What is the command to show SecureXL status?
What does it mean if Deyra sees the gateway status? (Choose the BEST answer.)
With MTA (Mail Transfer Agent) enabled the gateways manages SMTP traffic and holds external email with potentially malicious attachments. What is required in order to enable MTA (Mail Transfer Agent) functionality in the Security Gateway?
What SmartEvent component creates events?
Which of the SecureXL templates are enabled by default on Security Gateway?
Using mgmt_cli, what is the correct syntax to import a host object called Server_1 from the CLI?
SandBlast appliances can be deployed in the following modes:
Which statement is true about ClusterXL?
Can multiple administrators connect to a Security Management Server at the same time?
In R80 spoofing is defined as a method of:
The “Hit count” feature allows tracking the number of connections that each rule matches. Will the Hit count feature work independently from logging and Track the hits if the Track option is set to “None”?
The following command is used to verify the CPUSE version:
You have existing dbedit scripts from R77. Can you use them with R80.10?
What information is NOT collected from a Security Gateway in a Cpinfo?
Which command shows actual allowed connections in state table?
When a packet arrives at the gateway, the gateway checks it against the rules in the hop Policy Layer, sequentially from top to bottom, and enforces the first rule that matches a packet. Which of the following statements about the order of rule enforcement is true?
NO: 219
What cloud-based SandBlast Mobile application is used to register new devices and users?
On the following picture an administrator configures Identity Awareness:
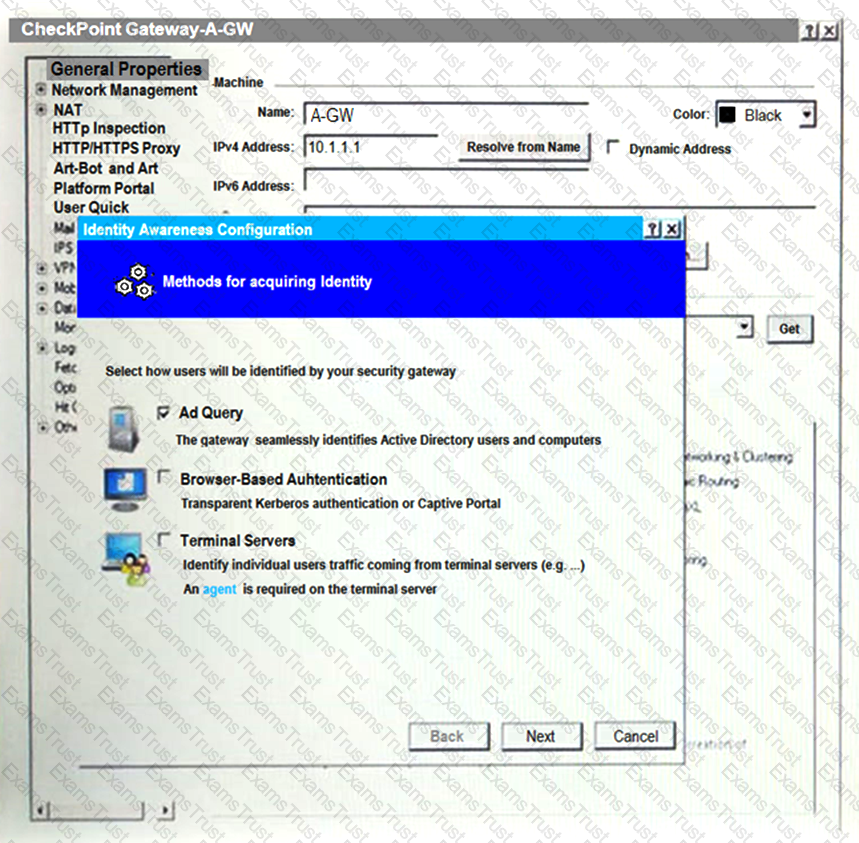
After clicking “Next” the above configuration is supported by:
Which command lists firewall chain?
Which of the following is NOT an attribute of packet acceleration?
How does the Anti-Virus feature of the Threat Prevention policy block traffic from infected websites?
You want to store the GAIA configuration in a file for later reference. What command should you use?
Fill in the blank: The R80 SmartConsole, SmartEvent GUI client, and _______ consolidate billions of logs and shows then as prioritized security events.
