Which customizable security report on Cisco Prime Infrastructure will show rogue APs detected since a point in time?
When configuring a Cisco WLC, which CLI command adds a VLAN with VLAN ID of 30 to a FlexConnect group named BranchA-FCG?
A Cisco WLC has been added to the network and Cisco ISE as a network device, but authentication is failing. Which configuration within the network device configuration should be verified?
An engineer is in the process of implementing Fastiane on a wireless network with a Mobility Express AP installed and Apple end-user devices. Due to a security concern, the IT department has updated all the iPads to version 14.5.423551943. Which QoS profile must the engineer configure on the user WLAN?
A wireless engineer needs to implement client tracking. Which method does the angle of arrival use to determine the location of a wireless device?
Refer to the exhibit.
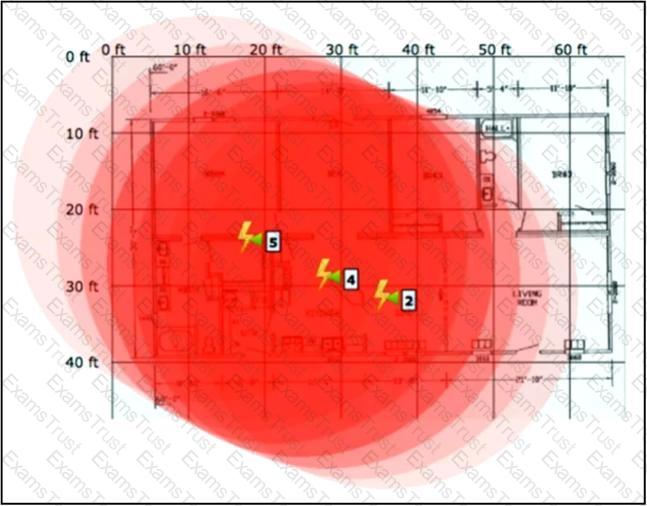
An engineer needs to manage non-802.11 interference. What is observed in the output on PI?
A wireless engineer deployed all remote sites as FlexConnect. The client VLAN assignment on these sites is configured manually mapped by WLAN and using local switching. Dynamic VLAN assignment is provided by the newly deployed Cisco ISE. Which IETF attribute must be configured on the AAA server to send that VLAN ID?
A controller shows that an AP in your environment is detecting interference, but the AP health score in Cisco DNA Center is unaffected. What are two reasons that Cisco DNA Center is ignoring the interference? (Choose two.)
The security policy mandates that only controller web management traffic is allowed from the IT subnet. In testing, an engineer is trying to connect to a WLAN with Web Authentication for guest users, but the page is timing out on the wireless client browser. What is the cause of the issue?
A customer wants to allow employees to easily onboard their personal devices to the wireless network. The visitors also must be able to connect to the same network without the need to engage with anyone from the reception desk. Which process must be configured on Cisco ISE to support this requirement?
A network is set up to support wired and wireless clients. Both types must authenticate using 802.1X before connecting to the network. Different types of client authentication must be separated on a Cisco ISE deployment. Which two configuration items achieve this task? (Choose two.)
CMX Facebook Wi-Fi allows access to the network before authentication. Which two elements are available? (Choose two.)
An engineer is performing a Cisco Hyperlocation accuracy test and executes the cmxloc start command on Cisco CMX. Which two parameters are
relevant? (Choose two.)
An engineer must configure MSE to provide guests access using social media authentication. Which service does the engineer configure so that guests use Facebook credentials to authenticate?
A customer managing a large network has implemented location services. Due to heavy load, it is needed to load balance the data coming through NMSP from the WLCs. Load must be spread between multiple CMX servers to help optimize the data flow for APs. Which configuration in CMX meets this requirement?
Refer to the exhibit.
