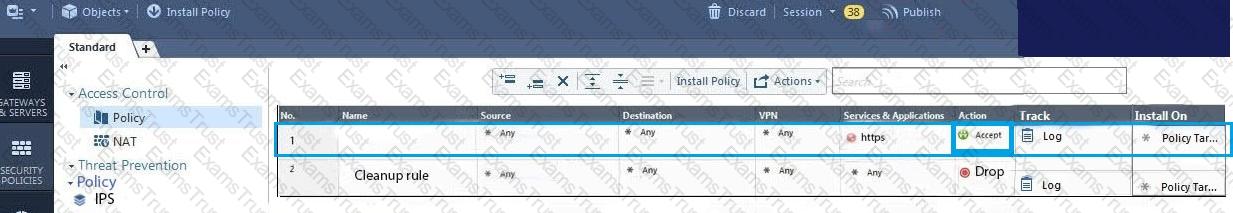
What must a Security Administrator do to comply with a management requirement to log all traffic accepted through the perimeter Security Gateway?
You believe Phase 2 negotiations are failing while you are attempting to configure a site-to-site VPN with one of your firm's business partners. Which SmartConsole application should you use to confirm your suspicious?
When using GAiA, it might be necessary to temporarily change the MAC address of the interface eth 0 to 00:0C:29:12:34:56. After restarting the network the old MAC address should be active. How do you configure this change?
An internal router is sending UDP keep-alive packets that are being encapsulated with GRE and sent through your R77 Security Gateway to a partner site. A rule for GRE traffic is configured for ACCEPT/LOG. Although the keep-alive packets are being sent every minute, a search through the SmartView Tracker logs for GRE traffic only shows one entry for the whole day (early in the morning after a Policy install).
Your partner site indicates they are successfully receiving the GRE encapsulated keep-alive packets on the 1-minute interval.
If GRE encapsulation is turned off on the router, SmartView Tracker shows a log entry for the UDP keep-alive packet every minute.
Which of the following is the BEST explanation for this behavior?
Which of these statements describes the Check Point ThreatCloud?
Which of the following actions do NOT take place in IKE Phase 1?
Your users are defined in a Windows 2008 R2 Active Directory server. You must add LDAP users to a Client Authentication rule. Which kind of user group do you need in the Client Authentication rule in R77?
Which limitation of CoreXL is overcome by using (mitigated by) Multi-Queue?
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his desktop with a static IP (10.0.0.19). He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
3) Changes from static IP address to DHCP for the client PC.
What should John request when he cannot access the web server from his laptop?
You are about to integrate RSA SecurID users into the Check Point infrastructure. What kind of users are to be defined via SmartDashboard?
As a Security Administrator, you must refresh the Client Authentication authorized time-out every time a new user connection is authorized. How do you do this? Enable the Refreshable Timeout setting:
You have just installed your Gateway and want to analyze the packet size distribution of your traffic with SmartView Monitor.
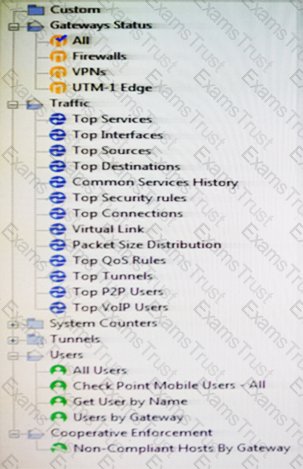
Unfortunately, you get the message:
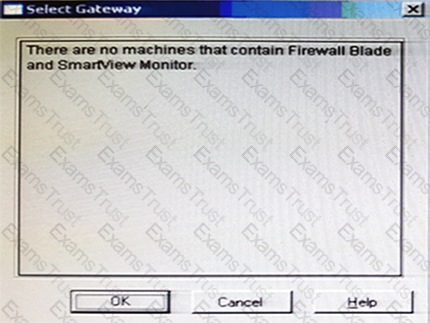
“There are no machines that contain Firewall Blade and SmartView Monitor”.
What should you do to analyze the packet size distribution of your traffic? Give the BEST answer.
Where does the security administrator activate Identity Awareness within SmartDashboard?
According to Check Point Best Practice, when adding a 3rd party gateway to a Check Point security solution what object SHOULD be added? A(n):
What is the appropriate default Gaia Portal address?