The system administrator of a company is trying to find out why acceleration is not working for the traffic. The traffic is allowed according to the rule base and checked for viruses. But it is not accelerated.
What is the most likely reason that the traffic is not accelerated?
Which of the following is NOT an option to calculate the traffic direction?
R80.10 management server can manage gateways with which versions installed?
What is a feature that enables VPN connections to successfully maintain a private and secure VPN session without employing Stateful Inspection?
Which of the following commands shows the status of processes?
What is mandatory for ClusterXL to work properly?
ClusterXL is fully supported by Gaia and available to all Check Point appliances. Which command is NOT related to redundancy and functions?
What is the most recommended way to install patches and hotfixes?
The Security Gateway is installed on GAIA R80. The default port for the Web User Interface is ______ .
What is the least amount of CPU cores required to enable CoreXL?
Connections to the Check Point R80 Web API use what protocol?
When an encrypted packet is decrypted, where does this happen?
SSL Network Extender (SNX) is a thin SSL VPN on-demand client that is installed on the remote user’s machine via the web browser. What are the two modes of SNX?
Which utility allows you to configure the DHCP service on Gaia from the command line?
What level of CPU load on a Secure Network Distributor would indicate that another may be necessary?
What is the command to see cluster status in cli expert mode?
In Advanced Permanent Tunnel Configuration, to set the amount of time the tunnel test runs without a
response before the peer host is declared ‘down’, you would set the_________?
SandBlast agent extends 0 day prevention to what part of the network?
NO: 240
You notice that your firewall is under a DDoS attack and would like to enable the Penalty Box feature, which command you use?
To fully enable Dynamic Dispatcher on a Security Gateway:
What is the correct order of the default “fw monitor” inspection points?
You need to change the MAC-address on eth2 interface of the gateway. What is the correct way to change MAC-address in Check Point Gaia?
To fully enable Dynamic Dispatcher with Firewall Priority Queues on a Security Gateway, run the following command in Expert mode then reboot:
What is not a component of Check Point SandBlast?
Which packet info is ignored with Session Rate Acceleration?
What is the valid range for Virtual Router Identifier (VRID) value in a Virtual Routing Redundancy Protocol (VRRP) configuration?
What will be the effect of running the following command on the Security Management Server?
In R80, where do you manage your Mobile Access Policy?
What has to be taken into consideration when configuring Management HA?
The SmartEvent R80 Web application for real-time event monitoring is called:
Which web services protocol is used to communicate to the Check Point R80 Identity Awareness Web API?
Aaron is a Syber Security Engineer working for Global Law Firm with large scale deployment of Check Point Enterprise Appliances running GAiA R80.X The Network Security Developer Team is having an issue testing the API with a newly deployed R80.X Security Management Server Aaron wants to confirm API services are working properly. What should he do first?
Which SmartConsole tab is used to monitor network and security performance?
In what way are SSL VPN and IPSec VPN different?
In order to get info about assignment (FW, SND) of all CPUs in your SGW, what is the most accurate CLI command?
Which of the following is a new R80.10 Gateway feature that had not been available in R77.X and older?
Fill in the blanks: A _______ license requires an administrator to designate a gateway for attachment whereas a ________ license is automatically attached to a Security Gateway.
Fill in the blank: The command ___________________ provides the most complete restoration of a R80 configuration.
With Mobile Access enabled, administrators select the web-based and native applications that can be accessed by remote users and define the actions that users can perform the applications. Mobile Access encrypts all traffic using:
Which of the following is NOT a component of Check Point Capsule?
The ____ software blade package uses CPU-level and OS-level sandboxing in order to detect and block malware.
Matt wants to upgrade his old Security Management server to R80.x using the Advanced Upgrade with Database Migration. What is one of the requirements for a successful upgrade?
How would you enable VMAC Mode in ClusterXL?
You work as a security administrator for a large company. CSO of your company has attended a security conference where he has learnt how hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. He wants to make sure that his company has the tight protections in place. Check Point has been selected for the security vendor.
Which Check Point product protects BEST against malware and zero-day attacks while ensuring quick delivery of safe content to your users?
What is the command to check the status of Check Point processes?
You plan to automate creating new objects using new R80 Management API. You decide to use GAIA CLI for this task.
What is the first step to run management API commands on GAIA’s shell?