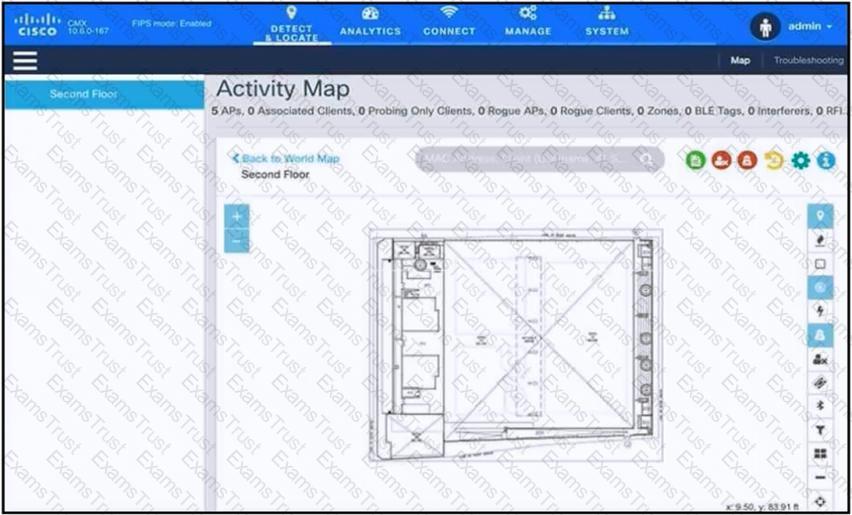
An engineer has deployed the Cisco CMX solution to track and detect the number of users who visit the office each day. The CMX dashboard is not showing any data. Which action resolves this issue?
Which three properties are used for client profiling of wireless clients? (Choose three.)
An engineer is deploying a virtual MSE. The network has 3000 APs and needs 7000 IPS licenses.
To which size server does the engineer scale it?
An engineer completed the basic installation for two Cisco CMX servers and is in the process of configuring high availability, but it fails. Which two statements about the root of the issue are true? (Choose two.)
An engineer must create an account to log in to the CLI of an access point for troubleshooting. Which configuration on the WLC will accomplish this?
An engineer just added a new MSE to Cisco Prime Infrastructure and wants to synchronize the MSE with the Cisco 5520 WLC, located behind a firewall in a DMZ. It is noticed that NMSP messages are failing between the two devices. Which traffic must be allowed on the firewall to ensure that the MSE and WLC are able to communicate using NMSP?
A wireless engineer must implement a corporate wireless network for a large company in the most efficient way possible. The wireless network must support 32 VLANs for 300 employees in different departments. Which solution must the engineer choose?
On a branch office deployment, it has been noted that if the FlexConnect AP is in standalone mode and loses connection to the WLC, all clients are disconnected, and the SSID is no longer advertised. Considering that FlexConnect local switching is enabled, which setting is causing this behavior?
What must be configured on the Global Configuration page of the WLC for an AP to use 802.1x to authenticate to the wired infrastructure?
All APs are receiving multicast traffic, instead of only the APs that need it. What is the cause of this problem?
What must be configured on ISE version 2.1 BYOD when using Single SSID?
What are two considerations when deploying a Cisco Hyperlocation? (Choose two.)
An engineer completes the setup of a two-node Cisco ISE deployment for a guest portal. When testing the portal, the engineer notices that sometimes there is a certificate CN mismatch. Which certificate type helps resolve this issue?
An engineer is implementing a FlexConnect group for access points at a remote location using local switching but central DHCP. Which client feature becomes available only if this configuration is changed?
An IT team is growing quickly and needs a solution for management device access. The solution must authenticate users from an external repository instead of the current local on the WLC, and it must also identify the user and determine what level of access users should have. Which protocol do you recommend to achieve these goals?
Which three characteristics of a rogue AP pose a high security risk? (Choose three.)
A network engineer wants to implement QoS across the network that supports multiple VLANs. All the APs are connected to switch ports and are configured in local mode. Which trust model must be configured on the switch ports to which the APs are connected?
A network engineer is implementing BYOD on a wireless network. Based on the customer requirements, a dual SSID approach must be taken. Which two advanced WLAN configurations must be performed? (Choose two.)
A customer requires wireless traffic from the branch to be routed through the firewall at corporate headquarters. A RADIUS server is in each branch location. Which Cisco FlexConnect configuration must be used?
An engineer must configure MSE to provide guests access using social media authentication. Which service does the engineer configure so that guests use Facebook credentials to authenticate?
