new ACI fabric. Unicast and multicast traffic must be routed between the two networks. Which L3Out implementation meets these requirements?
Which statement about ACI syslog is true or Which statement describes the ACI syslog?
Which two IP address types are available for transport over the ISN when they are configured from Cisco ACI Multi-Site Orchestrator? (Choose two.)
An engineer created two interface protocol policies called Pol_CDP40275332 and Pol_LLDP46783451. The policies must be used together in a single policy. Which ACI object must be used?
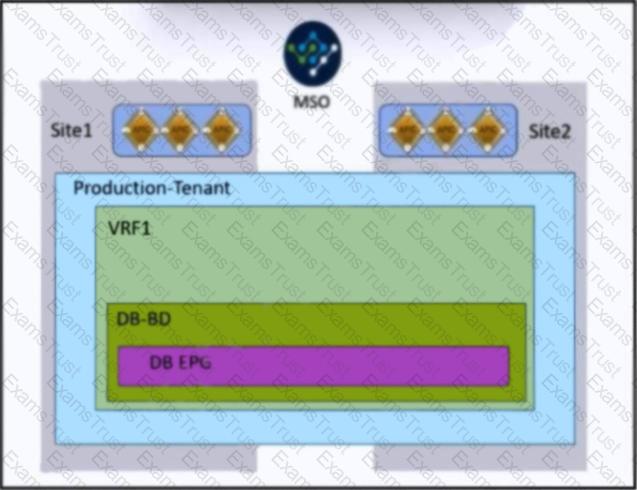
Refer to the exhibit. An engineer must allow IP mobility between Site1 and Site2 in a Cisco ACI Multi-Site orchestrator. The design must meet these requirements:
A disaster recovery (DR) solution must exist between the sites that do not require vMotion support.
The application must be started at a DR site without having to re-IP the application servers.
The solution must avoid any broadcast storms between the sites.
Which two actions meet these criteria? (Choose two.)
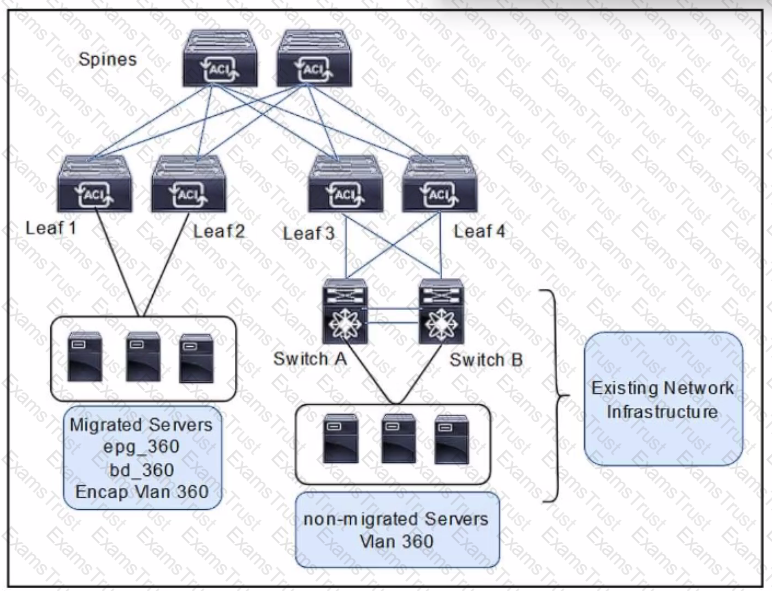
Refer to the exhibit. An engineer is migrating legacy servers into the Cisco ACI environment. The requirement is to ensure that all endpoints and MAC addresses are learned properly in legacy and Cisco ACI switches. Which configuration set must be configured under the bridge domain called bd__360 to accomplish this goal?
What two actions should be taken to deploy a new Cisco ACI Multi-Pod setup? (Choose two.)
Refer to the exhibit.
