An engineer is modifying an existing data policy for VPN 115 to meet these additional requirements:
When browsing government websites, the traffic must use direct internet access.
The source address of the traffic leaving the site toward the government websites must be set to an IP range associated with the country itself, a particular TLOC.
The policy configuration is as follows:

Which policy sequence meets the requirements without interfering with other destinations?
The branch users of an organization must be prevented from accessing malicious destinations, and the local files on users' systems must be protected from malware. Which two Cisco products must the organization deploy? (Choose two.)
Which component of the Cisco SD-WAN control plane architecture should be located in a public Internet address space and facilitates NAT-traversal?
An engineer wants to automate the onboarding process for a WAN Edge router with vManage. Which command will accomplish this?
Refer to the exhibit.
An organization is testing a Cisco SD-WAN solution and decided to have the control plane established first and not the data plane at the time of migration. Which configuration achieves this goal?
Which feature allows reachability to an organization’s internally hosted application for an active DNS security policy on a device?
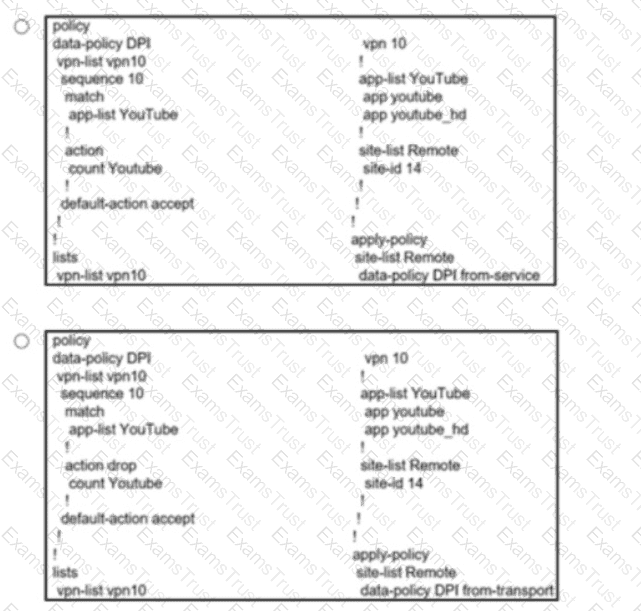
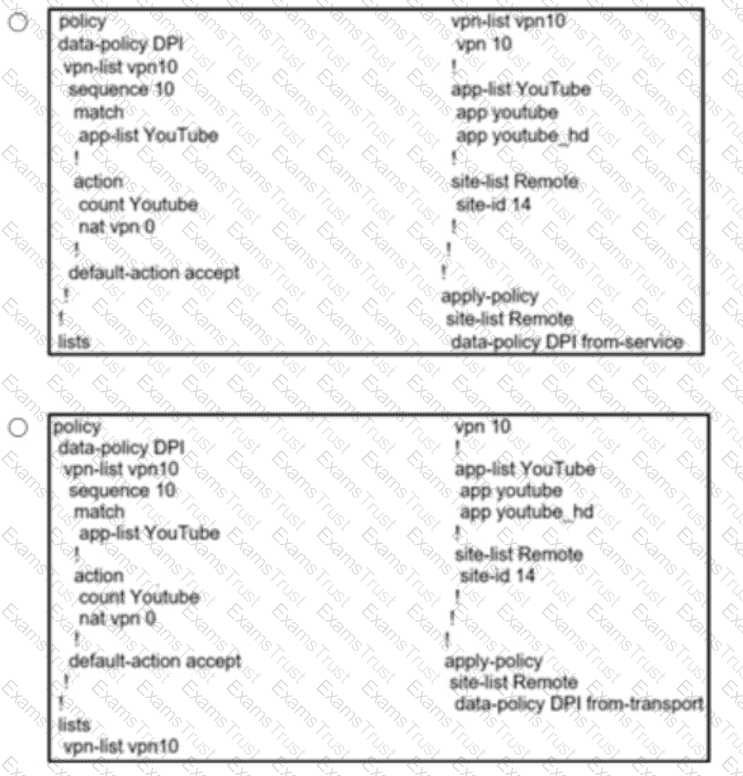
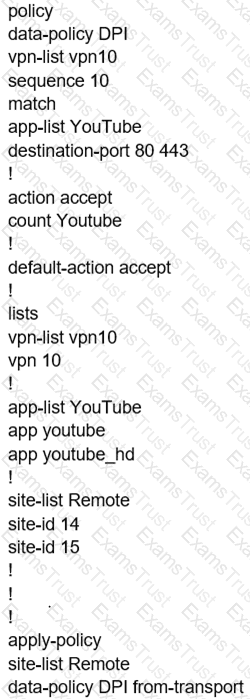
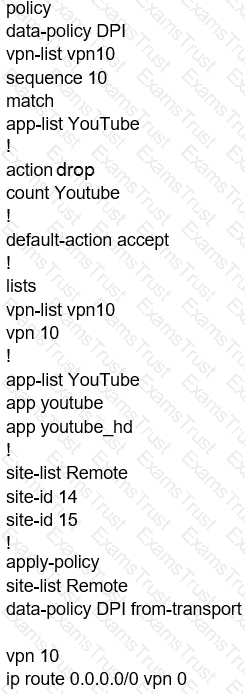
Which configuration change allows direct internet access at the branch site for YouTube traffic?
What do receivers request to join multicast streams in a Cisco SO-WAN network?
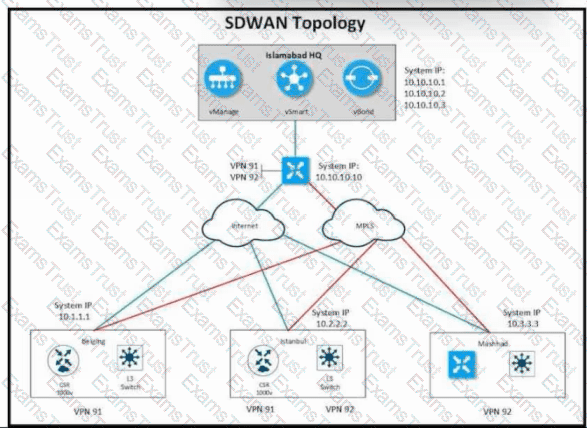
Refer to the exhibit. Company ABC has a hub-and-spoke topology in place and currently is load balancing their data traffic at the hub site over MPLS and the public Internet. The leased circuit must be preferred over the shared circuit. Which configuration meets the requirement?
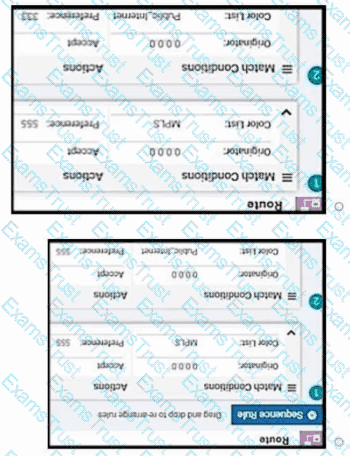
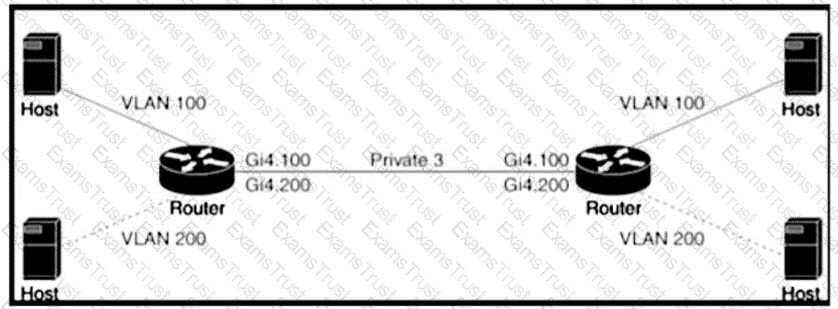
Refer to the exhibit An engineer is configuring a QoS policy to shape traffic for VLAN 100 on a subinterface Which policy configuration accomplishes the task?
A)
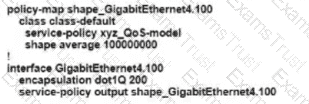
B)

C)

D)
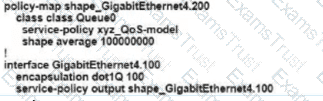
Which two platforms for the Cisco SD-WAN architecture are deployable in a hypervisor on-premises or in IAAS Cloud? (Choose two.)
Which two WAN Edge devices should be deployed in a cloud? (Choose two.)
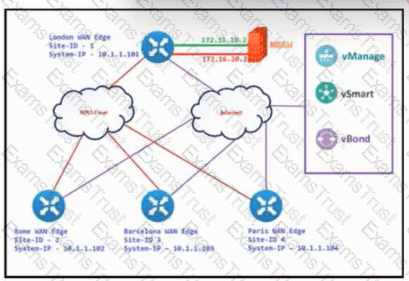
Refer to the exhibit. The Cisco SD-WAN is deployed using the default topology. The engineer wants to configure a service insertion policy such that all data traffic between Rome to Paris is forwarded through the NGFW located in London. Which configuration fulfills this requirement, assuming that the Service VPN ID is 1?
What is the threshold to generate a warning alert about CPU or memory usage on a WAN Edge router?
Refer to the exhibit.