You have two rules, ten users, and two user groups in a Security Policy. You create database version 1 for this configuration. You then delete two existing users and add a new user group. You modify one rule and add two new rules to the Rule Base. You save the Security Policy and create database version 2. After a while, you decide to roll back to version 1 to use the Rule Base, but you want to keep your user database. How can you do this?
When defining QoS global properties, which option below is not valid?
What is the purpose of Priority Delta in VRRP?
What is the mechanism behind Threat Extraction?
The system administrator of a company is trying to find out why acceleration is not working for the traffic. The traffic is allowed according to the rule base and checked for viruses. But it is not accelerated. What is the most likely reason that the traffic is not accelerated?
In order to modify Security Policies the administrator can use which of the following tools? Select the BEST answer.
You installed Security Management Server on a computer using GAiA in the MegaCorp home office. You use IP address 10.1.1.1. You also installed the Security Gateway on a second GAiA computer, which you plan to ship to another Administrator at a MegaCorp hub office. What is the correct order for pushing SIC certificates to the Gateway before shipping it?
1. Run cpconfig on the Gateway, select Secure Internal Communication, enter the activation key, and reconfirm.
2. Initialize Internal Certificate Authority (ICA) on the Security Management Server.
3. Configure the Gateway object with the host name and IP addresses for the remote site.
4. Click the Communication button in the Gateway object's General screen, enter the activation key, and click Initialize and OK.
5. Install the Security Policy.
You are going to upgrade from R77 to R80. Before the upgrade, you want to back up the system so that, if there are any problems, you can easily restore to the old version with all configuration and management files intact. What is the BEST backup method in this scenario?
On the following picture an administrator configures Identity Awareness:
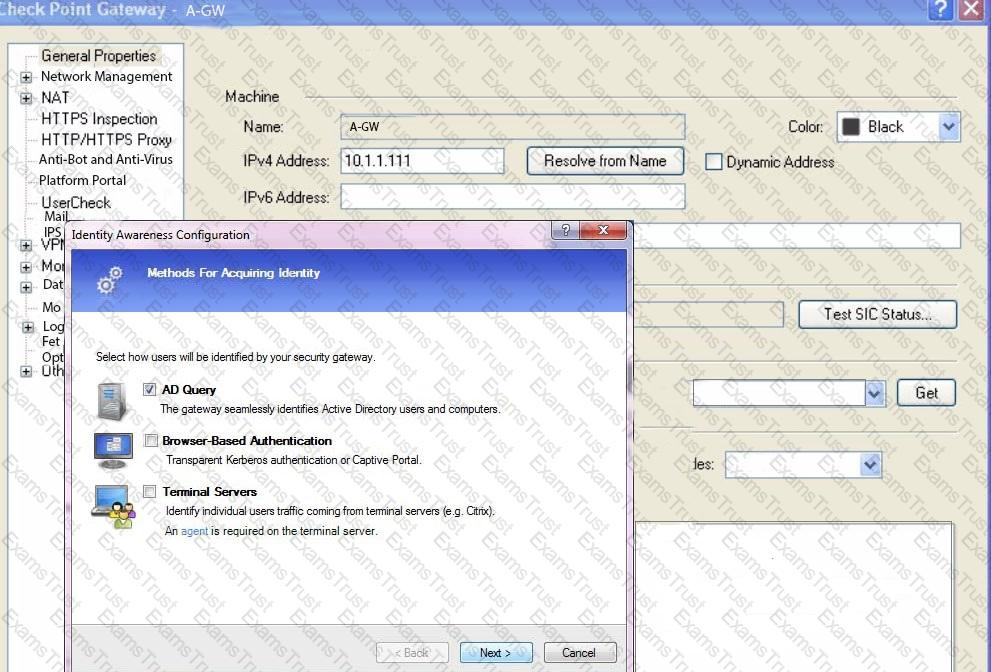
After clicking “Next” the above configuration is supported by:
Your manager requires you to setup a VPN to a new business partner site. The administrator from the partner site gives you his VPN settings and you notice that he setup AES 128 for IKE phase 1 and AES 256 for IKE phase 2. Why is this a problematic setup?