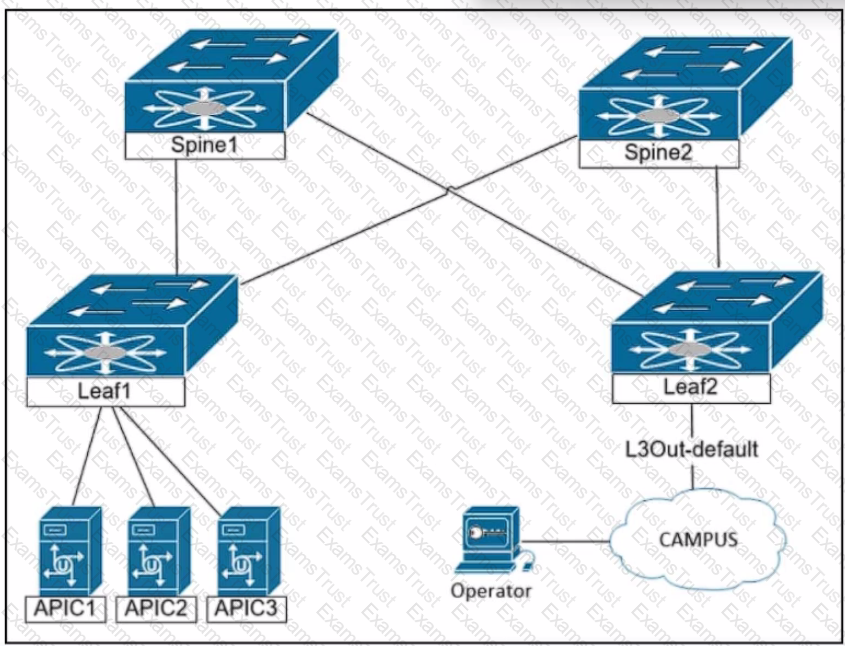
The engineer is planning to configure in-band management for the Cisco ACI fabric. The goal is to allow the network operators to reach the Cisco APIC servers and fabric switches from the in-band network. Which configuration must be applied on the bridge domain to accomplish these goals?
Which two statements regarding ACI Multi-Site are true? (Choose two.)
An engineer configured a bridge domain with the hardware-proxy option for Layer 2 unknown unicast traffic. Which statement is true about this configuration?
An engineer must configure a Layer 3 connection to the WAN router. The hosts in production VRF must access WAN subnets. The engineer associates EPGs in the production VRF with the external routed domain. Which action completes the task?
An engineer configures port-12 on Leaf-101 and Leaf-102 to connect to a new server, SVR-12. The new server will belong to EPG-12 and use encap VLAN-1212. The engineer configured SVR-12 as a VPC member port and statically bound the VPC member port to EPG-12. Which additional step must the engineer take to configure connectivity?
A customer implements RBAC on a Cisco APIC using a Windows RADIUS server that is configured with network control policies. The APIC is as follows:
Tenant = TenantX
Security Domain = Tenantx-SD
User = X
The customer requires User X to have access to TenantX only, without any extra privilege in the Cisco ACI fabric domain. Which Cisco AV pair must be implemented on the RADIUS server to meet these requirement?
When Layer 3 routed traffic is destined to a Cisco ACI fabric, which mechanism does ACI use to detect silent hosts?
Cisco ACI fabric is integrated with VMware VDS. The fabric must apply a security policy to check the integrity of traffic out of the network adapter. Which action must be taken to drop the .. when the ESXi host discovers a mismatch between the actual source MAC address transmitted by the guest operating system and the effective MAC address of the virtual machine ….?
A network engineer must allow secure access to the Cisco ACl out-of-band (OOB) management only from external subnets 10 0 0024 and 192.168 20 G'25. Which configuration set accomplishes this goal?
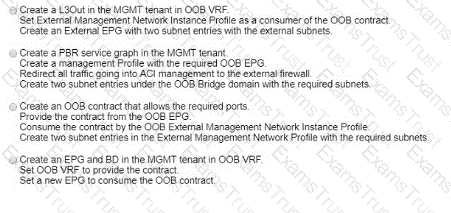
An ACI engineer is implementing a Layer 3 out inside the Cisco ACI fabric that must meet these requirements:
The data center core switch must be connected to one of the leaf switches with a single 1G link.
The routes must be exchanged using a link-state routing protocol that supports hierarchical network design.
The data center core switch interface must be using 802.1Q tagging, and each vlan will be configured with a dedicated IP address.
Which set of steps accomplishes these goals?