What does the BFD value of 8 represent?
Refer to the exhibit.
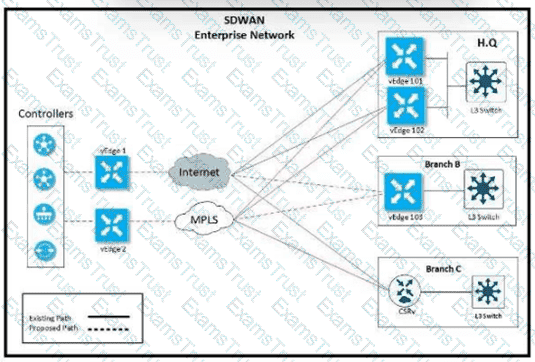
The network team must configure branch B WAN Edge device 103 to establish dynamic full-mesh IPsec tunnels between all colors with branches over MPLS and Internet circuits. The branch ts configured with:
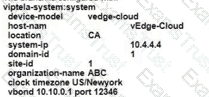
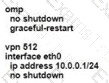
Which configuration meets the requirement?
A)

B)

C)

D)

What is the maximum number of IPsec that are temporarily created and converged on a new set if IPsec Sas in the pairwise keys process during a simultaneous rekey?
Which data policy configuration influences BGP routing traffic flow from LAN to WAN?
A)

B)

C)

D)

Refer to the exhibit. An administrator is configuring a policy in addition to an existing hub-and-spoke policy for two sites that should directly communicate with each other. How is this policy configured?
What is the default value for the number of paths advertised per prefix in the OMP feature template?
Which protocol is used by the REST API to communicate with network devices in the Cisco SD-WAN network?
A network administrator is configuring an application-aware firewall between inside zones to an outside zone on a WAN edge router using vManage GUI. What kind of Inspection is performed when the ‘’inspect’’ action is used?
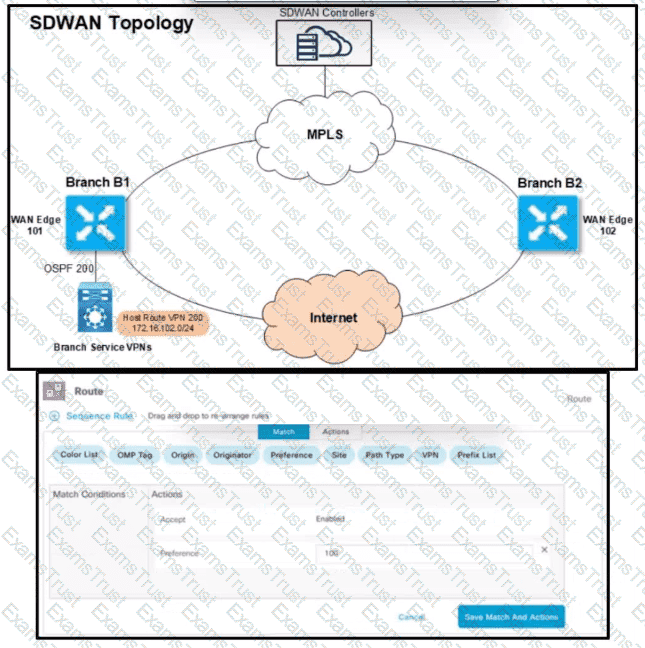
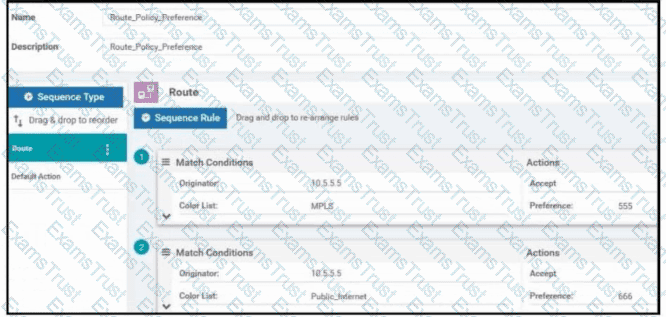
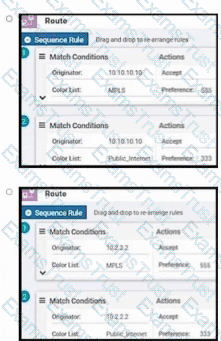
Refer to the exhibit. An engineer must configure the Overlay Management Protocol route preference so that when B2 tries to reach host routes advertised by B1 it always chooses the MPLS circuit. Which two match conditions must be configured to accomplish this task? (Choose two.)
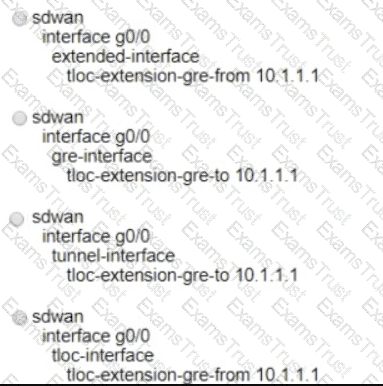
A network administrator is configuring a tunnel interface on a branch Cisco IOS XE router to run TLOC extensions. Which configuration will extend a TLOC over a GRE tunnel to another router in the branch?
Which two mechanisms are used by vManage to ensure that the certificate serial number of the WAN Edge router that is needed to authenticate is listed in the WAN Edge Authorized Señal Number Hst’ (Choose two)
Which protocol Is used by the REST API to communicate with network services in the Cisco SO-WAN network?
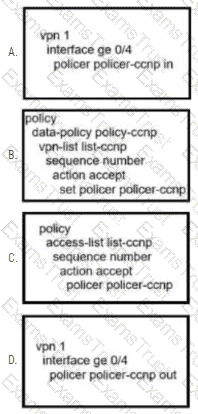
An administrator wants to create a policy to add a traffic policer called "politer-ccnp" to police data traffic on the WAN Edge. Which configuration accomplishes this task in vSmart?
What prohibits deleting a VNF image from the software repository?
What is the result during a WAN Edge software upgrade process if the version of the WAN Edge software is higher than the one running on a controller device?
How does the replicator role function in cisco SD-WAN?
Which cloud based component in cisco SD-WAN is responsible for establishing a secure connection to each WAN edge router and distributes routers and policy information via omp?
An organization wants to discover monitor and track the applications running on the WAN Edge device on the LAN Which configuration achieves this goal?
An engineer must apply the configuration for certificate installation to vBond Orchestrator and vSmart Controller. Which configuration accomplishes this task?
Which TCP Optimization feature is used by WAN Edge to prevent unnecessary retransmissions and large initial TCP window sizes to maximize throughput and achieve a better quality?
WAN Edge routers are configured manually to use UDP port offset to use nondefault offset values when IPsec tunnels are created. What is the offse range?
What is the size of SGT data in the metadata header?
How is a TLOC uniquely identified from a WAN Edge router to the SD-WAN transport network?
Which protocol is used for the vManage to connect to the vSmart Controller hosted in Cloud?
Which Cisco SD-WAN configuration provides the advantages of day-zero deployment and reusable configuration components?
How is the scalability of the vManage increased in Cisco SD-WAN Fabric?
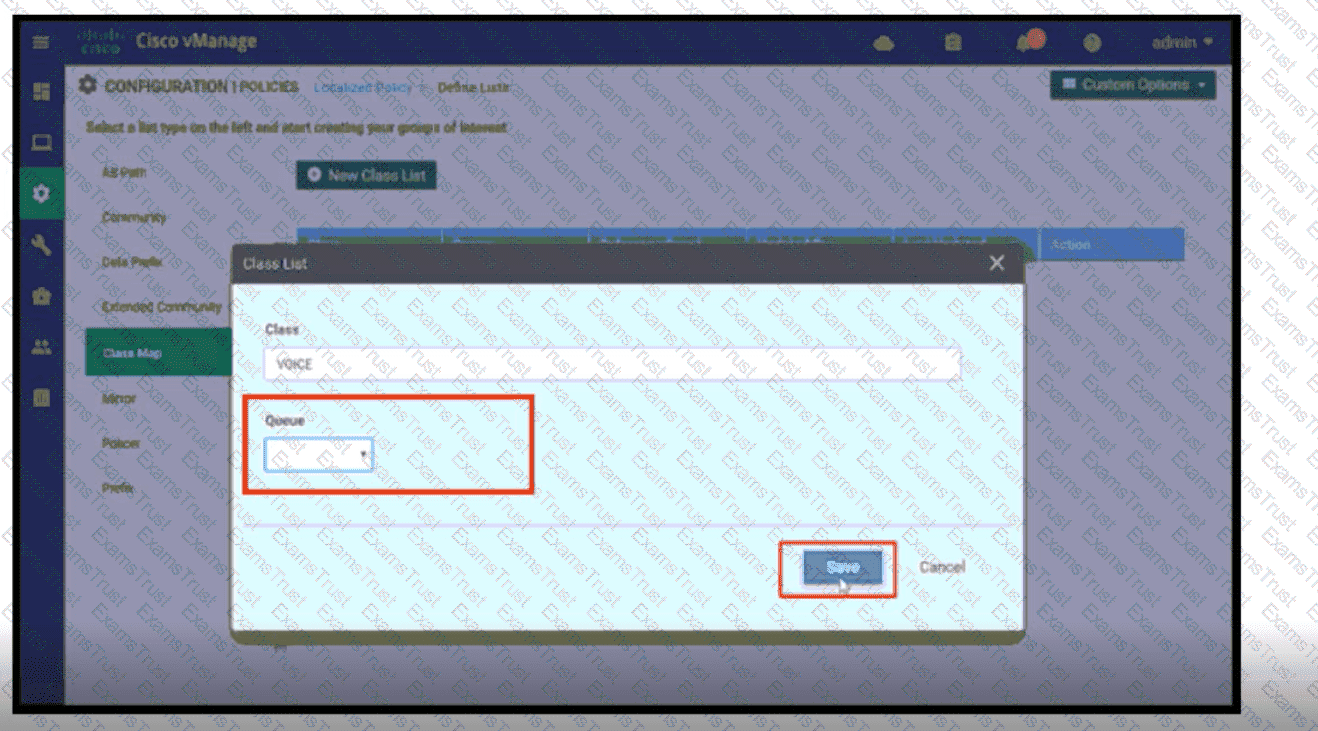
Refer to the exhibit. A network administrator is setting the queueing value for voice traffic for one of the WAN Edge routers using vManager GUI. Which queue value must be set to accomplish this task?
How many concurrent sessions does a vManage REST API have before it invalidates the least recently used session if the maximum concurrent session number is reached?
Which routing protocol is used to exchange control plane information between vSmart controllers and WAN Edge routers in the Cisco SD-WAN secure extensible network?
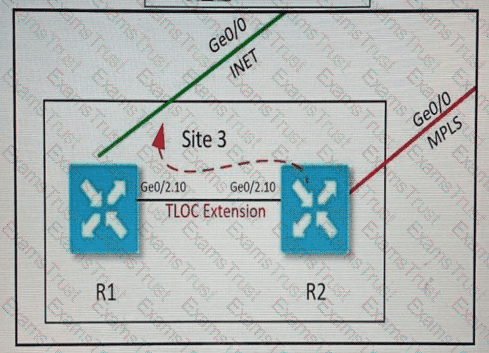
Refer to the exhibit. Which configuration extends the INET interface on R1 to be used by R2 for control and data connections?
A)

