Steve is troubleshooting a connection problem with an internal application. If he knows the source IP address is 192.168.4.125, how could he filter this traffic?
Fill in the blank.
Type the command and syntax to configure the Cluster Control Protocol (CCP) to use Broadcast.
Fill in the blank.
The command useful for debugging by capturing packet information, including verifying LDAP authentication on all Check Point platforms is _____
Jon is explaining how the inspection module works to a colleague. If a new connection passes through the inspection module and the packet matches the rule, what is the next step in the process?
Fill in the blank.
Write the full fw command and syntax that you would use to troubleshoot ClusterXL sync issues.
Which Check Point tool allows you to open a debug file and see the VPN packet exchange details.
Fill in the blank.
To view the number of concurrent connections going through core 0 on the firewall, you would use the command and syntax _____ _____ _____ _____ _____ _____ _____.
MegaCorp is using SmartCenter Server with several gateways. Their requirements result in a heavy log load. Would it be feasible to add the SmartEvent Correlation Unit and SmartEvent Server to their SmartCenter Server?
Fill in the blanks.
To view the number of concurrent connections going through your firewall, you would use the command and syntax _____ _____ _____ _____ _____.
You run cphaprob -a if. When you review the output, you find the word DOWN. What does DOWN mean?
Security server configuration settings are stored in _____.
When an Endpoint user is able to authenticate but receives a message from the client that it is unable to enforce the desktop policy, what is the most likely scenario?
What is the proper command for importing users into the R77 User Database?
Anytime a client initiates a connection to a server, the firewall kernel signals the FWD process using a trap. FWD spawns the _____ child service, which runs the security server.
The process that performs the authentication for SSL VPN Users is:
Which of the following CLISH commands would you use to set the admin user's shell to bash?
When configuring an LDAP Group object, select option _____ if you want the gateway to reference a specific group defined on the LDAP server for authentication purposes.
User definitions are stored in _____.
The process _____ executes the authentication for logging in to SmartDashboard.
The process _____ is responsible for the authentication for Remote Access clients.
Where do you define NAT properties so that NAT is performed either client side or server side? In SmartDashboard under:
You are the MegaCorp Security Administrator. This company uses a firewall cluster, consisting of two cluster members. The cluster generally works well but one day you find that the cluster is behaving strangely. You assume that there is a connectivity problem with the cluster synchronization link (cross-over cable). Which of the following commands is the BEST for testing the connectivity of the crossover cable?
The “MAC Magic” value must be modified under the following condition:
What is the proper CLISH syntax to configure a default route via 192.168.255.1 in GAiA?
What firewall kernel table stores information about port allocations for Hide NAT connections?
When using Captive Portal to send unidentified users to a Web portal for authentication, which of the following is NOT a recommended use for this method?
Which two processes are responsible on handling Identity Awareness?
Which of the following access options would you NOT use when configuring Captive Portal?
If using AD Query for seamless identity data reception from Microsoft Active Directory (AD), which of the following methods is NOT Check Point recommended?
Which is NOT a method through which Identity Awareness receives its identities?
MultiCorp is located in Atlanta. It has a branch office in Europe, Asia, and Africa.
Each location has its own AD controller for local user login.
How many AD queries have to be configured?
To backup all events stored in the SmartEvent Server, you should back up the contents of which folder(s)?
Your primary SmartCenter Server is installed on a Secure PlatformPro machine, which is also a VPN-1 Pro Gateway. You want to implement Management High Availability (HA). You have a spare machine to configure as the secondary SmartCenter Server. How do you configure the new machine to be the standby SmartCenter Server, without making any changes to the existing primary SmartCenter Server? (Changes can include uninstalling and reinstalling.)
What is a task of the SmartEvent Client?
All of the following are used by the DLP engine to match a message during a scan, EXCEPT:
In a Management High Availability (HA) configuration, you can configure synchronization to occur automatically, when:
1. The Security Policy is installed.
2. The Security Policy is saved.
3. The Security Administrator logs in to the secondary SmartCenter Server, and changes its status to active.
4. A scheduled event occurs.
5. The user database is installed.
Select the BEST response for the synchronization sequence. Choose one.
If Victor wanted to edit new Signature Protections, what tab would he need to access in SmartDashboard?
Which one of the following processes below would not start if there was a licensing issue?
In R76, My Organization e-mail addresses or domains are used for:
You have installed a R77 Security Gateway on GAiA. To manage the Gateway from the enterprise Security Management Server, you create a new Gateway object and Security Policy.
When you install the new Policy from the Policy menu, the Gateway object does not appear in the Install Policy window as a target. What is the problem?
When restoring a Security Management Server from a backup file, the restore package can be retrieved from which source?