Which type of profile needs to be created to deploy an access port policy group?
What is the advantage of implementing an active-active firewall cluster that is stretched across separate pods when anycast services are configured?
On which two interface types should a user configure storm control to protect against broadcast traffic? (Choose two.)
When Cisco ACI connects to an outside Layers 2 network, where does the ACI fabric flood the STP BPDU frame?
Refer to the exhibit.
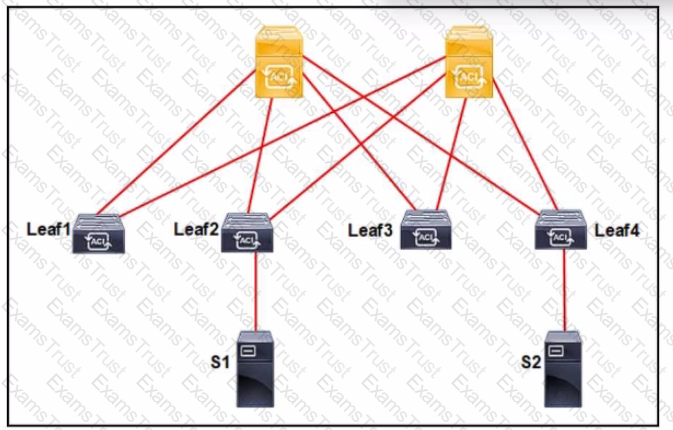
An application called App_1 is hosted on the server called S1. A silent host application. App_2. is hosted on S2. Both applications use the same VLAN encapsulation, which action forces Cisco ACI fabric to learn App_2 on ACI leaf 2?
An engineer configures an L30ut in VRF-1 that was configured for Import Route Control Enforcement. The L30ut uses OSPF to peer with a core switch. The L30ut has one external EPG, it has been configured with a subnet 10.1.0.0/24. Which scope must be set to force 10.1.0.0/24 to populate in the routing table for VRF-1?
Refer to the exhibit. VM1 and VM2 are in Cisco ACI POD1 and communication takes place. Which event is triggered when VM2 is live migrated from POD1 to POD2?
Where are STP BPDUSs flooded in Cisco ACI fabric?
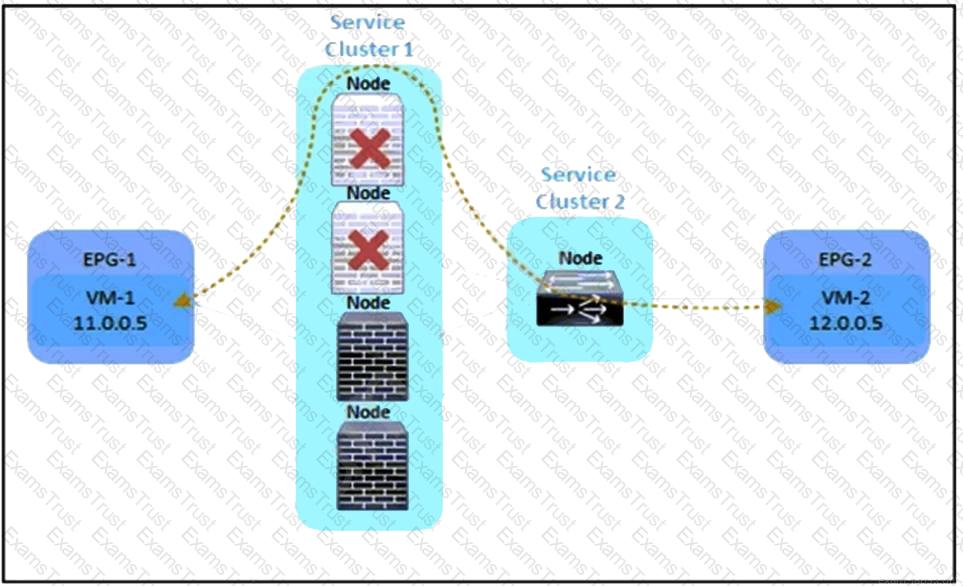
Refer to the exhibit. An engineer must divert the traffic between VM-1 and VM-2 by using a Multi-Node service graph. The solution should prevent an insufficient number of available Layer 4 to Layer 7 devices in the first cluster. Which configuration set accomplishes this goal?