B)

C)
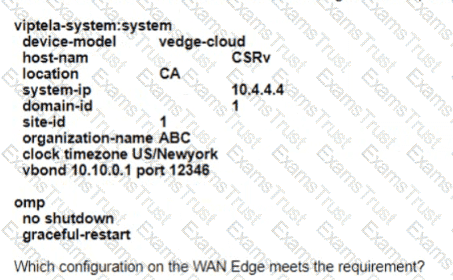
A customer must upgrade the cisco SD-WAN devices and controllers from version 19.2 to version 20.3. The devices include WAN Edge cloud, vManage, vSmart, and vBond. Which types of image types of image files are needed for this upgrade?
In which Cisco SD-WAN deployment scenario does Cisco Umbrella SIG deliver the most value?
Which port is used for vBond under controller certificates if no alternate port is configured?
Which policy configures an application-aware routing policy under Configuration > Policies?
What are the default username and password for vSmart Controller when it is installed on a VMware ESXi hypervisor'?
Which component of the Cisco SD-WAN secure extensible network provides a single pane of glass approach to network monitoring and configuration?
An engineer is configuring a data policy IPv4 prefixes for a site WAN edge device on a site with edge devices. How is this policy added using the policy configuration wizard?
What is a requirement for a WAN Edge to reach vManage, vBond, and vSmart controllers in a data center?
Which configuration component is used in a firewall security policy?
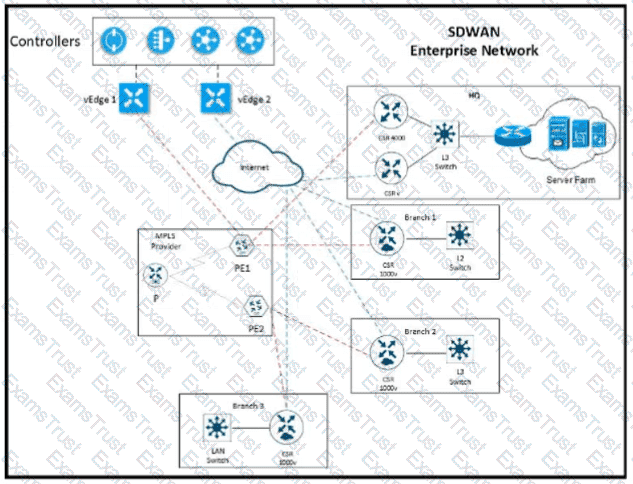
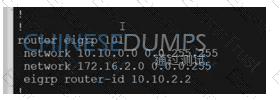
Refer to the exhibit The network team must configure El GRP peering at HQ with devices in the service VPN connected to WAN Edge CSRv. CSRv is currently configured with
A)

B)

C)
D)

Drag and drop the alarm states from the left onto the corresponding alarm descriptions on the right.

Which two performance data details are provided by Cisco SO-WAN vAnalytics? (Choose two)
Where on vManage does an engineer find the details of control node failure?
A company is using Catalyst SD-WAN Manager as its root certificate authority server and must generate a root certificate using the vShell (Linux) built into the CLI of Catalyst SD-WAN Manager. Which command must be issued to generate the root certificate?
A voice packet requires a latency of 50 msec. Which policy is configured to ensure that a voice packet is always sent on the link with less than a 50 msec delay?
For data plane resiliency, what does the Cisco SD-WAN software implement?
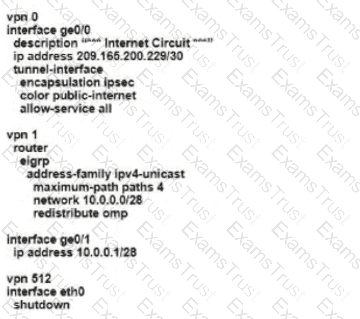
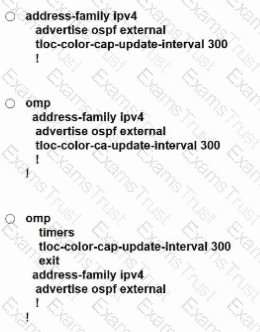
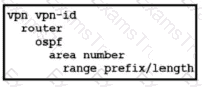
An engineer must advertise OSPF-learned routes and modify the update interval for route filtering by TLOC color to 300 on an SD-WAN device. Which configuration accomplishes this
task?

