Your supervisor tells you that you will participate in a CVSS assessment.
What will you be doing?
Move each definition from the list on the left to the correct CIA Triad term on the right.
Note: You will receive partial credit for each correct answer.

During an incident response, the security team needs to isolate a compromised server from the rest of the network but still allow forensic analysis. Which action should they take?
The company web server collects information through a form. The form is accessed by using port 80. The form content is transferred to an encrypted database for storage. You are investigating a complaint that the form content has been compromised.
What is the cause of the security breach?
Which two basic metrics should be taken into consideration when assigning a severity to a vulnerability during an assessment?(Choose 2.)
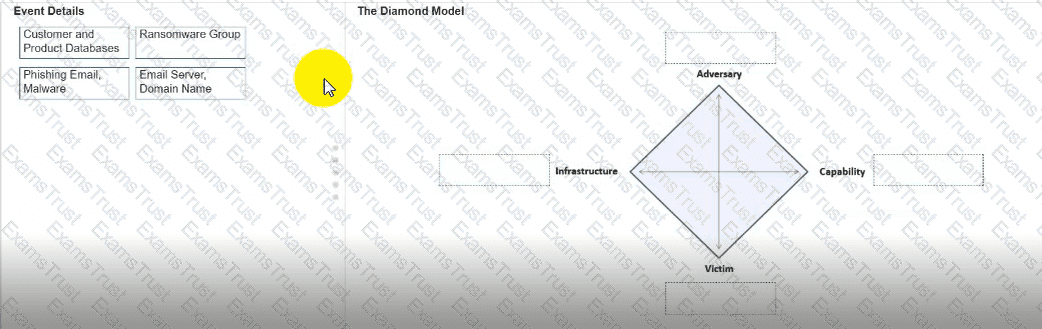
You need to diagram an intrusion event by using the Diamond Model.
Move each event detail from the list on the left to the correct location in the diagram on the right.
Note: You will receive partial credit for each correct response.
A threat actor sets up a rogue access point (AP) at a local cafe. The rogue AP captures traffic and then forwards the traffic to the cafe AP.
Which type of attack does this scenario describe?
An employee accidentally sends an email containing sensitive corporate information to an external email address.
Which type of threat does this scenario describe?
Your manager asks you to review the output of some vulnerability scans and report anything that may require escalation.
Which two findings should you report for further investigation as potential security vulnerabilities?(Choose 2.)
Which macOS security feature encrypts the entire macOS volume?
Which Windows app is a command-line interface that includes a sophisticated scripting language used to automate Windows tasks?
Move each NIST Incident Response Lifecycle phase from the list on the left to the correct description on the right.
Note: You will receive partial credit for each correct answer.

An administrator wants to ensure that any files downloaded from the internet are automatically scanned for malicious code before execution. Which security control should be implemented?
You notice that a new CVE has been shared to an email group that you belong to.
What should you do first with the CVE?
You need a software solution that performs the following tasks:
Compiles network data
Logs information from many sources
Provides orchestration in the form of case management
Automates incident response workflows
What product should you use?