After launching a new Amazon EC2 instance from a Microsoft Windows 2012 Amazon Machine Image (AMI), the SysOps Administrator is unable to connect to the instance using Remote Desktop Protocol (RDP). The instance is also unreachable. As part of troubleshooting, the Administrator deploys a second instance from a different AMI using the same configuration and is able to connect to the instance.
What should be the next logical step in troubleshooting the first instance?
A serverless application running on AWS Lambda is expected to receive a significant increase in traffic. A SysOps Administrator needs to ensure that the Lambda function is configured to scale so the application can process the increased traffic.
What should the Administrator do to accomplish this?
A company’s website went down for several hours. The root cause was a full disk on one of the company’s Amazon EC2 instances.
Which steps should the SysOps Administrator take to prevent this from happening in this future?
A company is deploying a web service to Amazon EC2 instances behind an Elastic Load Balancer. All resources will be defined and created in a single AWS CloudFormation stack using a template. The creation of each EC2 instance will not be considered complete until an initialization script has been run successfully on the EC2 instance. The Elastic Load Balancer cannot be created until all EC2 instances have been created.
Which CloudFormation resource will coordinate the Elastic Load Balancer creation in the CloudFormation stack template?
A sysops administrator is reviewing AWS Trusted Advisor warnings and encounters a warning for an S3 bucket policy that has open access permissions. While discussing the issue with the bucket owner, the administrator realizes the S3 bucket is an origin for an Amazon CloudFront web distribution.
A security researcher has published a new Common Vulnerabilities and Exposures (CVE) report that impacts a popular operating system A SysOps Administrator is concerned with the new CVE report and wants to patch the company's systems immediately The Administrator contacts AWS Support and requests the patch be applied to all Amazon EC2 instances
How will AWS respond to this request?
A company designed a specialized Amazon EC2 instance configuration for its Data Scientists. The Data Scientists want to create end delete EC2 instances on their own, but are not comfortable with configuring all the settings for EC2 instances without assistance. The configuration runs proprietary software that must be kept private within the company's AWS accounts and should be available to the Data Scientists, but no other users within the accounts.
Which solution should a SysOps Administrator use to allow the Data Scientists to deploy their workloads with MINIMAL effort?
A company has a web application that runs both on-premises and on Amazon EC2 instances. Over time both the on-premises servers and EC2 instances begin crashing A sysops administrator suspects a memory leak in the application and wants a unified method to monitor memory utilization over time.
How can the Administrator track both the EC2 memory utilization and on-premises server memory utilization over time?
A company uses multiple accounts for its applications. Account A manages the company’s Amazon Route 53 domains and hosted zones. Account B uses a load balancer fronting the company’s web servers.
How can the company use Route 53 to point to the load balancer in the MOST cost-effective and efficient manner?
Which component of an Ethernet frame is used to notify a host that traffic is coming?
A SysOps administrator is managing a VPC network consisting of public and private subnets. Instances in the private subnets access the internet through a NAT gateway. A recent AWS bill shows that the NAT gateway charges have doubled. The administrator wants to identify which instances are creating the most network traffic.
How should this be accomplished?
Security has identified an IP address that should be explicity denied for both ingress and egress requests for all services in an Amazon VPC immediately.
Which feature can be used to meet this requirement?
A sysops administrator has an AWS Lambda function that performs maintenance on various AWS resources. This function must be run nightly. Which is the MOST cost-effective solution?
A company received its latest bill with a large increase in the number of requests against Amazon SQS as compared to the month prior. The company is not aware of any major changes in its SQA usage. The company is concerned about the cost increase and who or what was making these calls.
What should a sysops administrator use to validate the calls mode to SQS?
A company needs to deploy a web application on two Amazon EC2 instances behind an Application Load Balancer (ALB). Two EC2 instances will also be deployed to host the database. The infrastructure needs to be designed across Availability Zones for high availability and must limit public access to the instances as much as possible.
How should this be achieved within a VPC?
A SysOps Administrator is creating additional Amazon EC2 instances and receives an InstanceLimitExceeded error.