Which device in the SD- WAN solution receives and categorizes event reports, and generates alarms?
In which VPN is the NAT operation on an outgoing interface configured for direct Interne! access?
What problem happens on a device with two serial numbers, a unique device identifier (UDI), and secure unique device identifier (SUDI) when an engineer provisions ISR 4000 by PnP using only a UDI?
Which set of platforms must he in separate VMS as of release 16.1?
What is an advantage of using auto mode versus static mode of power allocation when an access point is connected to a PoE switch port?
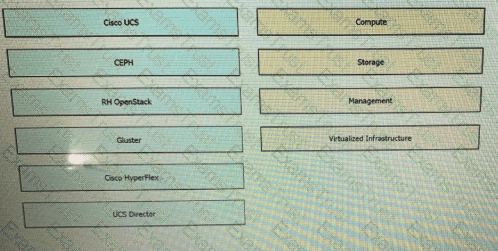
Drag and drop the components from the left onto the corresponding Cisco NFV infrastructure Building Blocks on the right. Not all options are used.
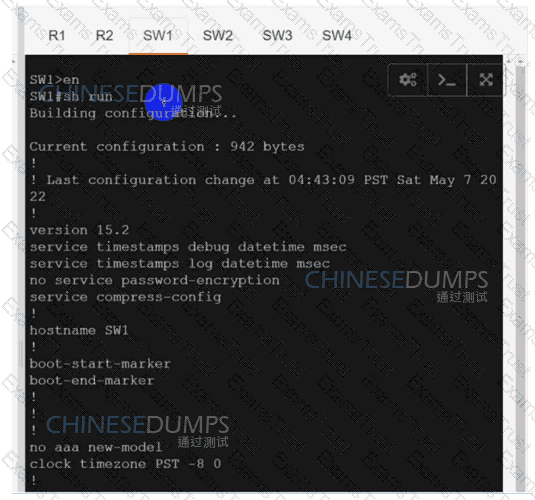
Configure individual VRFs for each customer according to the topology to achieve these goals :
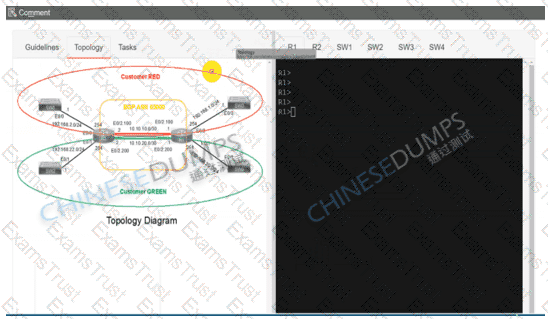

