Click the Exhibit button.
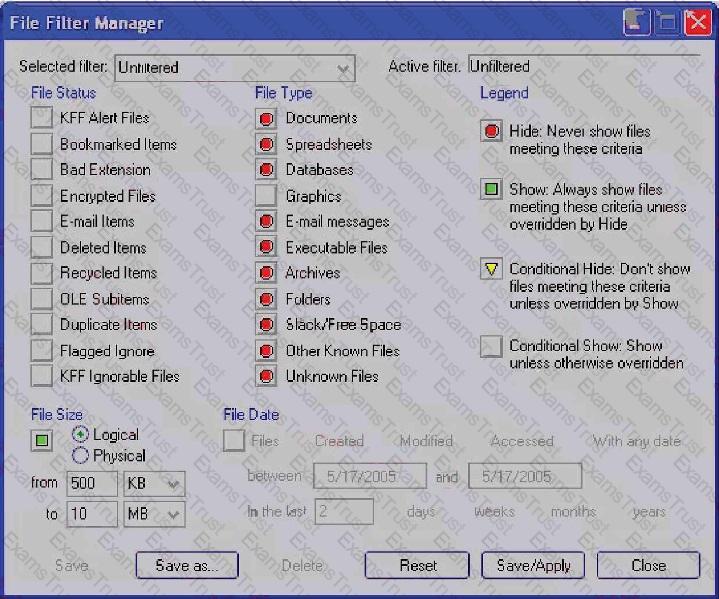
What change do you make to the file filter shown in the exhibit in order to show only graphics with a logical size between 500 kilobytes and 10 megabytes?
What is the purpose of the Golden Dictionary?
What happens when a duplicate hash value is imported into a KFF database?
In FTK, which search broadening option allows you to find grammatical variations of the word "kill" such as "killer," "killed," and "killing"?
To obtain protected files on a live machine with FTK Imager, which evidence item should be added?
You are using FTK to process e-mail files. In which two areas can E-mail attachments be
located? (Choose two.)
What are two functions of the Summary Report in Registry Viewer? (Choose two.)
FTK Imager can be invoked from within which program?
When previewing a physical drive on a local machine with FTK Imager, which statement is true?