What statement is true regarding Visitor Mode?
MyCorp has the following NAT rules. You need to disable the NAT function when Alpha-internal networks try to reach the Google DNS (8.8.8.8) server.
What can you do in this case?
Which command is used to obtain the configuration lock in Gaia?
Which of the following is NOT defined by an Access Role object?
What is the default shell of Gaia CLI?
What port is used for delivering logs from the gateway to the management server?
Which authentication scheme requires a user to possess a token?
When using LDAP as an authentication method for Identity Awareness, the query:
Your bank's distributed R77 installation has Security Gateways up for renewal. Which SmartConsole application will tell you which Security Gateways have licenses that will expire within the next 30 days?
R80 Security Management Server can be installed on which of the following operating systems?
Which of the following is NOT an advantage to using multiple LDAP servers?
Administrator wishes to update IPS from SmartConsole by clicking on the option “update now” under the IPS tab. Which device requires internet access for the update to work?
You want to define a selected administrator's permission to edit a layer. However, when you click the + sign in the “Select additional profile that will be able edit this layer” you do not see anything. What is the most likely cause of this problem? Select the BEST answer.
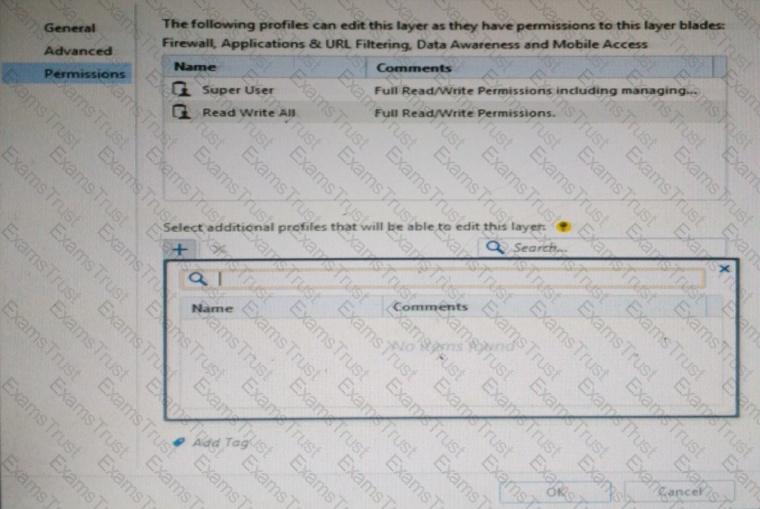
Provide very wide coverage for all products and protocols, with noticeable performance impact.
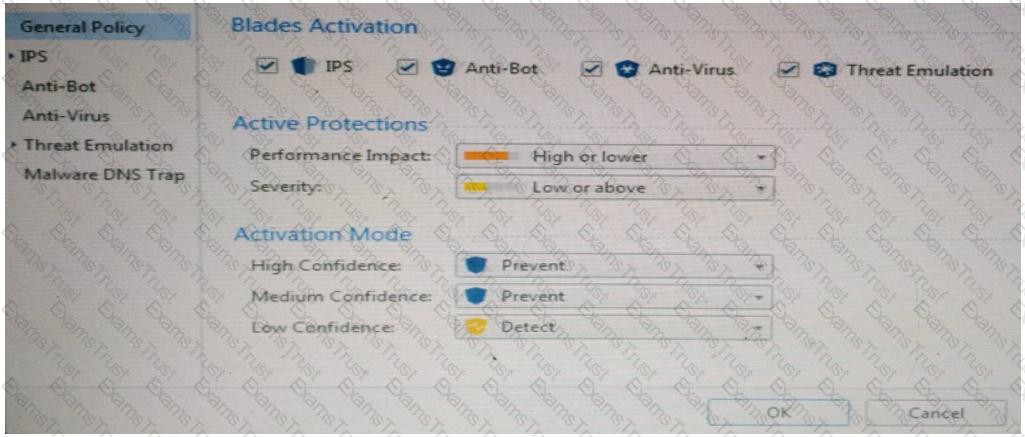
How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
Which Check Point software blade provides protection from zero-day and undiscovered threats?
You are the administrator for Alpha Corp. You have logged into your R80 Management server. You are making some changes in the Rule Base and notice that rule No.6 has a pencil icon next to it.