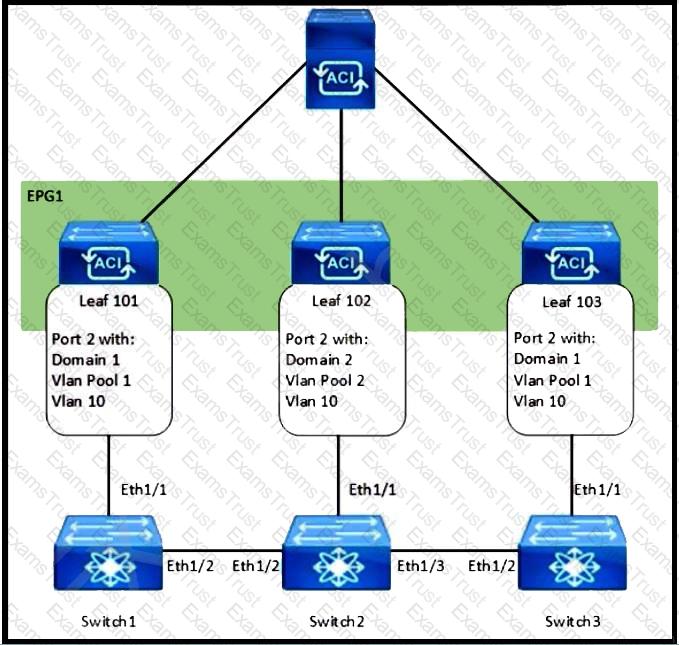
Refer to the exhibit. How are the STP BPDUs forwarded over Cisco ACI fabric?
Engineer must configure SNMP inside a Cisco ACI fabric. The engineer has created an SNMP Policy, called SNMP-policy and an SNMP Monitoring Group called SNMP-group1 that Contains five trap receivers. Which configuration set completes the configuration?
An engineer is implementing a Cisco ACI environment that consists of more than 20 servers. Two of the servers support only Cisco Discovery Protocol with no order link discovery protocol. The engineer wants the servers to be discovered automatically by the Cisco ACI fabric when connected. Which action must be taken to meet this requirement?
A customer must upgrade the Cisco ACI fabric to use a feature from the new code release. However, there is no direct path from the current release to the desired one. Based on the Cisco APIC Upgrade/Downgrade Support Matrix, the administrator must go through one intermediate release.
Which set of steps must be taken to upgrade the fabric to the new release?
When creating a subnet within a bridge domain, which configuration option is used to specify the network visibility of the subnet?
An engineer must configure VMM domain integration on a Cisco UCS B-Series server that is connected to a Cisco ACI fabric. Drag and drop the products used to create VMM domain from the bottom into the sequence in which they should be implemented at the top. Products are used more than once.
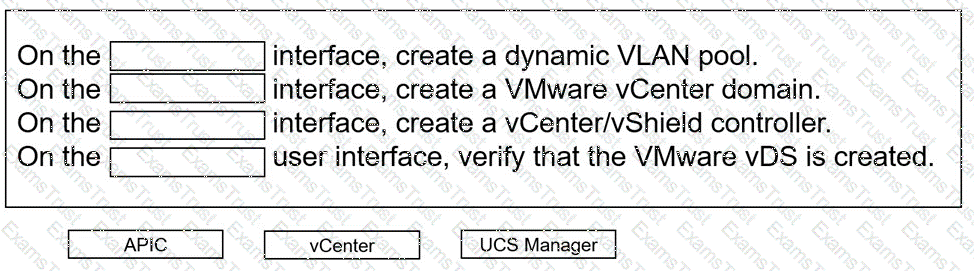
An engineer must allow multiple external networks to communicate with internal ACI subnets. Which action should the engineer take to assign the prefix to the class ID of the external Endpoint Group?
An engineer must connect Cisco ACI fabric using Layer 2 with external third-party switches. The third-party
switches are configured using 802.1s protocol. Which two constructs are required to complete the task?
(Choose two.)
Refer to the exhibit.