What is the cause of the issue and how can it be resolved?
A SysOps administrator is evaluating Amazon Route 53 DNS options to address concerns about high availability tor an on-premises website. The website consists of two servers: a primary active server and a secondary passive server. Route 53 should route traffic to the primary server if the associated health check returns 2xx or 3xx HTTP codes. AH other traffic should be directed to the secondary passive server. The failover record type, set ID, and routing policy have been set appropriately for both primary and secondary servers.
Which next step should be taken to configure Route 53?
A security researcher has published a new Common Vulnerabilities and Exposures (CVE) report that impacts a popular operating system A SysOps Administrator is concerned with the new CVE report and wants to patch the company's systems immediately The Administrator contacts AWS Support and requests the patch be applied to all Amazon EC2 instances
How will AWS respond to this request?
A SysOps administrator is implementing automated I/O load performance testing as part of lite continuous integraliorVcontinuous delivery (CI'CD) process for an application The application uses an Amazon Elastic Block Store (Amazon E8S) Provisioned IOPS volume for each instance that is restored from a snapshot and requires consistent I/O performance. During the initial tests, the I/O performance results are sporadic. The SysOps administrator must ensure that the tests yield more consistent results.
Which actions could the SysOps administrator take to accomplish this goal? (Select TWO.)
A SysOps administrator implemented the following bucket policy to allow only the corporate IP address range of 54.240.143.0/24 to access objects in an Amazon S3 bucket. 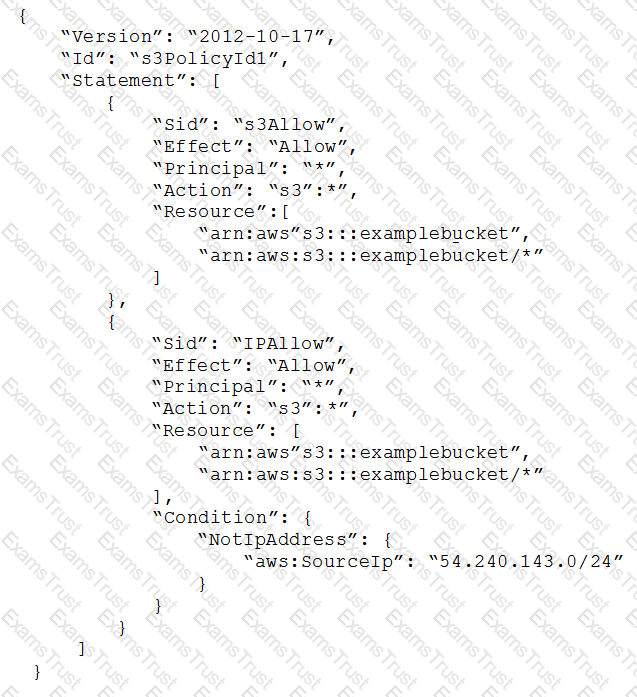
Some employees are reporting that they are able to access the S3 bucket from IP addresses outside the corporate IP address range.
How can the Administrator address this issue?
A company has an AWS account for each department and wants to consolidate billing and reduce overhead. The company wants to make sure that the finance team is denied from accessing services other than Amazon EC2: the security team is denied from accessing services other than AWS CloudTrail. and IT can access any resource.
Which solution meets these requirements with the LEAST amount of operational overhead''
An application running on Amazon EC2 allows users to launch batch jobs for data analysis. The jobs are run asynchronously, and the user is notified when they are complete. While multiple jobs can run concurrently, a user’s request need not be fulfilled for up to 24 hours. To run a job, the application launches an additional EC2 instance that performs all the analytics calculations. A job takes between 75 and 110 minutes to complete and cannot be interrupted.
What is the MOST cost-effective way to run this workload?
A SysOps administrator is configuring an application on AWS to be used over the internet by departments in other countries For remote locations, the company requires a static public IP address to be explicitly allowed as a target for outgoing internet traffic
How should the SysOps administrator deploy the application to meet this requirement?