Typically, when you upgrade the Security Management Server, you install and configure a fresh R77 installation on a new computer and then migrate the database from the original machine.
What is the correct order of the steps below to successfully complete this procedure?
1) Export databases from source.
2) Connect target to network.
3) Prepare the source machine for export.
4) Import databases to target.
5) Install new version on target.
6) Test target deployment.
MegaCorps' disaster recovery plan is past due for an update to the backup and restore section to enjoy the benefits of the new distributed R77 installation. You must propose a plan that meets the following required and desired objectives:
Required: Security Policy repository must be backed up no less frequently than every 24 hours.
Desired: Back up R77 components enforcing the Security Policies at least once a week.
Desired: Back up R77 logs at least once a week.
You develop a disaster recovery plan proposing the following:
The corporate IT change review committee decides your plan:
What tool exports the Management Configuration into a single file?
MegaCorp has two different types of hardware with Check Point GAiA installed and set up as gateways. The Administrator wants to provide redundancy in case one of them fails. Choose the best approach.
Which command would you use to save the interface information before upgrading a GAiA Gateway?
You need to back up the routing, interface, and DNS configuration information from your R77 GAiA Security Gateway. Which backup-and-restore solution do you use?
Which of the following statements accurately describes the migrate command?
What process manages the dynamic routing protocols (OSPF, RIP, etc.) on GAiA?
Select the command set best used to verify proper failover function of a new ClusterXL configuration.
Which of the following is NOT a feature of ClusterXL?
What could be a reason why synchronization between primary and secondary Security Management Servers does not occur?
In Management High Availability, what is an Active SMS?
A connection is said to be Sticky when:
How do new connections get established through a Security Gateway with SecureXL enabled?
What can you do to see the current number of kernel instances in a system with CoreXL enabled?
In SmartDirectory, what is each LDAP server called?
The process _____ complies $FWDIR/CONF/*.W files into machine language.
Which is the lowest Gateway version manageable by SmartCenter R77?
When migrating the SmartEvent data base from one server to another, the last step is to save the files on the new server. Which of the following commands should you run to save the SmartEvent data base files on the new server?
When restoring R76 using the command upgrade_import, which of the following items are NOT restored?
To change the default port of the Management Portal:
Which Check Point QoS feature is used to dynamically allocate relative portions of available bandwidth?
A user cannot authenticate to SSL VPN. You have verified the user is assigned a user group and reproduced the problem, confirming a failed-login session. You do not see an indication of this attempt in the traffic log. The user is not using a client certificate for login.
To debug this error, where in the authentication process could the solution be found?
Which Protection Mode does not exist in IPS?
Which of the following statements is FALSE regarding OSPF configuration on Secure Platform Pro?
What are you required to do before running upgrade_export?
You configure a Check Point QoS Rule Base with two rules:
an H.323 rule with a weight of 10, and the Default Rule with a weight of 10.
The H.323 rule includes a per-connection guarantee of 384 Kbps. and a per-connection limit of 512 Kbps. The per-connection guarantee is for four connections, and no additional connections are allowed in the Action properties. If traffic is passing through the QoS Module matches both rules, which of the following statements is TRUE?
You are configuring the VoIP Domain object for a Skinny Client Control Protocol (SCCP) environment protected by VPN-1 NGX. Which VoIP Domain object type can you use?
Laura notices the Microsoft Visual Basic Bits Protection is set to inactive. She wants to set the Microsoft Visual Basic Kill Bits Protection and all other Low Performance Impact Protections to Prevent. She asks her manager for approval and stated she can turn theses on.
But he wants Laura to make sure no high Performance Impacted Protections are turned on while changing this setting.
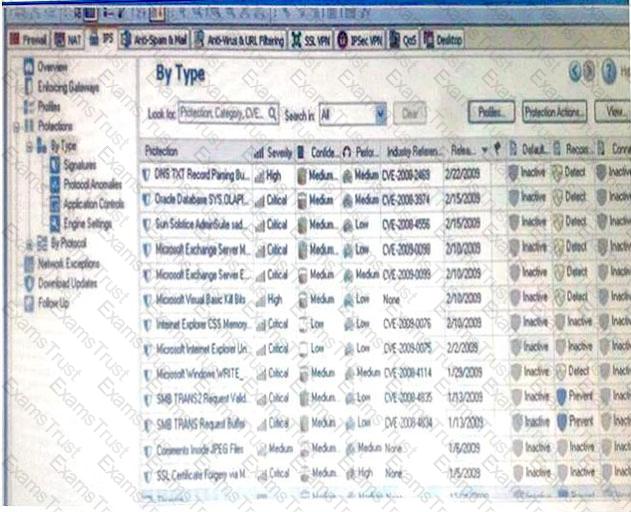
Using the out below, how would Laura change the Default_Protection on Performance Impact Protections classified as low from inactive to prevent until meeting her other criteria?