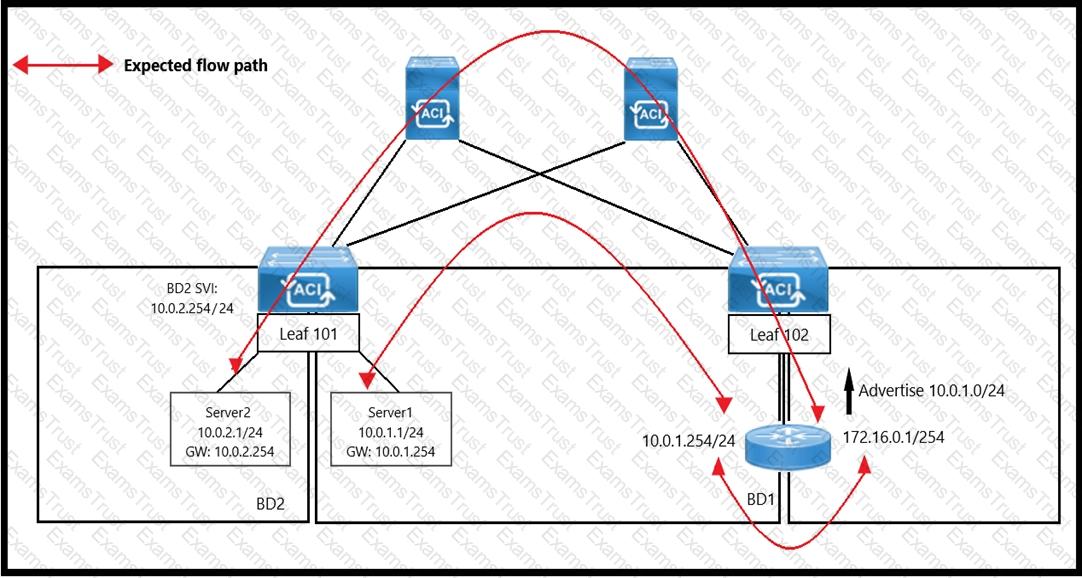
An engineer wants to initiate an ICMP ping from Server1 to Server2. The requirement is for the BD1 to enforce ICMP replies that follow the expected path. The packets must be prevented from taking the direct path from Leaf1 to Server1. Which action must be taken on BD1 to meet these requirements?
What is the name of the automatically configured VLAN 3600 presented during Cisco ACI fabric discovery?

Network engineer configured a Cisco ACI fabric as follows:
• An EPG called EPG-A is created and associated with a VMM domain called North. •The EPG-A is associated with BD-A and is in an application profile called Apps-A.
• The BD-A is associated with VRF-1 in the Prod tenant.
Which port group must be selected to place VMs in EPG-A?
In-band is currently configured and used to manage the Cisco ACI fabric. The requirement is for leaf and spine switches to use out-of-band management for NTP protocol. Which action accomplishes this goal?
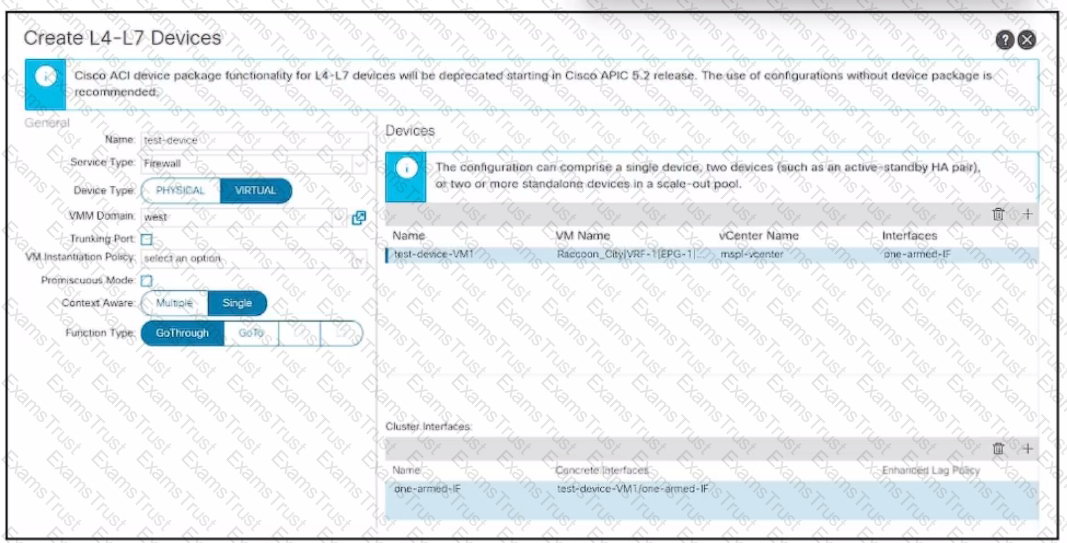
Refer to the exhibit. An engineer configures a Layer 4 to Layer 7 device object. The device is a virtual firewall with a single network adapter and it must be deployed in routed mode. Which .. completes the configuration of the device object?