A company has deployed a fleet of Amazon EC2 web servers for the upcoming release of a new product. The SysOps Administrator needs to test the Amazon CloudWatch notification settings for this deployment to ensure that a notification is sent using Amazon SNS if the CPU utilization of an EC2 instance exceeds 70%.
How should the Administrator accomplish this?
A SysOps Administrator observes a large number of rogue HTTP requests on an Application Load Balancer (ALB). The requests originate from various IP addresses.
Which action should be taken to block this traffic?
A SysOps Administrate is building a process for sharing Amazon RDS database snapshots between different accounts associated with different business units within the same company All data must be encrypted at rest
How should the Administrate implement this process?
Company issued SSL certificates to its users, and needs to ensure the private keys that are used to sign the certificates are encrypted. The company needs to be able to store the private and perform cryptographic signing operations in a secure environment.
Which service should be used to meet these requirements?
A SysOps Administrator must remove public IP addresses from all Amazon EC2 Instances to prevent exposure to the internet. However, many corporate applications running on those EC2 instances need to access Amazon S3 buckets. The administrator is tasked with allowing the EC2 instances to continue to access the S3 buckets.
Which solutions can be used? (Select Two).
A SysOpsAdministrator is managing a large organization with multiple accounts on the Business Support plan all linked to a single payer account. The Administrator wants to be notified automatically of AWS Personal Health Dashboard events.
In the main payer account, the Administrator configures Amazon CloudWatch Events triggered by AWS Health events triggered by AWS Health triggered by AWS Health events to issue notifications using Amazon SNS, but alerts in the linked accounts failed to trigger.
Why did the alerts fail?
A recent AWS CloudFormation stack update has failed and returned the error update_rollback_failed. A Sysops administrator is tasked with returning the CloudFormation stack to its previous working state.
What must be done to accomplish this?
A company needs to run a distributed application that processes large amounts of data across multiple EC2 instances. The application is designed to tolerate processing interruptions.
What is the MOST cost-effective Amazon EC2 pricing model for these requirements?
Development teams are maintaining several workloads on AWS. Company management is concerned about rising costs and wants the SysOps Administrator to configure alerts so teams are notified when spending approaches preset limits.
Which AWS service will satisfy these requirements?
A company uses federation to authenticate users and grant AWS permissions. The SysOps Administrator has been asked to determine who made a request to AWS Organizations for a new AWS account.
What should the Administrator review to determine who made the request?
An application is running on multiple EC2 instances. As part of an initiative to improve overall infrastructure security, the EC2 instances were moved to a private subnet. However, since moving, the EC2 instances have not been able to automatically update, and a SysOps Administrator has not been able to SSH into them remotely.
Which two actions could the Administrator take to securely resolve these issues? (Choose two.)
A company is managing a website with a global user base hosted on Amazon EC2 with an Application Load Balancer (ALB). To reduce the load on the web servers, a SysOps administrator configures an Amazon CloudFront distribution with the ALB as the origin After a week of monitoring the solution, the administrator notices that requests are still being served by the ALB and there is no change in the web server load.
What are possible causes tor this problem? (Select TWO.)
A company creates custom AMI images by launching new Amazon EC2 instances from an AWS CloudFormation template. It installs and configures necessary software through AWS OpsWorks, and takes images of each EC2 instance. The process of installing and configuring software can take between 2 to 3 hours, but at times, the process stalls due to installation errors.
The SysOps Administrator must modify the CloudFormation template so if the process stalls, the entire stack will fail and roll back.
Based on these requirements, what should be added to the template?
A company has deployed its infrastructure using AWS CloudFormation Recently the company made manual changes to the infrastructure. A SysOps Administrator is tasked with determining what was changed and updating the CloudFormation template
Which solution will ensure all the changes are captured?
A SysOps Administrator is configuring AWS SSO tor the first time. The Administrator has already created a directory in the master account using AWS Directory Service and enabled full access in AWS Organizations
What should the Administrator do next to configure the service?
A company is running critical applications on Amazon EC2 instances. The company needs to ensure its resources are automatically recovered if they become impaired due to an underlying hardware failure.
Which service can be used to monitor and recover the EC2 instances?