The security learn is concerned about the access to all network devices, including the Cisco WLC. To permit only the admin subnet to have access to management, a CPU ACL is created and applied. However, guest users cannot get to the web portal. What must be configured to permit only admins to have access?
What is an important consideration when implementing a dual SSID design for BYOD?
Which QoS level is recommended for guest services?
An IT team is growing quickly and needs a solution for management device access. The solution must authenticate users from an external repository instead of the current local on the WLC, and it must also identify the user and determine what level of access users should have. Which protocol do you recommend to achieve these goals?
You plan to implement Cisco Identity Based Networking Services on a Cisco Catalyst 3850 Series Switch. Which switch command is required when configuring downloadable ACLs?
What must be configured on ISE version 2.1 BYOD when using Single SSID?
An engineer set up a VoWLAN with QoS on the WLC and a class map on the switch, but the markings are not being preserved correctly in the end-to- end traffic flow. Which two configurations on the wired network ensure end-to-end QoS? (Choose two.)
A Cisco 8540 WLC manages Cisco Aironet 4800 Series Aps and sends AoA data to a Cisco CMX 3375 Appliance for Hyperlocation. The load from the WLC is distributed to another virtual CMX server using CMX grouping. The virtual CMX server shows location RSSI data and not Hyperlocation. No AoA metrics are shown on the metrics page of the CMX virtual appliance under System > Metrics > Location Metrics. How must the network administrator resolve this issue?
An engineer configures the wireless LAN controller to perform 802.1x user authentication. Which configuration must be enabled to ensure that client devices can connect to the wireless, even when WLC cannot communicate with the RADIUS?
A network administrator managing a Cisco Catalyst 9800 WLC must place all iOS-connected devices to the guest SSID on VLAN 101. The rest of the clients must connect on VLAN 102 to distribute load across subnets. To achieve this configuration, the administrator configures a local policy on the WLC. Which two configurations are required? (Choose two.)
An engineer is following the proper upgrade path to upgrade a Cisco AireOS WLC from version 7.3 to 8.9. Which two ACLs for Cisco CWA must be configured when upgrading from the specified codes? (Choose two.)
A corporation has a wireless network where all access points are configured in FlexConnect. The WLC has a Data WLAN and a VoWiFi WLAN implemented where centrally-switched SSID is configured for the APs. Which QoS configuration must be implemented for the wireless packets to maintain the marking across the wired and wireless network?
A network engineer observes a spike in controller CPU overhead and overall network utilization after multicast is enabled on a controller with 500 APs. Which feature corrects the issue?
An IT administrator is managing a wireless network in which most devices are Apple iOS. A QoS issue must be addressed on the WLANs. Which configuration must be performed?
An engineer is implementing a FlexConnect group for access points at a remote location using local switching but central DHCP. Which client feature becomes available only if this configuration is changed?
An engineer is configuring multicast for two WLCs. The controllers are in different physical locations and each handles around 500 wireless clients. How should the CAPWAP multicast group address be assigned during configuration?
An engineer has configured Media Stream on the WLC and must guarantee at least 2 Mbps stream per user. Which RRC template should the engineer use?
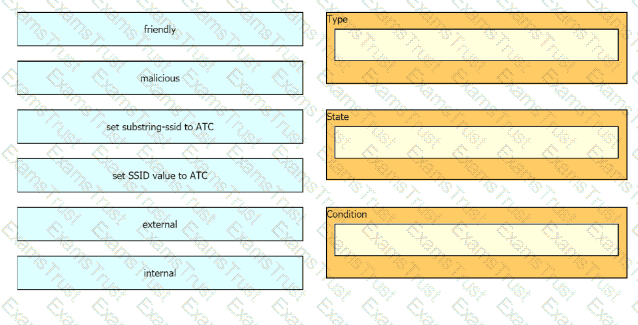
The network management team in a large shopping center has detected numerous rogue APs from local coffee shops that are broadcasting SSIDs. All of these SSIDs have names starting with ATC (for example, ATC302, ATC011, and ATC566). A wireless network engineer must appropriately classify these SSIDs using the Rogue Rules feature. Drag and drop the options from the left onto the categories in which they must be used on the right. Not all options are used.
An engineer must create an account to log in to the CLI of an access point for troubleshooting. Which configuration on the WLC will accomplish this?