A bridge domain for an EPC called “Web Servers” must be created in the Cisco APIC. The configuration must meet these requirements:
Only traffic to known Mac addresses must be allowed to reduce noice.
The multicast traffic must be limited to the ports that are participating in multicast routing.
The endpoints within the bridge domain must be kept in the endpoint table for 20 minultes without any updates.
Which set of steps configures the bridge domain that satisfies the requirements?
New ESXi hosts are procured in a data center compute expansion project. An engineer must update the
configuration on the Cisco APIC controllers to support the addition of the new servers to the existing VMM
domain. Which action should be taken to support this change?
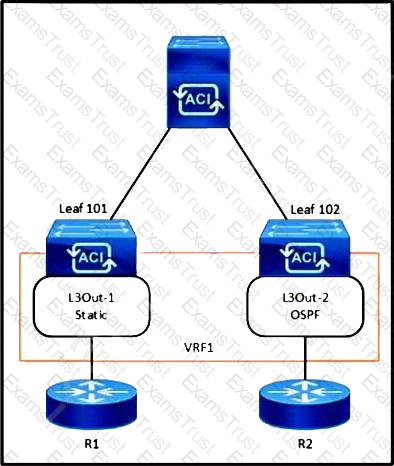
Refer to the exhibit. The 0.0.0.0/0 is configured as a default static route on L3Out-1. Which action should be taken for the 0.0.0.0/0 prefix to advertise out on L3Out-2 OSPF?
An engineer must set up a Cisco ACI fabric to send Syslog messages related to hardware events, such as chassis line card failures. The messages should be sent to a dedicated Syslog server. Where in the Cisco APIC should the policy be configured to meet this requirement?
An engineer must perform a Cisco ACI fabric upgrade that minimizes the impact on user traffic and allows only permitted users to perform an upgrade. Which two configuration steps should be taken to meet these requirements?
Refer to the exhibit.
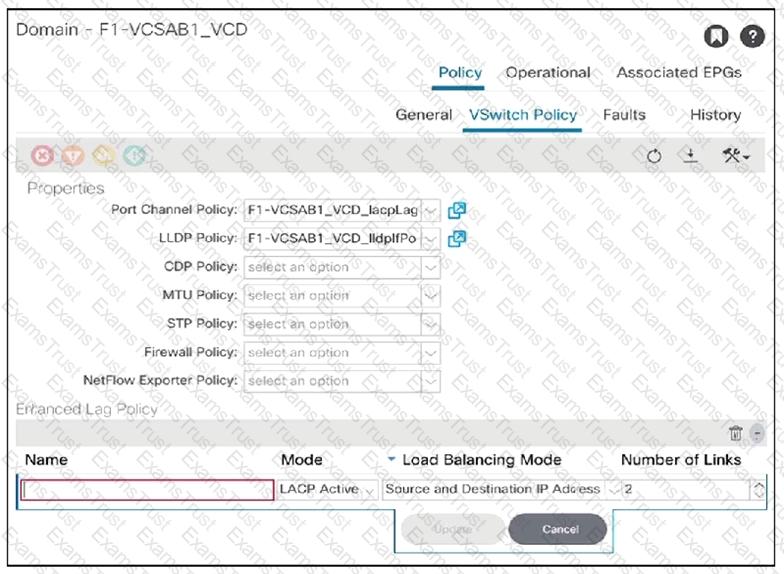
An engineer configures the Cisco ACI fabric for VMM integration with ESXi servers that are to be connected to the ACI leaves. The server team requires the network switches to initiate the LACP negotiation as opposed to the servers. The LAG group consists of two 10 Gigabit Ethernet links. The server learn also wants to evenly distribute traffic across all available links. Which two enhanced LAG policies meet these requirements? (Choose two.)
