You are attempting to establish an FTP session between your computer and a remote server, but it is not being completed successfully. You think the issue may be due to IPS. Viewing SmartView Tracker shows no drops. How would you confirm if the traffic is actually being dropped by the gateway?
Tom is troubleshooting NAT issues using fw monitor and Wireshark. He tries to initiate a connection from the external network to a DMZ server using the public IP which the firewall translates to the actual IP of the server. He analyzes the captured packets using Wireshark and observes that the destination IP is being changed as required by the firewall but does not see the packet leave the external interface. What could be the reason?
Which flag in the fw monitor command is used to print the position of the kernel chain?
Ann wants to hide FTP traffic behind the virtual IP of her cluster. Where is the relevant file table.def located to make this modification?
Where would you go to adjust the number of Kernels in CoreXL?
A firewall has 8 CPU cores and the correct license. CoreXL is enabled. How could you set kernel instance #3 to run on processing core #5?
A Security Administrator wants to increase the amount of processing cores on a Check Point Security Gateway. He starts by increasing the number of cores, however the number of kernel instances remain the same way. What is the correct process to increase the number of kernel instances?
What is required when changing the configuration of the number of workers in CoreXL?
You have just taken over as a firewall administrator. Your company is using Geo Protections on your gateway, but you want to verify that the protections are up-to-date. How can you see when these were updated?
Which of the following CANNOT be used as a source/destination for an IPS network exception?
You have spent time configuring the IPS profile on your primary gateway firewall. You want to ensure that this profile can be applied to all gateway firewalls in your environment. How can you share this information between firewalls?
You are a system administrator and would like to configure Geo Protection on your gateway to comply with a new corporate policy. What must you have to do this?
From which version can you add Proxy ARP entries through the GAiA portal?
If you need to use a Domain object in the Rule Base, where should this rule be located?
Where would you find CPU information like model, number of cores, vendor and architecture?
The 'Maximum Entries' value in the GAiA Portal corresponds to the 'gc_thresh3' parameter in the Linux kernel and has value of 1024. Knowing this, you know that gc_thresh2 and gc_thresh1 if are automatically set to the values:
After creating and pushing out a new policy, Joe finds that an old connection is still being allowed that should have been closed after his changes. He wants to delete the connection on the gateway, and looks it up with fw tab –t connections –u. Joe finds the connection he is looking for. What command should Joe use to remove this connection?
<0,a128c22,89,a158508,89,11;10001,2281,25,15b,a1,4ecdfeee,ac,691400ac,7b6,3e,ffffffff,3c,3c,0,0,0,0,0,0,0,0,0,0,0,0,0,0>
Extended Cluster Anti-Spoofing checks what value to determine if a packet with the source IP of a gateway in the cluster is being spoofed?
What is the function of the setting "no_hide_services_ports" in the tables.def files?
Your customer receives an alert from their network operation center, they are seeing ARP and Ping scans of their network originating from the firewall. What could be the reason for the behaviour?
What is the best way to see how much traffic went through the firewall that was TCP, UDP and ICMP?
ACME Corp has a cluster consisting of two 13500 appliances. As the Firewall Administrator, you notice that on an output of top, you are seeing high CPU usage of the cores assigned as SNDs, but low CPU usage on cores assigned to individual fw_worker_X processes. What command should you run next to performance tune your cluster?
When a cluster member is completely powered down, how will the other member identify if there is network connectivity?
How would you determine the value of 'Maximum concurrent connections' of the NAT Table?
Which operating systems support Wire mode?
Where do you configure VTIs on your R77 gateway in VSX mode?
You would like to configure unnumbered VTIs and your environment uses load sharing clustering. Would this clustering technology be supported by your unnumbered VTI’s?
When configuring a Numbered VPN-Tunnel, what parameters are necessary?
When VPN user-based authentication fails, which of the following debug logs is essential to understanding the issue?
You are attempting to establish a VPN tunnel between a Check Point gateway and a 3rd party vendor. When attempting to send traffic to the peer gateway it is failing. You look in SmartView Tracker and see that the failure is due to “Encryption failure: no response from peer”. After running a VPN debug on the problematic gateway, what is one of the files you would want to analyze?
What would the following command fw monitor tell you?
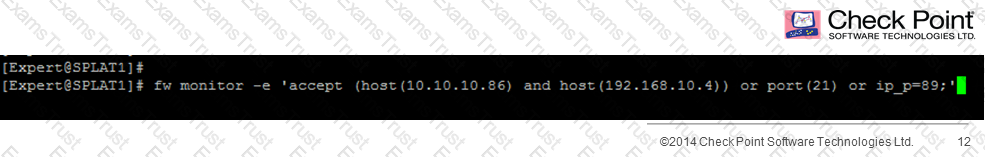
In IKEView while troubleshooting a VPN issue between your gateway and a partner site you see an entry that states “Invalid ID”. Which of the following is the most likely cause?