A Cisco 8540 WLC manages Cisco Aironet 4800 Series Aps and sends AoA data to a Cisco CMX 3375 Appliance for Hyperlocation. The load from the WLC is distributed to another virtual CMX server using CMX grouping. The virtual CMX server shows location RSSI data and not Hyperlocation. No AoA metrics are shown on the metrics page of the CMX virtual appliance under System > Metrics > Location Metrics. How must the network administrator resolve this issue?
Refer to the exhibit.
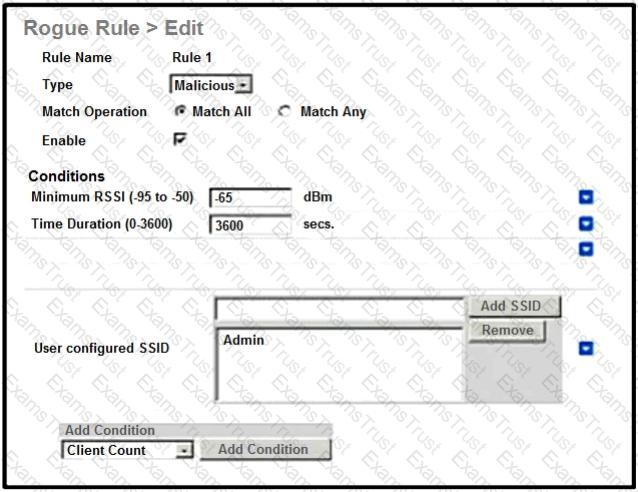
An engineer tries to manage the rogues on the Cisco WLC. Based on the configuration, which AP is marked as malicious by the controller?
An engineer must provide a graphical report with summary grouped data of the total number of wireless clients on the network. Which Cisco Prime Infrastructure report provides the required data?
An engineer needs to provision certificates on a Cisco Catalyst 9800 Series Wireless Controller. The customer uses a third-party CA server. Which protocol must be used between the controller and CA server to request and install certificates?
A network engineer must segregate all IPads on the guest WLAN to a separate VLAN. How does the engineer accomplish this task without using Cisco
ISE?
A user is trying to connect to a wireless network that is configured for WPA2-Enterprise security using a corporate laptop. The CA certificate for the authentication server has been installed on the Trusted Root Certification Authorities store on the laptop. The user has been prompted to enter the credentials multiple times, but the authentication has not succeeded. What is causing the issue?
A company is concerned about unauthorized APs on their wired and wireless networks. The company implements a Cisco Catalyst Center (formerly DNA Center) solution. Which feature must be enabled?
Where is a Cisco OEAP enabled on a Cisco Catalyst 9800 Series Wireless Controller?
The CTO of an organization wants to ensure that all Android devices are placed into a separate VLAN on their wireless network. However, the CTO does not want to deploy ISE. Which feature must be implemented on the Cisco WLC?
Which statement about the VideoStream/Multicast Direct feature is true?
An organization is supporting remote workers in different locations. In order to provide wireless network connectivity and services, OfficeExtend has been implemented. The wireless connectivity is working, but users report losing connectivity to their local network printers. Which solution must be used to address this issue?
A wireless administrator must assess the different client types connected to Cisco Catalyst 9800 Series Wireless Controller without using any external servers. Which configuration must be added to the controller to achieve this assessment?
A customer is concerned that their wireless network is detecting spurious threats from channels that are not being used by their wireless infrastructure. Which two technologies must they deploy? (Choose two.)
An IT administrator deployed an OEAP to the home of a remote user, but the OEAP cannot reach the WLC. Which two configuration settings must be completed before an OEAP is deployed successfully? (Choose two.)
An administrator receives reports of many interferers in the wireless network and wants to get the location of these interferers from the maps in Cisco Prime Infrastructure.
When looking at the floor plans/maps, the administrator does not see any interferers, but can see all wireless clients located successfully.
Which two statements define the cause of the issue? (Choose two.)
Refer to the exhibit.