Refer to the exhibit.
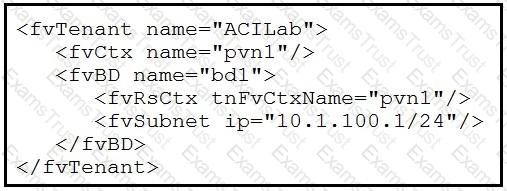
Which two objects are created as a result of the configuration? (Choose two.)
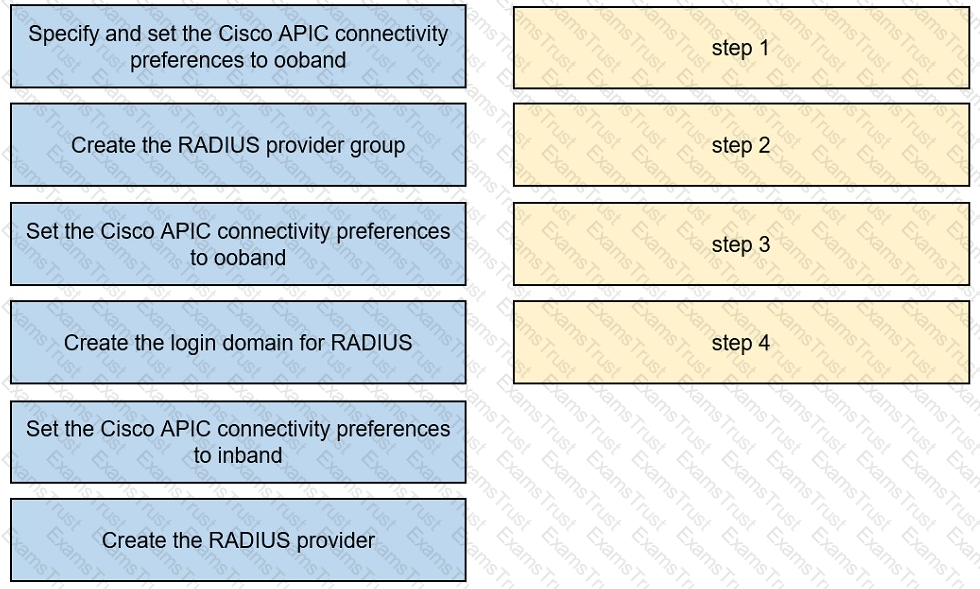
An engineer must configure RADIUS authentication with Cisco ACI for remote authentication with out-of-band management access. Drag and drop the RADIUS configuration steps from the left into the required implementation order on the right. Not all steps are used.
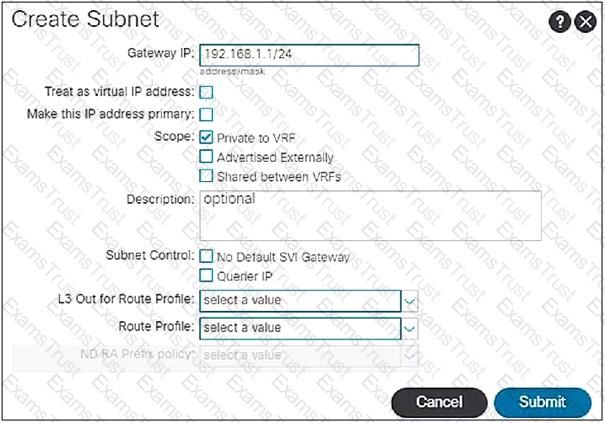
When the subnet is configured on a bridge domain, on which physical devices is the gateway IP address configured?
A Cisco ACI is integrated with a VMware vSphere environment. The port groups must be created automatically in vSphere and propagated to hypervisors when created in the ACI environment. Which action accomplishes this goal?
The Application team reports that a previously existing port group has disappeared from vCenter. An engineer confirms that the VM domain association for the EPG is no longer present. Which action determines which user is responsible for the change?