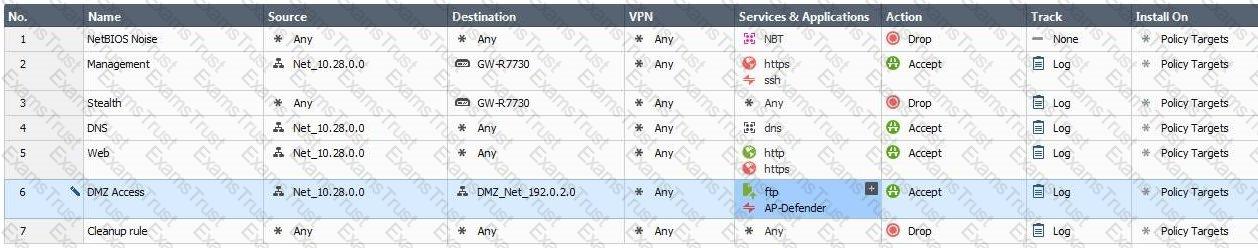
What does this mean?
Which Threat Prevention Software Blade provides comprehensive against malicious and unwanted network traffic, focusing on application and server vulnerabilities?
Fill in the blank: To build an effective Security Policy, use a ________ and _______ rule.
By default, which port does the WebUI listen on?
Which one of the following is the preferred licensing model? Select the Best answer.
Tom has been tasked to install Check Point R80 in a distributed deployment. Before Tom installs the systems this way, how many machines will he need if he does NOT include a SmartConsole machine in his calculations?
Which options are given on features, when editing a Role on Gaia Platform?
Fill in the blank: The __________ is used to obtain identification and security information about network users.
When doing a Stand-Alone Installation, you would install the Security Management Server with which other Check Point architecture component?
Which type of Check Point license is tied to the IP address of a specific Security Gateway and cannot be transferred to a gateway that has a different IP address?
What are the three essential components of the Check Point Security Management Architecture?
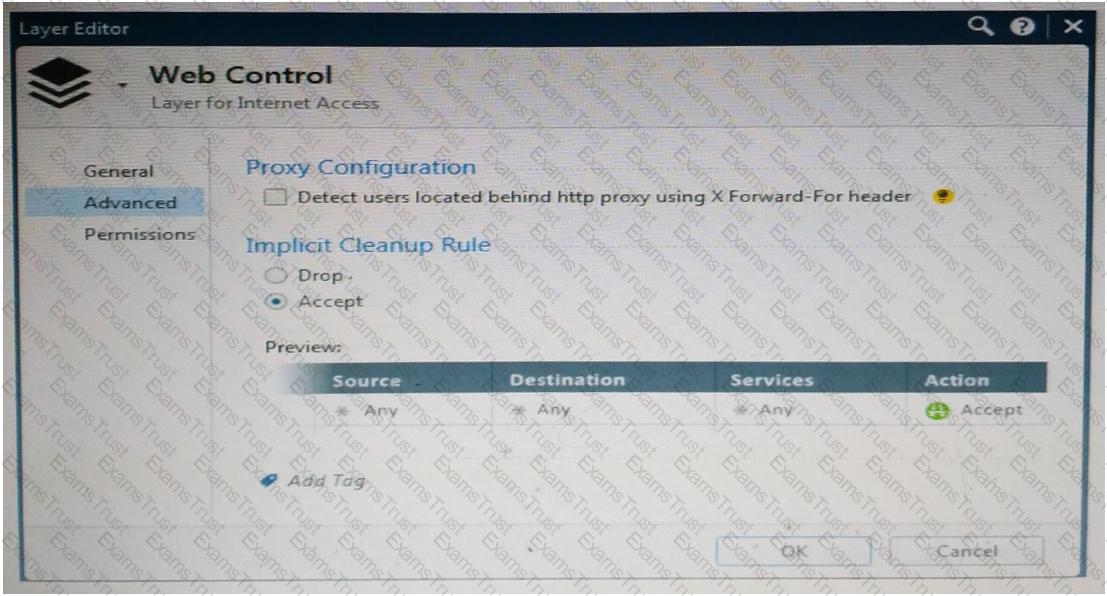
Web Control Layer has been set up using the settings in the following dialogue:
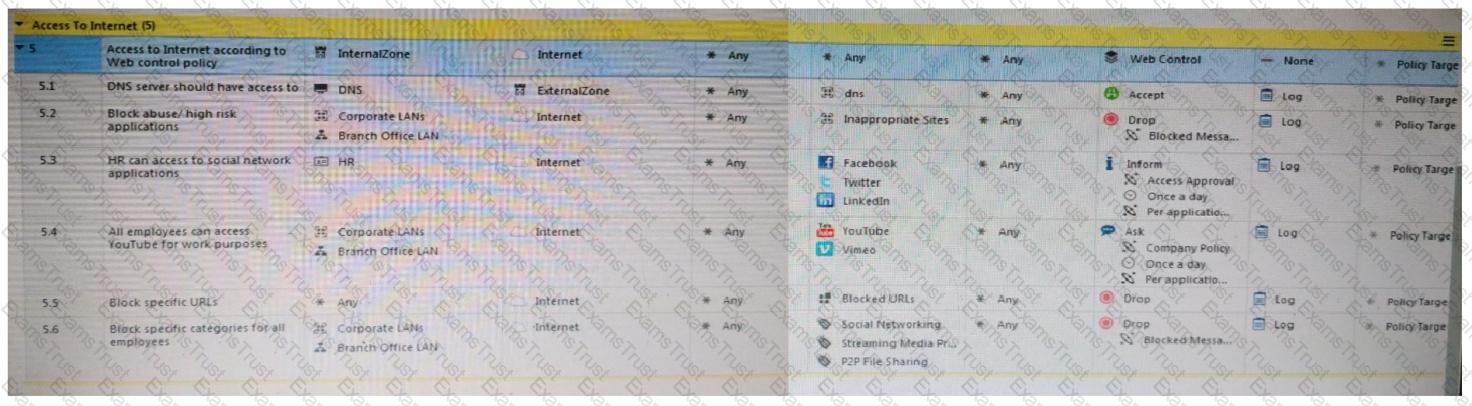
Consider the following policy and select the BEST answer.
Which of the following Automatically Generated Rules NAT rules have the lowest implementation priority?
Which of the following ClusterXL modes uses a non-unicast MAC address for the cluster IP address?
While enabling the Identity Awareness blade the Identity Awareness wizard does not automatically detect the windows domain. Why does it not detect the windows domain?
On the following graphic, you will find layers of policies.
What is a precedence of traffic inspection for the defined polices?
Which Check Point feature enables application scanning and the detection?