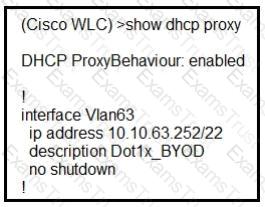
A network administrator deploys the DHCP profiler service in two ISE servers: 10.3.10.101 and 10.3.10.102. All BYOD devices connecting to WLAN on VLAN63 have been incorrectly profiled and are assigned as unknown profiled endpoints. Which action efficiently rectifies the issue according to Cisco recommendations?
An engineer must achieve the highest level of location accuracy possible for a new mobile application. Which technology must be implemented for this use case?
Which CLI command do you use to shut down the 2.4 GHz radio of the Floor1_AP1 AP on a Cisco 3850 Switch?
An engineer is following the proper upgrade path to upgrade a Cisco AireOS WLC from version 7.3 to 8.9. Which two ACLs for Cisco CWA must be configured when upgrading from the specified codes? (Choose two.)
An IT administrator deploys Cisco 2802i APs in all office locations, including main campus and branch offices. The WLC that manages the APs is located at the data center on the main campus. The APs on the main campus are configured to use Local mode and the APs in the branches use FlexConnect mode. Which configuration must be applied to the APs for corporate devices on the main campus to be mapped to the local LAN switch on different VLANs according to the VLAN tag ID and WLAN?
After looking in the logs, an engineer notices that RRM keeps changing the channels for non-IEEE 802.11 interferers. After surveying the area, it has been decided that RRM should not change the channel. Which feature must be enabled to ignore non-802.11 interference?
An engineer must enable LSS for the AppleTV mDNS service only when ORIGIN is set to Wired. Which action meets this requirement?
A customer is experiencing performance issues with its wireless network and asks a wireless engineer to provide information about all sources of interference and their impacts to the wireless network over the past few days. Where can the requested information be accessed?
An SSID is set up with central web authentication using Cisco ISE The new SSID uses guest tunneling from the foreign controller to the anchor controller. Which device must be configured ISE as the one performing the RADIUS authentication requests for the web authentication method?
An engineer is setting up a new unique NAD on a Cisco ISE.
Which two parameters must be configured? (Choose two.)
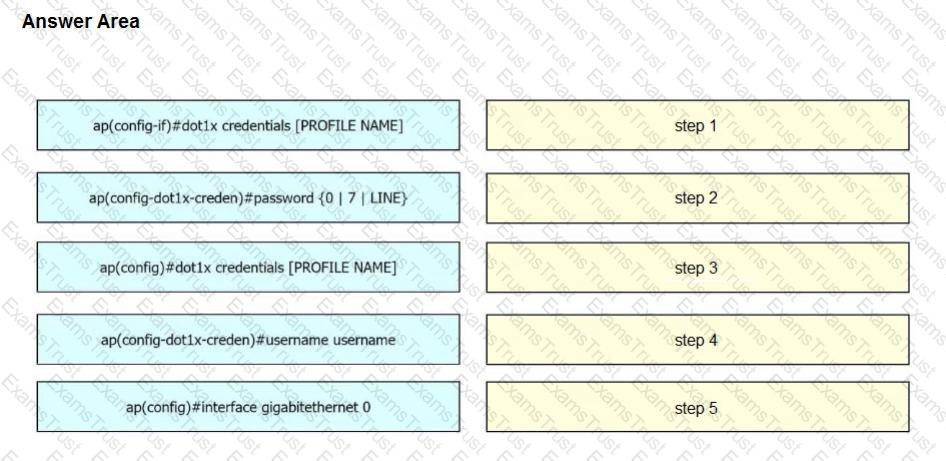
A network engineer must get an autonomous AP to authenticate to the upstream switch via IEEE 802.1 X. Drag and drop the commands from the left onto the right to complete the configuration.
An engineer is planning an image upgrade of the WLC, and hundreds of APs are spread across remote sites with limited WAN bandwidth. The engineer must minimize the WAN utilization for this upgrade. Which approach must be used for the AP image upgrade?
An engineer is configuring location services within Cisco Spaces (formerly Cisco DNA Spaces). The solution must track interfering devices. Which component of Cisco Spaces must be configured?
A WLC must be configured to allow multiple mDNS profiles based on a user authentication profile configured in Cisco ISE. Which WLAN setting must be configured?