R1
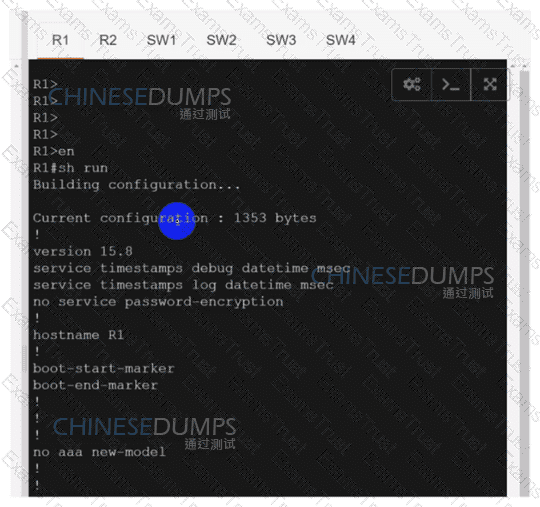
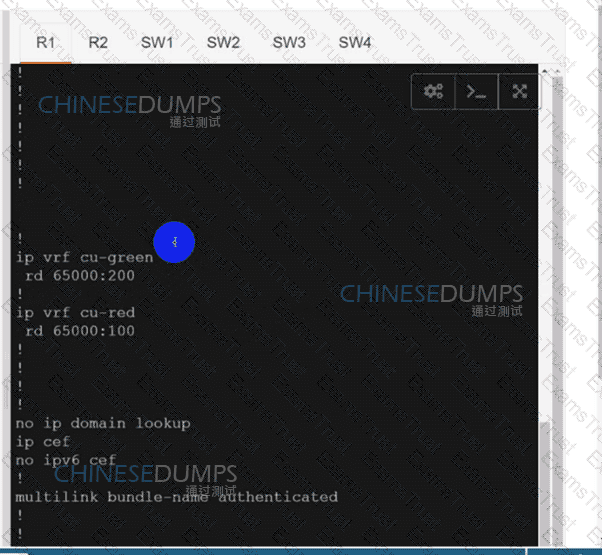
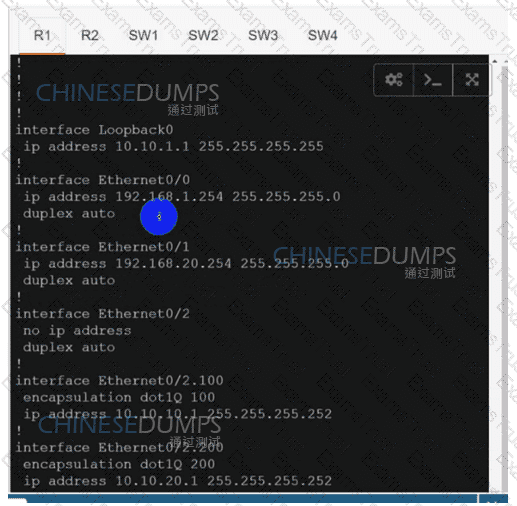
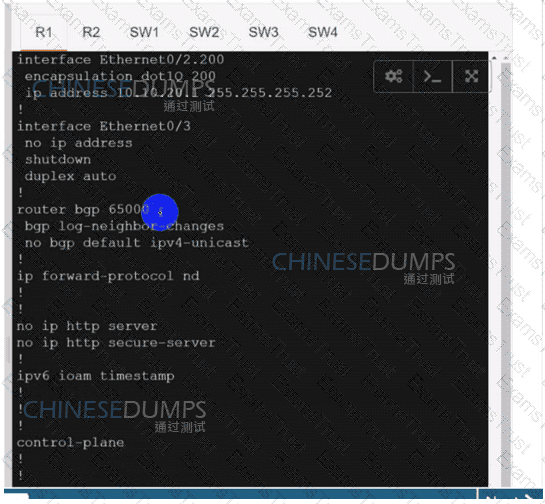
R2
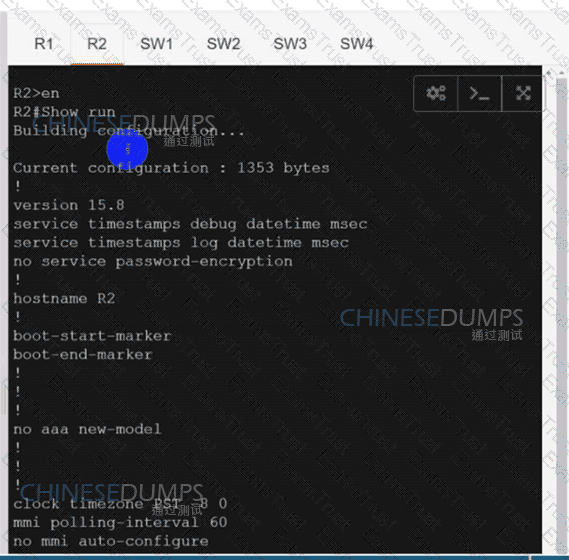
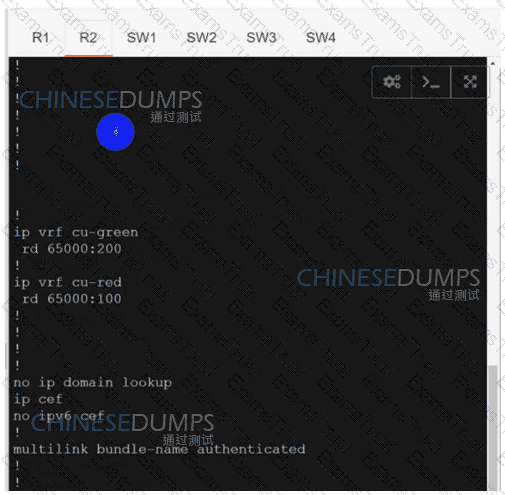
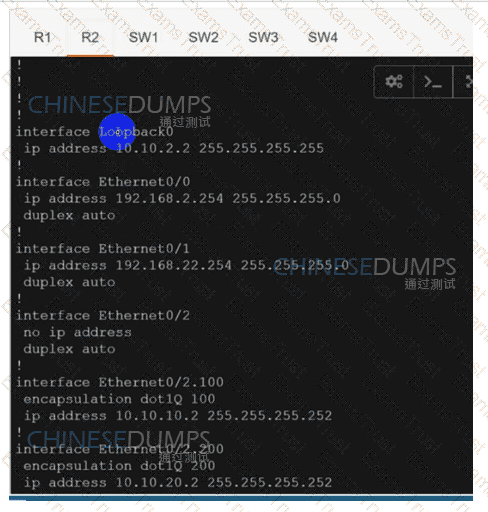
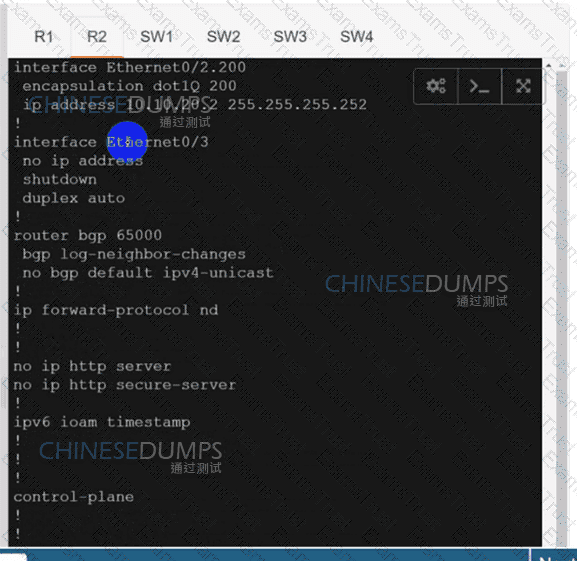
SW1
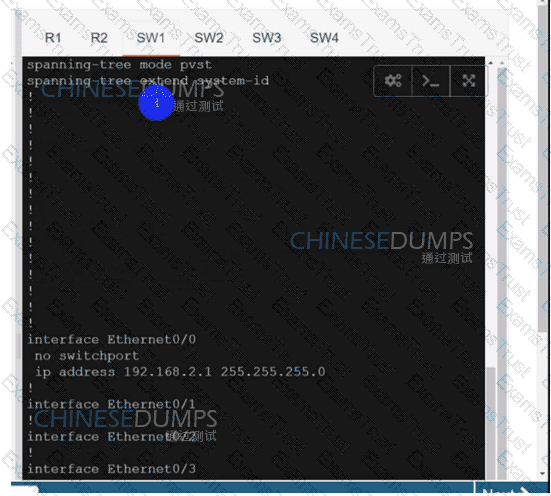
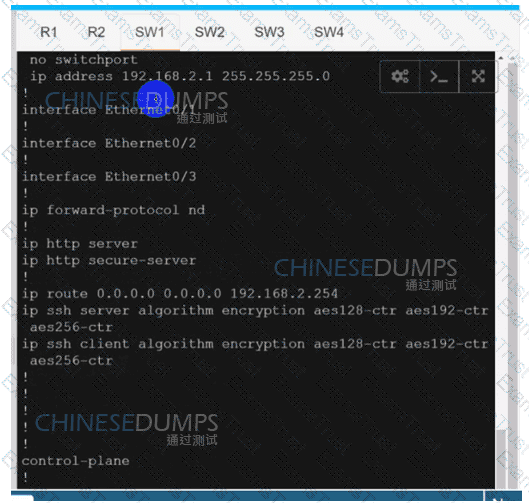
SW2
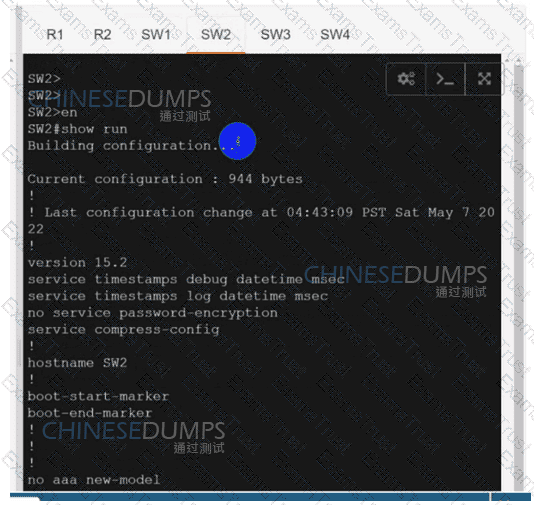
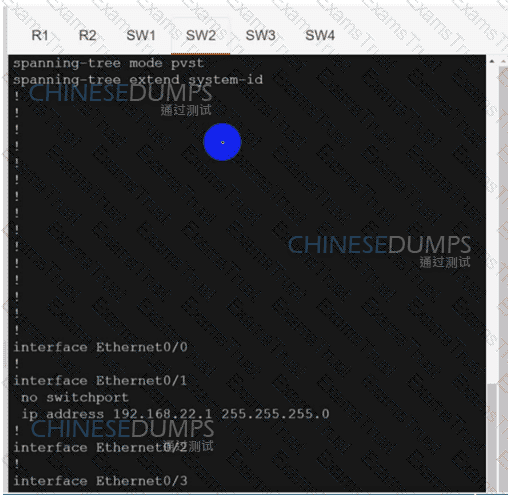
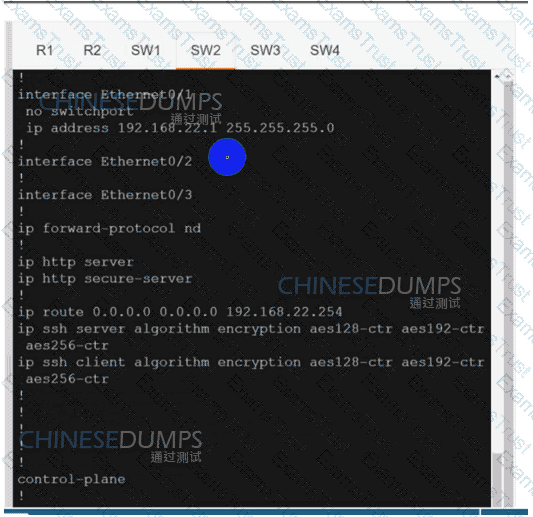
SW3
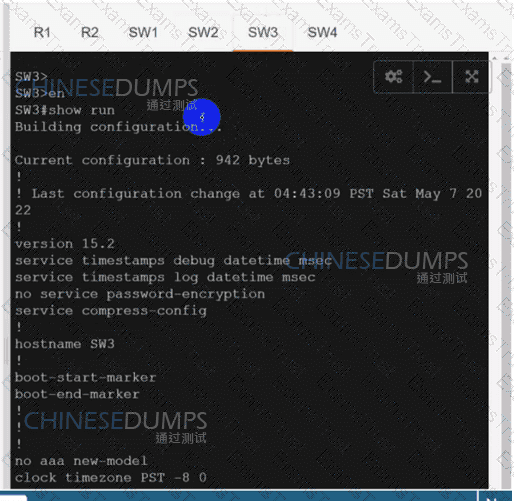
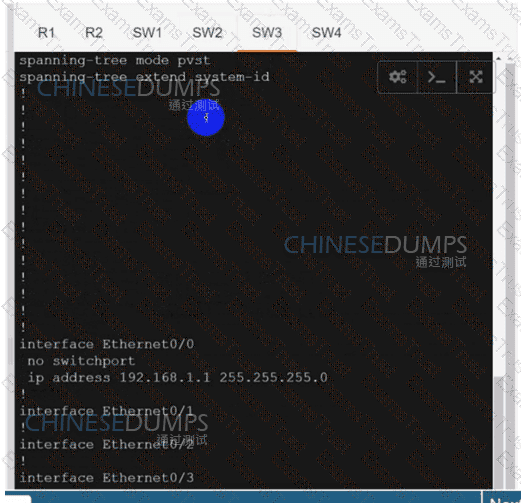
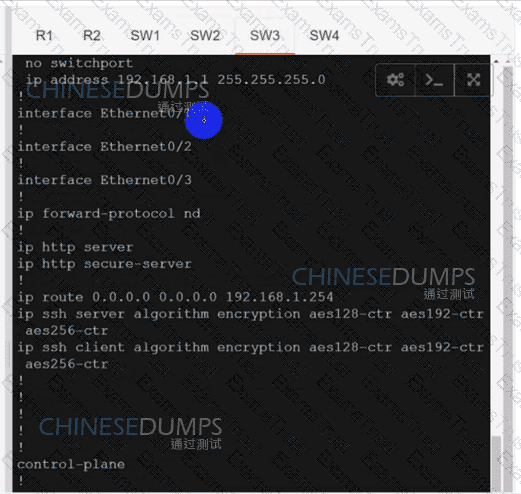
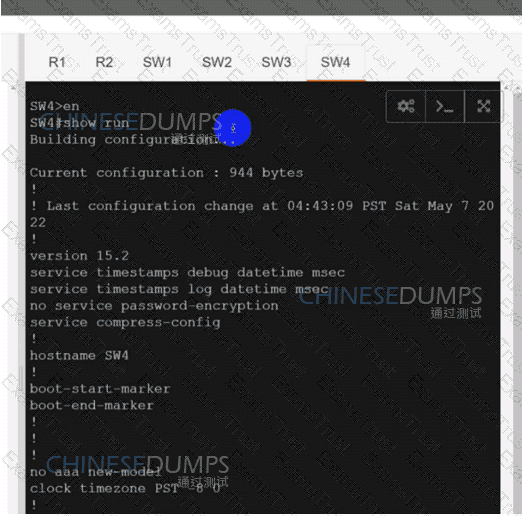
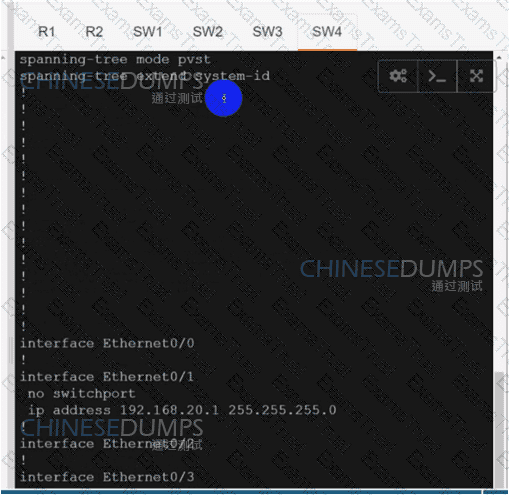
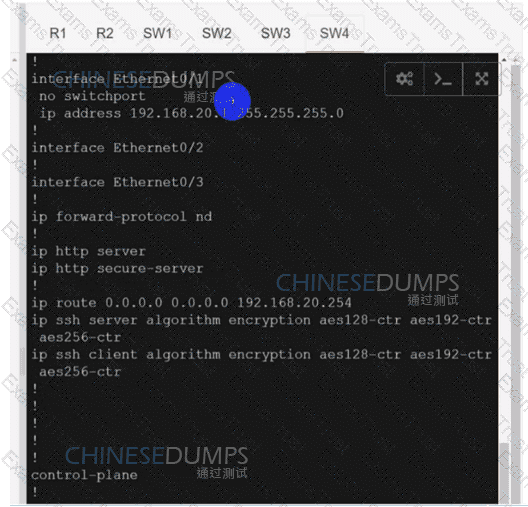
An engineer must configure two branch WAN Edge devices where an Internet connection is available and the controllers are in the headquarters. The requirement is to have IPsec VPN tunnels established between the same colors. Which configuration meets the requirement on both WAN Edge devices?
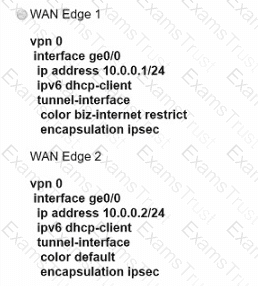
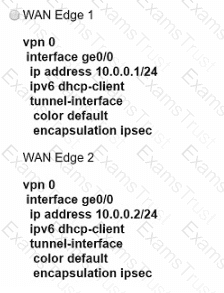