What does the IP Options Strip represent under the fw chain output?
When you perform an install database, the status window is filled with large amounts of text. What could be the cause?
The command _____________ shows which firewall chain modules are active on a gateway.
You are running a debugging session and you have set the debug environment to TDERROR_ALL_ALL=5 using the command export TDERROR_ALL_ALL=5. How do you return the debug value to defaults?
Which of the following statements are TRUE about SecureXL?
I. SecureXL is able to accelerate all connections through the firewall.
II. Medium path acceleration will still cause some CPU utilization of CoreXL cores.
III. F2F connections represent “forwarded to firewall” connections that are not accelerated and fully processed through the firewall kernel.
IV. Packets going through SecureXL must be inspected by the firewall kernel before being accelerated.
Consider the following Rule Base;
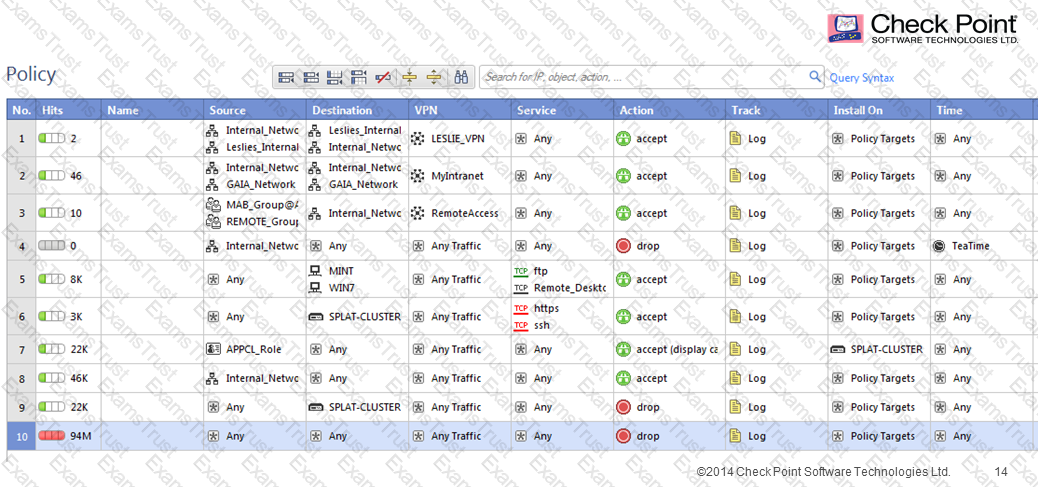
What can be concluded in regards to SecureXL Accept Templates?
Look at the follow Rule Base display. Rule 5 contains a TIME object. What is the effect on the following rules?
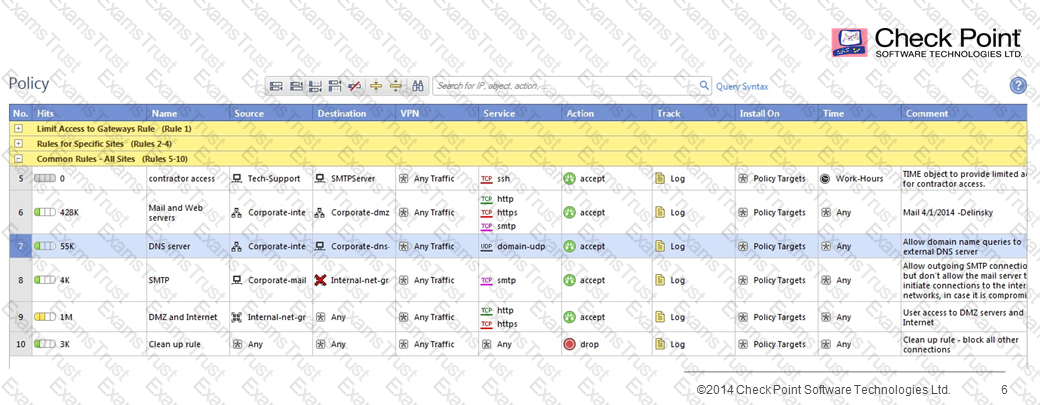
When optimizing a customer firewall Rule Base, what is the BEST way to start the analysis?
Which of the following is true when IPv6 is enabled on a Security Gateway?
Which of these commands can be used to display the IPv6 routes?
Does R77 SmartDashboard support IPv6?
True or False: It is possible to operate a Security Gateway entirely with IPv6 addressing.