MegaCorp is running Smartcenter R70, some Gateways at R65 and some other Gateways with R60. Management wants to upgrade to the most comprehensive IPv6 support. What should the administrator do first?
MultiCorp is running Smartcenter R71 on an IPSO platform and wants to upgrade to a new Appliance with R77. Which migration tool is recommended?
Paul has just joined the MegaCorp security administration team. Natalie, the administrator, creates a new administrator account for Paul in SmartDashboard and installs the policy. When Paul tries to login it fails. How can Natalie verify whether Paul’s IP address is predefined on the security management server?
Which of the following is NOT an internal/native Check Point command?
How does Check Point recommend that you secure the sync interface between gateways?
How do you verify the Check Point kernel running on a firewall?
Katie has enabled User Directory and applied the license to Security Management Server, Green. Her supervisor has asked her to configure the Password Strength options of the least one digit, one symbol, 8 characters long and include an uppercase character. How should she accomplish this?
Which graded parameters help determine the protections to activate for security and which can be safely deactivated? Select the most correct answer.
Frank is concerned with performance and wants to configure the affinities settings. His gateway does not have the Performance pack running. What would Frank need to perform in order configure those settings?
Which Check Point ClusterXL mode is used to synchronize the physical interface IP and MAC addresses on all clustered interfaces.
Which of the following log files contains verbose information regarding the negotiation process and other encryption failures?
Which of the following statements is TRUE concerning MEP VPN’s?
Fill in the blank.
To verify that a VPN Tunnel is properly established, use the command _____.
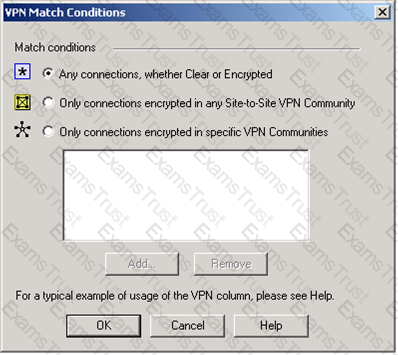
You are trying to configure Directional VPN Rule Match in the Rule Base. But the Match column does not have the option to see the Directional Match. You see the following window. What must you enable to see the Directional Match?
Exhibit:
If you need strong protection for the encryption of user data, what option would be the BEST choice?
Which statement defines Public Key Infrastructure? Security is provided:
Which of the following is TRUE concerning unnumbered VPN Tunnel Interfaces (VTIs)?
What is the most common cause for a Quick mode packet 1 failing with the error “No Proposal Chosen” error?
Remote clients are using SSL VPN to authenticate via LDAP server to connect to the organization. Which gateway process is responsible for the authentication?
When configuring a Permanent Tunnel between two gateways in a Meshed VPN community, in what object is the tunnel managed?
When two or more DLP rules are matched, the action taken is the most restrictive action.
Rank the following items from the lowest restriction level (1) to the highest (4).
1. Ask User
2. Prevent
3. Detect
4. Inform User
Choose all correct statements. SmartUpdate, located on a VPN-1 NGX SmartCenter Server, allows you to:
(1) Remotely perform a first time installation of VPN-1 NGX on a new machine
(2) Determine OS patch levels on remote machines
(3) Update installed Check Point and any OPSEC certified software remotely
(4) Update installed Check Point software remotely
(5) Track installed versions of Check Point and OPSEC products
(6) Centrally manage licenses
You just upgraded to R71 and are using the IPS Software Blade.
You want to enable all critical protections while keeping the rate of false positive very low.
How can you achieve this?
Which of the following are valid reasons for beginning with a fresh installation VPN-1 NGX R65, instead of upgrading a previous version to VPN-1 NGX R65? Select all that apply.
Which of these four Check Point QoS technologies prevents the transmission of redundant packets when multiple copies of a packet are concurrently queued on the same flow?
Public-key cryptography is considered which of the following?
Your customer wishes to install the SmartWorkflow Software Blade on a R70 Security Management server (Secure Platform).
Which is the correct method?
Your company is planning on moving their server farm to a new datacenter which requires IP changes to important network services including DNS, DHCP, and TFTP. Rather than manually logging in to all your firewalls and modifying the settings individually, you decide to purchase and enable SmartProvisioning. Assuming all your firewalls are on SPLAT, what is the minimum version required to update the firewalls' DNS and backup settings via SmartProvisioning?
What happens in relation to the CRL cache after a cpstop;spstart has been initiated?
A user attempts to initialize a network application using SSL Network Extender.
The application fails to start. What is the MOST LIKELY solution?