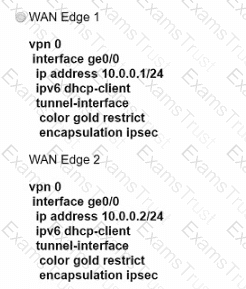
What are the two advantages of configuration groups in a Cisco SD-WAN deployment? (Choose two.)
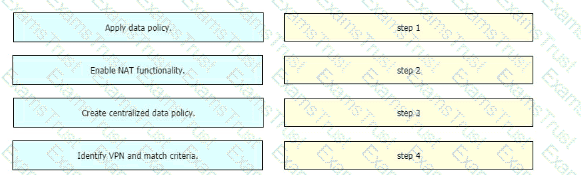
Drag and drop the actions from the left into the correct sequence on the right to create a data policy to direct traffic to the Internet exit.
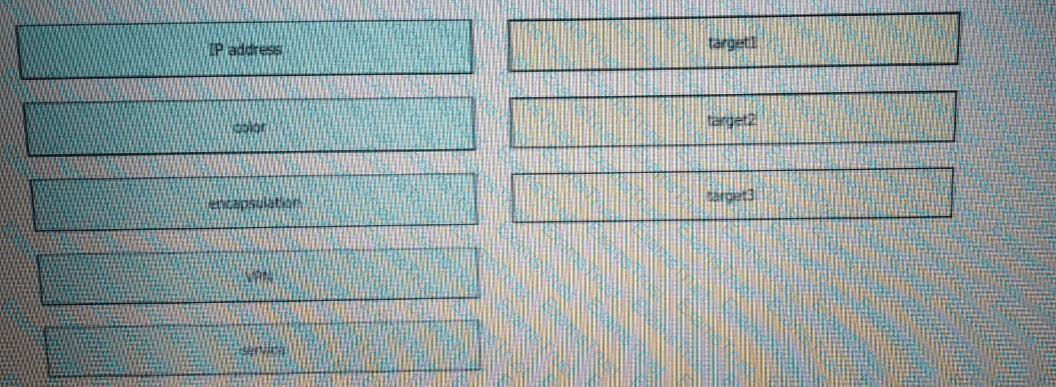
Drag and drop the attributes from the left that make each transport location unique onto the right. Not all options are used.
A vEdge platform is sending VRRP advertisement messages every 10 seconds. Which value configures the router back to the default timer?
Refer to the exhibit. Which issue is shown, and which action must an engineer take to resolve the issue?
Which OSPF command makes the WAN Edge router a less preferred exit from a site with a dual WAN Edge design?
A)
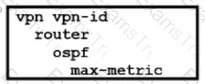
B)
C)

D)
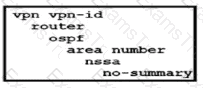
Which third-party Enterprise CA server must be used (or a cloud-based vSmart controller?
At which layer does the application-aware firewall block applications on a WAN Edge?
What is the function of colocation in Cloud OnRamp SaaS?
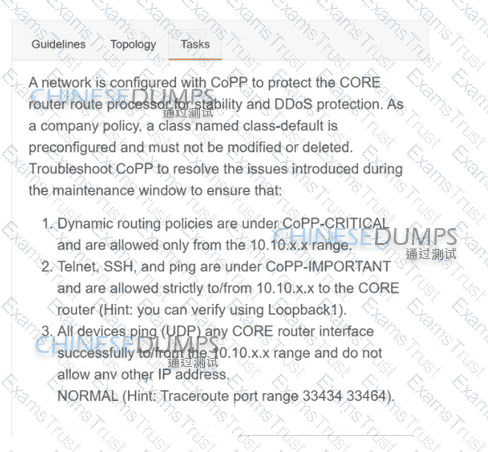
A network is configured with CoPP to protect the CORE router route processor for stability and DDoS protection. As a company policy, a class named class-default is preconfigured and must not be modified or deleted. Troubleshoot CoPP to resolve the issues introduced during the maintenance window to ensure that:
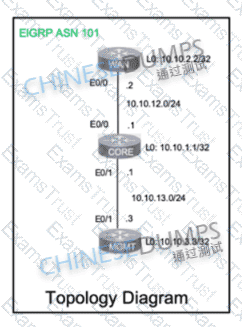
WAN