When a packet arrives at the gateway, the gateway checks it against the rules in the top Policy Layer, sequentially from top to bottom, and enforces the first rule that matches a packet. Which of the following statements about the order of rule enforcement is true?
Which of the following is NOT a component of a Distinguished Name?
Joey wants to configure NTP on R80 Security Management Server. He decided to do this via WebUI. What is the correct address to access the Web UI for Gaia platform via browser?
If the Active Security Management Server fails or if it becomes necessary to change the Active to Standby, the following steps must be taken to prevent data loss. Providing the Active Security Management Server is responsible, which of these steps should NOT be performed:
What Check Point technologies deny or permit network traffic?
Identify the ports to which the Client Authentication daemon listens on by default?
How Capsule Connect and Capsule Workspace differ?
SandBlast offers flexibility in implementation based on their individual business needs. What is an option for deployment of Check Point SandBlast Zero-Day Protection?
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
Which of the following are types of VPN communities?
What is the BEST command to view configuration details of all interfaces in Gaia CLISH?
Which of the following is NOT a policy type available for each policy package?
Can multiple administrators connect to a Security Management Server at the same time?
What Check Point tool is used to automatically update Check Point products for the Gaia OS?
What is the purpose of the Clean-up Rule?
Which one of the following is a way that the objects can be manipulated using the new API integration in R80 Management?
Which message indicates IKE Phase 2 has completed successfully?
When a Security Gateways sends its logs to an IP address other than its own, which deployment option is installed?
True or False: In a Distributed Environment, a Central License can be installed via CLI on a Security Gateway
Which deployment adds a Security Gateway to an existing environment without changing IP routing?
What are the two types of NAT supported by the Security Gateway?