CORE
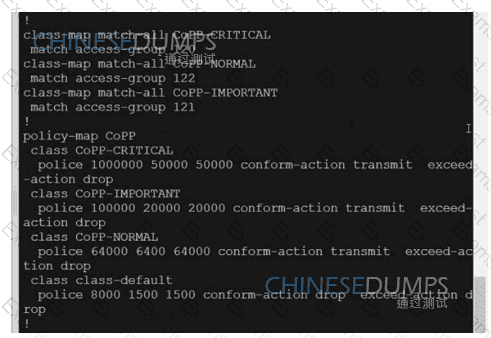


MGMT

Which platform cannot provide IPS and URL filtering capabilities?
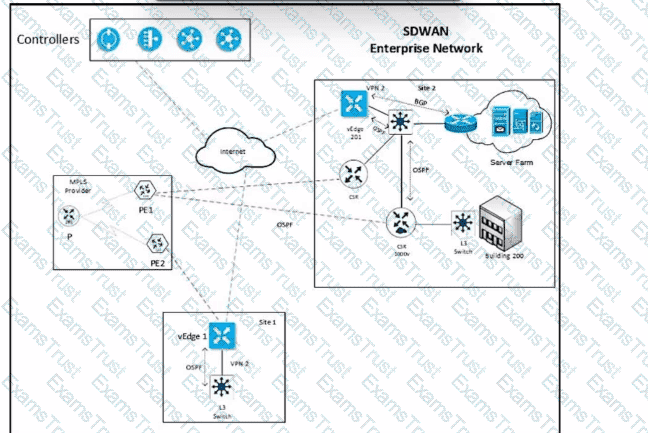
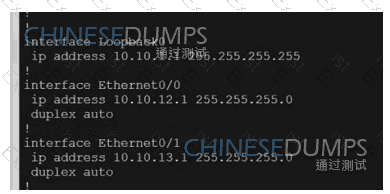
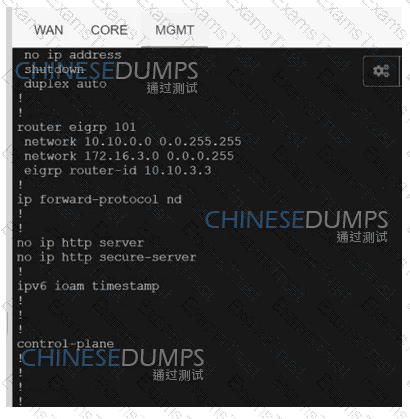
Refer to the exhibit. Which configuration ensures that OSPP routes learned from Site2 are reachable at Stein and vice-versa?
Which alarm setting is configured to monitor serious events that affect but do not shut down, the operation of a network function?
An enterprise needs DIA on some of its branches with a common location ID: A041:B70C: D78E::18 Which WAN Edge configuration meets the requirement?
A)
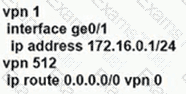
B)
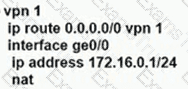
C)
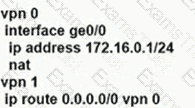
D)
Which protocol runs between the vSmart controllers and WAN Edge routers when the vSmart controller acts like a route reflector?
What is a benefit of the application aware firewall feature in the Cisco SD-WAN solution?
An engineer must avoid routing loops on the SD-WAN fabric for routes advertised between data center sites Which BGP loop prevention attribute must be configured on the routers to meet this requirement?
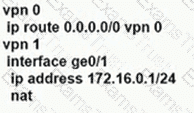
Refer to the exhibit.
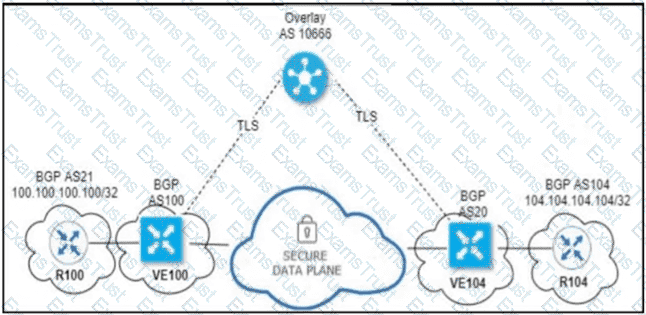
An engineer configured OMP with an overlay-as of 10666. What is the AS-PATH for prefix 104.104.104.104/32 on R100?
In a Cisco SD-WAN network, which component is responsible for distributing route and policy information via the OMP?
What is the behaviour of vBond orchestrator?
Refer to the exhibit.

The network design team has advised to use private IP addresses and private colors over the SP circuit for the data plane connections. The Public IP should be used for control connections. Which configuration should be applied at SiteA to achieve this task?


Which secure tunnel type should be used to connect one WAN Edge router to other WAN Edge routers?
Which two image formats are supported for controller codes? (Choose two.)
How many cloud gateway instance(s) can be created per region when provisioning Cloud OnRamp for Multicloud from AWS in a multiregion environment?
An engineer is configuring a WAN Edge router for DIA based on matching QoS parameters. Which two actions accomplish this task? (Choose two.)
Which two algorithms authenticate a user when configuring SNMPv3 monitoring on a WAN Edge router? (Choose two.)
Which pathway under Monitor > Network > Select Device is used to verify service insertion configuration?
Refer to the exhibit.
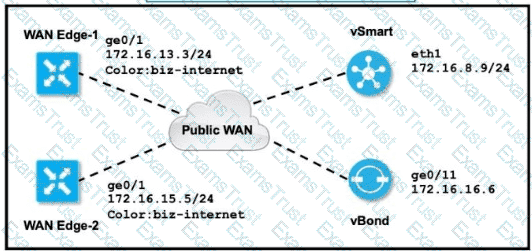
The tunnel interface configuration on both WAN Edge routers is:

Which configuration for WAN Edge routers will connect to the Internet?

Which two protocols are supported for software image delivery when images are hosted on a remote server? (Choose two.)
Which OMP route is selected for equal OMP route preference values on WAN Edge routers?
Which two metrics must a cloud Edge router use to pick the optimal path for a SaaS application reachable via a gateway site? (Choose two.)
Which two different states of a WAN Edge certificate are shown on vManage? (Choose two.)
An organization wants to use the cisco SD-WAN regionalized service-chaining feature to optimize cost and user experience with application in the network, which allows branch routers to analyze and steer traffic toward the required network function. Which feature meets this requirement?
Which two actions are necessary to set the Controller Certificate Authorization mode to indicate a root certificate? (Choose two)
An administrator must configure an ACL for traffic coming in from the service-side VPN on a specific WAN device with circuit ID 391897770. Which policy must be used to configure this ACL?
How many vManage NMSs should be installed in each domain to achieve scalability and redundancy?
Which configuration defines the groups of interest before creation of the access list or route map?
A)
B)
C)
D.
Which configuration allows users to reach YouTube from a local Internet breakout?
A)
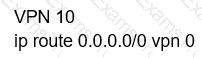
B)
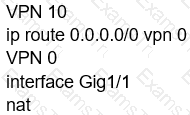
C)
D)
What is the ZTP workflow for Cisco IOS XE-based devices?

A customer is receiving routes via OMP from vSmart controller for a specific VPN. The customer must provide access to the W2 loopback received via OMP to the OSPF neighbor on the service-side VPN, which configuration fulfils these requirements?


Which feature delivers traffic to the Cisco Umbrella SIG cloud from a Cisco SD-WAN domain?
How many subnets are necessary in Azure VNet for a WAN Edge device to function in the cloud deployment?
An administrator is configuring the severity level on the vManage NMS for events that indicate that an action must be taken immediately. Which severity level must be configured?

Refer to the exhibit A user has selected the options while configuring a VPN Interface Ethernet feature template What is the required configuration parameter the user must set in this template for this feature to function?
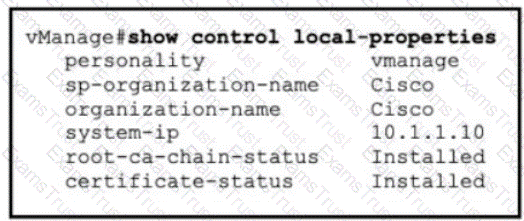
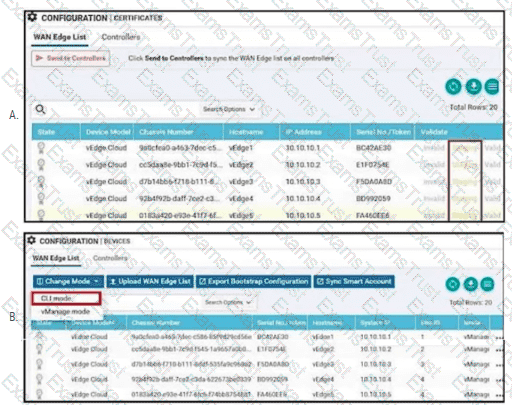
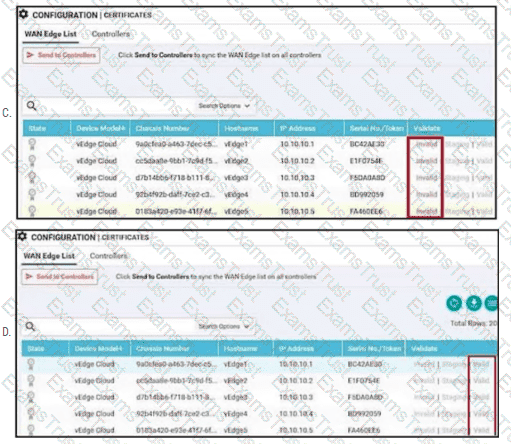
Refer to the exhibit A vBond controller was added to the controller list with the same Enterprise Root CA certificate as vManage. The two controllers can reach each other via VPNO and share the same organization name, but the control connection is not initiated- Which action resolves the issue?
Which SD-WAN component is configured to enforce a policy to redirect branch-to-branch traffic toward a network service such as a firewall or IPS?
A network administrator is tasked to make sure that an OMP peer session is closed after missing three consecutive keepalive messages in 3 minutes. Additionally, route updates must be sent every minute. If a WAN Edge router becomes unavailable, the peer must use last known information to forward packets for 12 hours. Which set of configuration commands accomplishes this task?
Which set of elements are verified by the controller to confirm the identity of edge devices?
Which protocol is used to measure jitter, loss, and latency on SD-WAN overlay tunnels?
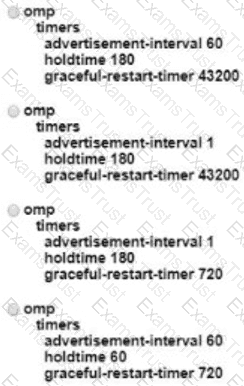
Which feature template configures OMP?
A)
B)
C)
D)
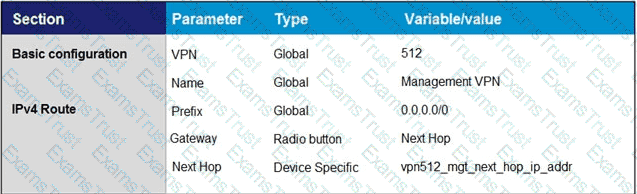
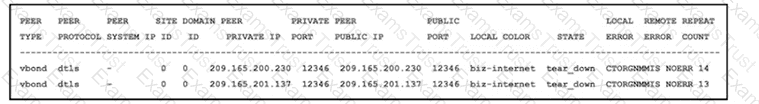
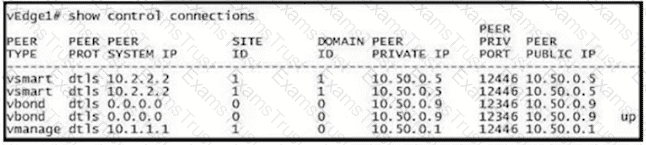
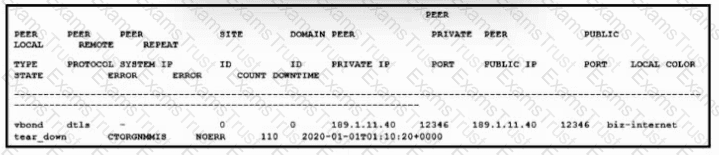
Refer to the exhibit An engineer is getting a CTORGNMMIS error on a controller connection Which action resolves this issue?
What is a restriction when configuring a tunnel interface?
Which SD-WAN component detects path performance information in the organization to report the issue to the service provider at site ID:S4288T5E44F04?
What is the function of the AppNav Controller in the Cisco SD-WAN AppNav solution?
What is a description of vManage NMS?
When redistribution is configured between OMP and BGP at two Data Center sites that have Direct Connection interlink, which step avoids learning the same routes on WAN Edge routers of the DCs from LAN?
Refer to the exhibit.
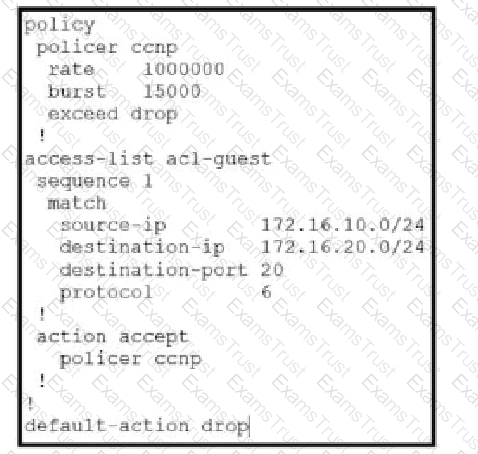
Which QoS treatment results from this configuration after the access list acl-guest is applied inbound on the vpn1 interface?
How many vCPUs and how much RAM are recommended to run the vSmart controller on the KVM server for 251 to 1000 devices in software version 20.4.x?
Refer to the exhibit.
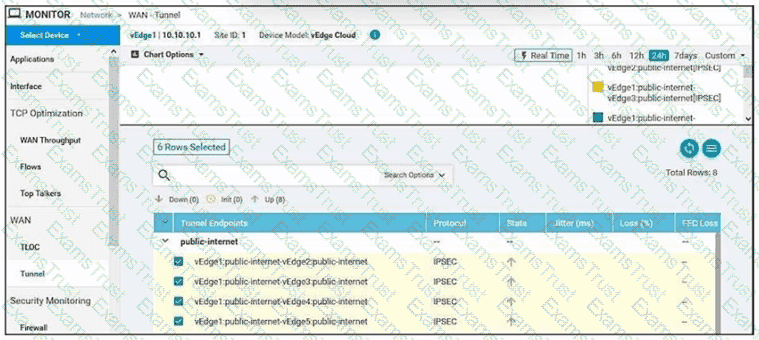
Which command-line configuration on a WAN Edge device achieves these results?
A)
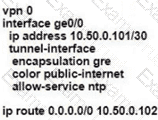
B)
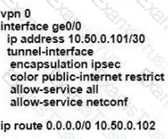
C)
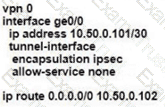
D)
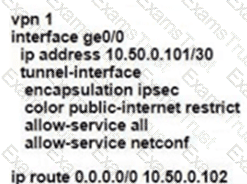
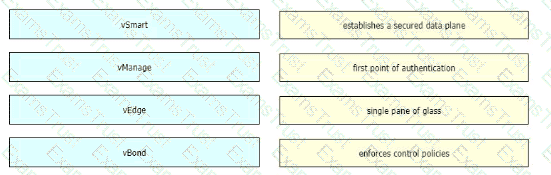
Drag and drop the devices from the left onto the correct functions on the right.
Which two products are used to deploy Cisco WAN Edge Router virtual platforms? (Choose two.)
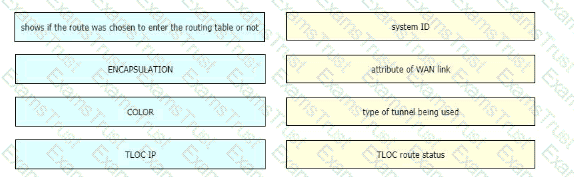
Drag and drop the route verification output from show omp tlocs from the left onto the correct explanations on the right.
What happens if the intelligent proxy is unreachable in the Cisco SD-WAN network?